In the age of digital, where screens have become the dominant feature of our lives yet the appeal of tangible printed objects isn't diminished. No matter whether it's for educational uses as well as creative projects or simply to add an element of personalization to your home, printables for free have proven to be a valuable resource. We'll take a dive to the depths of "Symmetric Key Encryption In Network Security," exploring what they are, where they can be found, and the ways that they can benefit different aspects of your life.
Get Latest Symmetric Key Encryption In Network Security Below

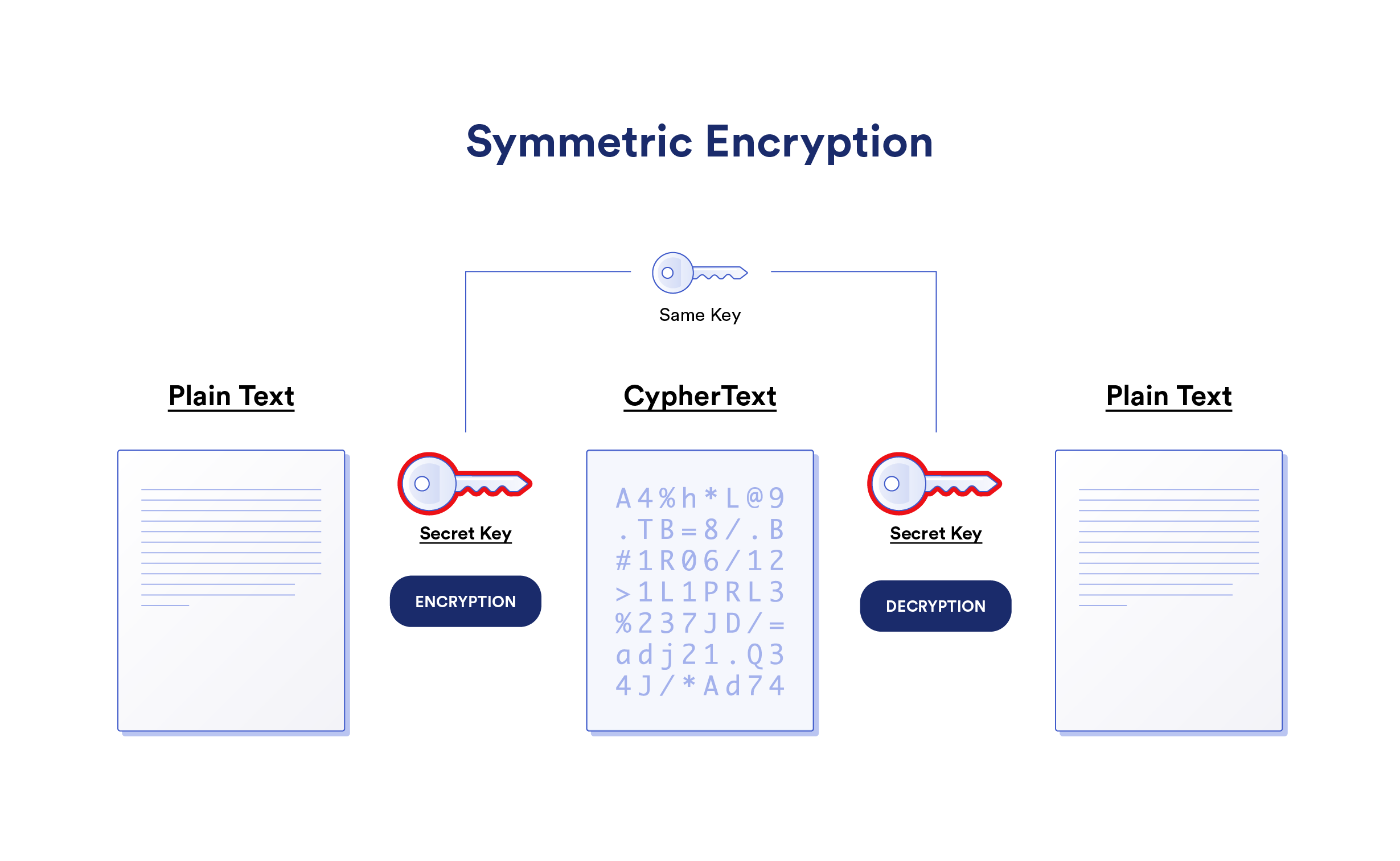
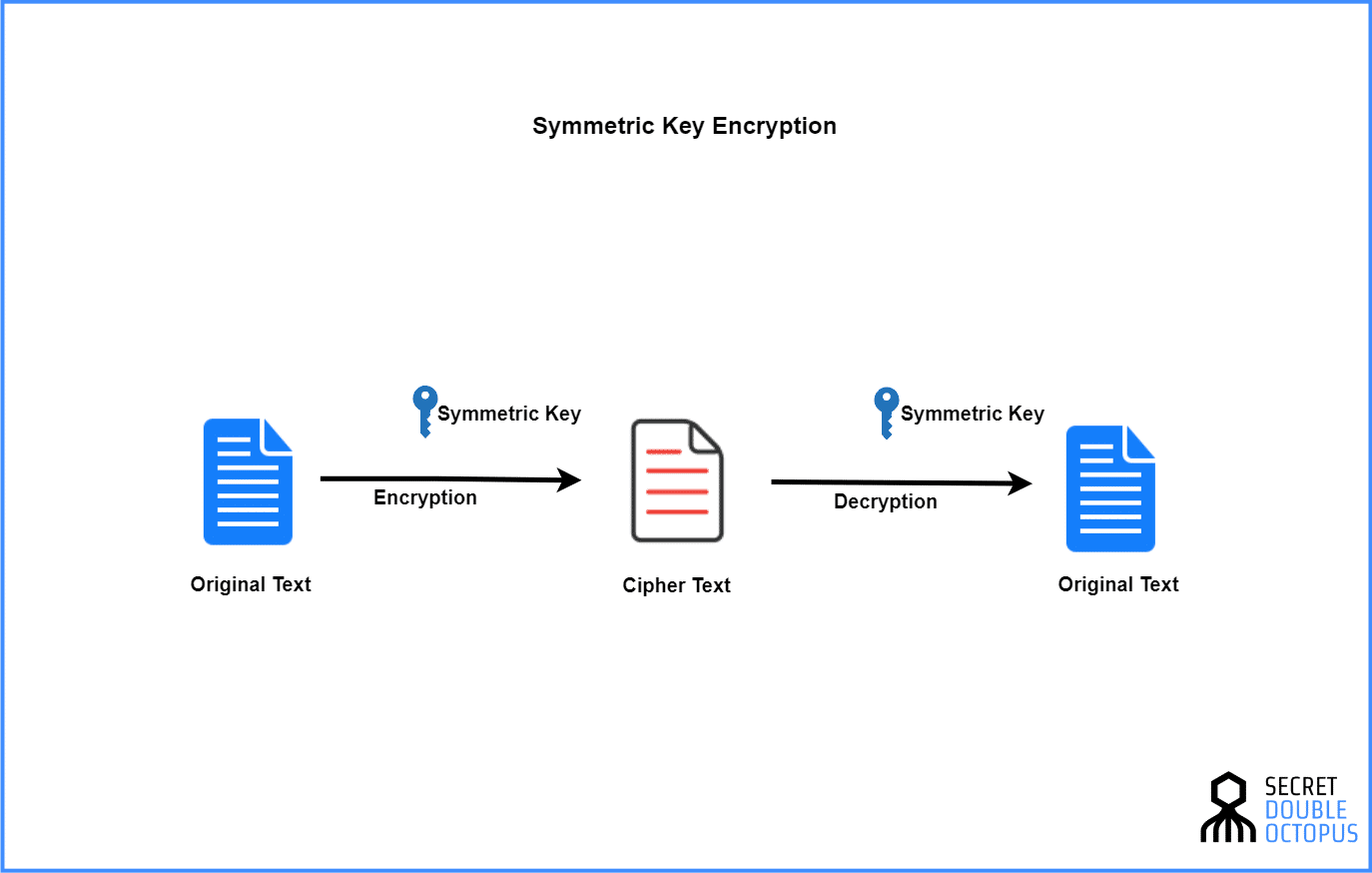
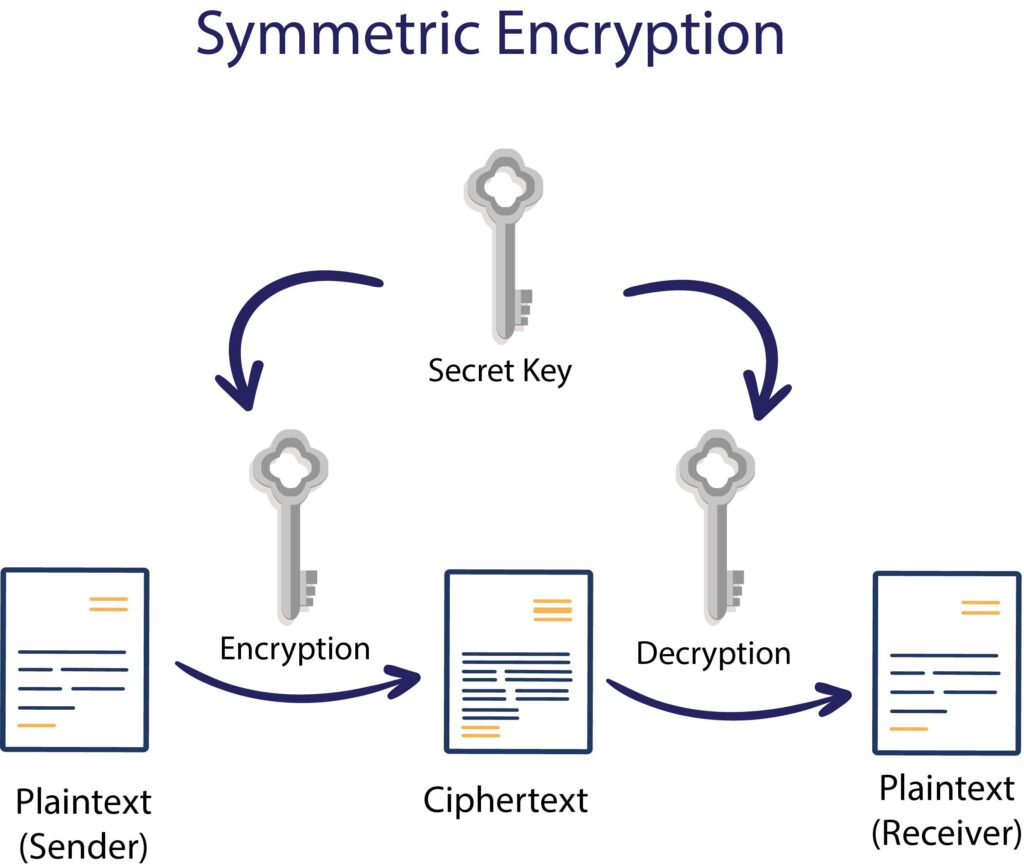
Symmetric Key Encryption In Network Security
Symmetric Key Encryption In Network Security - Symmetric Key Encryption In Network Security, Symmetric Key Cryptography In Network Security, Symmetric Key Encryption In Cyber Security, Symmetric Key Cryptography In Information Security, Symmetric And Asymmetric Key Cryptography In Network Security, What Is Symmetric Encryption Key, What Is Encryption In Network Security, Symmetric Encryption Principles In Network Security
[desc-5]
XNXX is just a content mirror of Xvideos and they have a safe content policy so you re not in any danger Even if you were simply viewing illegal content by accident isn t a
Printables for free cover a broad collection of printable materials available online at no cost. These resources come in various forms, including worksheets, templates, coloring pages and many more. The beauty of Symmetric Key Encryption In Network Security is their versatility and accessibility.
More of Symmetric Key Encryption In Network Security
What Is Symmetric Key Cryptography Encryption Security Wiki

What Is Symmetric Key Cryptography Encryption Security Wiki
[desc-4]
[desc-6]
Symmetric Key Encryption In Network Security have gained immense appeal due to many compelling reasons:
-
Cost-Effective: They eliminate the necessity of purchasing physical copies or expensive software.
-
Modifications: It is possible to tailor designs to suit your personal needs such as designing invitations making your schedule, or even decorating your house.
-
Educational Value Printables for education that are free are designed to appeal to students from all ages, making them a valuable instrument for parents and teachers.
-
The convenience of The instant accessibility to the vast array of design and templates helps save time and effort.
Where to Find more Symmetric Key Encryption In Network Security
What Is Zero Knowledge Encryption Chainlink Blog
What Is Zero Knowledge Encryption Chainlink Blog
[desc-9]
[desc-7]
If we've already piqued your interest in printables for free We'll take a look around to see where they are hidden gems:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy offer an extensive collection of Symmetric Key Encryption In Network Security to suit a variety of applications.
- Explore categories such as home decor, education, craft, and organization.
2. Educational Platforms
- Educational websites and forums often offer worksheets with printables that are free for flashcards, lessons, and worksheets. tools.
- Perfect for teachers, parents or students in search of additional sources.
3. Creative Blogs
- Many bloggers provide their inventive designs and templates for free.
- The blogs are a vast range of interests, ranging from DIY projects to planning a party.
Maximizing Symmetric Key Encryption In Network Security
Here are some unique ways for you to get the best of printables that are free:
1. Home Decor
- Print and frame gorgeous art, quotes, or seasonal decorations that will adorn your living areas.
2. Education
- Use free printable worksheets to aid in learning at your home, or even in the classroom.
3. Event Planning
- Design invitations, banners as well as decorations for special occasions like weddings or birthdays.
4. Organization
- Be organized by using printable calendars including to-do checklists, daily lists, and meal planners.
Conclusion
Symmetric Key Encryption In Network Security are an abundance of practical and imaginative resources that can meet the needs of a variety of people and interests. Their accessibility and flexibility make they a beneficial addition to any professional or personal life. Explore the wide world of Symmetric Key Encryption In Network Security now and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables for free really are they free?
- Yes they are! You can print and download these items for free.
-
Can I utilize free printables for commercial uses?
- It's determined by the specific conditions of use. Always verify the guidelines provided by the creator prior to printing printables for commercial projects.
-
Are there any copyright concerns with printables that are free?
- Certain printables might have limitations on usage. Check the conditions and terms of use provided by the author.
-
How do I print Symmetric Key Encryption In Network Security?
- You can print them at home using a printer or visit the local print shops for more high-quality prints.
-
What program do I need in order to open printables for free?
- A majority of printed materials are in the format of PDF, which can be opened with free software such as Adobe Reader.
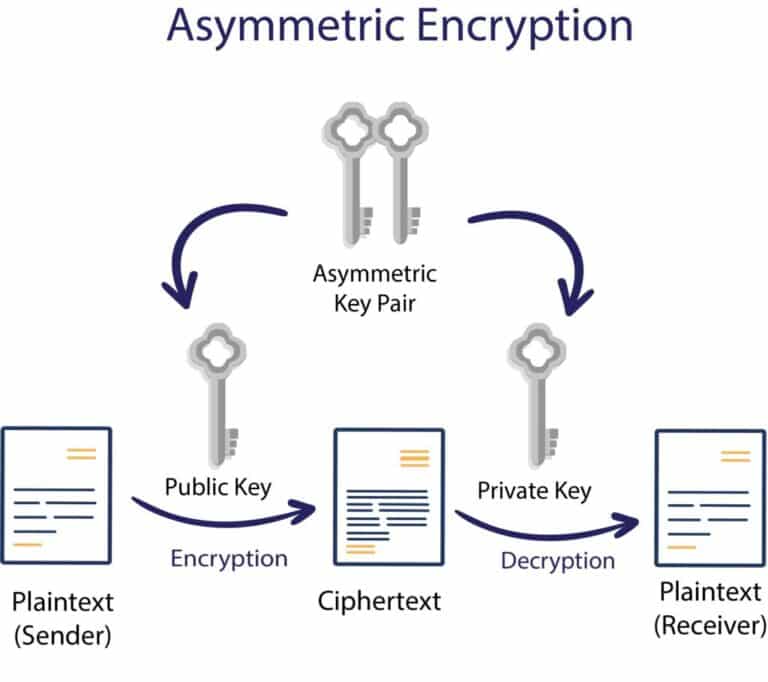
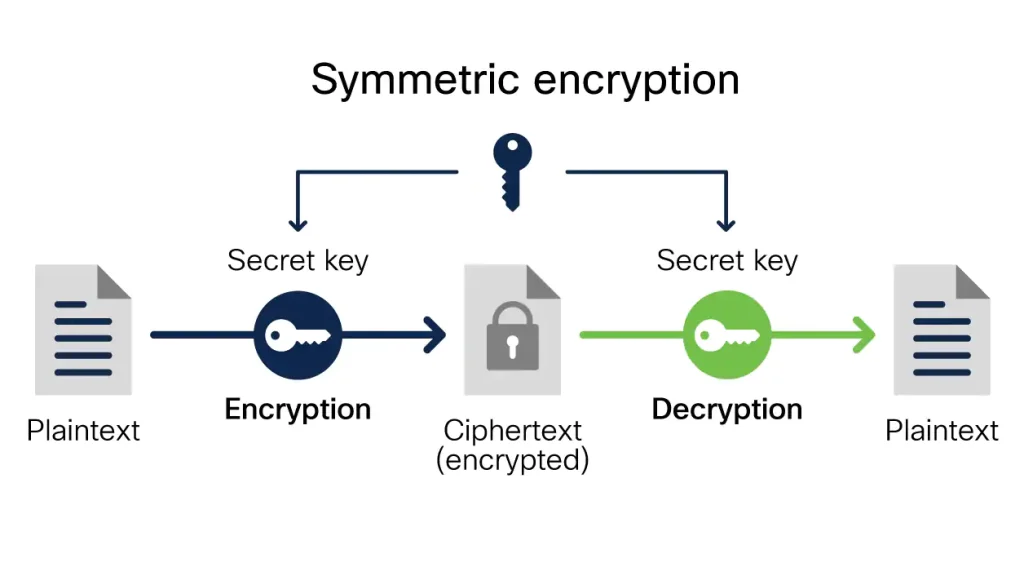
Difference Between Symmetric And Asymmetric Encryption Symmetric Key

Encryption And Decryption Jean s Blog

Check more sample of Symmetric Key Encryption In Network Security below
Encrypting Data Best Practices For Security Prey

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

How Public Key Encryption Ensures Data Integrity

Asymmetric Encryption What It Is Why Your Security Depends On It

What Is Cryptography In Security What Are The Different Types Of
Digital Signature Algorithm DSA In Cryptography A Complete Guide

https://www.reddit.com › NoStupidQuestions › comments › is_xnxx...
XNXX is just a content mirror of Xvideos and they have a safe content policy so you re not in any danger Even if you were simply viewing illegal content by accident isn t a
https://www.reddit.com › AskRedditNSFW › comments › which_is...
Xnxx Because it s easy to type with one hand Reply reply Indepemdent policy32 That s the most
XNXX is just a content mirror of Xvideos and they have a safe content policy so you re not in any danger Even if you were simply viewing illegal content by accident isn t a
Xnxx Because it s easy to type with one hand Reply reply Indepemdent policy32 That s the most

Asymmetric Encryption What It Is Why Your Security Depends On It

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

What Is Cryptography In Security What Are The Different Types Of

Digital Signature Algorithm DSA In Cryptography A Complete Guide

Asymmetric Encryption How Asymmetric Encryption Works
What Is Key Management How Does Key Management Work Encryption

What Is Key Management How Does Key Management Work Encryption
Encryption THE CHETTER