In the age of digital, in which screens are the norm and the appeal of physical printed objects isn't diminished. Be it for educational use and creative work, or just adding some personal flair to your area, Symmetric Key Cryptography In Cyber Security are now a useful source. For this piece, we'll dive to the depths of "Symmetric Key Cryptography In Cyber Security," exploring what they are, where they can be found, and how they can add value to various aspects of your lives.
Get Latest Symmetric Key Cryptography In Cyber Security Below

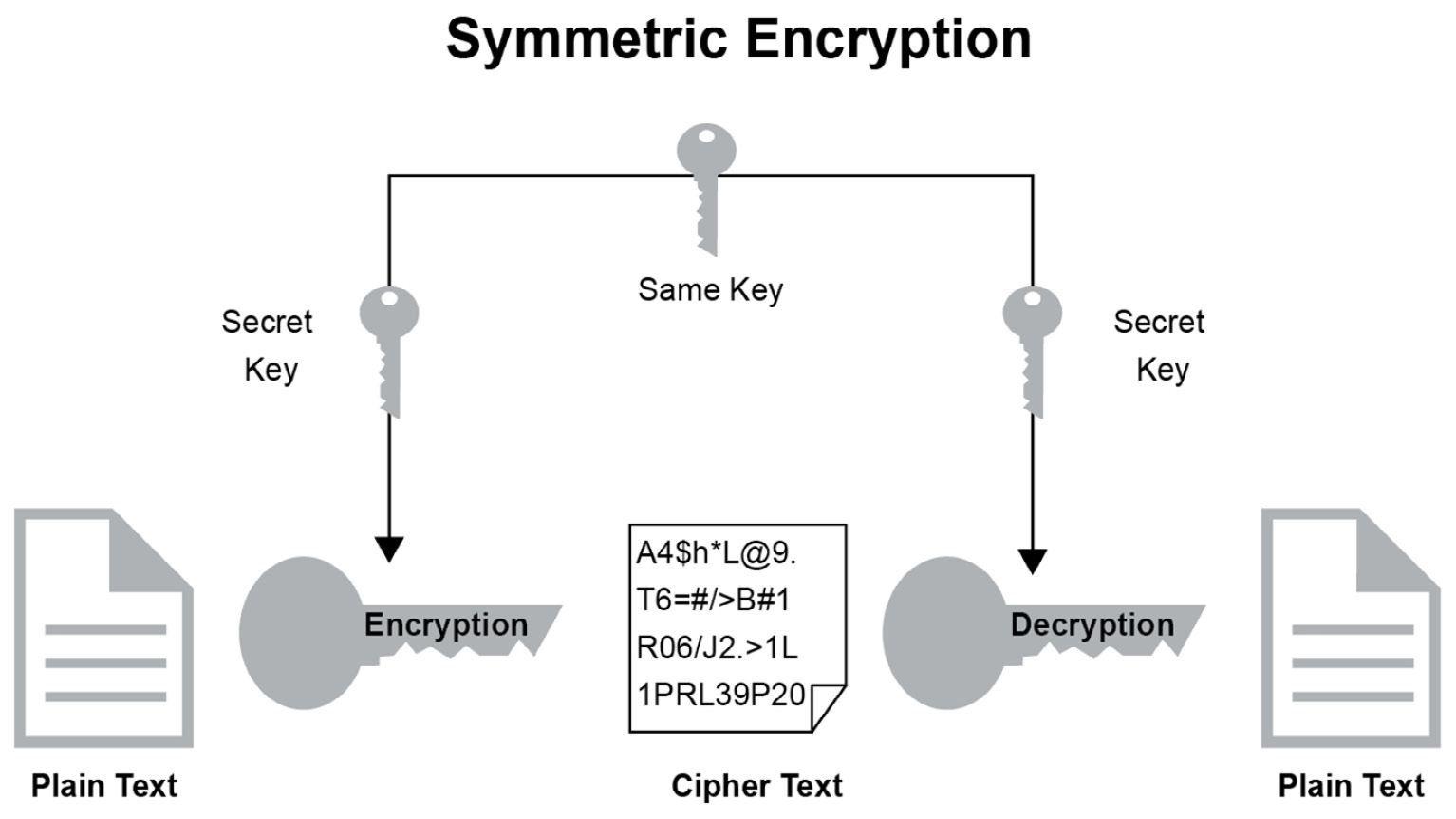
Symmetric Key Cryptography In Cyber Security
Symmetric Key Cryptography In Cyber Security - Symmetric Key Cryptography In Cyber Security, Symmetric Key Cryptography In Information Security, Symmetric Key Encryption In Cyber Security, Symmetric Key Encryption In Network Security, Symmetric And Asymmetric Key Cryptography In Network Security, Symmetric Key Ciphers In Cryptography And Network Security, Symmetric Encryption In Cyber Security, What Is Symmetric Key Cryptography, What Is The Difference Between Symmetric Key Cryptography And Asymmetric Key Cryptography, Types Of Symmetric Key Cryptography
Action Movies Series Animated Movies Series Comedy Movies Series Crime Mystery Thriller Movies Series
The Real Housewives of Atlanta The Bachelor Sister Wives 90 Day Fiance Wife Swap The Amazing Race Australia Married at First Sight
Symmetric Key Cryptography In Cyber Security provide a diverse range of printable, free documents that can be downloaded online at no cost. The resources are offered in a variety kinds, including worksheets coloring pages, templates and more. The benefit of Symmetric Key Cryptography In Cyber Security is their flexibility and accessibility.
More of Symmetric Key Cryptography In Cyber Security
Role Of Cryptography In Information Security Cloudkul
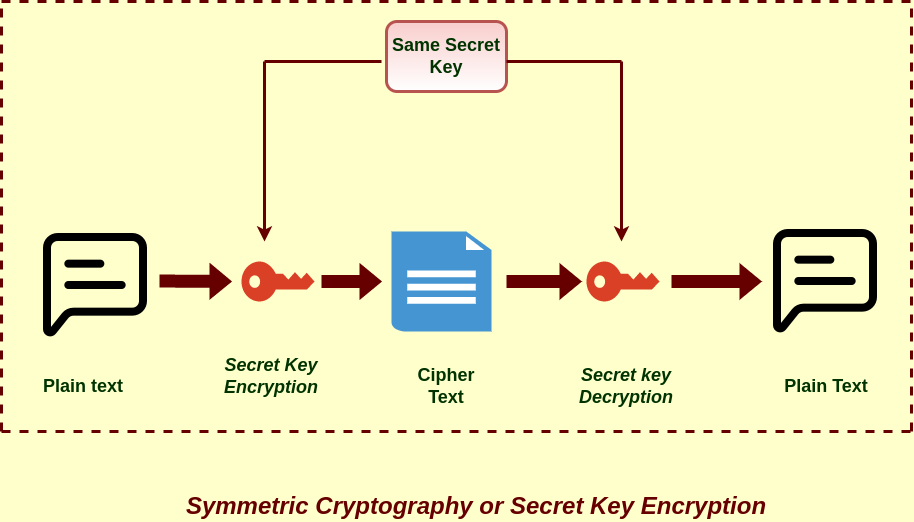
Role Of Cryptography In Information Security Cloudkul
The Real Housewives of Atlanta The Bachelor Sister Wives 90 Day Fiance Wife Swap The Amazing Race Australia Married at First Sight The Real Housewives of Dallas My
939K subscribers in the Brawlstars community Subreddit for Brawl Stars the free multiplayer mobile arena fighter party brawler shoot em up game
Symmetric Key Cryptography In Cyber Security have risen to immense recognition for a variety of compelling motives:
-
Cost-Effective: They eliminate the requirement of buying physical copies or costly software.
-
customization There is the possibility of tailoring designs to suit your personal needs in designing invitations for your guests, organizing your schedule or even decorating your house.
-
Educational Worth: Printables for education that are free cater to learners of all ages. This makes them an essential resource for educators and parents.
-
Convenience: The instant accessibility to a myriad of designs as well as templates, which saves time as well as effort.
Where to Find more Symmetric Key Cryptography In Cyber Security
Encryption Encoding And Hashing Explained

Encryption Encoding And Hashing Explained
This community doesn t have any posts yet Make one and get this feed started Create a post
I think this is addressed multiple times during the game as both the Sole Survivor and even some companions call out Piper on her poor editorial work IIRC in a dialogue between her and
Now that we've ignited your interest in Symmetric Key Cryptography In Cyber Security and other printables, let's discover where they are hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy offer a huge selection in Symmetric Key Cryptography In Cyber Security for different uses.
- Explore categories such as design, home decor, organizing, and crafts.
2. Educational Platforms
- Educational websites and forums frequently offer worksheets with printables that are free with flashcards and other teaching tools.
- This is a great resource for parents, teachers and students who are in need of supplementary resources.
3. Creative Blogs
- Many bloggers provide their inventive designs and templates for no cost.
- These blogs cover a wide array of topics, ranging all the way from DIY projects to party planning.
Maximizing Symmetric Key Cryptography In Cyber Security
Here are some fresh ways in order to maximize the use use of Symmetric Key Cryptography In Cyber Security:
1. Home Decor
- Print and frame beautiful images, quotes, or decorations for the holidays to beautify your living areas.
2. Education
- Print worksheets that are free for teaching at-home either in the schoolroom or at home.
3. Event Planning
- Design invitations, banners, and decorations for special occasions like birthdays and weddings.
4. Organization
- Get organized with printable calendars, to-do lists, and meal planners.
Conclusion
Symmetric Key Cryptography In Cyber Security are a treasure trove of innovative and useful resources catering to different needs and pursuits. Their access and versatility makes they a beneficial addition to each day life. Explore the world of Symmetric Key Cryptography In Cyber Security today to unlock new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables that are free truly gratis?
- Yes you can! You can print and download these materials for free.
-
Are there any free printables in commercial projects?
- It depends on the specific conditions of use. Be sure to read the rules of the creator prior to utilizing the templates for commercial projects.
-
Do you have any copyright problems with printables that are free?
- Certain printables may be subject to restrictions on use. You should read the conditions and terms of use provided by the author.
-
How do I print printables for free?
- Print them at home using printing equipment or visit an in-store print shop to get superior prints.
-
What software do I need in order to open printables for free?
- The majority of printed documents are with PDF formats, which can be opened with free programs like Adobe Reader.
Encryption Choices Rsa Vs Aes Explained Prey

Concept Of Cryptography In Blockchain

Check more sample of Symmetric Key Cryptography In Cyber Security below
What Is Symmetric Key Cryptography Encryption Security Wiki

Cryptography CarolinaRiley
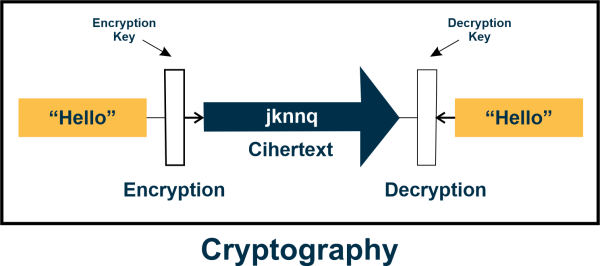
Cryptography CyberSecurity Studio
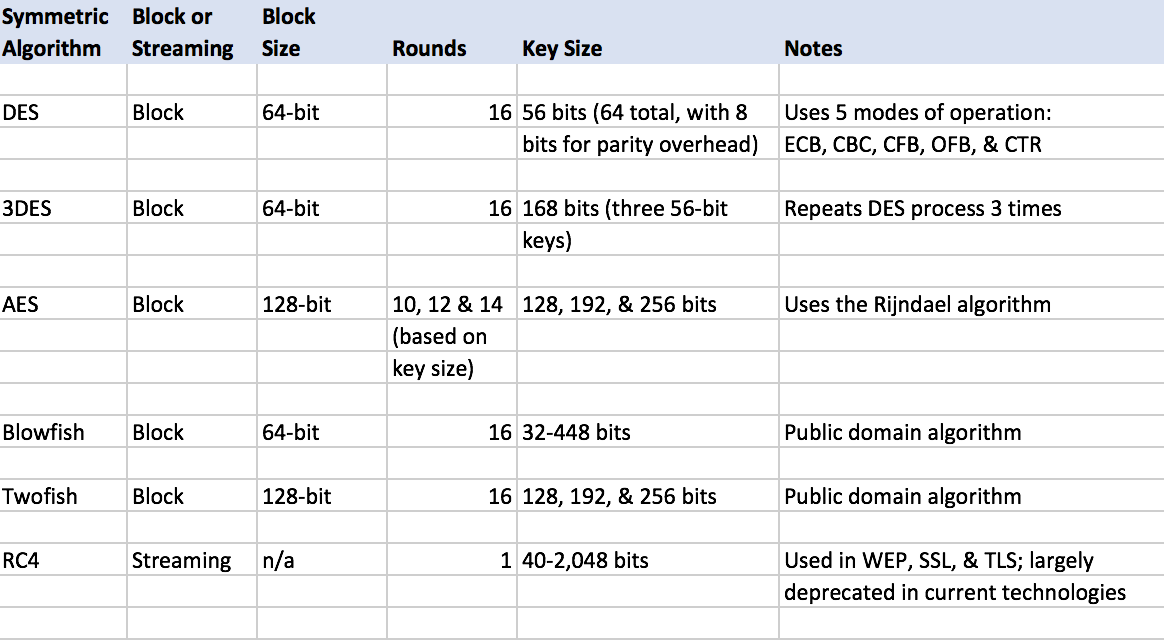
Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Symmetric Vs Asymmetric Encryption Differences Explained

Symmetric And Asymmetric Key Cryptography The Key Differences Explained


https://www.reddit.com › user › PiperPresley
The Real Housewives of Atlanta The Bachelor Sister Wives 90 Day Fiance Wife Swap The Amazing Race Australia Married at First Sight
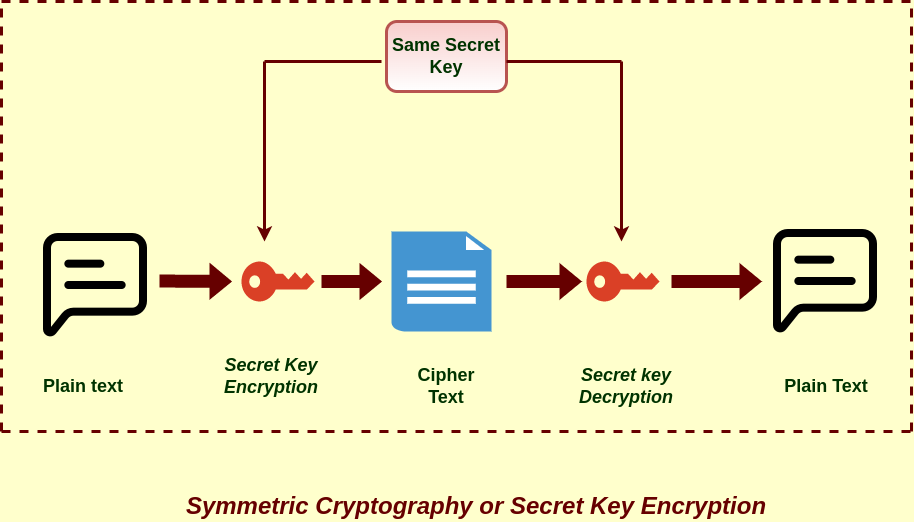
https://www.reddit.com › user › PiperPresley › comments
Action Movies Series Animated Movies Series Comedy Movies Series Crime Mystery Thriller Movies Series
The Real Housewives of Atlanta The Bachelor Sister Wives 90 Day Fiance Wife Swap The Amazing Race Australia Married at First Sight
Action Movies Series Animated Movies Series Comedy Movies Series Crime Mystery Thriller Movies Series

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Cryptography CarolinaRiley

Symmetric Vs Asymmetric Encryption Differences Explained

Symmetric And Asymmetric Key Cryptography The Key Differences Explained
HTTPS HTTP Secure

Encryption And Decryption Jean s Blog

Encryption And Decryption Jean s Blog

Unlocking Blockchain s Fort Knox The Power Of Cryptography For