In this day and age where screens have become the dominant feature of our lives yet the appeal of tangible printed items hasn't gone away. Be it for educational use such as creative projects or just adding an individual touch to the home, printables for free have proven to be a valuable resource. Here, we'll dive into the sphere of "Symmetric And Asymmetric Key Cryptography In Network Security," exploring their purpose, where to find them and the ways that they can benefit different aspects of your lives.
Get Latest Symmetric And Asymmetric Key Cryptography In Network Security Below
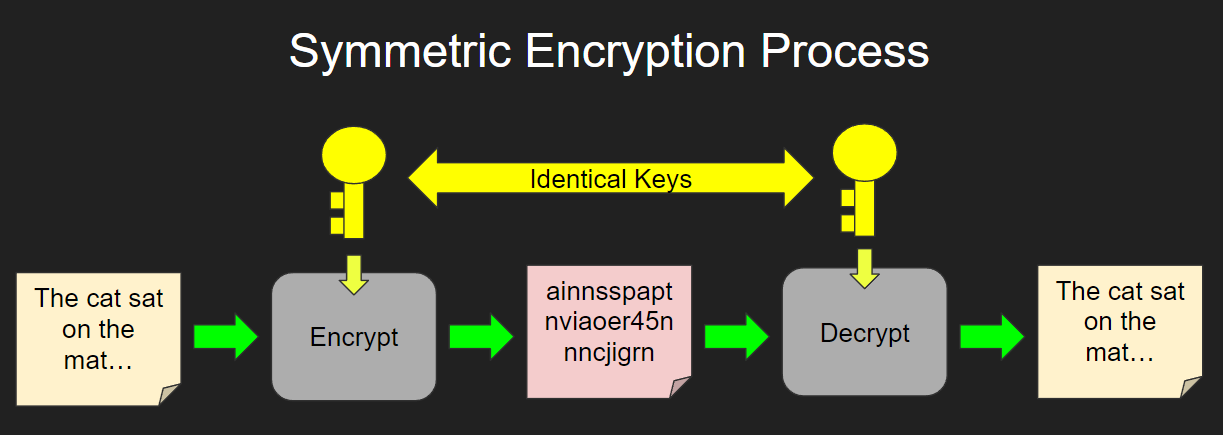
Symmetric And Asymmetric Key Cryptography In Network Security
Symmetric And Asymmetric Key Cryptography In Network Security - Symmetric And Asymmetric Key Cryptography In Network Security
I want porno movies that are made with guys like me in mind Guys who know that the sexiest thing in the world is a woman who is smarter than you are You can have the whole
Hello New users on the forum won t be able to send PM untill certain criteria are met you need to have at least 6 posts in any sub forum
Printables for free cover a broad range of printable, free materials that are accessible online for free cost. These printables come in different types, such as worksheets templates, coloring pages, and more. The value of Symmetric And Asymmetric Key Cryptography In Network Security is in their variety and accessibility.
More of Symmetric And Asymmetric Key Cryptography In Network Security
Public Key Cryptography Decoded What Is Cryptography Ntirawen

Public Key Cryptography Decoded What Is Cryptography Ntirawen
Forum index hu Magyarorsz g els s legnagyobb f rum szolg ltat sa A web kett pre b t ja amit 1997 ta t ltenek meg tartalommal a f rumlak k
Hello Personal info as kik email skype etc is not allowed email is kik is same as my username on our forum
Symmetric And Asymmetric Key Cryptography In Network Security have risen to immense popularity because of a number of compelling causes:
-
Cost-Effective: They eliminate the requirement of buying physical copies of the software or expensive hardware.
-
Individualization You can tailor designs to suit your personal needs such as designing invitations and schedules, or even decorating your home.
-
Educational Value Free educational printables provide for students of all ages, which makes them a great tool for parents and educators.
-
Simple: Instant access to the vast array of design and templates, which saves time as well as effort.
Where to Find more Symmetric And Asymmetric Key Cryptography In Network Security
Beginners Guide To Cryptography Quick

Beginners Guide To Cryptography Quick
Hello You can now get verified on forum The way it s gonna work is that you can send me a PM with a verification picture
dv z llek a Klubban meszike aprop itt a rendszer r gt n azt jelzi hogy tagd j elmarad sod van k rlek egyenl tsd ki hamarost
Now that we've piqued your interest in printables for free Let's look into where you can find these gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a large collection of Symmetric And Asymmetric Key Cryptography In Network Security to suit a variety of objectives.
- Explore categories such as home decor, education, crafting, and organization.
2. Educational Platforms
- Educational websites and forums typically provide free printable worksheets along with flashcards, as well as other learning materials.
- The perfect resource for parents, teachers or students in search of additional resources.
3. Creative Blogs
- Many bloggers share their creative designs and templates at no cost.
- These blogs cover a wide spectrum of interests, starting from DIY projects to party planning.
Maximizing Symmetric And Asymmetric Key Cryptography In Network Security
Here are some innovative ways to make the most of Symmetric And Asymmetric Key Cryptography In Network Security:
1. Home Decor
- Print and frame beautiful art, quotes, or seasonal decorations to adorn your living spaces.
2. Education
- Use free printable worksheets to build your knowledge at home as well as in the class.
3. Event Planning
- Design invitations for banners, invitations and other decorations for special occasions such as weddings, birthdays, and other special occasions.
4. Organization
- Stay organized by using printable calendars including to-do checklists, daily lists, and meal planners.
Conclusion
Symmetric And Asymmetric Key Cryptography In Network Security are an abundance of innovative and useful resources that cater to various needs and passions. Their accessibility and versatility make them a fantastic addition to both professional and personal life. Explore the endless world of Symmetric And Asymmetric Key Cryptography In Network Security right now and open up new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free available for download?
- Yes you can! You can download and print these free resources for no cost.
-
Does it allow me to use free templates for commercial use?
- It's dependent on the particular usage guidelines. Always review the terms of use for the creator prior to printing printables for commercial projects.
-
Do you have any copyright issues when you download Symmetric And Asymmetric Key Cryptography In Network Security?
- Some printables could have limitations on use. Be sure to review the terms and regulations provided by the author.
-
How can I print printables for free?
- You can print them at home using any printer or head to a local print shop for the highest quality prints.
-
What software must I use to open Symmetric And Asymmetric Key Cryptography In Network Security?
- Many printables are offered in the PDF format, and can be opened using free software, such as Adobe Reader.
Symmetric And Asymmetric Key Cryptography The Key Differences Explained

Symmetric Vs Asymmetric Encryption Differences Explained

Check more sample of Symmetric And Asymmetric Key Cryptography In Network Security below
Chirag s Blog Difference Between Symmetric And Asymmetric Key

What Is Symmetric Key Cryptography Encryption Security Wiki

Difference Between Symmetric And Asymmetric Encryption Symmetric Key

Demystifying Symmetric And Asymmetric Encryption Cyber Security


Encryption Choices Rsa Vs Aes Explained Prey

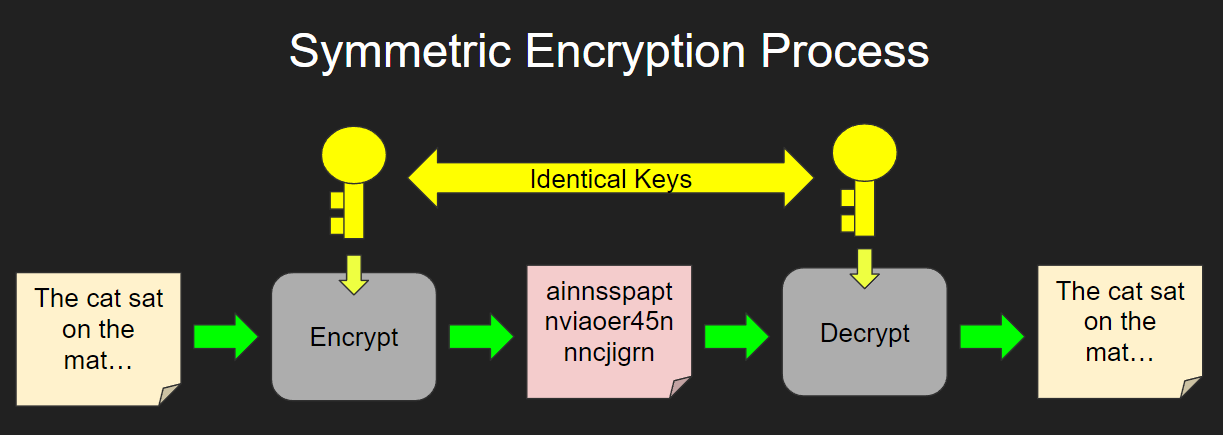
https://forum.xnxx.com › threads
Hello New users on the forum won t be able to send PM untill certain criteria are met you need to have at least 6 posts in any sub forum
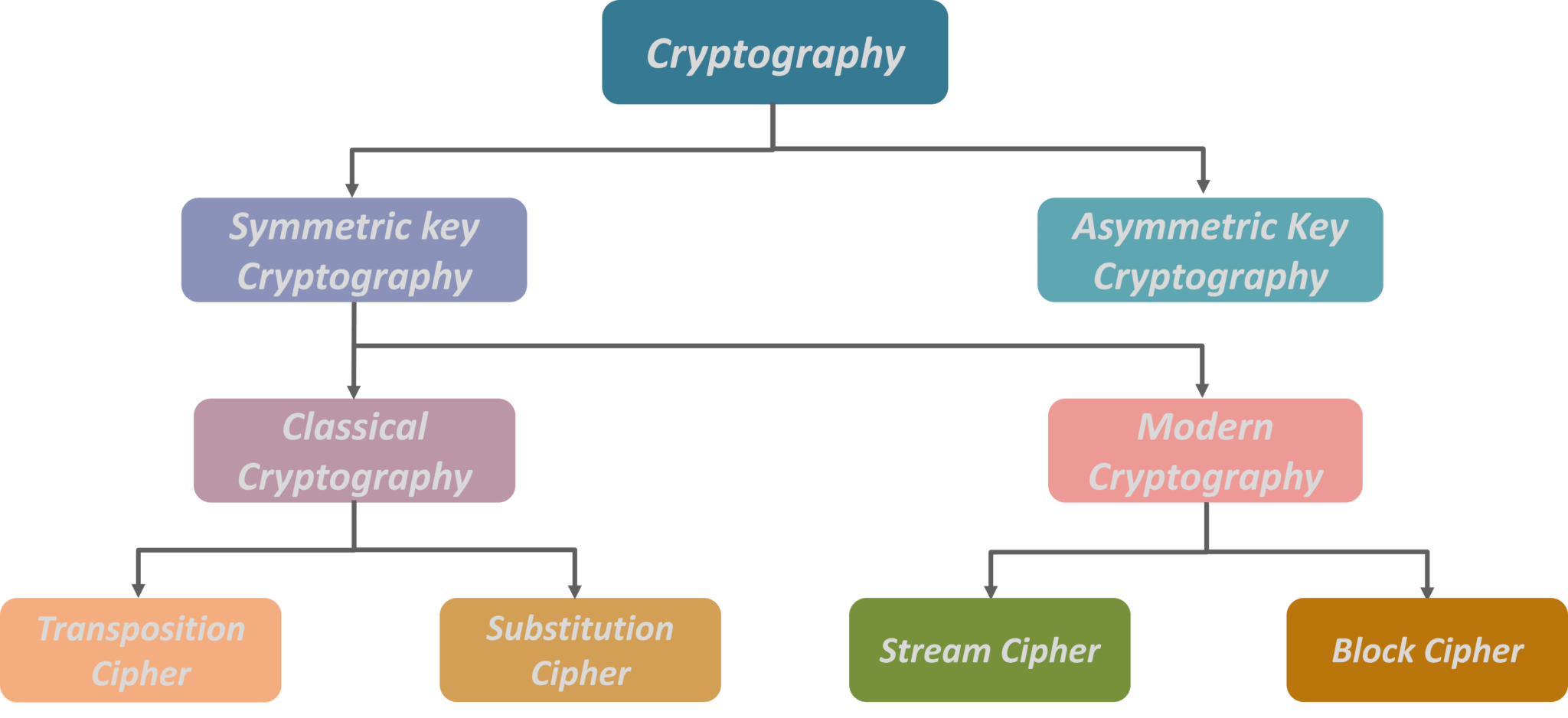
https://forum.xnxx.com › threads
I ve been looking for a complete list of 1980 s female porn stars with no real luck I get some but not a complete list I know there were many that I
Hello New users on the forum won t be able to send PM untill certain criteria are met you need to have at least 6 posts in any sub forum
I ve been looking for a complete list of 1980 s female porn stars with no real luck I get some but not a complete list I know there were many that I

Demystifying Symmetric And Asymmetric Encryption Cyber Security

What Is Symmetric Key Cryptography Encryption Security Wiki


Encryption Choices Rsa Vs Aes Explained Prey
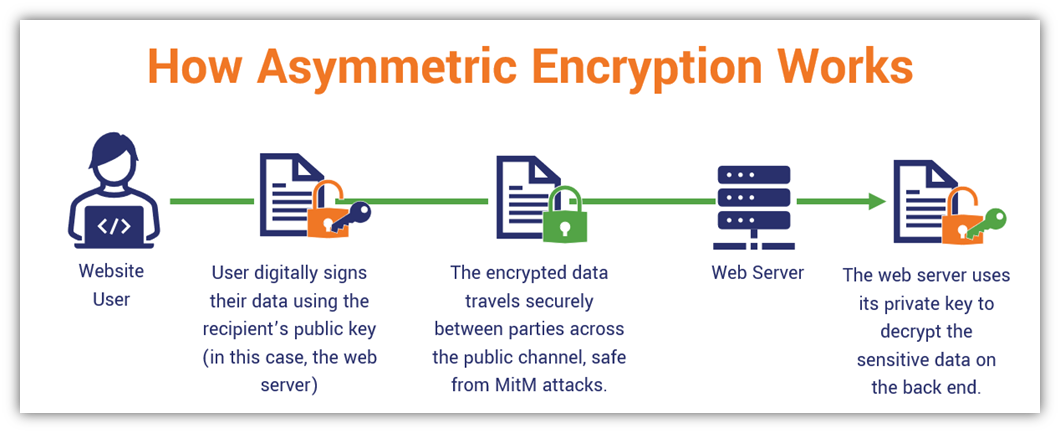
Asymmetric Encryption What It Is Why Your Security Depends On It

Asymmetric Encryption How Asymmetric Encryption Works

Asymmetric Encryption How Asymmetric Encryption Works

What Is Asymmetric Encryption How Does It Work InfoSec Insights