Today, where screens have become the dominant feature of our lives yet the appeal of tangible printed products hasn't decreased. Whether it's for educational purposes in creative or artistic projects, or just adding a personal touch to your home, printables for free are now a useful source. The following article is a take a dive in the world of "What Is Cryptographic Attack In Cyber Security," exploring what they are, where they are, and how they can be used to enhance different aspects of your lives.
Get Latest What Is Cryptographic Attack In Cyber Security Below
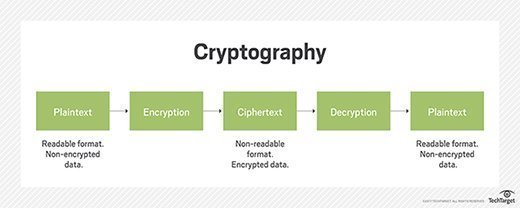
What Is Cryptographic Attack In Cyber Security
What Is Cryptographic Attack In Cyber Security -
owf prf prg
Cryptographic services gt Cryptographic Services gt
What Is Cryptographic Attack In Cyber Security provide a diverse array of printable items that are available online at no cost. They are available in numerous types, such as worksheets templates, coloring pages and much more. The great thing about What Is Cryptographic Attack In Cyber Security is in their variety and accessibility.
More of What Is Cryptographic Attack In Cyber Security
Protecting Cryptographic Keys Used To Secure Data Singapore
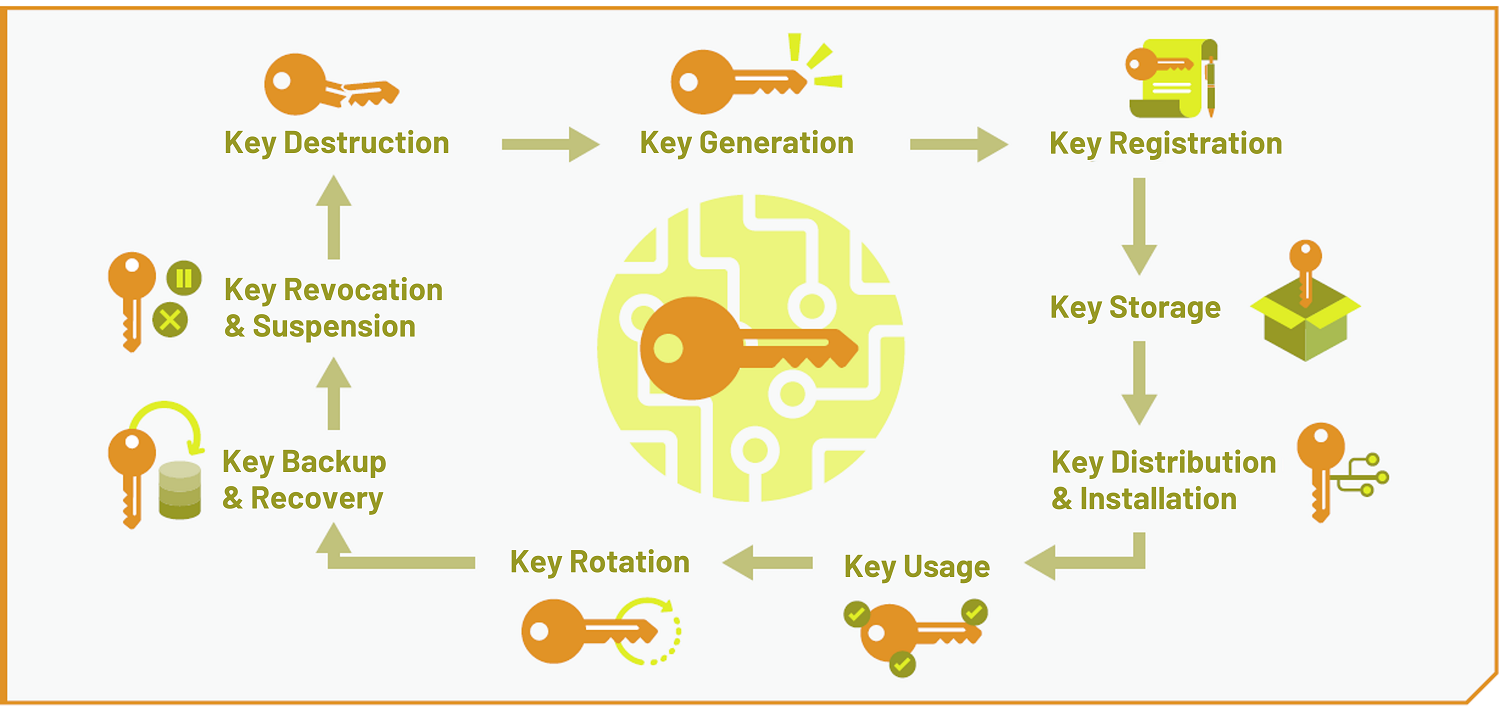
Protecting Cryptographic Keys Used To Secure Data Singapore
EDA ISSCC DAC 5 3 1 Symposium on VLSI Circuits VLSI C 2 Custom Integrated
2011 1
What Is Cryptographic Attack In Cyber Security have garnered immense popularity due to a myriad of compelling factors:
-
Cost-Efficiency: They eliminate the need to buy physical copies or costly software.
-
Flexible: The Customization feature lets you tailor the design to meet your needs whether it's making invitations or arranging your schedule or decorating your home.
-
Education Value Education-related printables at no charge can be used by students of all ages. This makes them a valuable instrument for parents and teachers.
-
Accessibility: Fast access an array of designs and templates is time-saving and saves effort.
Where to Find more What Is Cryptographic Attack In Cyber Security
What Are Cryptographic Protocols Coding Ninjas

What Are Cryptographic Protocols Coding Ninjas
[desc-9]
[desc-7]
We hope we've stimulated your curiosity about What Is Cryptographic Attack In Cyber Security Let's take a look at where you can locate these hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a wide selection and What Is Cryptographic Attack In Cyber Security for a variety goals.
- Explore categories like design, home decor, organization, and crafts.
2. Educational Platforms
- Educational websites and forums often offer free worksheets and worksheets for printing as well as flashcards and other learning tools.
- Perfect for teachers, parents as well as students who require additional resources.
3. Creative Blogs
- Many bloggers share their imaginative designs with templates and designs for free.
- These blogs cover a wide range of topics, ranging from DIY projects to planning a party.
Maximizing What Is Cryptographic Attack In Cyber Security
Here are some inventive ways how you could make the most use of printables that are free:
1. Home Decor
- Print and frame beautiful art, quotes, or other seasonal decorations to fill your living spaces.
2. Education
- Print free worksheets for teaching at-home also in the classes.
3. Event Planning
- Create invitations, banners, and other decorations for special occasions like weddings and birthdays.
4. Organization
- Be organized by using printable calendars checklists for tasks, as well as meal planners.
Conclusion
What Is Cryptographic Attack In Cyber Security are an abundance of fun and practical tools which cater to a wide range of needs and needs and. Their availability and versatility make them a fantastic addition to every aspect of your life, both professional and personal. Explore the vast array of What Is Cryptographic Attack In Cyber Security right now and discover new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free free?
- Yes they are! You can download and print these materials for free.
-
Can I make use of free templates for commercial use?
- It's dependent on the particular rules of usage. Make sure you read the guidelines for the creator before utilizing printables for commercial projects.
-
Are there any copyright violations with printables that are free?
- Certain printables could be restricted regarding their use. Always read the terms and conditions set forth by the author.
-
How do I print What Is Cryptographic Attack In Cyber Security?
- Print them at home using a printer or visit any local print store for better quality prints.
-
What program do I require to open printables at no cost?
- The majority of printed documents are with PDF formats, which is open with no cost software, such as Adobe Reader.
New Attack Against SSL Threatens Secure Connections

Cryptographic Authentication And Key Exchange Security Assurance
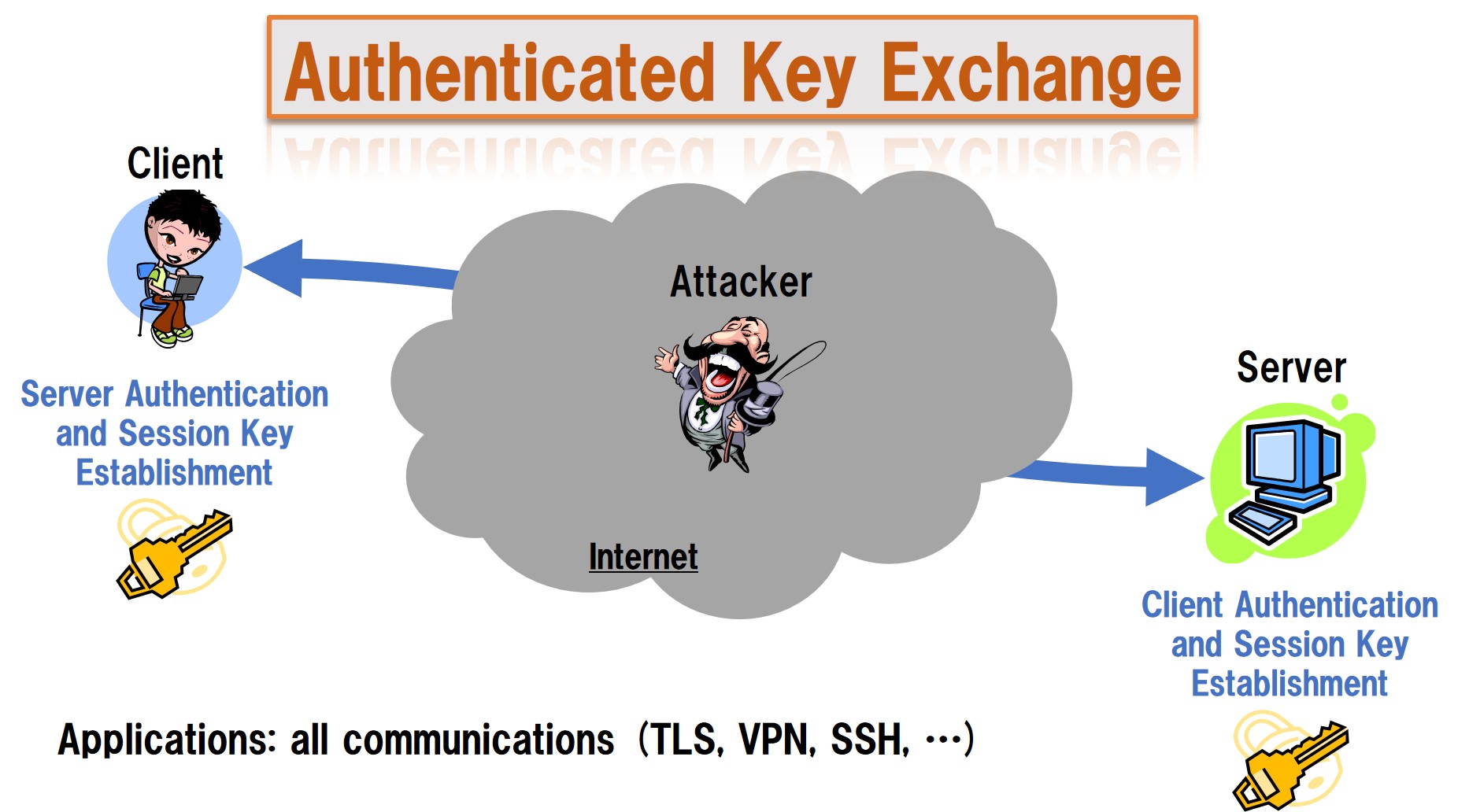
Check more sample of What Is Cryptographic Attack In Cyber Security below
Cryptography And Network Security Scaler Topics

What Is A Hardware Security Module
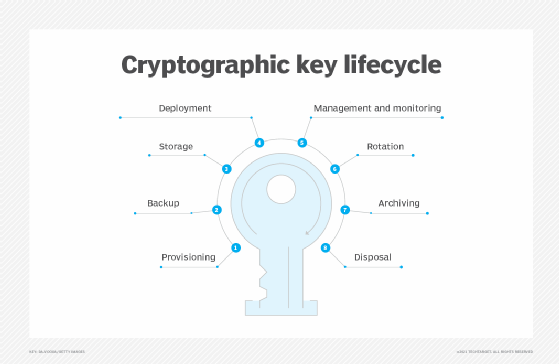
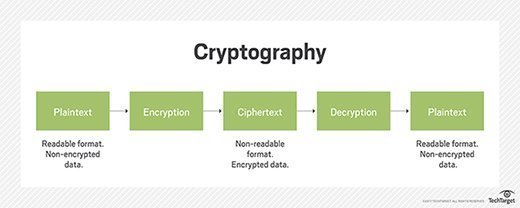
What Is Cryptography Cryptographic Algorithms Types Of
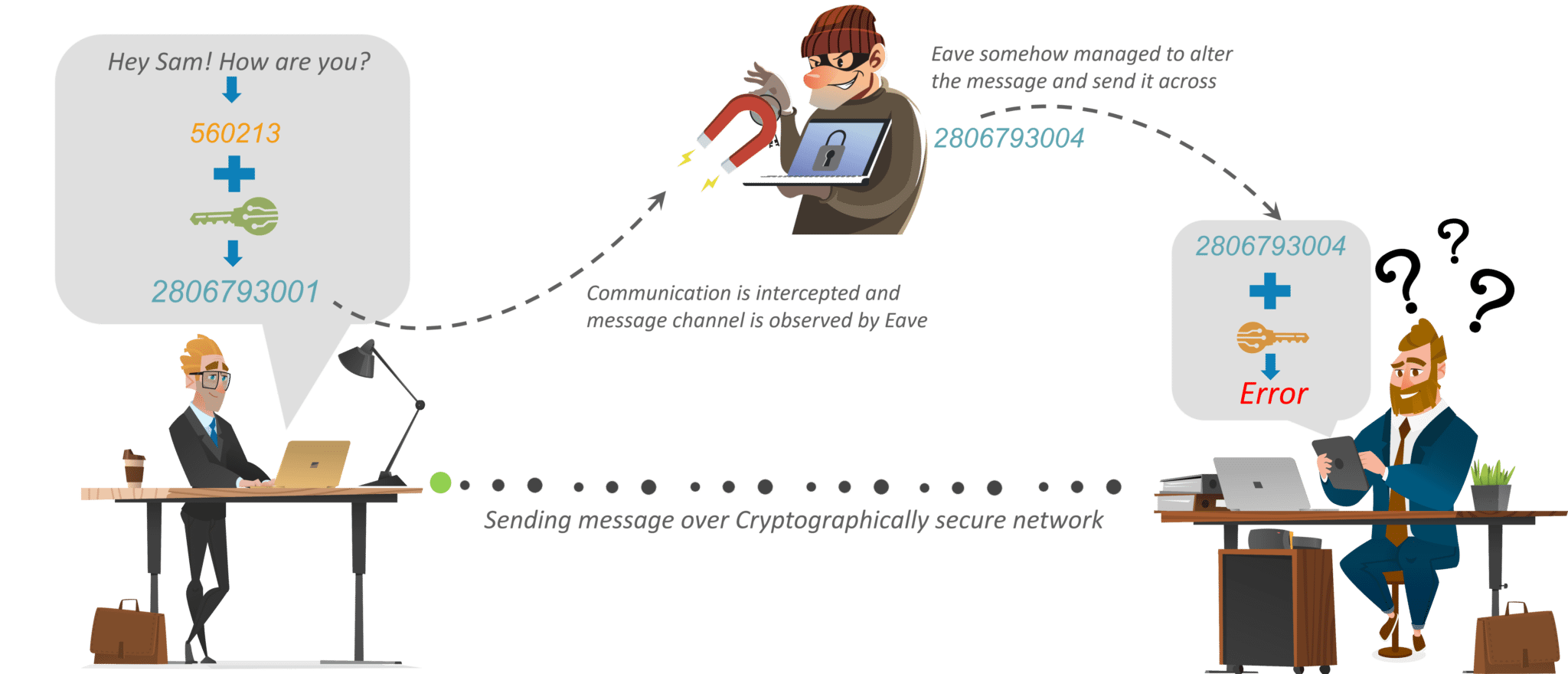
What Is Cryptography Cryptographic Algorithms Types Of

What Is A Cryptographic Key Keys And SSL Encryption Cloudflare
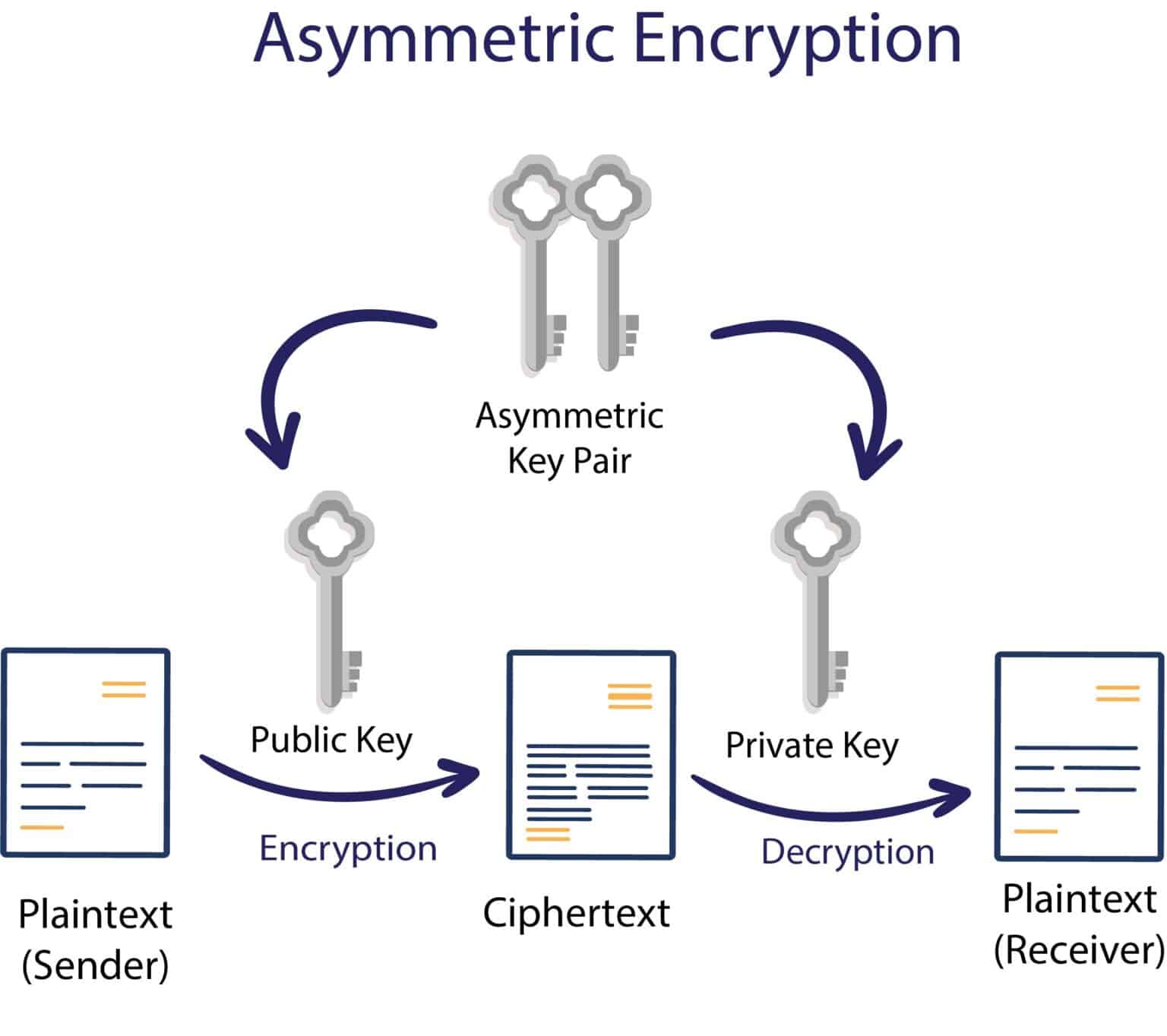
What Is The Difference Between Symmetric And Asymmetric Encryption
https://zhidao.baidu.com › question
Cryptographic services gt Cryptographic Services gt
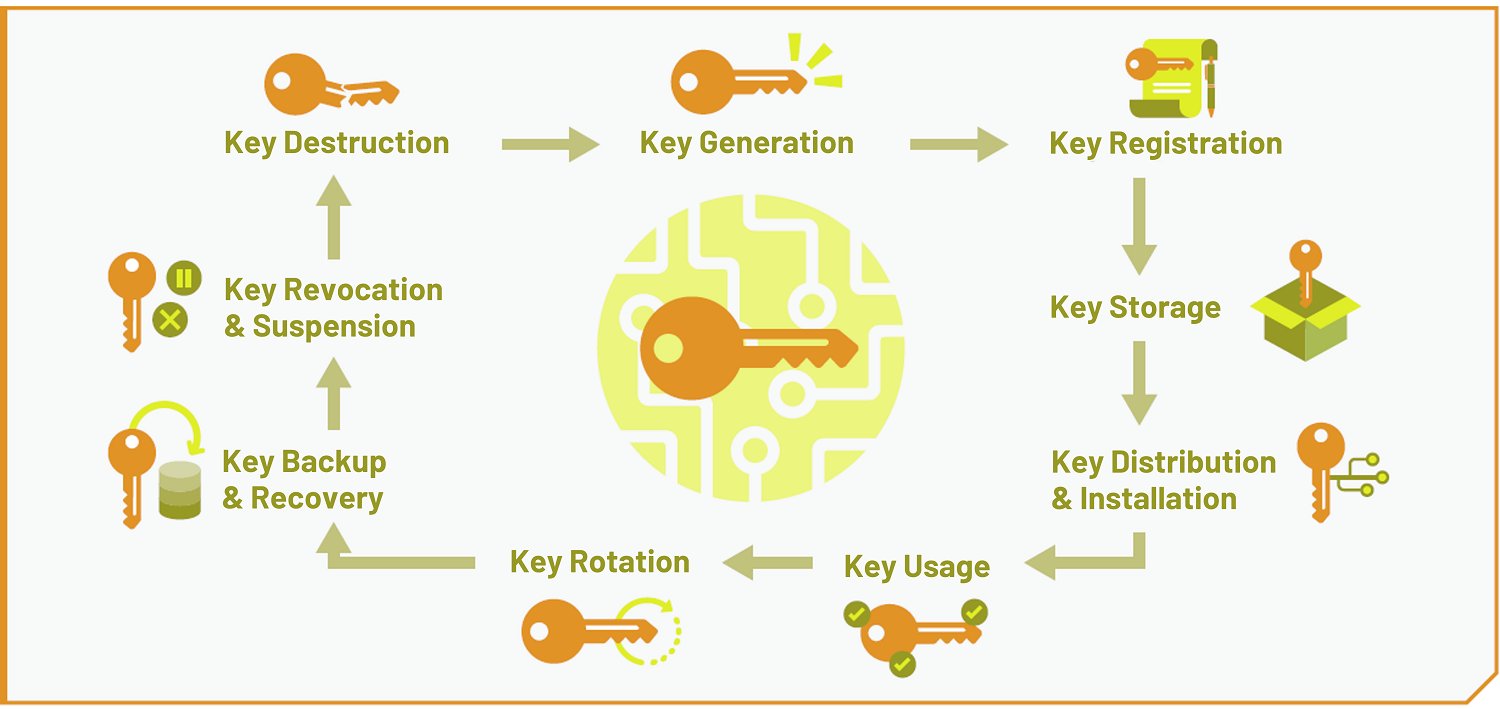
https://jingyan.baidu.com › article
Cryptographic Services 1 5 5 6
Cryptographic services gt Cryptographic Services gt
Cryptographic Services 1 5 5 6

What Is Cryptography Cryptographic Algorithms Types Of

What Is A Hardware Security Module

What Is A Cryptographic Key Keys And SSL Encryption Cloudflare

What Is The Difference Between Symmetric And Asymmetric Encryption
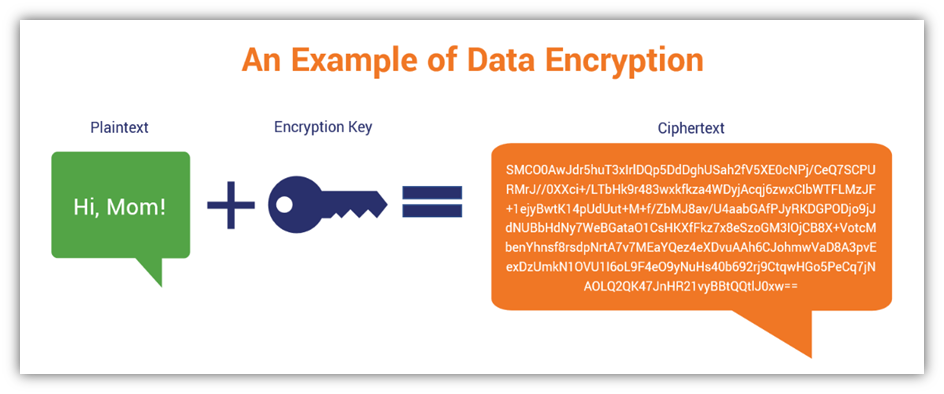
What Is Encryption A 5 Minute Overview Of Everything Encryption
Explainer What Is Post quantum Cryptography MIT Technology Review

Explainer What Is Post quantum Cryptography MIT Technology Review
2024 Complete Guide To SHA Encryption Types