In the age of digital, where screens dominate our lives and the appeal of physical, printed materials hasn't diminished. If it's to aid in education in creative or artistic projects, or simply adding a personal touch to your home, printables for free are now an essential resource. In this article, we'll take a dive into the world "Cyber Security Architecture Best Practices," exploring the benefits of them, where you can find them, and the ways that they can benefit different aspects of your daily life.
Get Latest Cyber Security Architecture Best Practices Below

Cyber Security Architecture Best Practices
Cyber Security Architecture Best Practices -
What is Cybersecurity Read about cyber security today learn about the top known cyber attacks and find out how to protect your home or business network from cyber threats
Cyber is a prefix derived from cybernetic used in terms relating to computers technology networks including Internet and others Cyber may also refer to Computers
The Cyber Security Architecture Best Practices are a huge collection of printable materials that are accessible online for free cost. These printables come in different designs, including worksheets templates, coloring pages, and more. One of the advantages of Cyber Security Architecture Best Practices is their versatility and accessibility.
More of Cyber Security Architecture Best Practices
Cyber Security Best Practices Employees Need To Know

Cyber Security Best Practices Employees Need To Know
Users must understand and comply with basic data protection and privacy security principles like choosing strong passwords being wary of attachments in email and backing up data Learn
Cybersecurity protects networks data and systems from cyber threats like malware phishing Learn key types of cyber security best practices for enterprises
Cyber Security Architecture Best Practices have garnered immense popularity due to several compelling reasons:
-
Cost-Efficiency: They eliminate the need to purchase physical copies of the software or expensive hardware.
-
customization This allows you to modify the design to meet your needs whether you're designing invitations, organizing your schedule, or even decorating your house.
-
Educational value: These Cyber Security Architecture Best Practices cater to learners from all ages, making the perfect tool for parents and teachers.
-
Affordability: Quick access to numerous designs and templates saves time and effort.
Where to Find more Cyber Security Architecture Best Practices
Cybersecurity Challenges In Indian Digital Transformation Techchef

Cybersecurity Challenges In Indian Digital Transformation Techchef
Cyber security is the practice of protecting digital devices networks and sensitive data from cyber threats such as hacking malware and phishing attacks It involves a range
Cybersecurity helps protect critical systems data and networks from digital attacks It involves processes best practices and technology solutions to safeguard against unauthorized
We've now piqued your interest in printables for free Let's take a look at where the hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy offer an extensive collection of Cyber Security Architecture Best Practices suitable for many purposes.
- Explore categories such as the home, decor, crafting, and organization.
2. Educational Platforms
- Forums and websites for education often provide worksheets that can be printed for free as well as flashcards and other learning tools.
- Great for parents, teachers as well as students who require additional sources.
3. Creative Blogs
- Many bloggers post their original designs and templates for free.
- The blogs covered cover a wide variety of topics, including DIY projects to party planning.
Maximizing Cyber Security Architecture Best Practices
Here are some fresh ways in order to maximize the use use of Cyber Security Architecture Best Practices:
1. Home Decor
- Print and frame stunning images, quotes, and seasonal decorations, to add a touch of elegance to your living areas.
2. Education
- Print free worksheets to help reinforce your learning at home or in the classroom.
3. Event Planning
- Design invitations for banners, invitations and decorations for special occasions such as weddings and birthdays.
4. Organization
- Stay organized with printable calendars along with lists of tasks, and meal planners.
Conclusion
Cyber Security Architecture Best Practices are a treasure trove of practical and imaginative resources that can meet the needs of a variety of people and desires. Their availability and versatility make them a great addition to your professional and personal life. Explore the vast collection that is Cyber Security Architecture Best Practices today, and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free gratis?
- Yes they are! You can print and download these documents for free.
-
Can I utilize free templates for commercial use?
- It's based on specific usage guidelines. Always verify the guidelines provided by the creator prior to utilizing the templates for commercial projects.
-
Do you have any copyright violations with Cyber Security Architecture Best Practices?
- Certain printables could be restricted on their use. Be sure to review the terms of service and conditions provided by the author.
-
How do I print printables for free?
- Print them at home with the printer, or go to the local print shops for premium prints.
-
What program do I need to open printables at no cost?
- Most printables come in the PDF format, and can be opened using free software such as Adobe Reader.
Top Security Architecture Best Practices For Maximum Protection Dig8ital

10 Cybersecurity Best Practices For Small Businesses

Check more sample of Cyber Security Architecture Best Practices below
The Importance Of Cyber Security How To Stay Safe In Today s Digital

Understanding The 3 Phases Of Cybersecurity Architecture Ardoq

What Is Cybersecurity Mesh Architecture CSMA A1 Technologies

Cyber Security Best Practices That Every Business Should Follow

Blog What Is Cyber Security Architecture FoxTech Cyber
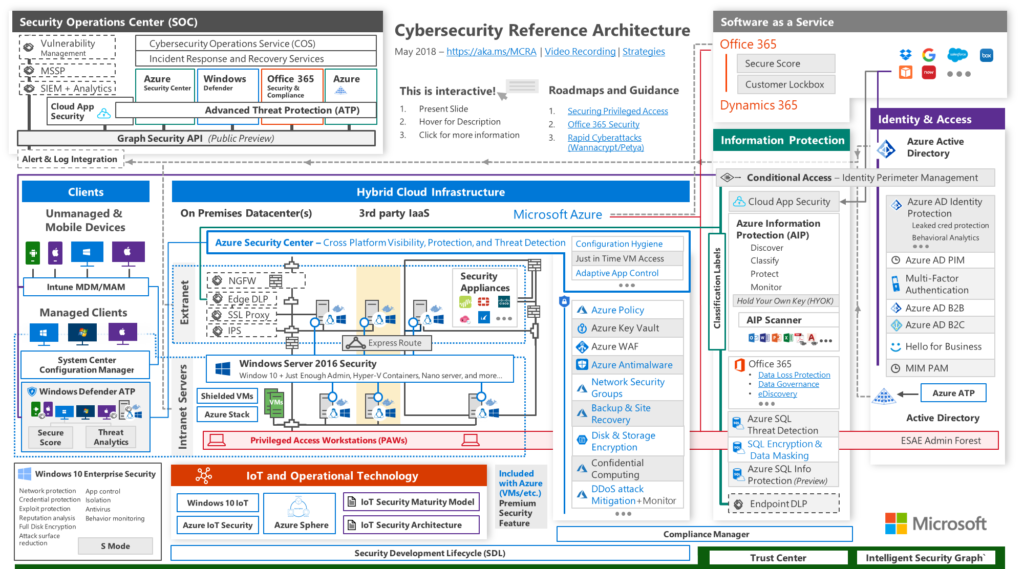
How To Create A Security Architecture Tutorial

https://en.wikipedia.org › wiki › Cyber
Cyber is a prefix derived from cybernetic used in terms relating to computers technology networks including Internet and others Cyber may also refer to Computers

https://dictionary.cambridge.org › dictionary › english › cyber
CYBER definition 1 involving using or relating to computers especially the internet 2 computers especially Learn more
Cyber is a prefix derived from cybernetic used in terms relating to computers technology networks including Internet and others Cyber may also refer to Computers
CYBER definition 1 involving using or relating to computers especially the internet 2 computers especially Learn more

Cyber Security Best Practices That Every Business Should Follow

Understanding The 3 Phases Of Cybersecurity Architecture Ardoq

Blog What Is Cyber Security Architecture FoxTech Cyber

How To Create A Security Architecture Tutorial

Open Source Security Best Practices You Can t Ignore In 2020

What Is Cyber Security Architecture

What Is Cyber Security Architecture

The Importance Of Good Cyber Security Practices Datacentreplus