In this age of technology, when screens dominate our lives and our lives are dominated by screens, the appeal of tangible printed objects hasn't waned. Be it for educational use and creative work, or simply adding some personal flair to your space, Security Attacks In Cryptography And Network Security Ppt are a great source. This article will take a dive through the vast world of "Security Attacks In Cryptography And Network Security Ppt," exploring the different types of printables, where to find them, and how they can enhance various aspects of your daily life.
Get Latest Security Attacks In Cryptography And Network Security Ppt Below

Security Attacks In Cryptography And Network Security Ppt
Security Attacks In Cryptography And Network Security Ppt -
Massive data breach exposes 184 million passwords for Google ZDNET
All the tech around us is collecting our personal data ZDNET s updated guide tells you everything you need to know about securing your online accounts and identity from
Security Attacks In Cryptography And Network Security Ppt cover a large selection of printable and downloadable materials online, at no cost. They are available in numerous forms, like worksheets coloring pages, templates and more. The attraction of printables that are free is their flexibility and accessibility.
More of Security Attacks In Cryptography And Network Security Ppt
IoT Security A Comprehensive Guide

IoT Security A Comprehensive Guide
Last year s cybersecurity predictions focused heavily on AI and its impact on how security teams will operate in the future This year s predictions also emphasize AI showing
API security is a subset of application security that prioritizes securing individual endpoints and managing access with fine grained permissions so that every data exchange is
Security Attacks In Cryptography And Network Security Ppt have garnered immense recognition for a variety of compelling motives:
-
Cost-Efficiency: They eliminate the necessity to purchase physical copies or expensive software.
-
customization: Your HTML0 customization options allow you to customize printing templates to your own specific requirements whether it's making invitations as well as organizing your calendar, or even decorating your house.
-
Educational Benefits: Education-related printables at no charge can be used by students of all ages, which makes these printables a powerful instrument for parents and teachers.
-
Convenience: instant access the vast array of design and templates reduces time and effort.
Where to Find more Security Attacks In Cryptography And Network Security Ppt
Cryptography And Network Security Scaler Topics

Cryptography And Network Security Scaler Topics
Chief information security officers CISOs who oversee information security efforts have become a fixture of corporate C suites Demand is rising for information security analysts
Even limited security might provide significant cost savings Those with limited AI security reported an average data breach cost of USD 4 04 million USD 400 000 less than
We've now piqued your interest in printables for free Let's look into where you can find these treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a large collection of Security Attacks In Cryptography And Network Security Ppt designed for a variety needs.
- Explore categories such as interior decor, education, organizing, and crafts.
2. Educational Platforms
- Educational websites and forums often offer worksheets with printables that are free as well as flashcards and other learning materials.
- Great for parents, teachers, and students seeking supplemental resources.
3. Creative Blogs
- Many bloggers offer their unique designs and templates free of charge.
- These blogs cover a broad array of topics, ranging everything from DIY projects to party planning.
Maximizing Security Attacks In Cryptography And Network Security Ppt
Here are some inventive ways ensure you get the very most use of printables for free:
1. Home Decor
- Print and frame stunning artwork, quotes, or even seasonal decorations to decorate your living spaces.
2. Education
- Use printable worksheets for free to enhance learning at home or in the classroom.
3. Event Planning
- Design invitations and banners and other decorations for special occasions like birthdays and weddings.
4. Organization
- Keep your calendars organized by printing printable calendars as well as to-do lists and meal planners.
Conclusion
Security Attacks In Cryptography And Network Security Ppt are a treasure trove of useful and creative resources catering to different needs and needs and. Their access and versatility makes these printables a useful addition to both personal and professional life. Explore the vast collection of Security Attacks In Cryptography And Network Security Ppt now and discover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables for free really are they free?
- Yes you can! You can download and print these materials for free.
-
Can I use the free printing templates for commercial purposes?
- It's dependent on the particular terms of use. Be sure to read the rules of the creator before utilizing their templates for commercial projects.
-
Do you have any copyright issues in Security Attacks In Cryptography And Network Security Ppt?
- Some printables may have restrictions on their use. You should read the terms and condition of use as provided by the designer.
-
How can I print Security Attacks In Cryptography And Network Security Ppt?
- Print them at home with an printer, or go to the local print shops for superior prints.
-
What software will I need to access printables that are free?
- Most PDF-based printables are available in the format PDF. This is open with no cost programs like Adobe Reader.
What Is Cryptography It s Types Algorithms And Features
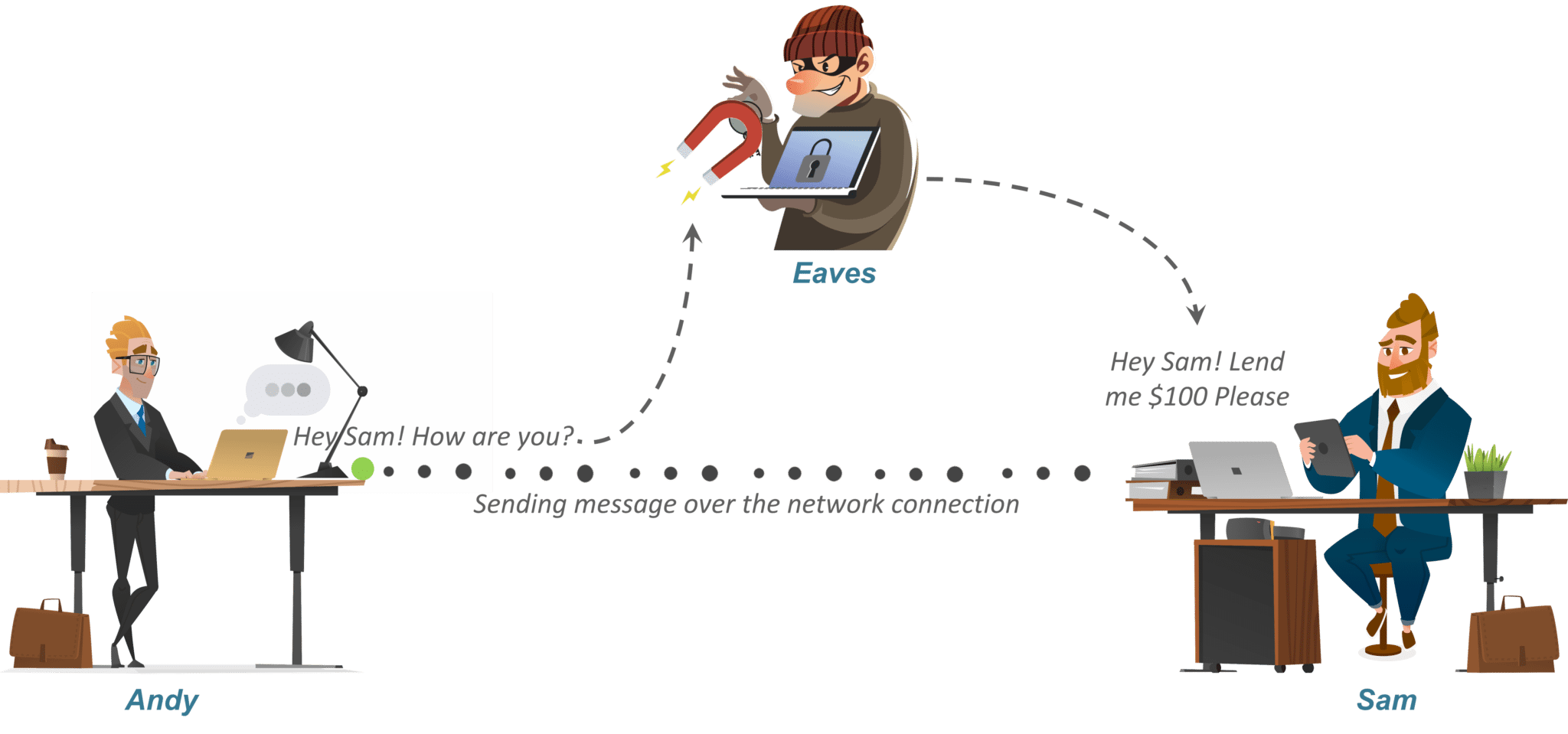
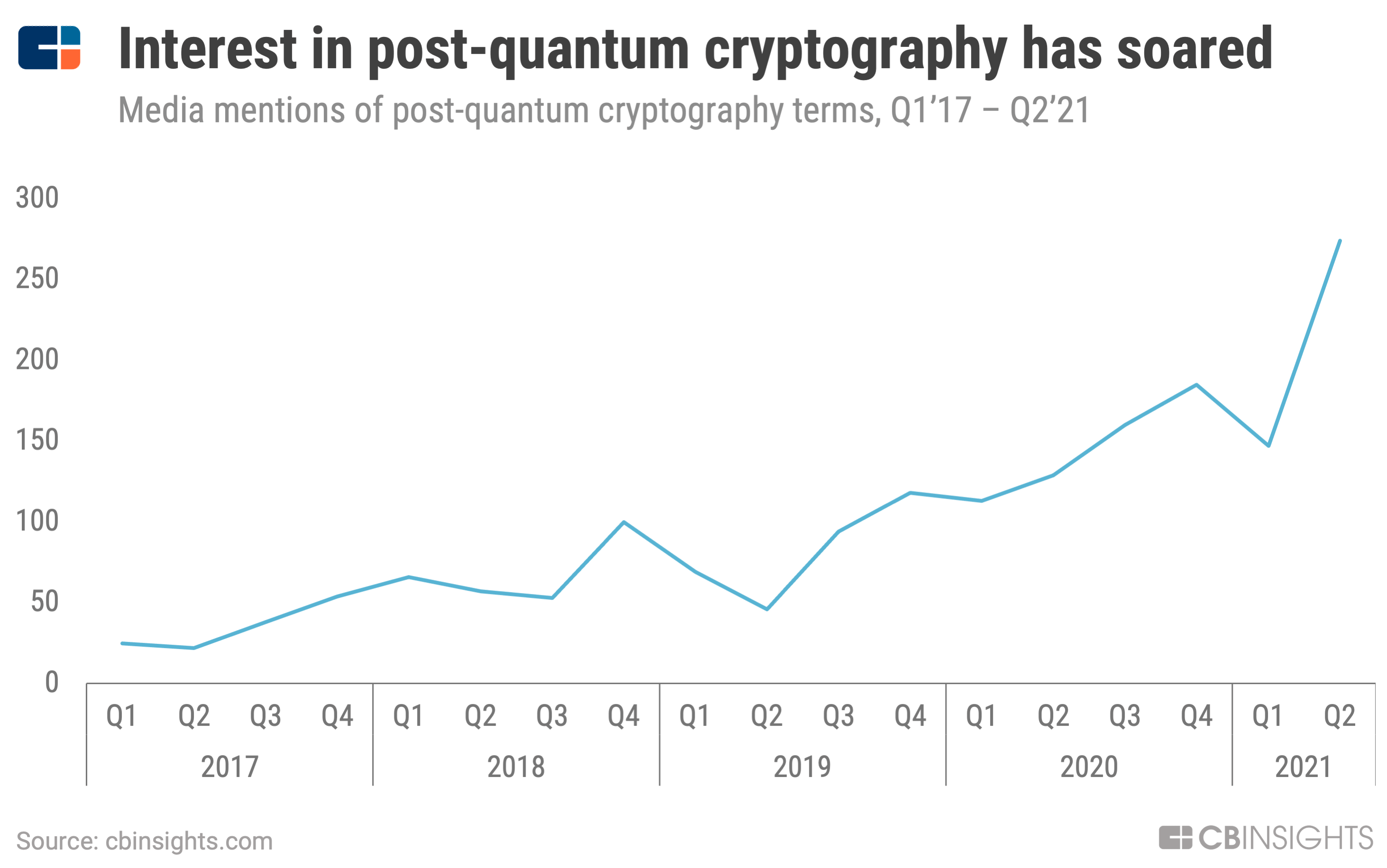
Post Quantum Cryptography A Look At How To Withstand Quantum Computer
Check more sample of Security Attacks In Cryptography And Network Security Ppt below
Post Quantum Cryptography A Look At How To Withstand Quantum Computer
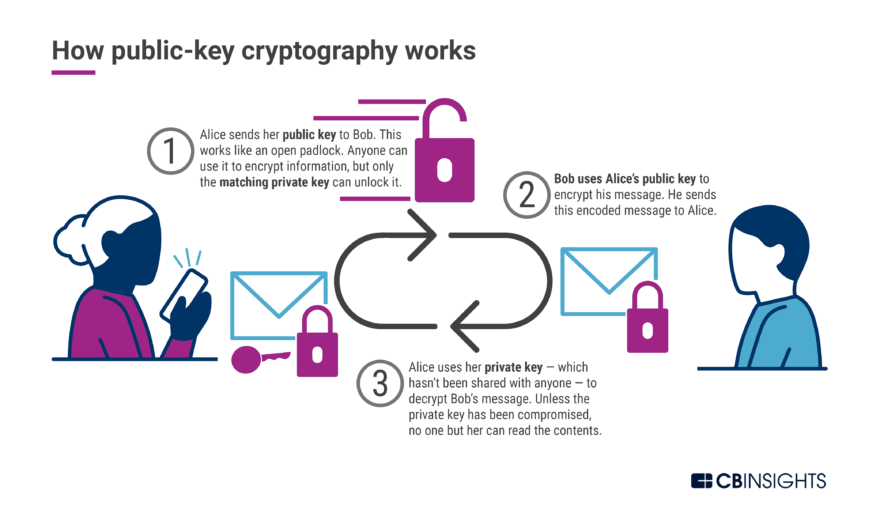
What Is Cryptography Cryptographic Algorithms Types Of

Cryptography Attacks 6 Types And Prevention Measures

Symmetric Encryption Algorithms Live Long Encrypt Hashed Out By

Active Passive Attacks Definition Differences Venafi
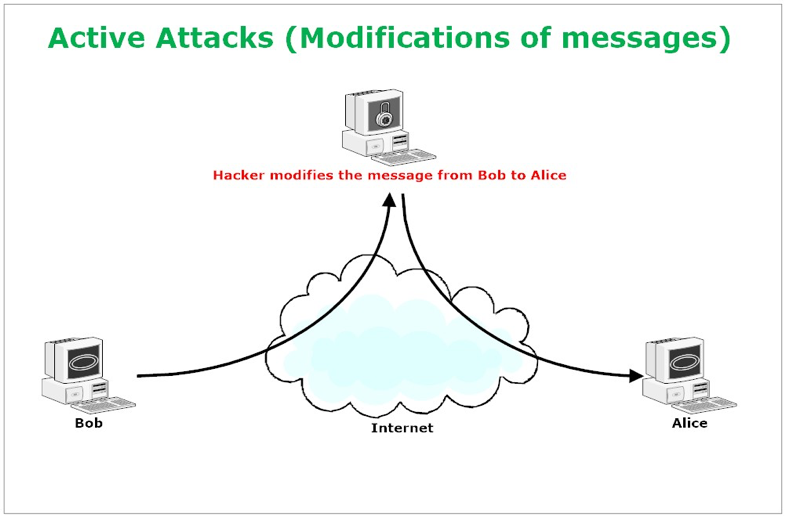
Cryptography And Network Security Principles And Practice 2 downloads

https://www.zdnet.com › article
All the tech around us is collecting our personal data ZDNET s updated guide tells you everything you need to know about securing your online accounts and identity from

https://www.ibm.com › think › topics › it-security
But IT security also includes physical security measures for example locks ID cards surveillance cameras required to protect buildings and devices that house data and IT
All the tech around us is collecting our personal data ZDNET s updated guide tells you everything you need to know about securing your online accounts and identity from
But IT security also includes physical security measures for example locks ID cards surveillance cameras required to protect buildings and devices that house data and IT

Symmetric Encryption Algorithms Live Long Encrypt Hashed Out By

What Is Cryptography Cryptographic Algorithms Types Of

Active Passive Attacks Definition Differences Venafi
Cryptography And Network Security Principles And Practice 2 downloads
2024 Complete Guide To SHA Encryption Types
7 Strategies For Enterprises To Combat Online Threats

7 Strategies For Enterprises To Combat Online Threats

Electronics Free Full Text A Review Of The NIST Lightweight