In this age of technology, where screens rule our lives but the value of tangible printed material hasn't diminished. If it's to aid in education such as creative projects or simply adding an individual touch to the area, Symmetric Encryption Principles In Network Security are now a vital resource. Through this post, we'll take a dive through the vast world of "Symmetric Encryption Principles In Network Security," exploring what they are, where you can find them, and what they can do to improve different aspects of your lives.
What Are Symmetric Encryption Principles In Network Security?
Symmetric Encryption Principles In Network Security encompass a wide variety of printable, downloadable content that can be downloaded from the internet at no cost. The resources are offered in a variety styles, from worksheets to templates, coloring pages, and much more. The appealingness of Symmetric Encryption Principles In Network Security lies in their versatility and accessibility.
Symmetric Encryption Principles In Network Security

Symmetric Encryption Principles In Network Security
Symmetric Encryption Principles In Network Security -
[desc-5]
[desc-1]
What Is Data Encryption Bitdefender Cyberpedia

What Is Data Encryption Bitdefender Cyberpedia
[desc-4]
[desc-6]
What Is Zero Knowledge Encryption Chainlink Blog
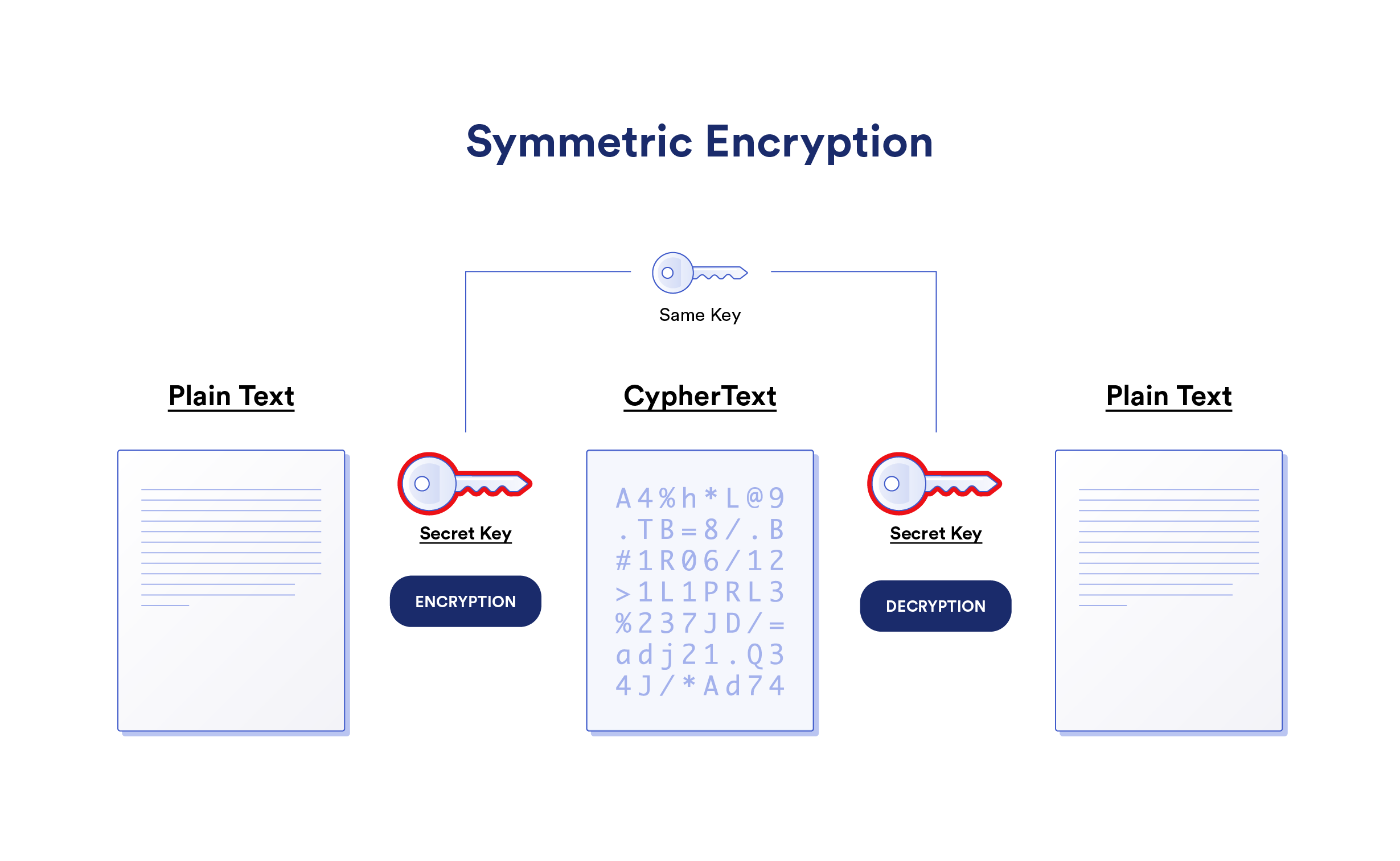
What Is Zero Knowledge Encryption Chainlink Blog
[desc-9]
[desc-7]

How To Decrypt Encrypted Schematic Calamity
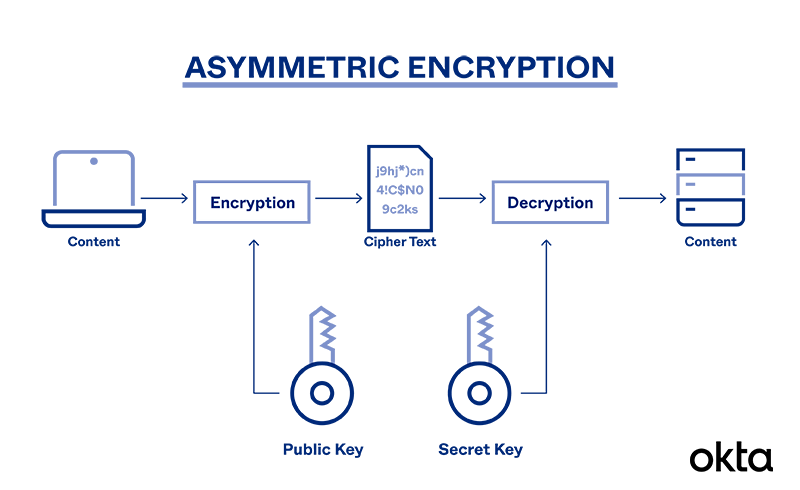
What Is Asymmetric Encryption Its Main Principles Okta

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Asymmetric Encryption How Asymmetric Encryption Works

How Public Key Encryption Ensures Data Integrity

What Is Secret Key Cryptography A Complete Guide Helenix

What Is Secret Key Cryptography A Complete Guide Helenix
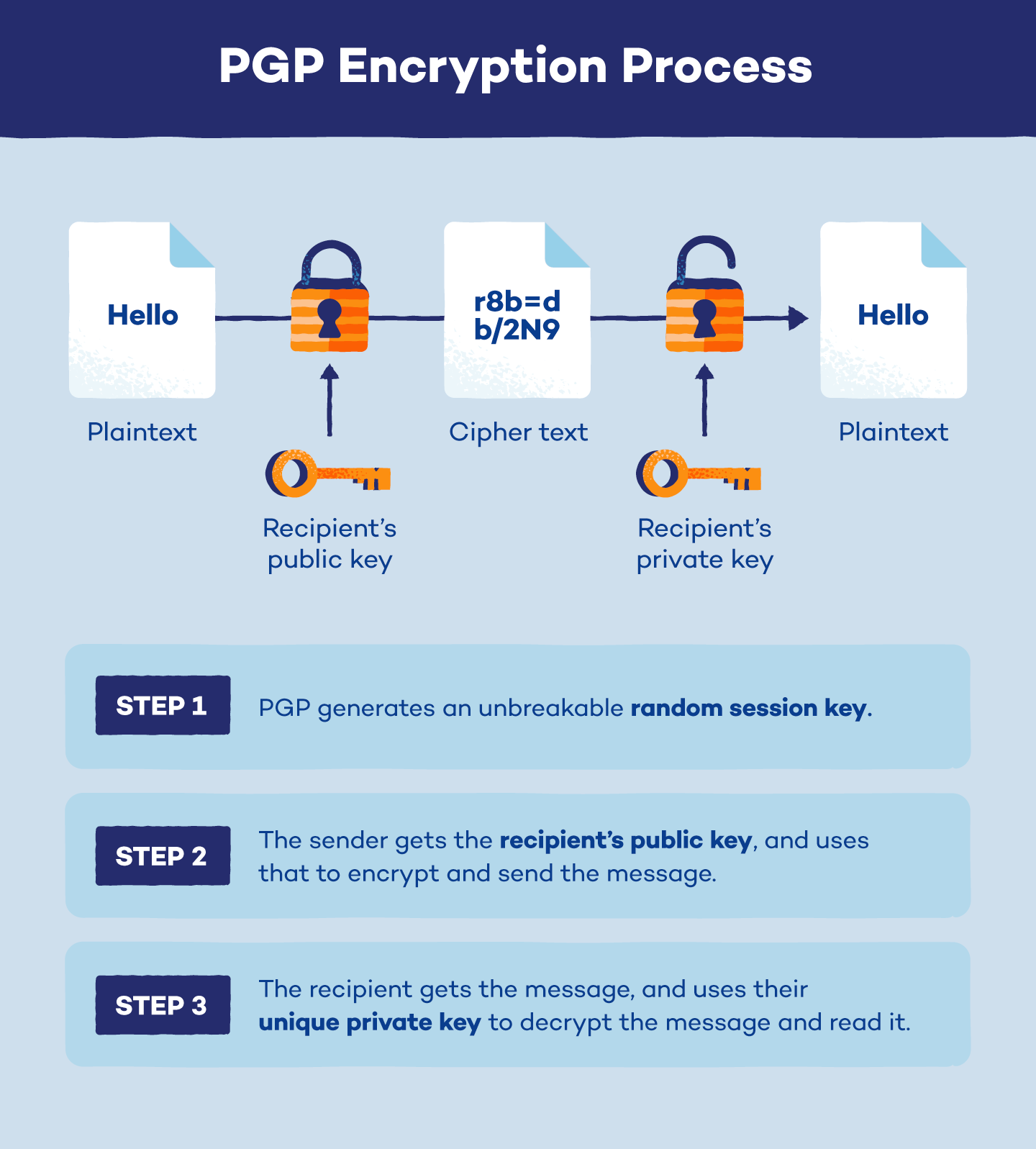
PGP Encryption The Email Security Standard Panda Security