In a world in which screens are the norm, the charm of tangible, printed materials hasn't diminished. Whatever the reason, whether for education for creative projects, just adding the personal touch to your home, printables for free can be an excellent source. In this article, we'll dive into the sphere of "What Is Attack In Cryptography And Network Security," exploring the benefits of them, where to get them, as well as how they can enhance various aspects of your daily life.
Get Latest What Is Attack In Cryptography And Network Security Below
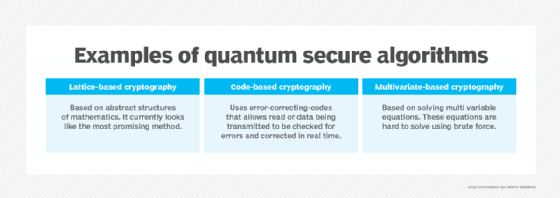
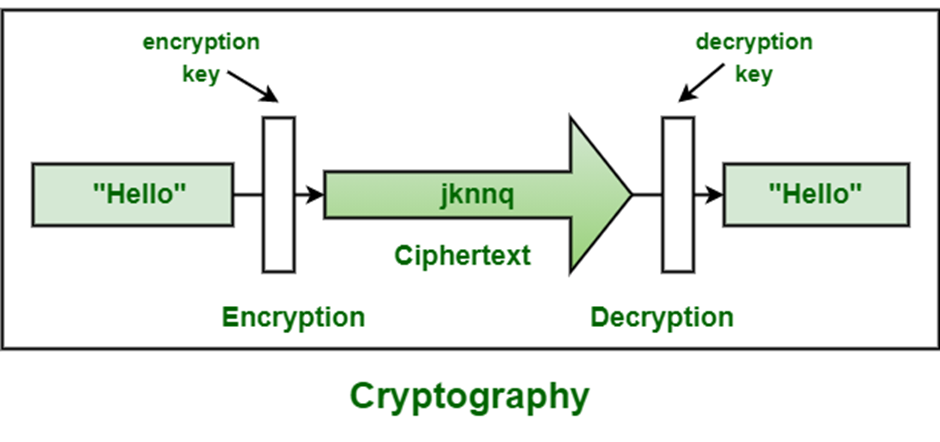
What Is Attack In Cryptography And Network Security
What Is Attack In Cryptography And Network Security - What Is Attack In Cryptography And Network Security, What Is Birthday Attack In Cryptography And Network Security, What Is Brute Force Attack In Cryptography And Network Security, What Is Cryptographic Attack In Cyber Security, Dos Attack In Cryptography And Network Security, Cryptographic Attacks In Cryptography And Network Security, Security Attacks In Cryptography And Network Security Ppt, Flooding Attacks In Cryptography And Network Security, Types Of Attacks In Cryptography And Network Security, What Is Security Attack In Cryptography
meta 0 z I2 1 Hartman 2008
ai ai
What Is Attack In Cryptography And Network Security cover a large collection of printable documents that can be downloaded online at no cost. They come in many forms, including worksheets, templates, coloring pages and more. One of the advantages of What Is Attack In Cryptography And Network Security is their flexibility and accessibility.
More of What Is Attack In Cryptography And Network Security
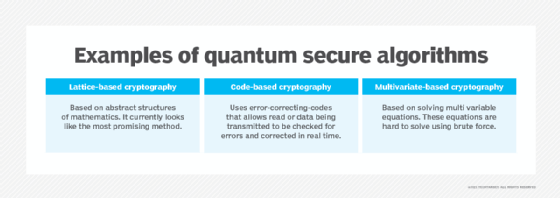
Quantum Safe Cryptography IBM Research Zurich
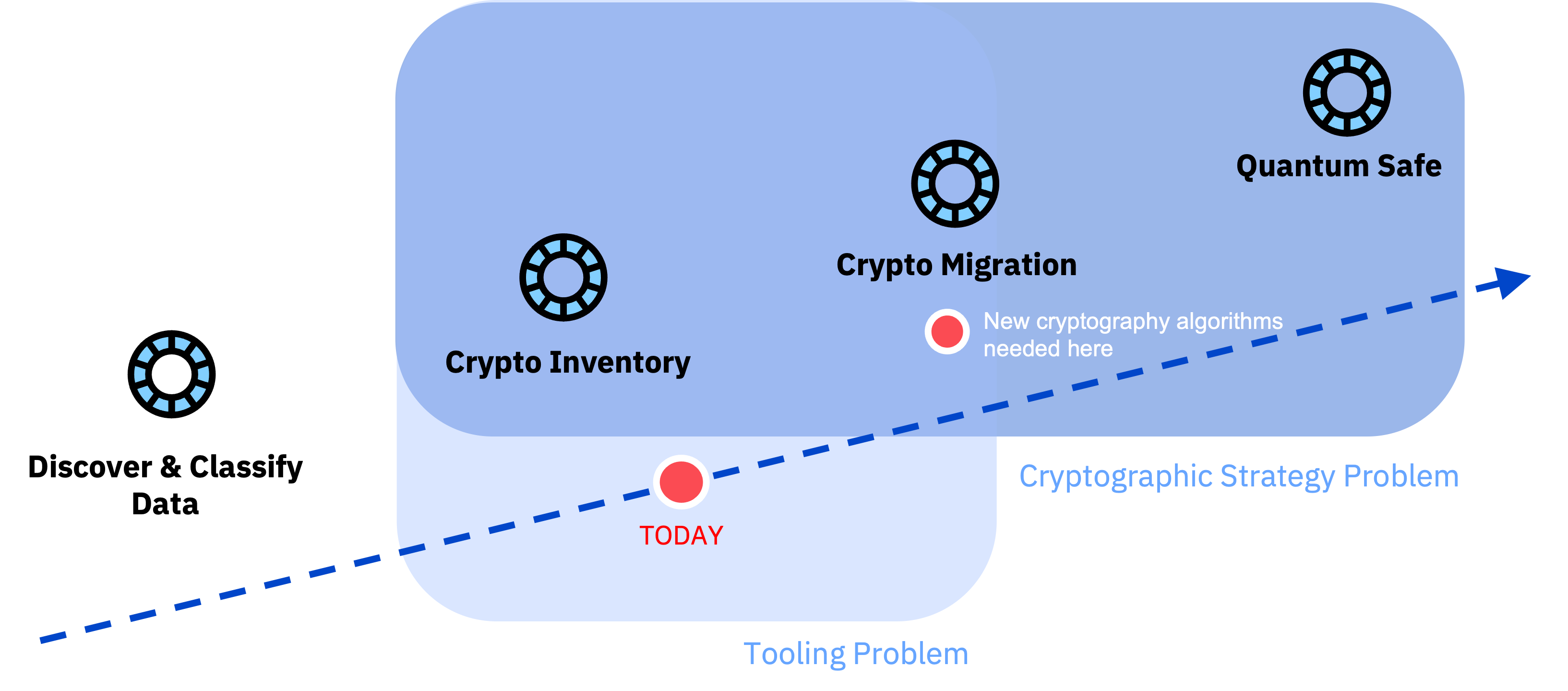
Quantum Safe Cryptography IBM Research Zurich
Python
steam 3 3 4
What Is Attack In Cryptography And Network Security have garnered immense popularity due to a myriad of compelling factors:
-
Cost-Efficiency: They eliminate the requirement of buying physical copies of the software or expensive hardware.
-
Flexible: This allows you to modify print-ready templates to your specific requirements such as designing invitations planning your schedule or even decorating your house.
-
Educational Value: Printing educational materials for no cost can be used by students of all ages. This makes them a vital aid for parents as well as educators.
-
Convenience: Instant access to a variety of designs and templates cuts down on time and efforts.
Where to Find more What Is Attack In Cryptography And Network Security
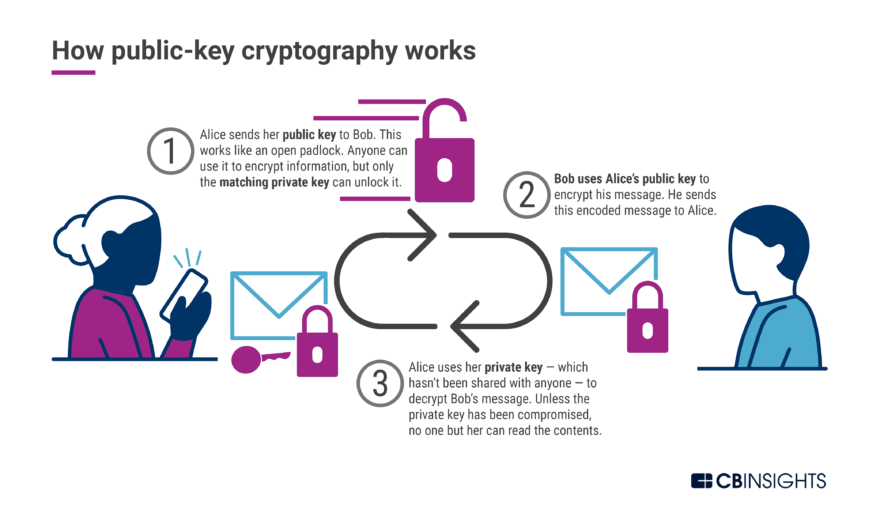
Concept Of Cryptography In Blockchain

Concept Of Cryptography In Blockchain
2 After the attack they returned to base 3 The family base was crucial to my development Basis
Y me sorprend a que el t tulo original Attack of the 50 Foot Woman empleaba el singular foot cuando se refiere a un n mero diferente a 1 gengo Senior Member
Now that we've ignited your interest in What Is Attack In Cryptography And Network Security and other printables, let's discover where they are hidden gems:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide an extensive selection of What Is Attack In Cryptography And Network Security for various goals.
- Explore categories like home decor, education, crafting, and organization.
2. Educational Platforms
- Educational websites and forums typically offer free worksheets and worksheets for printing, flashcards, and learning materials.
- Great for parents, teachers and students in need of additional resources.
3. Creative Blogs
- Many bloggers share their innovative designs and templates for no cost.
- The blogs covered cover a wide range of interests, that includes DIY projects to planning a party.
Maximizing What Is Attack In Cryptography And Network Security
Here are some ideas in order to maximize the use of printables for free:
1. Home Decor
- Print and frame stunning artwork, quotes or festive decorations to decorate your living areas.
2. Education
- Use these printable worksheets free of charge to reinforce learning at home, or even in the classroom.
3. Event Planning
- Invitations, banners and other decorations for special occasions such as weddings, birthdays, and other special occasions.
4. Organization
- Keep your calendars organized by printing printable calendars checklists for tasks, as well as meal planners.
Conclusion
What Is Attack In Cryptography And Network Security are an abundance of practical and imaginative resources for a variety of needs and hobbies. Their accessibility and versatility make these printables a useful addition to both professional and personal life. Explore the vast array of printables for free today and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables actually are they free?
- Yes, they are! You can print and download these tools for free.
-
Does it allow me to use free printables for commercial uses?
- It depends on the specific conditions of use. Be sure to read the rules of the creator prior to printing printables for commercial projects.
-
Do you have any copyright problems with printables that are free?
- Some printables may come with restrictions on usage. Always read the terms and conditions offered by the designer.
-
How do I print What Is Attack In Cryptography And Network Security?
- You can print them at home using the printer, or go to an in-store print shop to get more high-quality prints.
-
What software do I need to run What Is Attack In Cryptography And Network Security?
- The majority are printed as PDF files, which can be opened using free software, such as Adobe Reader.
What Is Quantum Cryptography And How It Works Sectigo Official
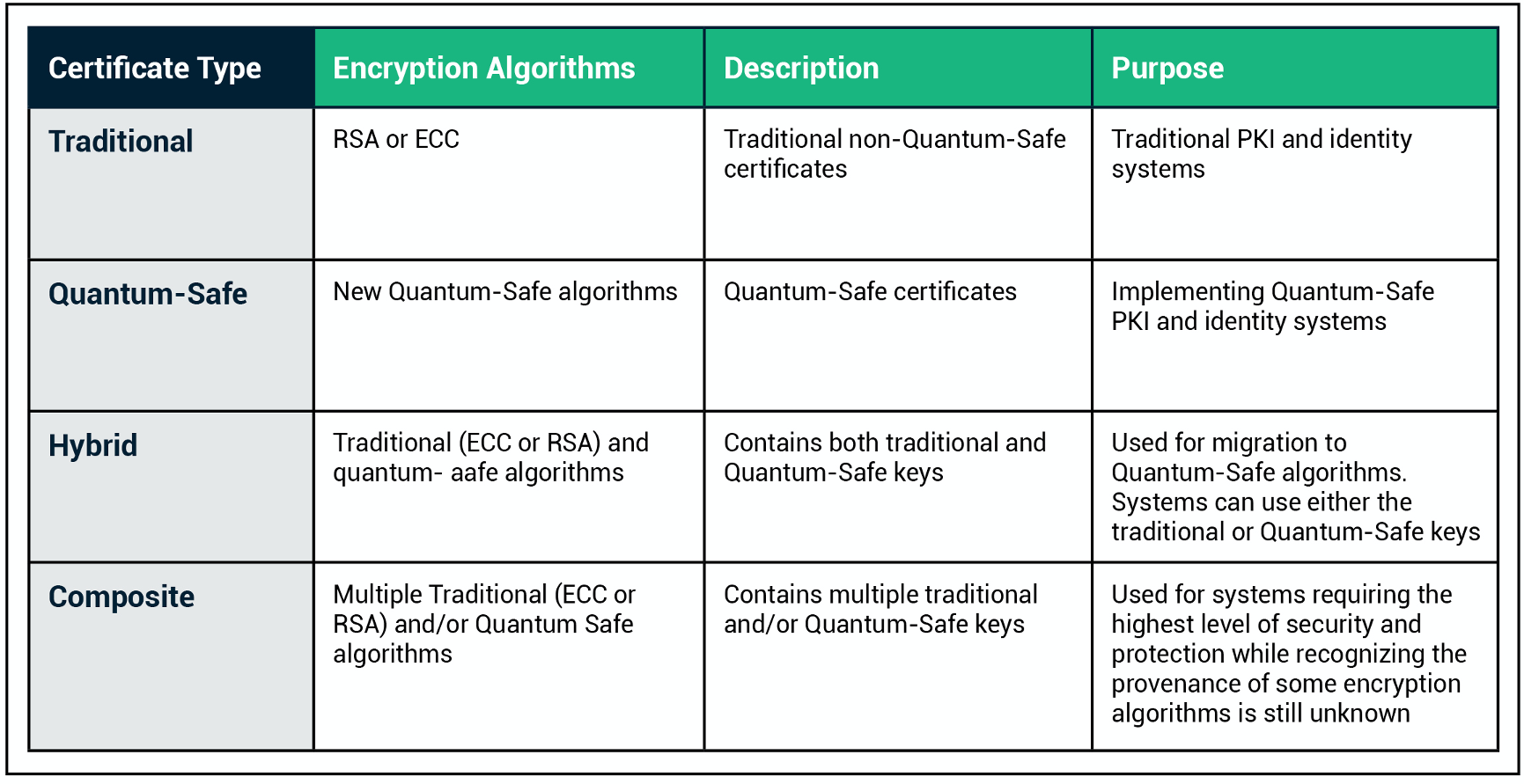
What Are Basic Cryptography Tools Coding Ninjas
Check more sample of What Is Attack In Cryptography And Network Security below
Cryptography And Network Security Scaler Topics

What Is Data Encryption Types And Best Practices
Post Quantum Cryptography A Look At How To Withstand Quantum Computer
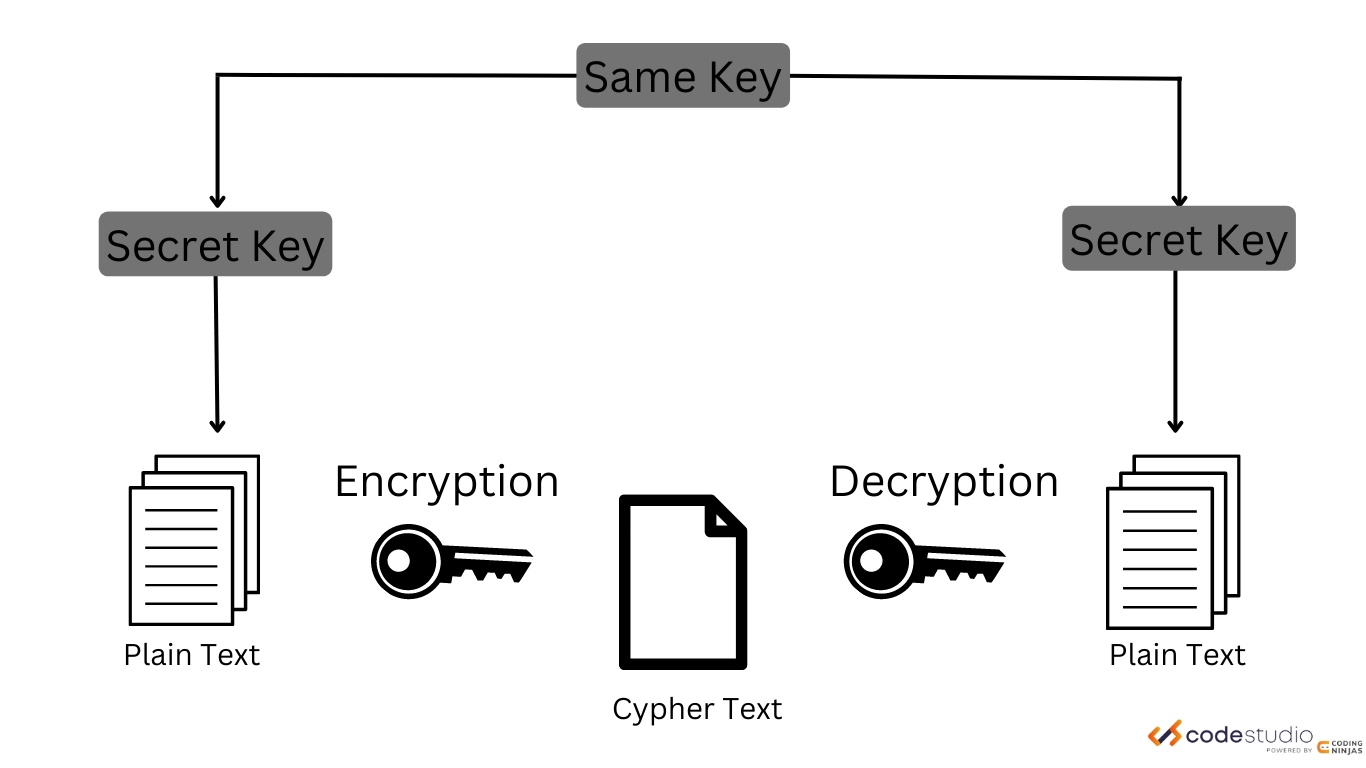
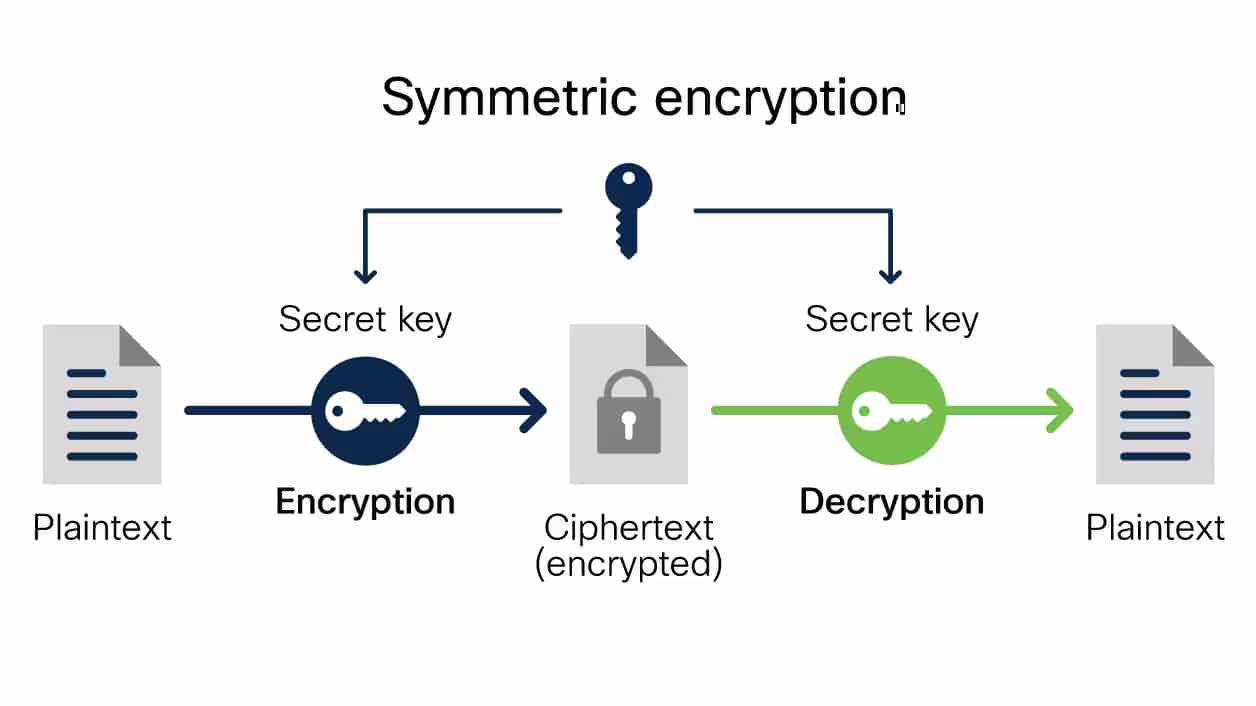
What Is Symmetric Key Cryptography Encryption Security Wiki

O Que Criptografia E Como Isso Afeta Voc Diariamente TecMundo
The History Of Cryptography DigiCert


ai ai
25 TB 14 16 Ultra 200H AI 300

What Is Symmetric Key Cryptography Encryption Security Wiki

What Is Data Encryption Types And Best Practices

O Que Criptografia E Como Isso Afeta Voc Diariamente TecMundo

The History Of Cryptography DigiCert

Cryptography In Blockchain Types Applications 2024 UpGrad Blog

2024 Complete Guide To SHA Encryption Types