In this age of technology, where screens rule our lives yet the appeal of tangible, printed materials hasn't diminished. Be it for educational use and creative work, or just adding some personal flair to your home, printables for free are now an essential resource. This article will dive in the world of "Symmetric Encryption In Information Security," exploring what they are, where to locate them, and how they can be used to enhance different aspects of your daily life.
Get Latest Symmetric Encryption In Information Security Below
Symmetric Encryption In Information Security
Symmetric Encryption In Information Security -
Once the bodies in Chapter 1 have been counted out and you ve closed the book the fisherman will call out and say that a storm is coming and tell you to finish your business and get down to
Return of the Obra Dinn The ship won t get hit by the storm until you leave There is an ingame reason for this as well see Soldiers of the Sea part 1 4 Showing 1 4
Printables for free include a vast assortment of printable material that is available online at no cost. These materials come in a variety of types, such as worksheets templates, coloring pages and much more. The appeal of printables for free is in their versatility and accessibility.
More of Symmetric Encryption In Information Security
Concept Of Cryptography In Blockchain

Concept Of Cryptography In Blockchain
Soldiers of the Sea part 1 is the first part of chapter VI in the plot of Return of the Obra Dinn It reveals the fate of topman Huang Li The ship turns around due to the escalating number of
Subreddit for the game Return of the Obra Dinn Members Online No spoilers please I have found all the parts of all chapters and the guy who got me on the boat says
Symmetric Encryption In Information Security have garnered immense popularity because of a number of compelling causes:
-
Cost-Effective: They eliminate the need to buy physical copies or expensive software.
-
Flexible: This allows you to modify printed materials to meet your requirements, whether it's designing invitations to organize your schedule or decorating your home.
-
Educational Use: These Symmetric Encryption In Information Security cater to learners from all ages, making them a vital aid for parents as well as educators.
-
Easy to use: You have instant access the vast array of design and templates is time-saving and saves effort.
Where to Find more Symmetric Encryption In Information Security
Encryption Choices Rsa Vs Aes Explained Prey

Encryption Choices Rsa Vs Aes Explained Prey
Return of the Obra Dinn tripped up about halfway through my investigation when the guy who rowed me out yelled that I had to hurry up because a storm was coming Not to
The storm has started and the boatman tells me that I won t be coming back Without too many spoilers what happens when I leave with him Return of the Obra Dinn
Now that we've ignited your curiosity about Symmetric Encryption In Information Security Let's take a look at where you can locate these hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy offer a vast selection of Symmetric Encryption In Information Security to suit a variety of purposes.
- Explore categories such as the home, decor, the arts, and more.
2. Educational Platforms
- Educational websites and forums typically provide free printable worksheets for flashcards, lessons, and worksheets. tools.
- It is ideal for teachers, parents and students in need of additional sources.
3. Creative Blogs
- Many bloggers share their imaginative designs and templates free of charge.
- The blogs covered cover a wide spectrum of interests, starting from DIY projects to party planning.
Maximizing Symmetric Encryption In Information Security
Here are some creative ways how you could make the most of printables that are free:
1. Home Decor
- Print and frame gorgeous images, quotes, or even seasonal decorations to decorate your living spaces.
2. Education
- Print worksheets that are free to enhance learning at home as well as in the class.
3. Event Planning
- Design invitations, banners and decorations for special occasions such as weddings and birthdays.
4. Organization
- Stay organized with printable calendars with to-do lists, planners, and meal planners.
Conclusion
Symmetric Encryption In Information Security are a treasure trove of innovative and useful resources which cater to a wide range of needs and interests. Their accessibility and versatility make these printables a useful addition to both personal and professional life. Explore the vast array of Symmetric Encryption In Information Security today and unlock new possibilities!
Frequently Asked Questions (FAQs)
-
Are Symmetric Encryption In Information Security truly available for download?
- Yes you can! You can print and download the resources for free.
-
Can I download free printables for commercial use?
- It's determined by the specific rules of usage. Make sure you read the guidelines for the creator prior to printing printables for commercial projects.
-
Do you have any copyright issues in printables that are free?
- Certain printables may be subject to restrictions on their use. Be sure to check the conditions and terms of use provided by the designer.
-
How do I print printables for free?
- You can print them at home with a printer or visit a local print shop to purchase more high-quality prints.
-
What software do I need in order to open printables at no cost?
- Many printables are offered in the PDF format, and is open with no cost software, such as Adobe Reader.
What Is Zero Knowledge Encryption Chainlink Blog
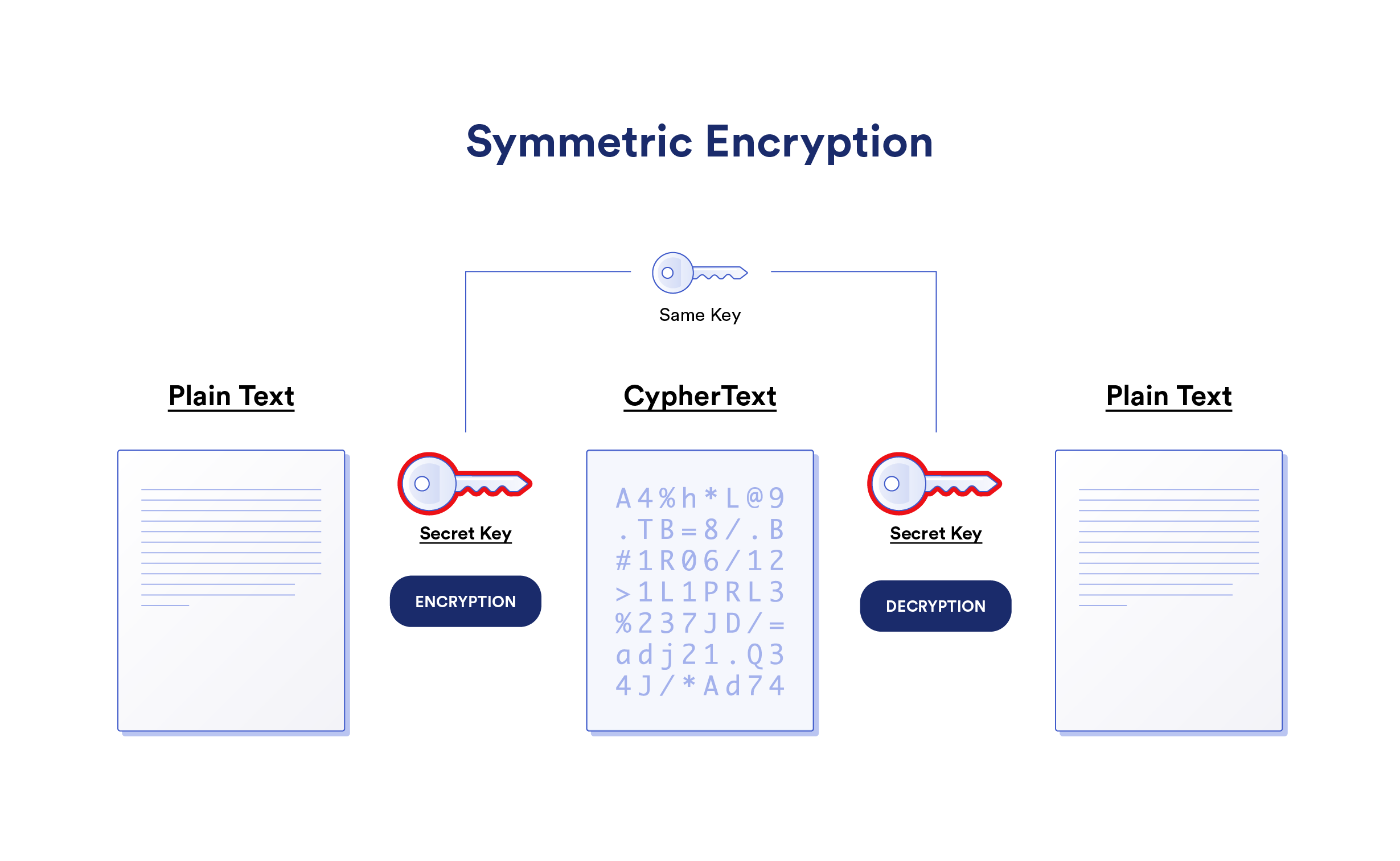
What Is Symmetric Key Cryptography Encryption Security Wiki

Check more sample of Symmetric Encryption In Information Security below
Symmetric Vs Asymmetric Encryption The World Financial Review
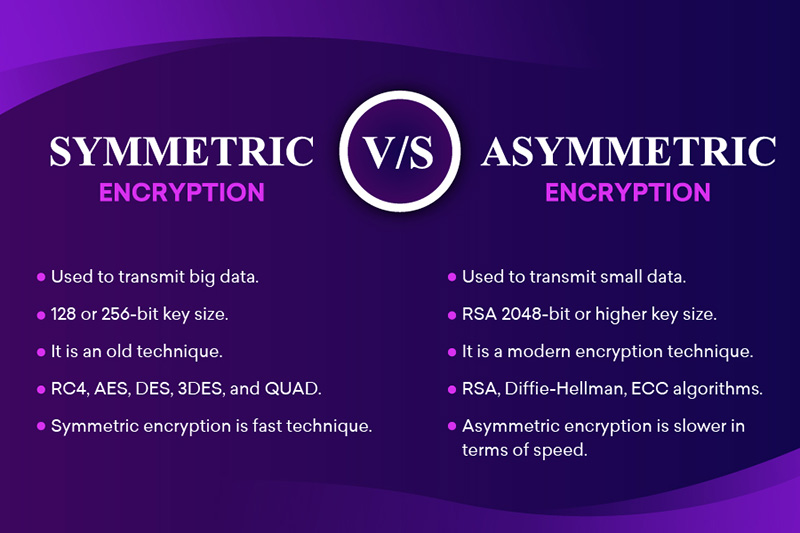
The Complete Cryptography Guide Asymmetric Vs Symmetric Encryption

Encryption Decryption What Are These Ideatebox

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Asymmetric Encryption How Asymmetric Encryption Works

Symmetric Key Encryption Complete Guide To Symmetric Key Encryption

https://steamcommunity.com › app › discussions
Return of the Obra Dinn The ship won t get hit by the storm until you leave There is an ingame reason for this as well see Soldiers of the Sea part 1 4 Showing 1 4

https://gamefaqs.gamespot.com › switch › faqs › ...
Also note the bones on the deck After a moment of exploration your boatman will call you down to pick up your luggage Climb down the same ladder and open your case In it
Return of the Obra Dinn The ship won t get hit by the storm until you leave There is an ingame reason for this as well see Soldiers of the Sea part 1 4 Showing 1 4
Also note the bones on the deck After a moment of exploration your boatman will call you down to pick up your luggage Climb down the same ladder and open your case In it

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

The Complete Cryptography Guide Asymmetric Vs Symmetric Encryption

Asymmetric Encryption How Asymmetric Encryption Works

Symmetric Key Encryption Complete Guide To Symmetric Key Encryption
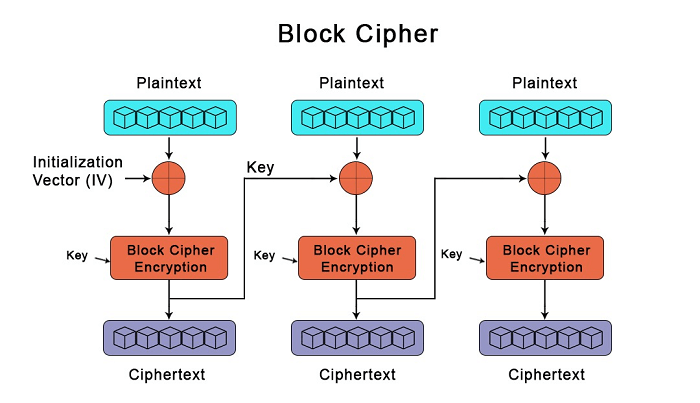
What Is Ciphertext In Network Cybersecurity Sangfor Glossary
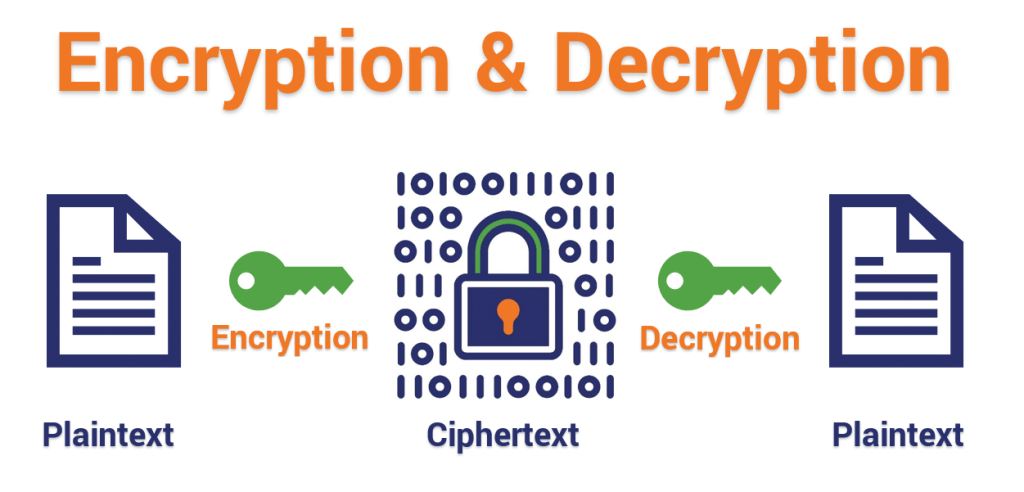
Encryption And Decryption In C Encryption Is The Process Of By

Encryption And Decryption In C Encryption Is The Process Of By

Symmetric Encryption Algorithms Live Long Encrypt Security Boulevard