In this age of electronic devices, when screens dominate our lives, the charm of tangible printed objects hasn't waned. If it's to aid in education or creative projects, or simply adding personal touches to your area, Cryptographic Attacks In Cryptography And Network Security are now an essential source. This article will dive in the world of "Cryptographic Attacks In Cryptography And Network Security," exploring what they are, where to find them, and how they can be used to enhance different aspects of your life.
Get Latest Cryptographic Attacks In Cryptography And Network Security Below
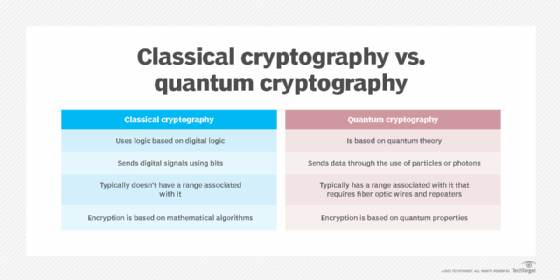
Cryptographic Attacks In Cryptography And Network Security
Cryptographic Attacks In Cryptography And Network Security -
Cryptographic Services 1 5 5 6
Microsoft base Cryptographic Provider v1 0 1 IE6 0sp1 IE
Printables for free include a vast array of printable content that can be downloaded from the internet at no cost. They are available in numerous kinds, including worksheets templates, coloring pages, and more. One of the advantages of Cryptographic Attacks In Cryptography And Network Security lies in their versatility as well as accessibility.
More of Cryptographic Attacks In Cryptography And Network Security
Concept Of Cryptography In Blockchain

Concept Of Cryptography In Blockchain
svchost exe Metasploit Meterpreter run metsvc
owf prf prg
Printables for free have gained immense popularity due to numerous compelling reasons:
-
Cost-Effective: They eliminate the requirement of buying physical copies or expensive software.
-
Personalization It is possible to tailor the design to meet your needs be it designing invitations as well as organizing your calendar, or even decorating your home.
-
Educational Value: The free educational worksheets cater to learners of all ages, making them an essential tool for parents and educators.
-
It's easy: Access to a myriad of designs as well as templates, which saves time as well as effort.
Where to Find more Cryptographic Attacks In Cryptography And Network Security
What Is Quantum Cryptography And How It Works Sectigo Official
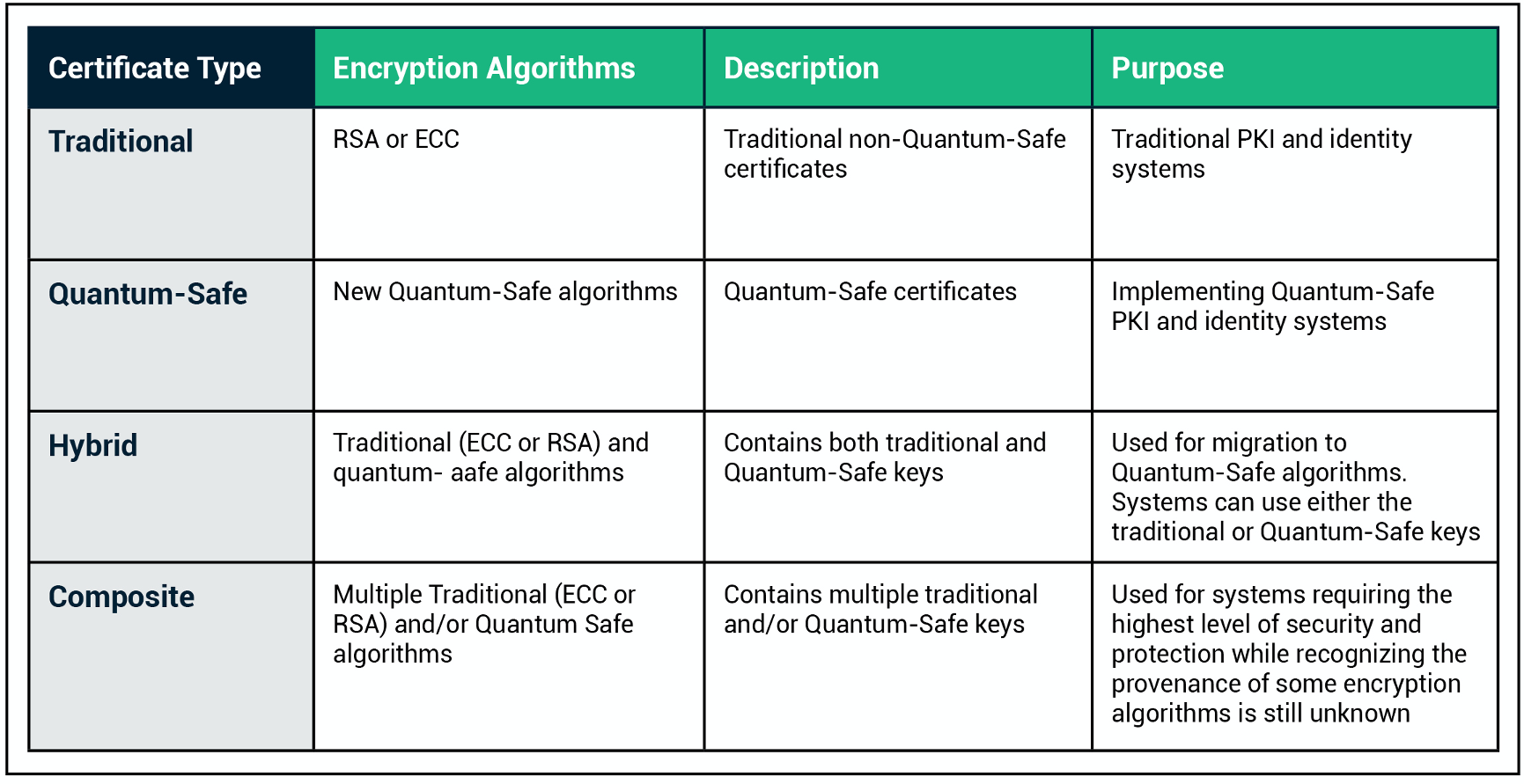
What Is Quantum Cryptography And How It Works Sectigo Official
3 Transactions on Cryptographic Hardware and Embedded Systems IACR CHES 2018 TCHES 4 Communications
Win10 chrome CryptographicServices 5 15 cpu
Since we've got your curiosity about Cryptographic Attacks In Cryptography And Network Security we'll explore the places you can discover these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide an extensive selection of printables that are free for a variety of goals.
- Explore categories like design, home decor, organisation, as well as crafts.
2. Educational Platforms
- Educational websites and forums usually provide worksheets that can be printed for free as well as flashcards and other learning tools.
- Ideal for parents, teachers, and students seeking supplemental sources.
3. Creative Blogs
- Many bloggers post their original designs and templates for free.
- These blogs cover a broad selection of subjects, including DIY projects to planning a party.
Maximizing Cryptographic Attacks In Cryptography And Network Security
Here are some innovative ways create the maximum value of printables for free:
1. Home Decor
- Print and frame stunning art, quotes, or seasonal decorations that will adorn your living spaces.
2. Education
- Use free printable worksheets to reinforce learning at home or in the classroom.
3. Event Planning
- Design invitations for banners, invitations as well as decorations for special occasions such as weddings, birthdays, and other special occasions.
4. Organization
- Be organized by using printable calendars, to-do lists, and meal planners.
Conclusion
Cryptographic Attacks In Cryptography And Network Security are an abundance of innovative and useful resources that meet a variety of needs and pursuits. Their availability and versatility make them a great addition to both professional and personal life. Explore the endless world of Cryptographic Attacks In Cryptography And Network Security and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables available for download really are they free?
- Yes you can! You can print and download these free resources for no cost.
-
Can I make use of free printing templates for commercial purposes?
- It's all dependent on the conditions of use. Always review the terms of use for the creator prior to using the printables in commercial projects.
-
Are there any copyright issues with Cryptographic Attacks In Cryptography And Network Security?
- Some printables may have restrictions on their use. Always read these terms and conditions as set out by the creator.
-
How do I print Cryptographic Attacks In Cryptography And Network Security?
- You can print them at home with either a printer or go to a local print shop for more high-quality prints.
-
What program do I need in order to open printables at no cost?
- The majority of printables are as PDF files, which can be opened using free software like Adobe Reader.
Cryptography And Network Security Scaler Topics

What Is Cryptography In Security Types Of Cryptography
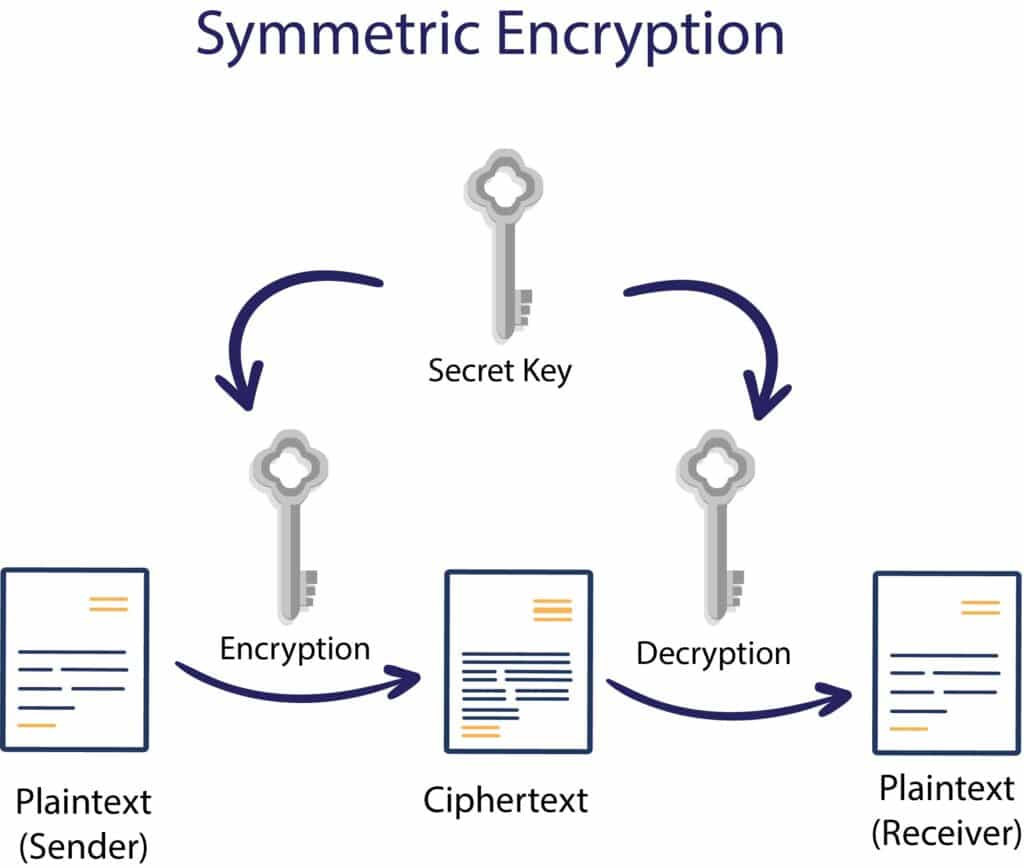
Check more sample of Cryptographic Attacks In Cryptography And Network Security below
What Is Cryptography It s Types Algorithms And Features
Post Quantum Cryptography A Look At How To Withstand Quantum Computer
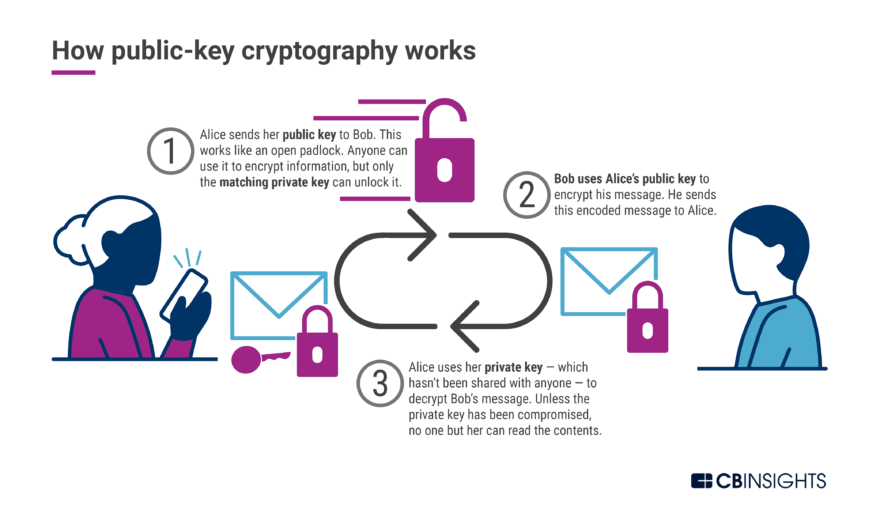
Cryptography Attacks 6 Types And Prevention Measures

Cryptography Demystified Protecting Your Digital Privacy
Cryptography Demystified Protecting Your Digital Privacy
Cryptography In Blockchain Types Applications 2024 UpGrad Blog

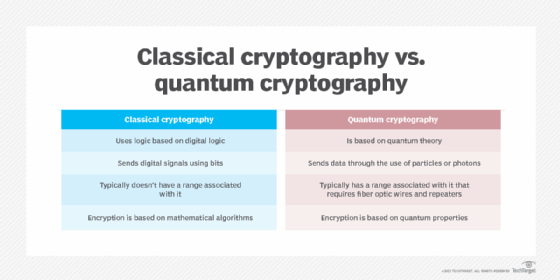
https://zhidao.baidu.com › question
Microsoft base Cryptographic Provider v1 0 1 IE6 0sp1 IE

https://zhidao.baidu.com › question
Cryptographic Services Cryptsvc sreng2 Cryptographic Services Cryptsvc System Repair Engineer
Microsoft base Cryptographic Provider v1 0 1 IE6 0sp1 IE
Cryptographic Services Cryptsvc sreng2 Cryptographic Services Cryptsvc System Repair Engineer
Cryptography Demystified Protecting Your Digital Privacy

Post Quantum Cryptography A Look At How To Withstand Quantum Computer
Cryptography Demystified Protecting Your Digital Privacy

Cryptography In Blockchain Types Applications 2024 UpGrad Blog
2024 Complete Guide To SHA Encryption Types

Asymmetric Vs Symmetric Encryption Definitions Differences Hashed

Asymmetric Vs Symmetric Encryption Definitions Differences Hashed

RSA Algorithm In Cryptography Rivest Shamir Adleman Explained Splunk