Today, where screens have become the dominant feature of our lives and our lives are dominated by screens, the appeal of tangible printed materials isn't diminishing. In the case of educational materials in creative or artistic projects, or simply to add some personal flair to your home, printables for free have become a valuable resource. With this guide, you'll dive into the sphere of "Network Security Architecture Best Practices," exploring what they are, how they can be found, and ways they can help you improve many aspects of your daily life.
Get Latest Network Security Architecture Best Practices Below

Network Security Architecture Best Practices
Network Security Architecture Best Practices - Network Security Architecture Best Practices, Cyber Security Architecture Best Practices, Web Application Security Architecture Best Practices, Network Security Best Practices, Security Architecture Best Practices, Network Architecture Best Practices, Network Security Best Practices Checklist
LAN A Local Area Network LAN is a network that covers a small area such as an office or a home LANs are typically used to connect computers and other devices within a
A computer network is a group of interconnected nodes or computing devices that exchange data and resources with each other A network connection between these devices
Network Security Architecture Best Practices offer a wide assortment of printable, downloadable material that is available online at no cost. These printables come in different designs, including worksheets templates, coloring pages, and many more. The value of Network Security Architecture Best Practices is their versatility and accessibility.
More of Network Security Architecture Best Practices
Network Topology Best Practices FortiDeceptor 4 0 0 Fortinet

Network Topology Best Practices FortiDeceptor 4 0 0 Fortinet
A network consists of multiple devices that communicate with one another It can be as small as two computers or as large as billions of devices While a traditional network is
List the different types of network devices used in a network Describe network communication principles like TCP IP DNS and ports Describe how these core components map to Azure
Network Security Architecture Best Practices have gained immense popularity due to a myriad of compelling factors:
-
Cost-Efficiency: They eliminate the requirement to purchase physical copies or expensive software.
-
The ability to customize: We can customize printables to fit your particular needs for invitations, whether that's creating them to organize your schedule or decorating your home.
-
Educational Value: Educational printables that can be downloaded for free can be used by students of all ages. This makes these printables a powerful device for teachers and parents.
-
Accessibility: immediate access a myriad of designs as well as templates is time-saving and saves effort.
Where to Find more Network Security Architecture Best Practices
Splunk Splunk Architecture Will s Ideas
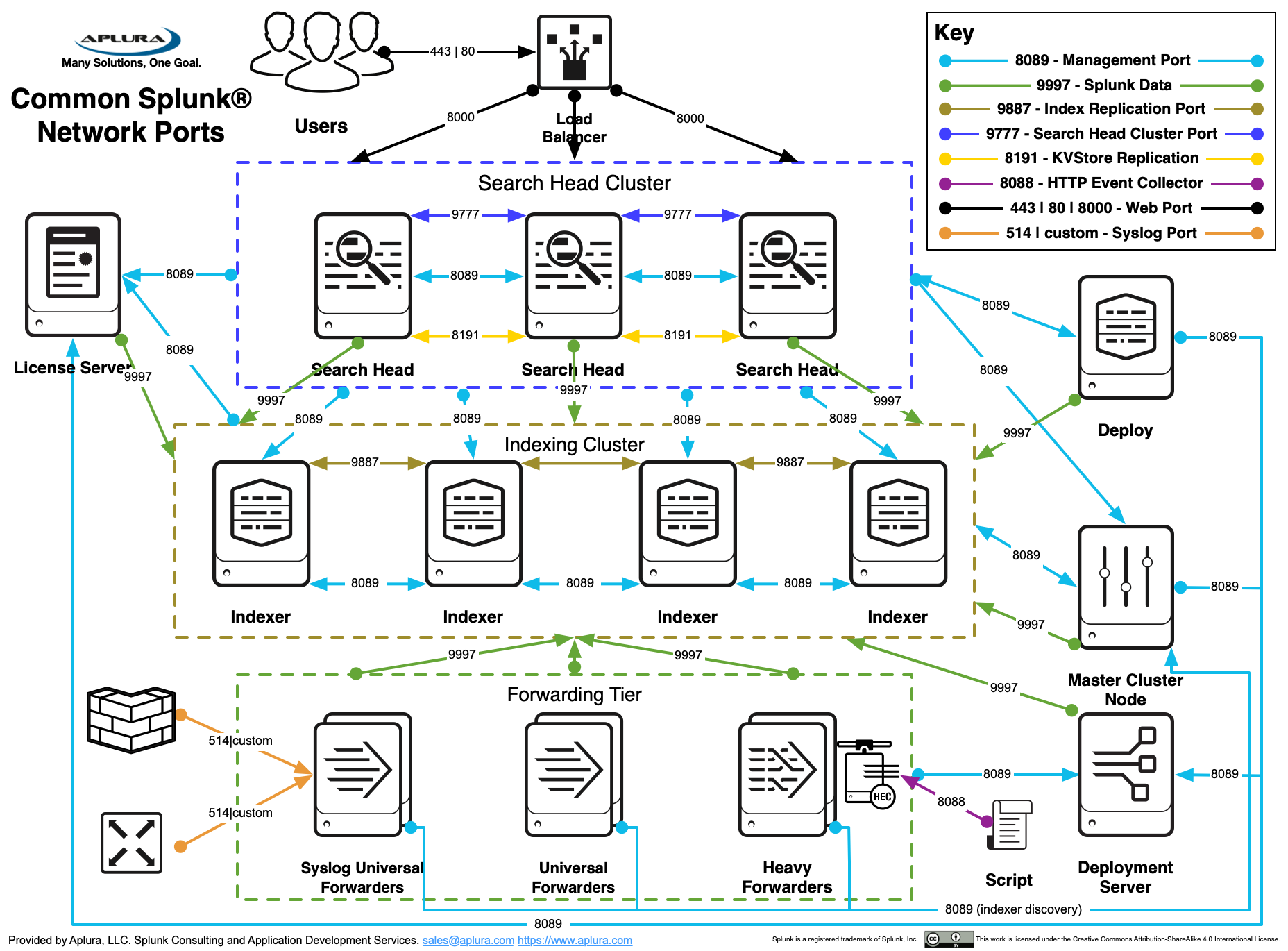
Splunk Splunk Architecture Will s Ideas
Switches routers and wireless access points perform very different functions in a network Switches Switches are the foundation of most business networks A switch acts as a
A computer network is made up of four essential components These components are End devices Media Protocols and Networking devices Let s discuss these components
We hope we've stimulated your curiosity about Network Security Architecture Best Practices Let's take a look at where the hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy offer a vast selection of Network Security Architecture Best Practices suitable for many motives.
- Explore categories such as the home, decor, organizational, and arts and crafts.
2. Educational Platforms
- Forums and educational websites often offer free worksheets and worksheets for printing including flashcards, learning materials.
- It is ideal for teachers, parents and students looking for extra sources.
3. Creative Blogs
- Many bloggers post their original designs and templates for free.
- The blogs covered cover a wide range of interests, all the way from DIY projects to party planning.
Maximizing Network Security Architecture Best Practices
Here are some innovative ways that you can make use of Network Security Architecture Best Practices:
1. Home Decor
- Print and frame beautiful artwork, quotes, or other seasonal decorations to fill your living areas.
2. Education
- Utilize free printable worksheets for teaching at-home or in the classroom.
3. Event Planning
- Make invitations, banners and decorations for special events such as weddings and birthdays.
4. Organization
- Be organized by using printable calendars, to-do lists, and meal planners.
Conclusion
Network Security Architecture Best Practices are an abundance of creative and practical resources that can meet the needs of a variety of people and interests. Their accessibility and versatility make these printables a useful addition to each day life. Explore the many options of Network Security Architecture Best Practices now and unlock new possibilities!
Frequently Asked Questions (FAQs)
-
Are Network Security Architecture Best Practices really gratis?
- Yes you can! You can download and print these files for free.
-
Can I use the free printing templates for commercial purposes?
- It's determined by the specific rules of usage. Always verify the guidelines of the creator before utilizing their templates for commercial projects.
-
Do you have any copyright violations with Network Security Architecture Best Practices?
- Some printables could have limitations concerning their use. Be sure to read these terms and conditions as set out by the designer.
-
How do I print Network Security Architecture Best Practices?
- Print them at home with the printer, or go to the local print shop for higher quality prints.
-
What software will I need to access printables that are free?
- The majority of printables are in PDF format, which can be opened with free software like Adobe Reader.
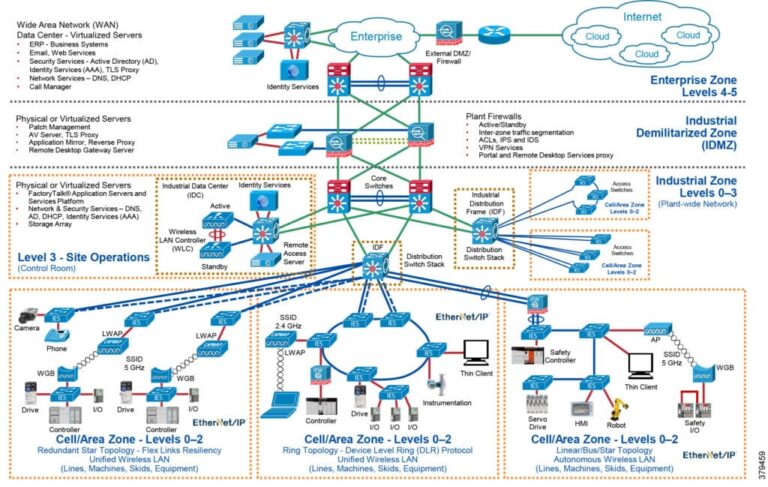
Industrial Network Design Best Practices Agilix Solutions
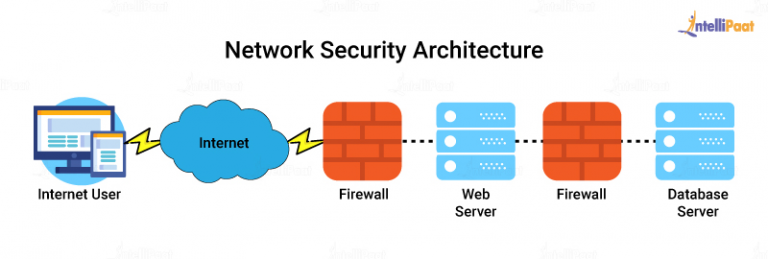
What Is Network Security Definition Types Attacks And Tools Images
Check more sample of Network Security Architecture Best Practices below
Best Practices For Network Segmentation Network Security Protocols

Top Security Architecture Best Practices For Maximum Protection Dig8ital

Security Architecture
Best Practices For Manufacturing OT Security AWS For Industries

Implement A Secure Hybrid Network Azure Architecture Center
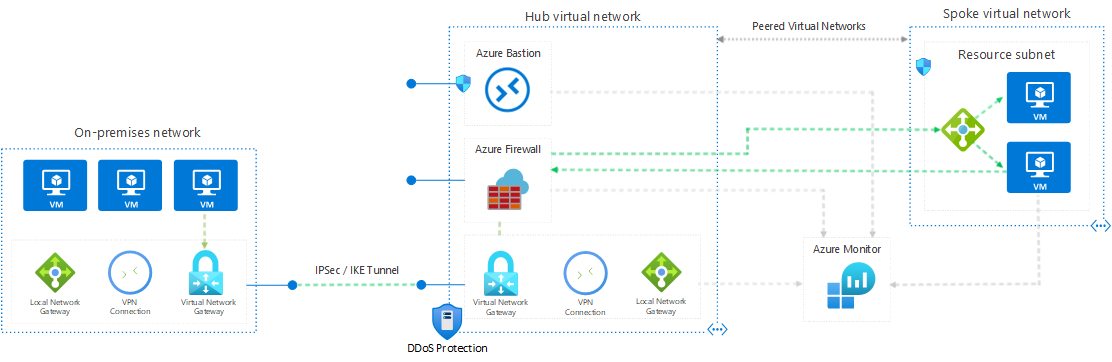
VPC And Subnet Considerations EKS Best Practices Guides


https://www.techtarget.com › searchnetworking › definition › network
A computer network is a group of interconnected nodes or computing devices that exchange data and resources with each other A network connection between these devices

https://www.ionos.com › ... › know-how › what-is-a-network
In information technology a network is defined as the connection of at least two computer systems either by a cable or a wireless connection The simplest network is a
A computer network is a group of interconnected nodes or computing devices that exchange data and resources with each other A network connection between these devices
In information technology a network is defined as the connection of at least two computer systems either by a cable or a wireless connection The simplest network is a

Best Practices For Manufacturing OT Security AWS For Industries

Top Security Architecture Best Practices For Maximum Protection Dig8ital

Implement A Secure Hybrid Network Azure Architecture Center

VPC And Subnet Considerations EKS Best Practices Guides
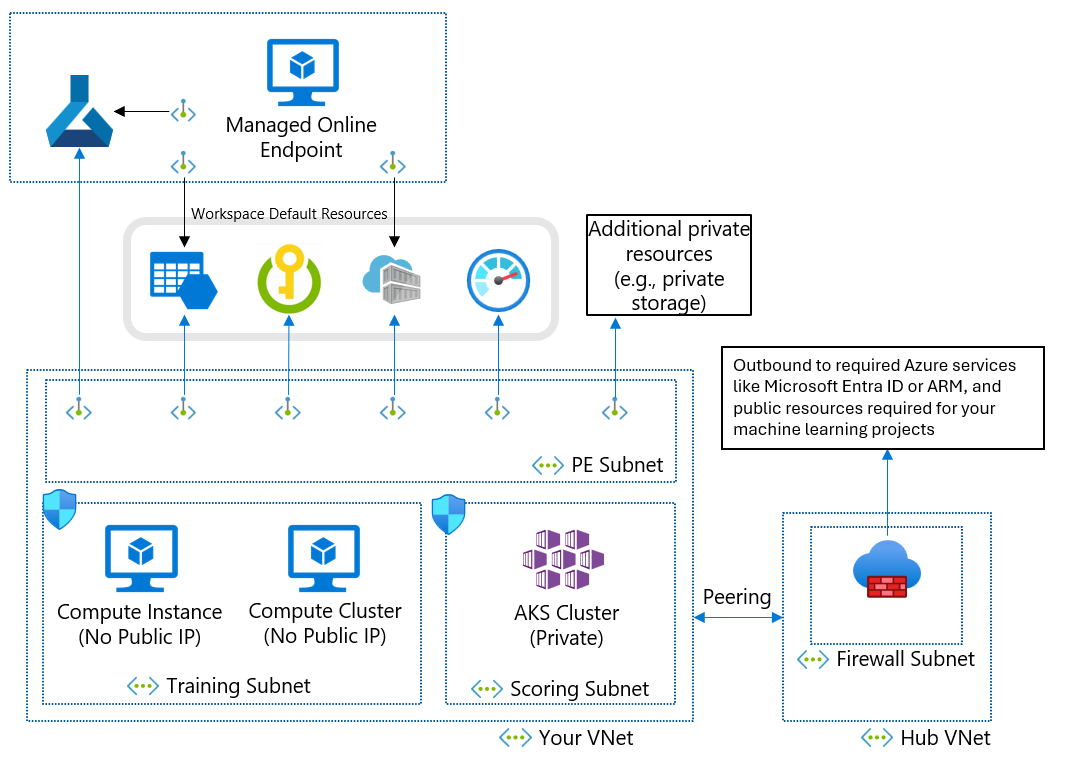
Machine Learning Enterprise Security Cloud Adoption Framework

DMZ Architecture And Security Strategy Best Practices

DMZ Architecture And Security Strategy Best Practices

Introduction To Cybersecurity Fundamentals Introduction To Network
