In this digital age, where screens have become the dominant feature of our lives yet the appeal of tangible printed items hasn't gone away. If it's to aid in education, creative projects, or just adding personal touches to your home, printables for free are now a useful source. Through this post, we'll dive deep into the realm of "Symmetric Key Ciphers In Cryptography And Network Security," exploring their purpose, where to get them, as well as how they can be used to enhance different aspects of your daily life.
Get Latest Symmetric Key Ciphers In Cryptography And Network Security Below
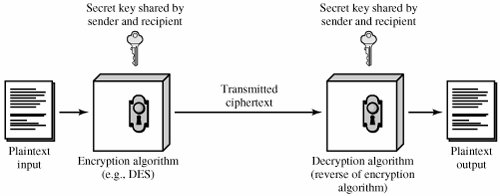
Symmetric Key Ciphers In Cryptography And Network Security
Symmetric Key Ciphers In Cryptography And Network Security - Symmetric Key Ciphers In Cryptography And Network Security, Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security, What Is Symmetric Key Cryptography, How Many Keys Are Used In Symmetric Cryptography, What Is The Difference Between Symmetric Key Cryptography And Asymmetric Key Cryptography, Symmetric Key Cryptography Techniques, Types Of Symmetric Key Cryptography
Einfache sichere und komfortable E Mail Kommunikation im E Mail Center der Telekom f r Ihr E Mail Postfach t online de
Alle aktuellen News zum Thema Deutsche Telekom sowie Bilder Videos und Infos zu Deutsche Telekom bei t online
Symmetric Key Ciphers In Cryptography And Network Security offer a wide assortment of printable, downloadable resources available online for download at no cost. These resources come in various forms, like worksheets templates, coloring pages and many more. The great thing about Symmetric Key Ciphers In Cryptography And Network Security is their flexibility and accessibility.
More of Symmetric Key Ciphers In Cryptography And Network Security
Cryptography Definition In Mathematics

Cryptography Definition In Mathematics
Um sich in Ihren E Mail Posteingang einzuloggen rufen Sie die T Online Startseite unter www t online de auf Klicken Sie oben rechts auf die Schaltfl che E Mail
Aktuelle News aus Politik Sport Unterhaltung Wirtschaft Finanzen Ratgeber Leben Gesundheit und Heim Garten E Mail und Shopping bei t online de
Symmetric Key Ciphers In Cryptography And Network Security have risen to immense popularity due to a myriad of compelling factors:
-
Cost-Efficiency: They eliminate the requirement of buying physical copies or expensive software.
-
customization The Customization feature lets you tailor printed materials to meet your requirements for invitations, whether that's creating them for your guests, organizing your schedule or decorating your home.
-
Educational value: Educational printables that can be downloaded for free provide for students of all ages, making them a useful resource for educators and parents.
-
An easy way to access HTML0: immediate access many designs and templates is time-saving and saves effort.
Where to Find more Symmetric Key Ciphers In Cryptography And Network Security
Beginners Guide To Cryptography Quick

Beginners Guide To Cryptography Quick
Das Postfach f r Ihre T Online Mail behalten Sie ber die kleine Box mit dem T Online E Mail Login am oberen rechten Bildschirm von www t online de stets im Blick Das geht ohne
Jetzt mit noch mehr Datenvolumen LTE Max und Telekom HotSpot Flat Vertragsverl ngerung Festnetz Jetzt auf Highspeed upgraden schneller surfen und 60 Gutschrift sichern
After we've peaked your curiosity about Symmetric Key Ciphers In Cryptography And Network Security Let's take a look at where you can discover these hidden gems:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide a variety of Symmetric Key Ciphers In Cryptography And Network Security to suit a variety of goals.
- Explore categories such as decorating your home, education, the arts, and more.
2. Educational Platforms
- Educational websites and forums often offer worksheets with printables that are free including flashcards, learning materials.
- Ideal for parents, teachers and students in need of additional sources.
3. Creative Blogs
- Many bloggers are willing to share their original designs and templates at no cost.
- The blogs covered cover a wide selection of subjects, including DIY projects to party planning.
Maximizing Symmetric Key Ciphers In Cryptography And Network Security
Here are some inventive ways in order to maximize the use use of Symmetric Key Ciphers In Cryptography And Network Security:
1. Home Decor
- Print and frame stunning artwork, quotes, or seasonal decorations to adorn your living spaces.
2. Education
- Use printable worksheets for free for reinforcement of learning at home as well as in the class.
3. Event Planning
- Make invitations, banners and decorations for special events like birthdays and weddings.
4. Organization
- Keep your calendars organized by printing printable calendars, to-do lists, and meal planners.
Conclusion
Symmetric Key Ciphers In Cryptography And Network Security are an abundance of creative and practical resources designed to meet a range of needs and interest. Their availability and versatility make them a valuable addition to both personal and professional life. Explore the endless world of Symmetric Key Ciphers In Cryptography And Network Security to explore new possibilities!
Frequently Asked Questions (FAQs)
-
Do printables with no cost really cost-free?
- Yes you can! You can download and print these resources at no cost.
-
Can I make use of free printables for commercial use?
- It is contingent on the specific conditions of use. Always review the terms of use for the creator prior to printing printables for commercial projects.
-
Do you have any copyright issues in printables that are free?
- Certain printables may be subject to restrictions in use. Check the conditions and terms of use provided by the creator.
-
How do I print Symmetric Key Ciphers In Cryptography And Network Security?
- You can print them at home using the printer, or go to a local print shop for better quality prints.
-
What program will I need to access printables for free?
- A majority of printed materials are in the PDF format, and is open with no cost programs like Adobe Reader.
What Is Symmetric Key Cryptography Encryption Security Wiki

What Is Symmetric Key Cryptography Elements Of Symmetric Key

Check more sample of Symmetric Key Ciphers In Cryptography And Network Security below
Symmetric Ciphers Brilliant Math Science Wiki
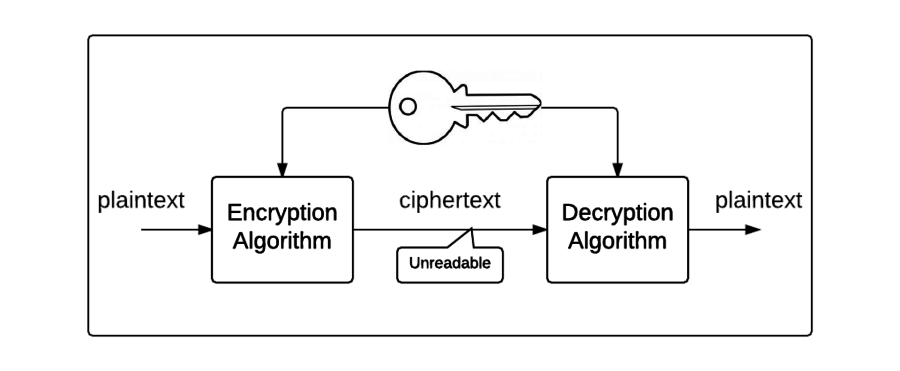
Encryption And Decryption Jean s Blog

Difference Between Symmetric And Asymmetric Encryption Symmetric Key

Symmetric Vs Asymmetric Encryption Differences Explained

Chirag s Blog Difference Between Symmetric And Asymmetric Key

Public Key Cryptography Decoded What Is Cryptography Ntirawen


https://www.t-online.de › themen › deutsche-telekom-ag
Alle aktuellen News zum Thema Deutsche Telekom sowie Bilder Videos und Infos zu Deutsche Telekom bei t online

https://www.t-online.de › finanzen › allfinanz
Aktuelle News aus Politik Sport Unterhaltung Wirtschaft Finanzen Ratgeber Leben Gesundheit und Heim Garten E Mail und Shopping bei t online de
Alle aktuellen News zum Thema Deutsche Telekom sowie Bilder Videos und Infos zu Deutsche Telekom bei t online
Aktuelle News aus Politik Sport Unterhaltung Wirtschaft Finanzen Ratgeber Leben Gesundheit und Heim Garten E Mail und Shopping bei t online de

Symmetric Vs Asymmetric Encryption Differences Explained

Encryption And Decryption Jean s Blog

Chirag s Blog Difference Between Symmetric And Asymmetric Key

Public Key Cryptography Decoded What Is Cryptography Ntirawen
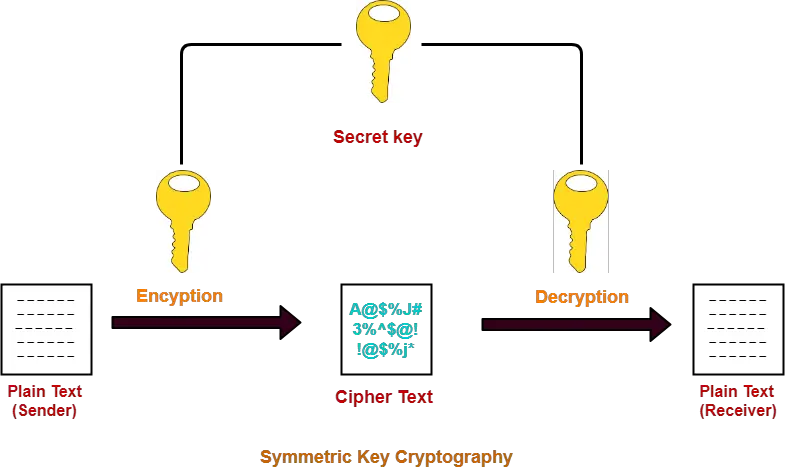
Symmetric Key Cryptography Cryptography Techniques Gate Vidyalay

What Is Asymmetric Encryption Babypips

What Is Asymmetric Encryption Babypips

Types Of Cryptography Download Scientific Diagram