In the digital age, when screens dominate our lives but the value of tangible printed objects hasn't waned. No matter whether it's for educational uses project ideas, artistic or simply adding personal touches to your home, printables for free have proven to be a valuable source. Through this post, we'll take a dive into the world "Types Of Attacks In Cryptography And Network Security," exploring what they are, where they can be found, and the ways that they can benefit different aspects of your daily life.
Get Latest Types Of Attacks In Cryptography And Network Security Below

Types Of Attacks In Cryptography And Network Security
Types Of Attacks In Cryptography And Network Security -
CSDN spring No Spring WebApplicationInitializer types detected on classpath spring No Spring
Types of things Here you re talking about a number of forms of a number of different categories Or you re talking about the things plural first and foremost and types is a
Types Of Attacks In Cryptography And Network Security offer a wide assortment of printable, downloadable items that are available online at no cost. They are available in numerous forms, including worksheets, coloring pages, templates and much more. The value of Types Of Attacks In Cryptography And Network Security lies in their versatility as well as accessibility.
More of Types Of Attacks In Cryptography And Network Security
What Is Quantum Cryptography And How It Works Sectigo Official
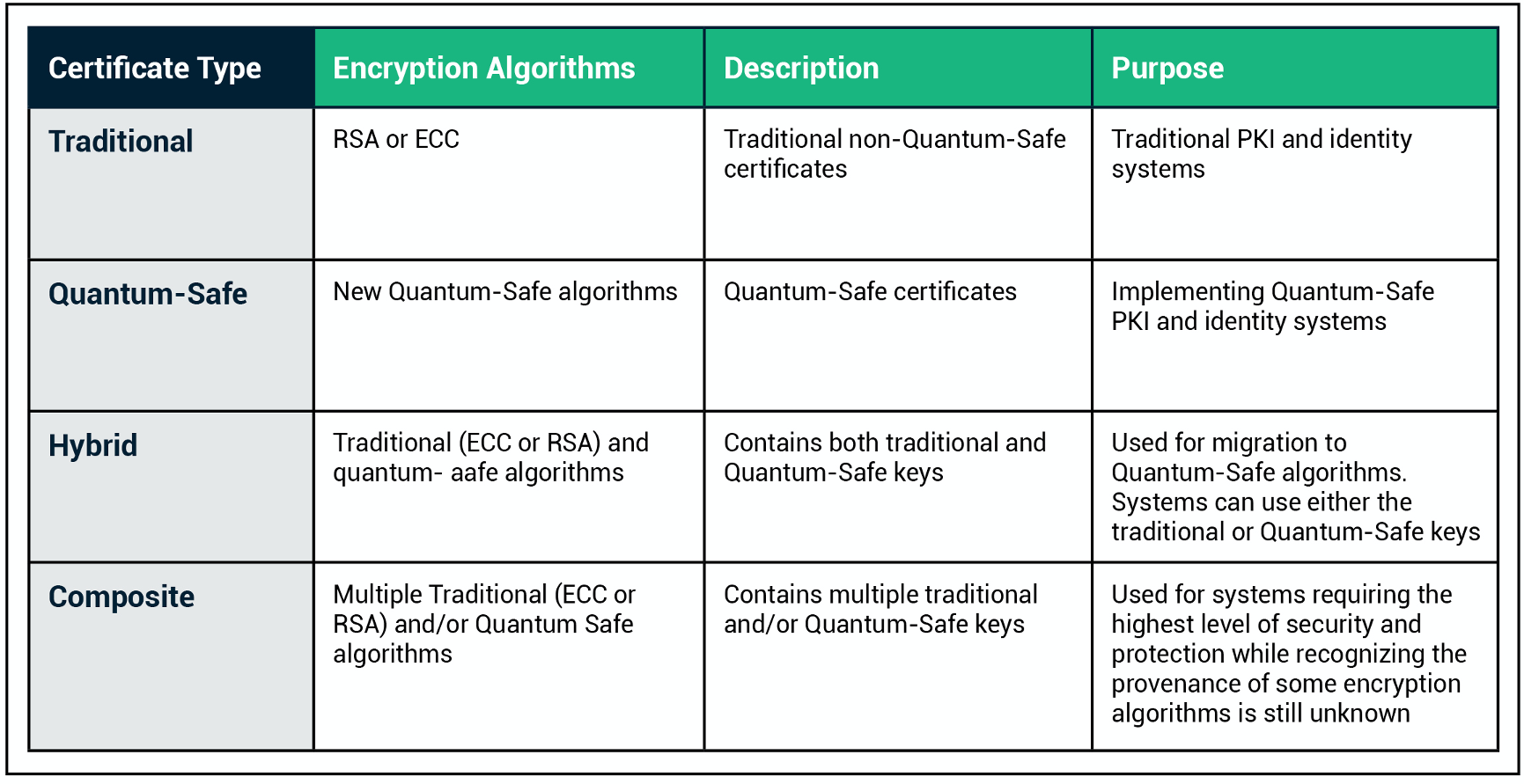
What Is Quantum Cryptography And How It Works Sectigo Official
I ve been digging through our English language as I am studying predicate logic I won t go into what that is accept for that it involves the use of variables much like maths
In addition to the ABO and Rh types are many more types which aren t contained in groups such as H or Bobmay antigen and Le Lewis types In the article about the
Print-friendly freebies have gained tremendous recognition for a variety of compelling motives:
-
Cost-Effective: They eliminate the requirement of buying physical copies or costly software.
-
Personalization Your HTML0 customization options allow you to customize the design to meet your needs be it designing invitations to organize your schedule or decorating your home.
-
Educational value: Printables for education that are free can be used by students of all ages. This makes them a vital device for teachers and parents.
-
Simple: Access to a plethora of designs and templates is time-saving and saves effort.
Where to Find more Types Of Attacks In Cryptography And Network Security
OSI Security Architecture Detailed Explanation InterviewBit
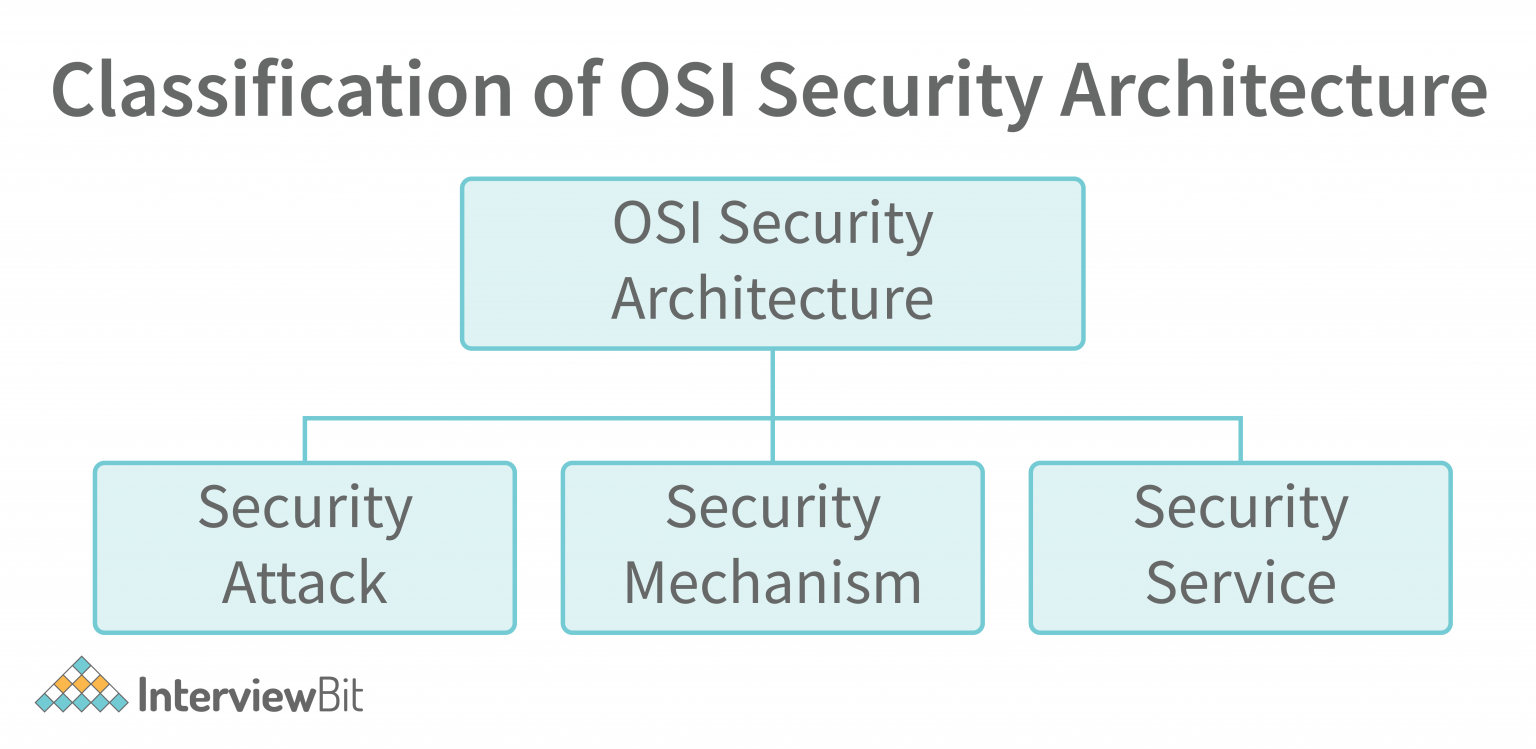
OSI Security Architecture Detailed Explanation InterviewBit
There are a few types of inherency Gap Inherency something is missing in the status quo that is required to solve the problems cited This meets the tests of inherency for
These kinds of dog multiple sub types of the type of animal known as dog these kinds of dogs multiple sub types of the multiple types of animal known as dog and not so
Now that we've ignited your interest in Types Of Attacks In Cryptography And Network Security Let's look into where you can discover these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy have a large selection with Types Of Attacks In Cryptography And Network Security for all motives.
- Explore categories like decorations for the home, education and management, and craft.
2. Educational Platforms
- Educational websites and forums often provide worksheets that can be printed for free as well as flashcards and other learning tools.
- It is ideal for teachers, parents as well as students who require additional sources.
3. Creative Blogs
- Many bloggers share their innovative designs and templates at no cost.
- These blogs cover a wide variety of topics, from DIY projects to party planning.
Maximizing Types Of Attacks In Cryptography And Network Security
Here are some new ways to make the most use of printables for free:
1. Home Decor
- Print and frame stunning artwork, quotes, as well as seasonal decorations, to embellish your living spaces.
2. Education
- Print worksheets that are free for reinforcement of learning at home (or in the learning environment).
3. Event Planning
- Design invitations and banners and decorations for special occasions like weddings or birthdays.
4. Organization
- Keep your calendars organized by printing printable calendars checklists for tasks, as well as meal planners.
Conclusion
Types Of Attacks In Cryptography And Network Security are an abundance of useful and creative resources for a variety of needs and passions. Their availability and versatility make them an essential part of any professional or personal life. Explore the many options of Types Of Attacks In Cryptography And Network Security right now and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are Types Of Attacks In Cryptography And Network Security really available for download?
- Yes, they are! You can download and print these items for free.
-
Can I use the free printouts for commercial usage?
- It's dependent on the particular usage guidelines. Always consult the author's guidelines before using their printables for commercial projects.
-
Do you have any copyright issues when you download printables that are free?
- Certain printables might have limitations on their use. Make sure you read the terms and conditions offered by the author.
-
How do I print printables for free?
- You can print them at home with printing equipment or visit a print shop in your area for premium prints.
-
What software do I require to open printables at no cost?
- The majority are printed in the PDF format, and can be opened using free software, such as Adobe Reader.
Cryptography And Network Security Scaler Topics

What Is Cryptography It s Types Algorithms And Features
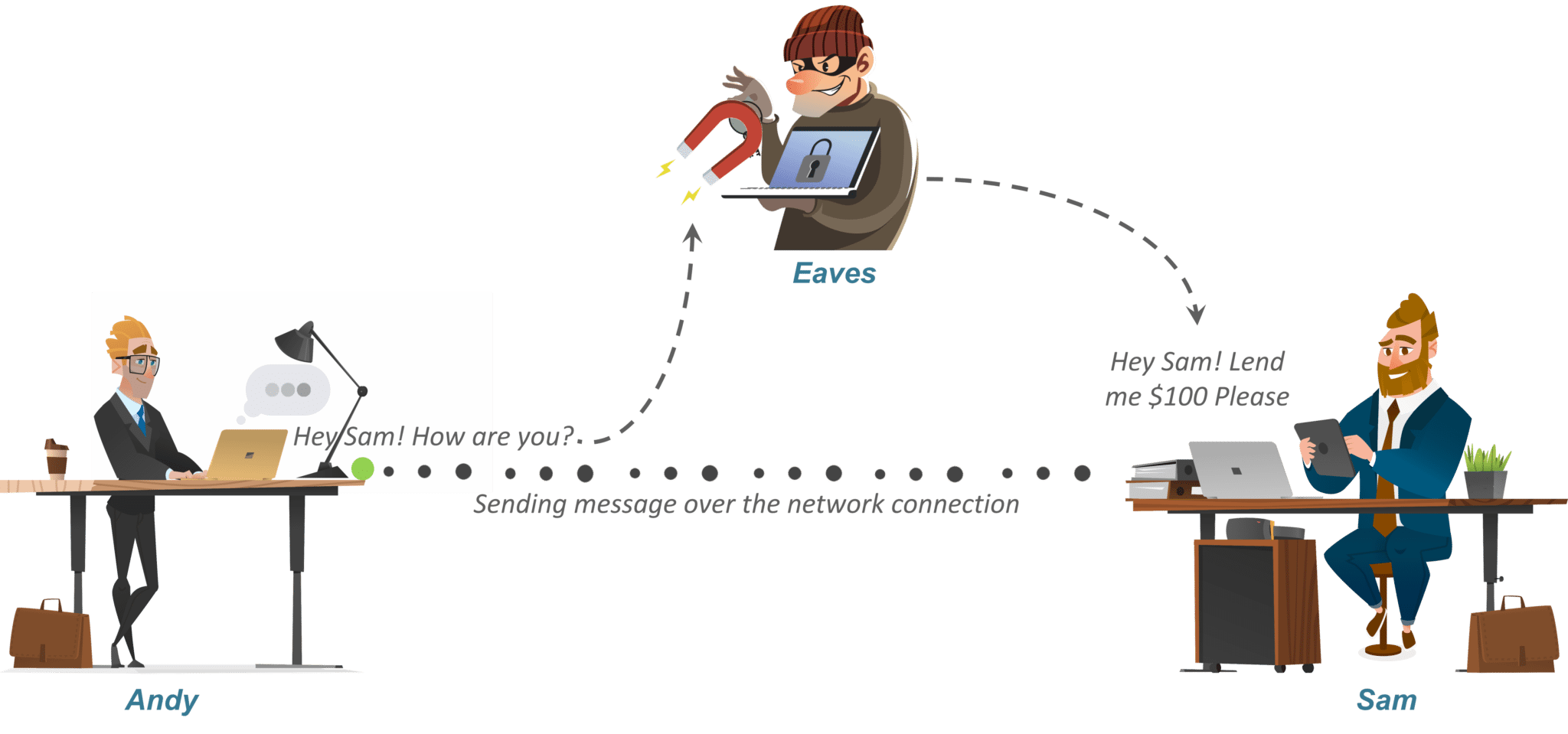
Check more sample of Types Of Attacks In Cryptography And Network Security below
Post Quantum Cryptography A Look At How To Withstand Quantum Computer
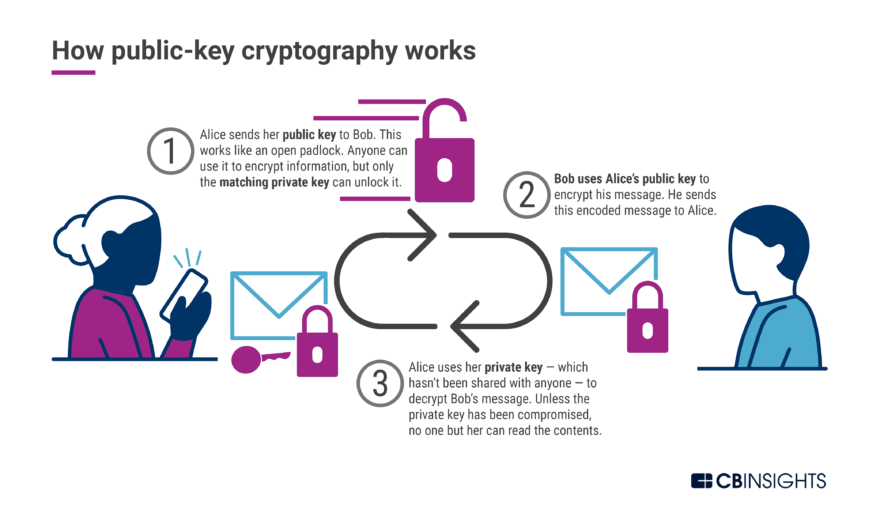
Cryptography Attacks 6 Types And Prevention Measures

What Is The Difference Between Encryption And Tokenization Which Is
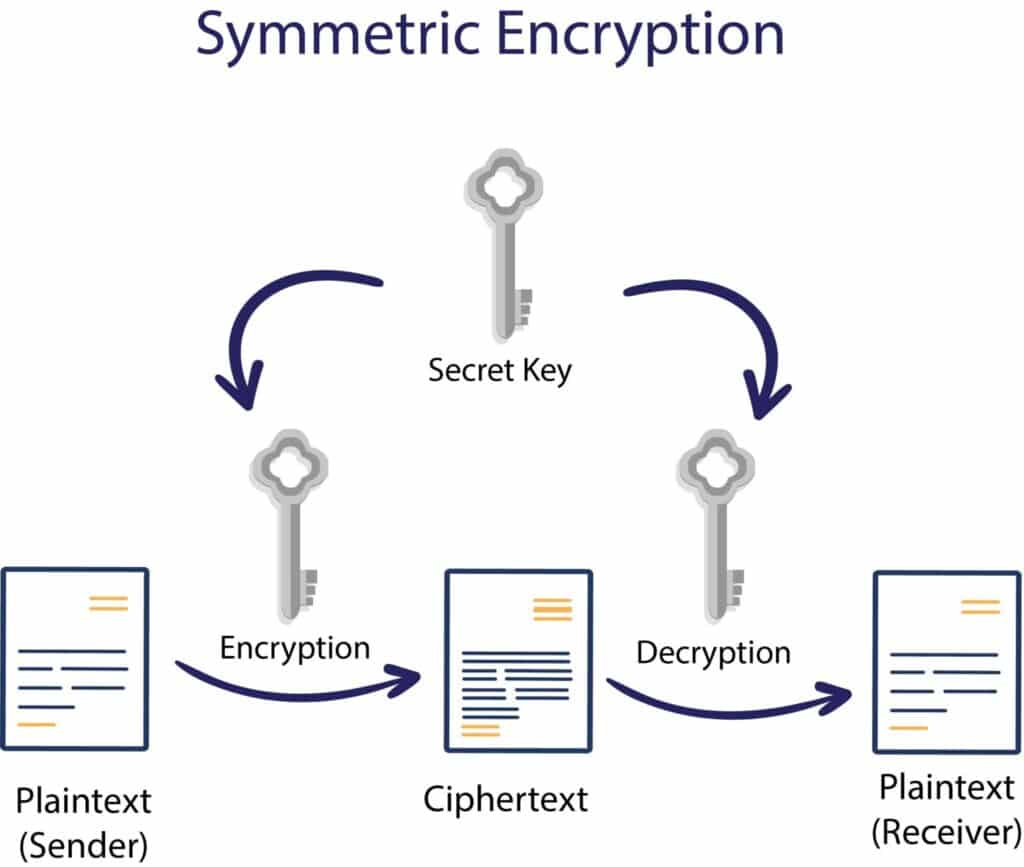
Security Attacks GATE Notes

Cryptography In Blockchain Types Applications 2024 UpGrad Blog

What Is Phishing Attack In Cyber Security Complete Guide

https://english.stackexchange.com › questions
Types of things Here you re talking about a number of forms of a number of different categories Or you re talking about the things plural first and foremost and types is a
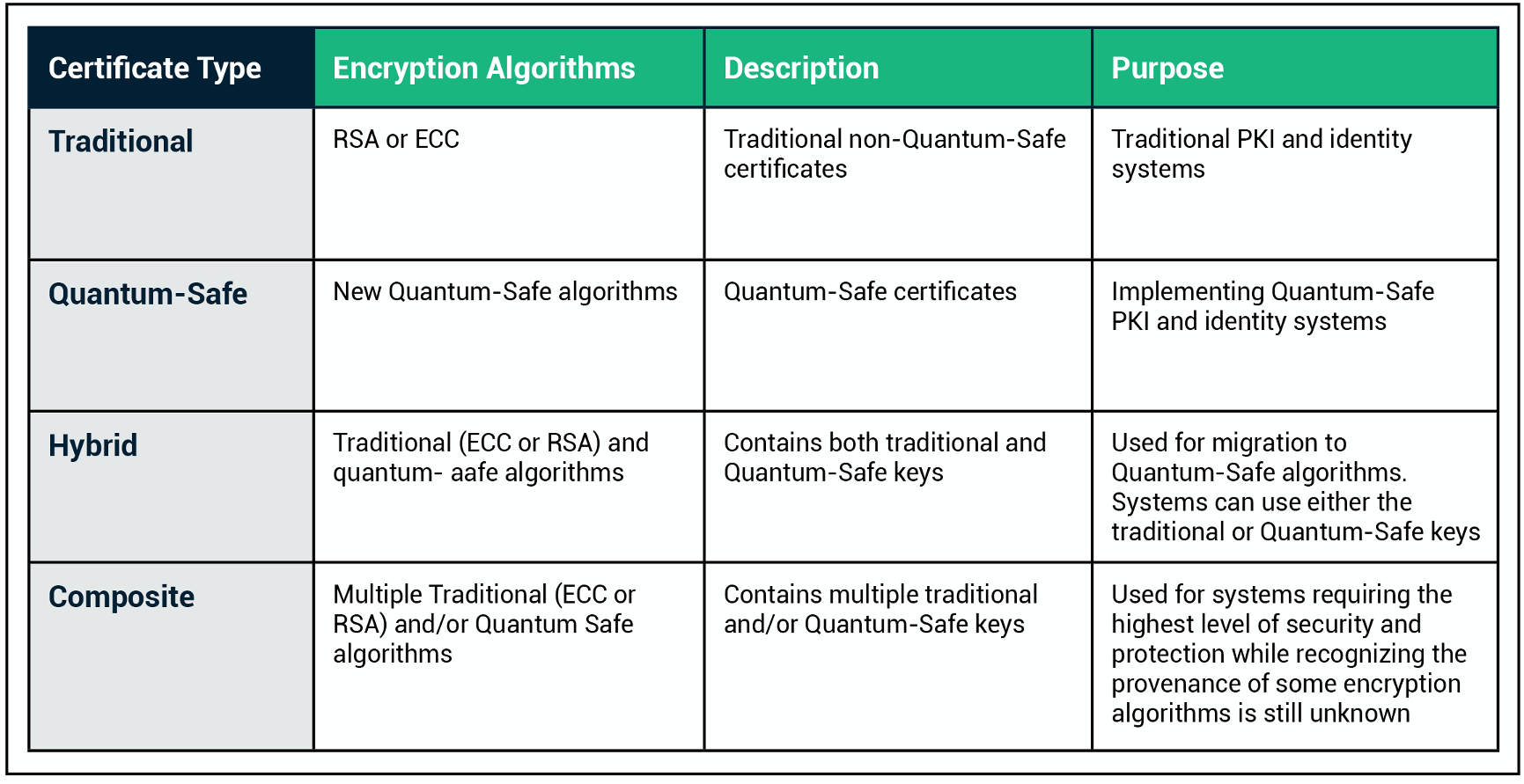
https://english.stackexchange.com › questions
Types of things vs types of thing When using the phrase types of or kinds of it often seems appropriate to follow with a singular noun e g types of rock but at other times a plural noun
Types of things Here you re talking about a number of forms of a number of different categories Or you re talking about the things plural first and foremost and types is a
Types of things vs types of thing When using the phrase types of or kinds of it often seems appropriate to follow with a singular noun e g types of rock but at other times a plural noun

Security Attacks GATE Notes

Cryptography Attacks 6 Types And Prevention Measures

Cryptography In Blockchain Types Applications 2024 UpGrad Blog
What Is Phishing Attack In Cyber Security Complete Guide
2024 Complete Guide To SHA Encryption Types

Asymmetric Vs Symmetric Encryption Definitions Differences Hashed

Asymmetric Vs Symmetric Encryption Definitions Differences Hashed
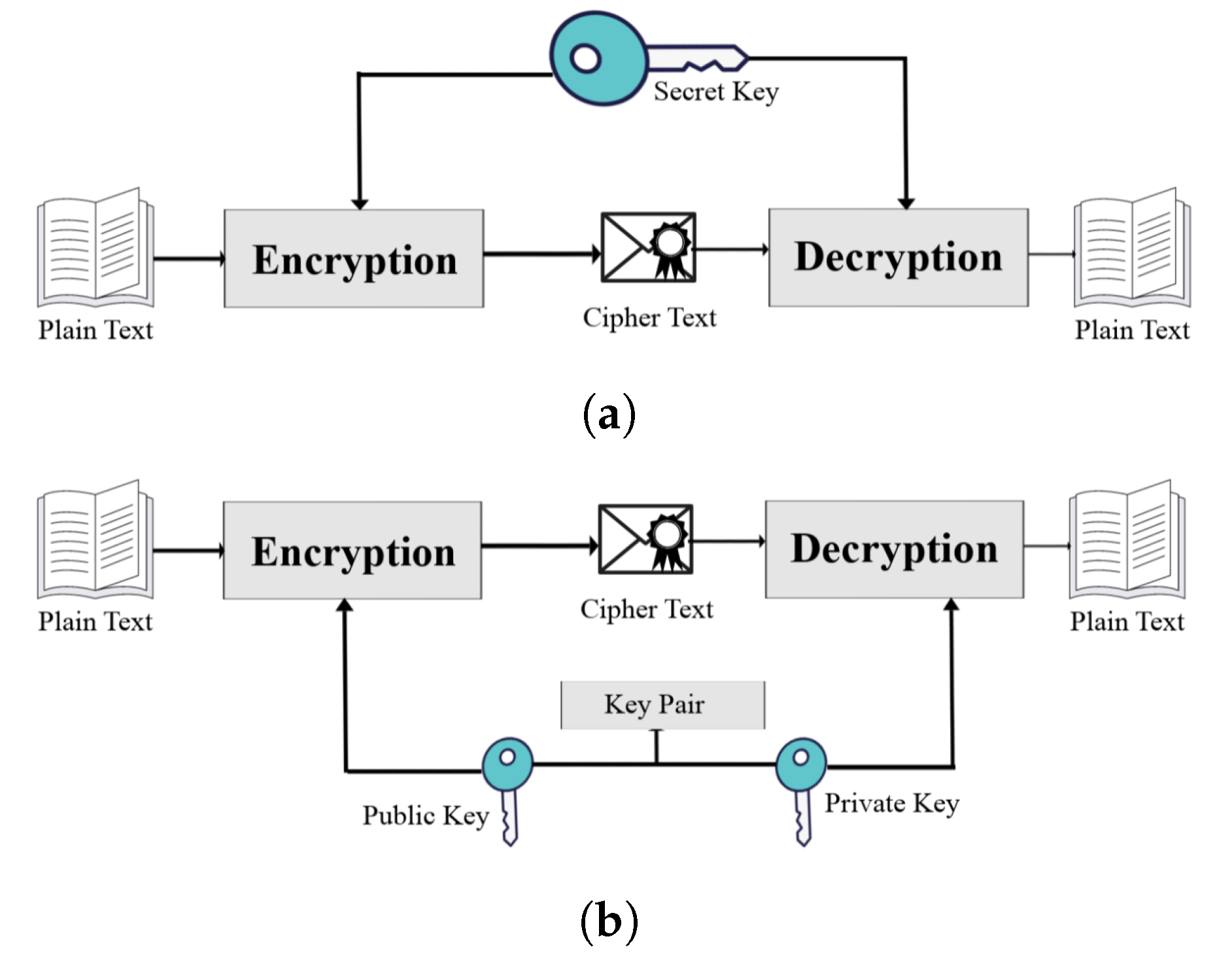
Sensors Free Full Text Resilience Optimization Of Post Quantum