In this age of electronic devices, where screens have become the dominant feature of our lives it's no wonder that the appeal of tangible printed materials hasn't faded away. If it's to aid in education in creative or artistic projects, or simply adding some personal flair to your area, Symmetric Key Cryptography In Information Security are a great resource. Through this post, we'll take a dive into the world of "Symmetric Key Cryptography In Information Security," exploring the different types of printables, where to find them and how they can improve various aspects of your lives.
Get Latest Symmetric Key Cryptography In Information Security Below
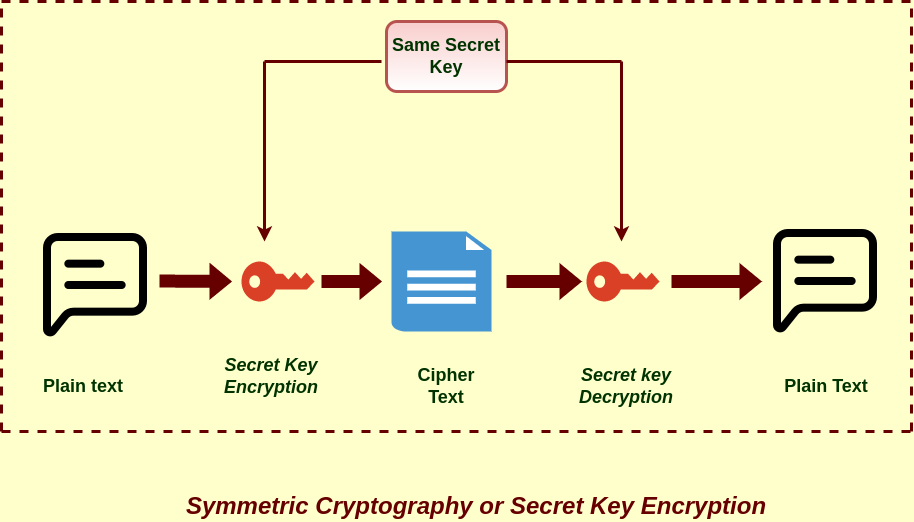
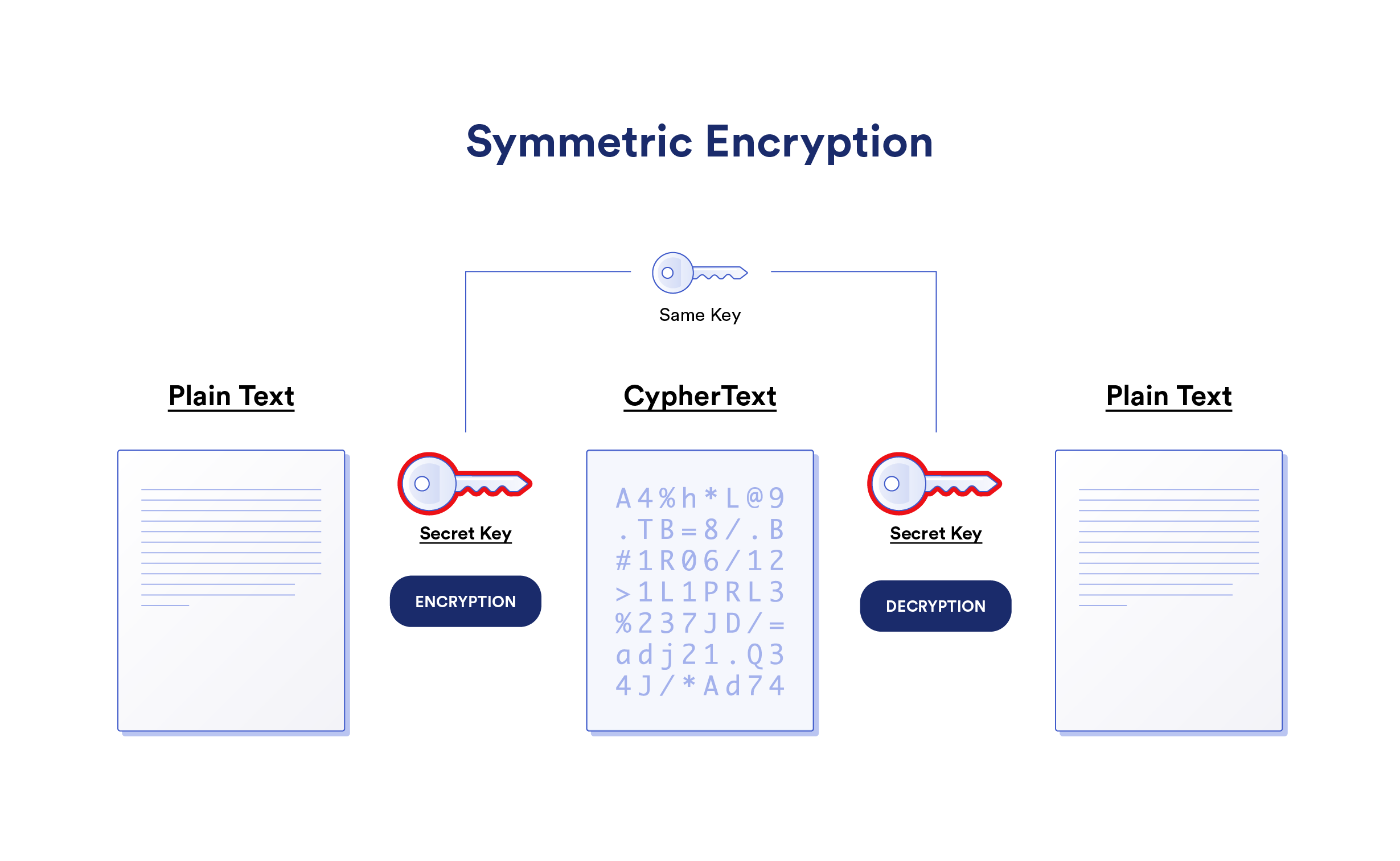
Symmetric Key Cryptography In Information Security
Symmetric Key Cryptography In Information Security - Symmetric Key Cryptography In Information Security, Symmetric Key Cryptography In Network Security, Symmetric Key Encryption In Cyber Security, Symmetric Key Encryption In Network Security, Asymmetric And Symmetric Key Cryptography In Information Security, Symmetric Key Ciphers In Cryptography And Network Security, Symmetric Encryption In Information Security, What Is Symmetric Key Cryptography, How Many Keys Are Used In Symmetric Cryptography, What Is Symmetric Encryption Key
Con cenos Datos pr cticos Carn BRMU Biblioteca accesible Normativa Recomendaciones Cat logos Biblioteca eBiblio Murcia eFilm Murcia Red de Bibliotecas P blicas Regi n de
La Biblioteca ofrece un servicio de reproducci n de fondos con el objetivo de facilitar el acceso a la informaci n
Printables for free include a vast range of printable, free materials that are accessible online for free cost. The resources are offered in a variety types, such as worksheets coloring pages, templates and more. The attraction of printables that are free is in their variety and accessibility.
More of Symmetric Key Cryptography In Information Security
Encryption Choices Rsa Vs Aes Explained Prey

Encryption Choices Rsa Vs Aes Explained Prey
Descubra la red de bibliotecas p blicas de la ciudad de Barcelona los horarios la programaci n cultural conozca las colecciones y los servicios que ofrecen
Localidad Valladolid Valladolid Tipo de Gesti n P blica Horario de apertura Horario habitual De lunes a viernes de 8 00 a 21 45 h S bados de 8 00 a 14 45 h Sala infantil De lunes a
The Symmetric Key Cryptography In Information Security have gained huge appeal due to many compelling reasons:
-
Cost-Efficiency: They eliminate the necessity to purchase physical copies or expensive software.
-
Flexible: They can make printables to fit your particular needs in designing invitations making your schedule, or even decorating your house.
-
Education Value Free educational printables cater to learners of all ages, which makes these printables a powerful resource for educators and parents.
-
Simple: instant access a variety of designs and templates, which saves time as well as effort.
Where to Find more Symmetric Key Cryptography In Information Security
Concept Of Cryptography In Blockchain

Concept Of Cryptography In Blockchain
Sistema Andaluz de Bibliotecas y Centros de Documentaci n Bibliotecas P blicas del Estado Bibliotecas Provinciales de Andaluc a Biblioteca P blica del Estado Biblioteca Provincial de
Biblioteca Te explicamos qu es una biblioteca y cu les son las categor as en que se organizan los libros Adem s sus caracter sticas su origen y sus tipos
In the event that we've stirred your curiosity about Symmetric Key Cryptography In Information Security Let's take a look at where you can get these hidden gems:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy offer a vast selection and Symmetric Key Cryptography In Information Security for a variety objectives.
- Explore categories like design, home decor, the arts, and more.
2. Educational Platforms
- Forums and educational websites often offer worksheets with printables that are free Flashcards, worksheets, and other educational tools.
- The perfect resource for parents, teachers and students looking for extra sources.
3. Creative Blogs
- Many bloggers post their original designs and templates for no cost.
- These blogs cover a wide range of interests, that includes DIY projects to planning a party.
Maximizing Symmetric Key Cryptography In Information Security
Here are some ideas that you can make use use of printables that are free:
1. Home Decor
- Print and frame gorgeous artwork, quotes, or even seasonal decorations to decorate your living areas.
2. Education
- Use free printable worksheets to enhance learning at home and in class.
3. Event Planning
- Design invitations, banners, and other decorations for special occasions such as weddings or birthdays.
4. Organization
- Keep your calendars organized by printing printable calendars or to-do lists. meal planners.
Conclusion
Symmetric Key Cryptography In Information Security are an abundance filled with creative and practical information catering to different needs and hobbies. Their accessibility and versatility make them an essential part of both professional and personal life. Explore the vast array of Symmetric Key Cryptography In Information Security to uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free available for download?
- Yes they are! You can print and download these documents for free.
-
Does it allow me to use free printables to make commercial products?
- It's all dependent on the terms of use. Always verify the guidelines provided by the creator prior to utilizing the templates for commercial projects.
-
Are there any copyright concerns with printables that are free?
- Certain printables might have limitations on usage. Be sure to review the terms of service and conditions provided by the designer.
-
How do I print Symmetric Key Cryptography In Information Security?
- Print them at home using printing equipment or visit a local print shop to purchase top quality prints.
-
What software must I use to open Symmetric Key Cryptography In Information Security?
- The majority of printed documents are in PDF format, which can be opened using free software, such as Adobe Reader.
What Is Symmetric Key Cryptography Encryption Security Wiki

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Check more sample of Symmetric Key Cryptography In Information Security below
Public Key Cryptography Basics Site Reliability Engineering

Encryption And Decryption Jean s Blog

Chirag s Blog Difference Between Symmetric And Asymmetric Key

Symmetric Key Encryption Complete Guide To Symmetric Key Encryption

What Is Cryptography In Security What Are The Different Types Of
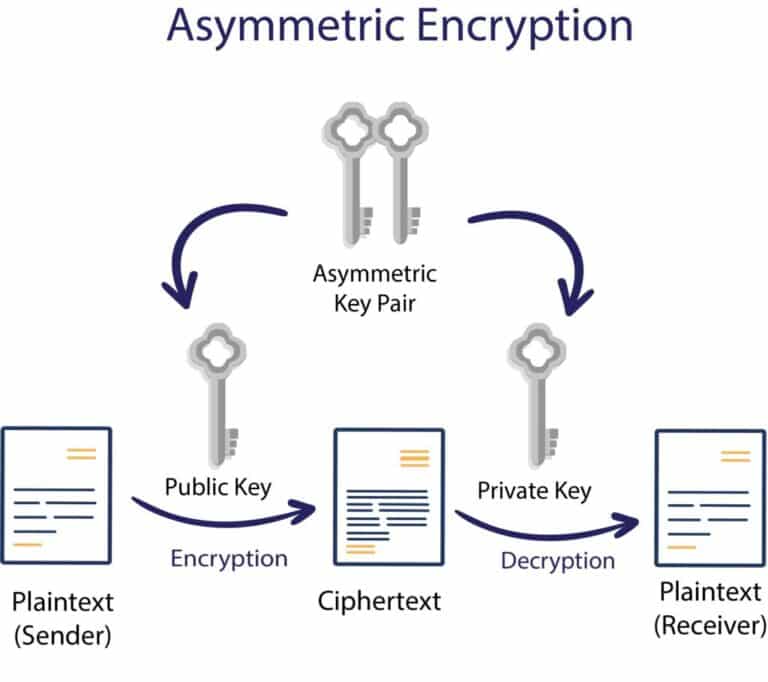
Asymmetric Encryption What It Is Why Your Security Depends On It

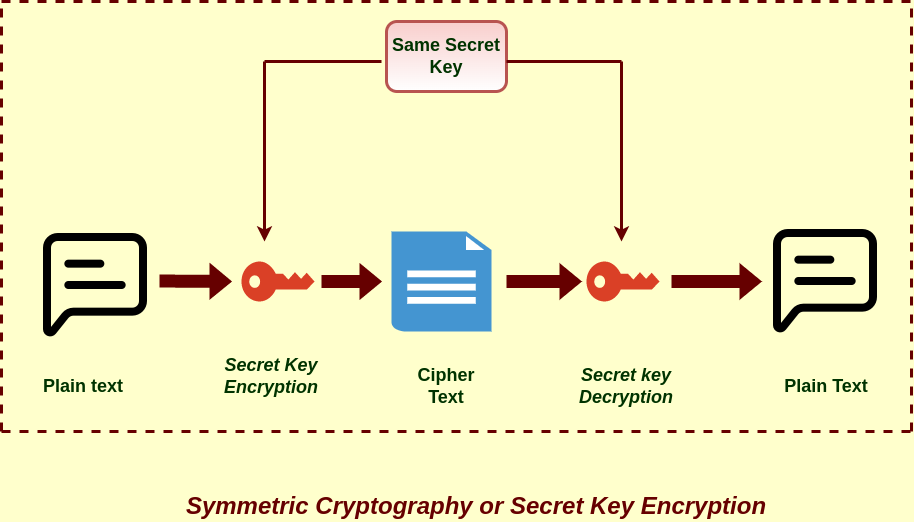
https://www.bne.es › es
La Biblioteca ofrece un servicio de reproducci n de fondos con el objetivo de facilitar el acceso a la informaci n

https://www.ehu.eus › es › web › biblioteka
Crimina et delicta en el derecho romano y su recepci n Exposici n bibliogr fica en la Biblioteca del Campus de Gipuzkoa abril mayo de 2025
La Biblioteca ofrece un servicio de reproducci n de fondos con el objetivo de facilitar el acceso a la informaci n
Crimina et delicta en el derecho romano y su recepci n Exposici n bibliogr fica en la Biblioteca del Campus de Gipuzkoa abril mayo de 2025

Symmetric Key Encryption Complete Guide To Symmetric Key Encryption

Encryption And Decryption Jean s Blog

What Is Cryptography In Security What Are The Different Types Of

Asymmetric Encryption What It Is Why Your Security Depends On It

Asymmetric Encryption How Asymmetric Encryption Works
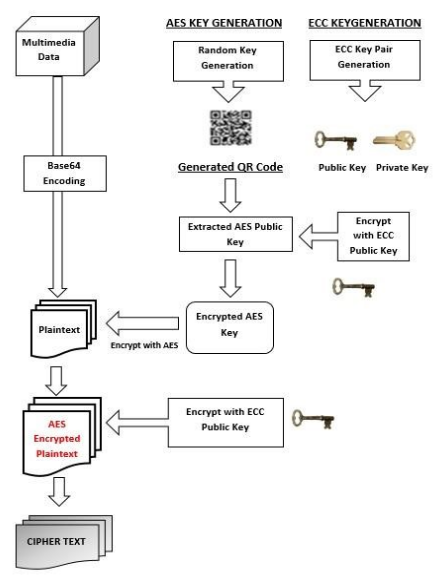
Hybrid Cryptography Implementation Of A System Capable Of Encryption

Hybrid Cryptography Implementation Of A System Capable Of Encryption
CoinStats What Is Zero Knowledge Encryption