In this age of technology, with screens dominating our lives and our lives are dominated by screens, the appeal of tangible printed materials hasn't faded away. It doesn't matter if it's for educational reasons as well as creative projects or simply adding an individual touch to your home, printables for free have become a valuable resource. With this guide, you'll take a dive through the vast world of "Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security," exploring what they are, how to find them and how they can add value to various aspects of your daily life.
Get Latest Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security Below

Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security
Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security - Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security
Introduction Introduction 5
Introduction Introduction main body conclusion
Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security encompass a wide assortment of printable content that can be downloaded from the internet at no cost. These printables come in different forms, including worksheets, coloring pages, templates and much more. The appeal of printables for free is in their versatility and accessibility.
More of Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security
Concept Of Cryptography In Blockchain

Concept Of Cryptography In Blockchain
Why An Introduction Is Needed Introduction Discussion Conclusion
2011 1
Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security have risen to immense popularity for several compelling reasons:
-
Cost-Effective: They eliminate the need to purchase physical copies of the software or expensive hardware.
-
Personalization We can customize printables to your specific needs, whether it's designing invitations planning your schedule or even decorating your house.
-
Educational Value: The free educational worksheets are designed to appeal to students of all ages, making them a valuable instrument for parents and teachers.
-
Easy to use: The instant accessibility to a variety of designs and templates reduces time and effort.
Where to Find more Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security
An Exploration Of Symmetric Key Cryptography History Working And

An Exploration Of Symmetric Key Cryptography History Working And
Introduction Introduction 1
Introduction AI AI
If we've already piqued your interest in Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security Let's see where you can locate these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy have a large selection in Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security for different uses.
- Explore categories like decorations for the home, education and the arts, and more.
2. Educational Platforms
- Educational websites and forums usually offer worksheets with printables that are free along with flashcards, as well as other learning materials.
- Ideal for teachers, parents or students in search of additional resources.
3. Creative Blogs
- Many bloggers share their imaginative designs with templates and designs for free.
- These blogs cover a broad selection of subjects, including DIY projects to party planning.
Maximizing Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security
Here are some inventive ways in order to maximize the use use of printables for free:
1. Home Decor
- Print and frame stunning artwork, quotes or seasonal decorations that will adorn your living areas.
2. Education
- Use free printable worksheets for teaching at-home as well as in the class.
3. Event Planning
- Design invitations, banners, and decorations for special occasions such as weddings or birthdays.
4. Organization
- Keep track of your schedule with printable calendars checklists for tasks, as well as meal planners.
Conclusion
Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security are a treasure trove of innovative and useful resources for a variety of needs and preferences. Their access and versatility makes them an essential part of any professional or personal life. Explore the vast world of Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security today and open up new possibilities!
Frequently Asked Questions (FAQs)
-
Are Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security really free?
- Yes you can! You can download and print these free resources for no cost.
-
Do I have the right to use free templates for commercial use?
- It's all dependent on the rules of usage. Always verify the guidelines of the creator prior to using the printables in commercial projects.
-
Do you have any copyright violations with printables that are free?
- Certain printables may be subject to restrictions in their usage. Check the terms and condition of use as provided by the designer.
-
How do I print printables for free?
- Print them at home using your printer or visit any local print store for high-quality prints.
-
What software do I need to open printables free of charge?
- The majority of printables are as PDF files, which can be opened using free programs like Adobe Reader.
Cryptography Definition In Mathematics

The Ultimate Guide To Symmetric Encryption
Check more sample of Introduction To Modern Symmetric Key Ciphers In Cryptography And Network Security below
Symmetric Encryption Key Cryptography Introduction To Modern Symmetric

What Is Zero Knowledge Encryption Chainlink Blog
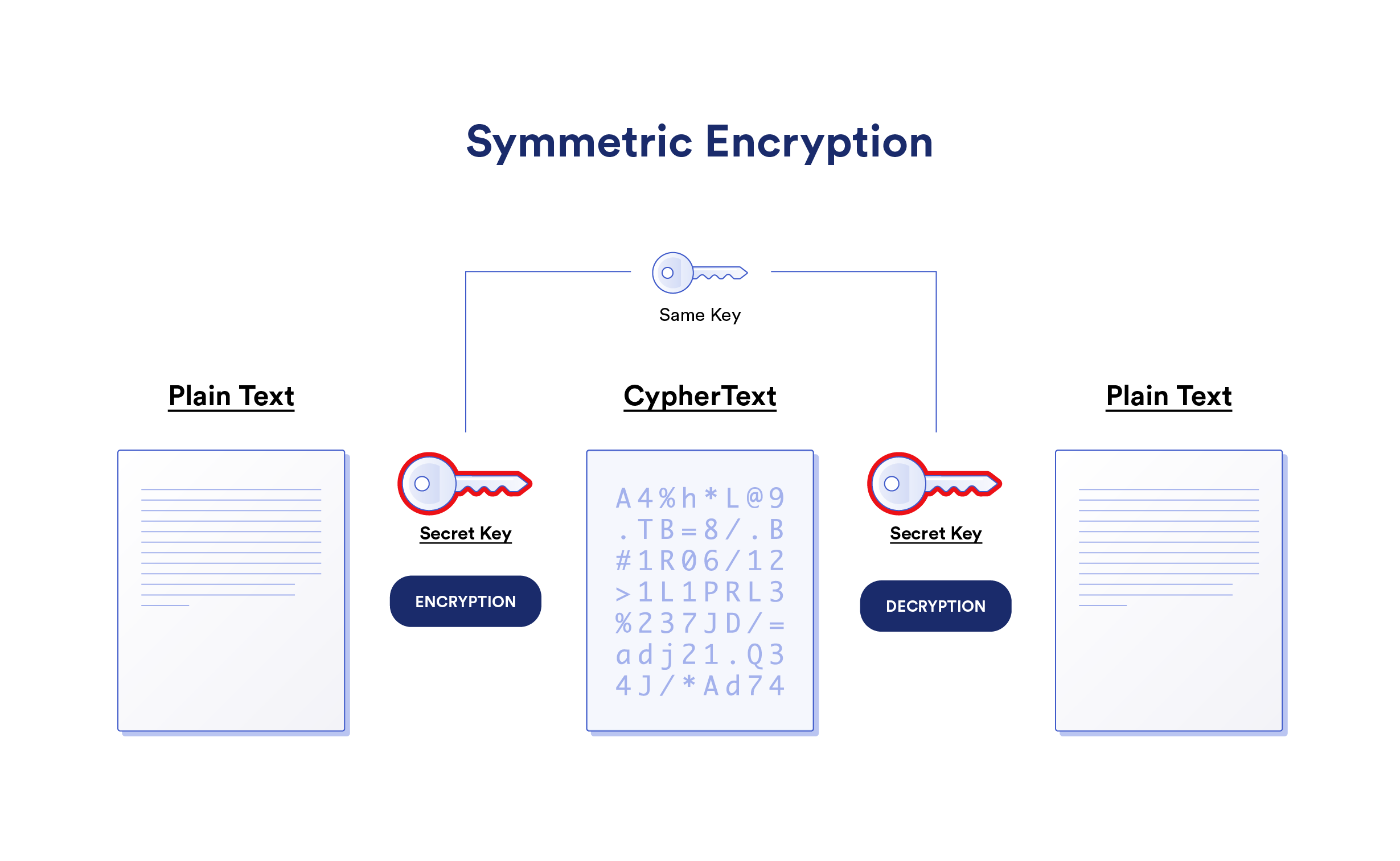
What Is Symmetric Key Cryptography Encryption Security Wiki

What Is Symmetric Key Cryptography Elements Of Symmetric Key

Difference Between Symmetric And Asymmetric Encryption Symmetric Key

Section 2 1 Symmetric Cipher Model Cryptography And Network Security
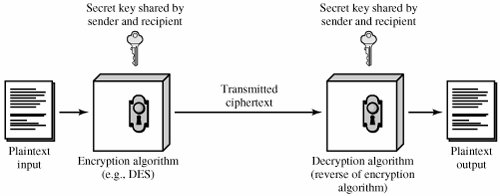

https://www.zhihu.com › question
Introduction Introduction main body conclusion

Introduction Introduction main body conclusion
Introduction background on the field

What Is Symmetric Key Cryptography Elements Of Symmetric Key

What Is Zero Knowledge Encryption Chainlink Blog

Difference Between Symmetric And Asymmetric Encryption Symmetric Key

Section 2 1 Symmetric Cipher Model Cryptography And Network Security

Symmetric And Asymmetric Key Cryptography The Key Differences Explained
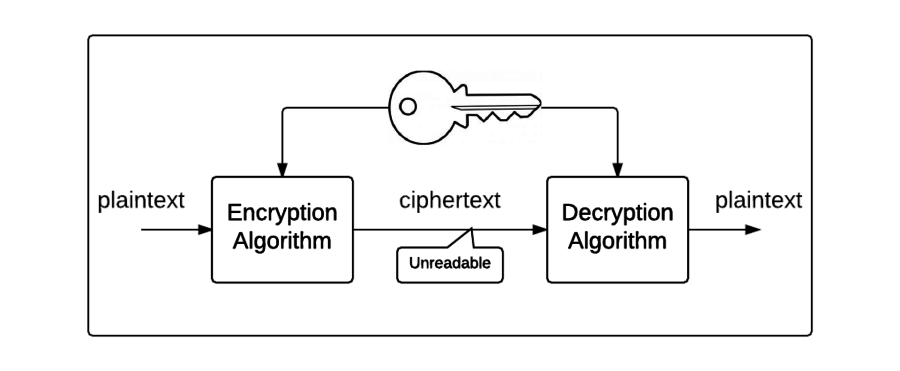
Symmetric Ciphers Brilliant Math Science Wiki

Symmetric Ciphers Brilliant Math Science Wiki
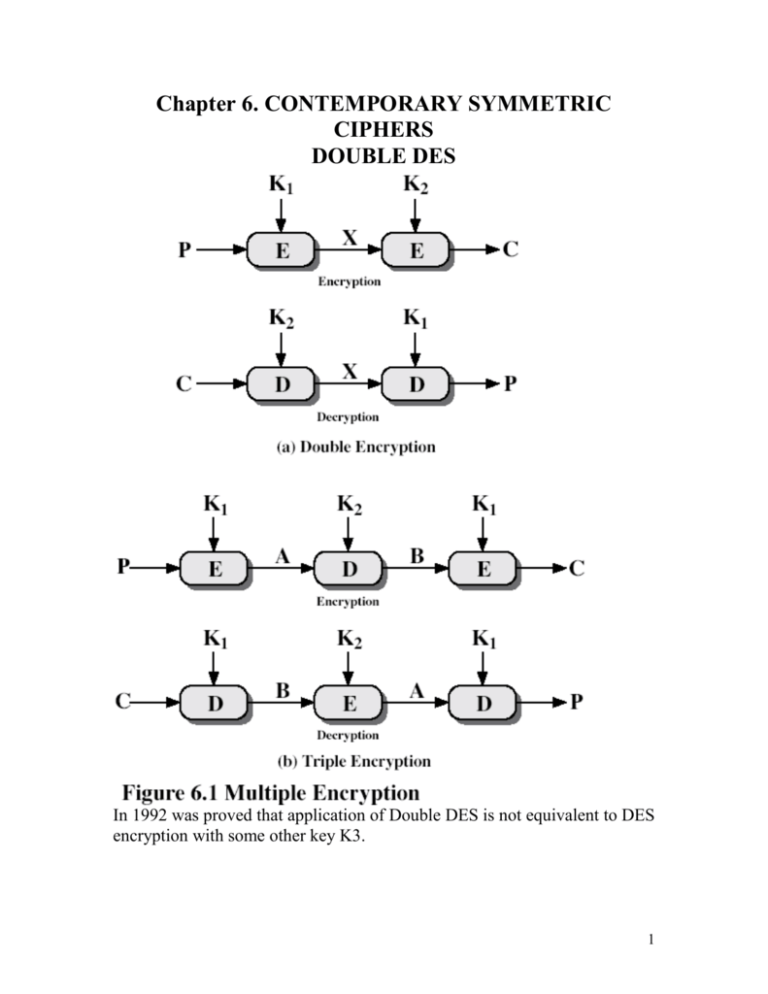
Chapter 6 Modern Symmetric Ciphers