In this day and age where screens have become the dominant feature of our lives yet the appeal of tangible printed materials hasn't faded away. For educational purposes as well as creative projects or just adding personal touches to your area, Network Security Best Practices have become an invaluable source. The following article is a dive into the world of "Network Security Best Practices," exploring the different types of printables, where you can find them, and the ways that they can benefit different aspects of your life.
Get Latest Network Security Best Practices Below

Network Security Best Practices
Network Security Best Practices - Network Security Best Practices, Network Security Best Practices Checklist, Network Security Best Practices Pdf, Network Security Best Practices Nist, Network Security Best Practices Cisco, Network Security Best Practices Guide, Cyber Security Best Practices, Information Security Best Practices, Web Security Best Practices, Cyber Security Best Practices For Business
Processor security extensions Atomic execution Anti tamper Self encrypting drive Trusted firmware updates Measured boot and attestation Bus encryption Given a scenario apply security solutions for infrastructure management Explain software assurance best practices Explain hardware assurance best practices 2 1 2 2 2 3
Cyber security hiring Tips and best practices Cybersecurity soft skills Career benefits of public speaking CompTIA Data certification Opening doors to new careers Surviving cybersecurity burnout Tips from industry experts How to make a mid career change to cybersecurity 7 top security certifications you should have in 2024
Network Security Best Practices offer a wide range of downloadable, printable material that is available online at no cost. They are available in numerous designs, including worksheets coloring pages, templates and many more. The great thing about Network Security Best Practices is in their variety and accessibility.
More of Network Security Best Practices
4 Security Best Practices For Every Small Business Infographic

4 Security Best Practices For Every Small Business Infographic
Cloud architects network engineers and administrators Those seeking to certify as IAM Level I for CSSP Analyst and CSSP Infrastructure Support role Core cloud concepts and principles Cloud designs and architectures Cloud security controls and configurations Deployment and operational best practices Immediate access to Infosec Skills
PC security issues Best practice procedures for malware removal Common mobile OS and application issues Common mobile OS and application security issues Day 5 Operational Procedures 1102 4 Best practices associated with documentation and support systems Basic change management best practices workstation backup and recovery
Printables for free have gained immense popularity because of a number of compelling causes:
-
Cost-Effective: They eliminate the requirement of buying physical copies of the software or expensive hardware.
-
Individualization It is possible to tailor the templates to meet your individual needs, whether it's designing invitations as well as organizing your calendar, or even decorating your home.
-
Educational Value: Free educational printables cater to learners of all ages, making them a useful tool for teachers and parents.
-
Accessibility: Fast access numerous designs and templates helps save time and effort.
Where to Find more Network Security Best Practices
Five Tips To Improve Your Network Security BizzSecure

Five Tips To Improve Your Network Security BizzSecure
One day you go into work and the nightmare has happened The company has had a data breach This scenario plays out many times each and every day across a
Master the Security domains for the 2024 exam with our in depth guide Learn about each domain s focus areas key concepts and preparation tips
Now that we've ignited your interest in printables for free and other printables, let's discover where you can locate these hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a variety of printables that are free for a variety of goals.
- Explore categories such as home decor, education, organizational, and arts and crafts.
2. Educational Platforms
- Educational websites and forums frequently provide free printable worksheets Flashcards, worksheets, and other educational materials.
- It is ideal for teachers, parents, and students seeking supplemental sources.
3. Creative Blogs
- Many bloggers provide their inventive designs and templates, which are free.
- These blogs cover a broad array of topics, ranging everything from DIY projects to planning a party.
Maximizing Network Security Best Practices
Here are some unique ways how you could make the most of printables for free:
1. Home Decor
- Print and frame gorgeous artwork, quotes, or seasonal decorations that will adorn your living areas.
2. Education
- Use free printable worksheets to enhance your learning at home either in the schoolroom or at home.
3. Event Planning
- Design invitations and banners and decorations for special events like birthdays and weddings.
4. Organization
- Keep your calendars organized by printing printable calendars with to-do lists, planners, and meal planners.
Conclusion
Network Security Best Practices are a treasure trove of fun and practical tools catering to different needs and interest. Their availability and versatility make them a great addition to both professional and personal lives. Explore the endless world of Network Security Best Practices right now and unlock new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables for free really free?
- Yes, they are! You can print and download these resources at no cost.
-
Do I have the right to use free printing templates for commercial purposes?
- It's based on the conditions of use. Always review the terms of use for the creator before using any printables on commercial projects.
-
Do you have any copyright violations with printables that are free?
- Some printables may contain restrictions on their use. Be sure to review the terms and regulations provided by the author.
-
How can I print Network Security Best Practices?
- You can print them at home using the printer, or go to an in-store print shop to get higher quality prints.
-
What program do I require to view Network Security Best Practices?
- The majority of PDF documents are provided in the PDF format, and can be opened using free software such as Adobe Reader.
Network Security Best Practices GBHackers Security 1 Globally
Top 5 network Security Best Practices That Don t Cost Much To Implement

Check more sample of Network Security Best Practices below
Network Security Best Practices TechPoint

12 Network Security Best Practices To Secure Your Business InfoSec
Network Security Best Practices

Security Best Practices Checklist For Palo Alto Networks

Network Security Best Practices YouTube

3 Network Security Best Practices To Follow Inception Network Strategies


https://resources.infosecinstitute.com/resources/professional-develo…
Cyber security hiring Tips and best practices Cybersecurity soft skills Career benefits of public speaking CompTIA Data certification Opening doors to new careers Surviving cybersecurity burnout Tips from industry experts How to make a mid career change to cybersecurity 7 top security certifications you should have in 2024

https://resources.infosecinstitute.com/globalassets/boot-ca…
Network and cloud engineers IT auditors Security officers and managers IT project managers DevOps teams Software developers Anyone looking to learn a baseline of security concepts Essential information security concepts Threats and attack vectors used by malicious actors Network security monitoring access control
Cyber security hiring Tips and best practices Cybersecurity soft skills Career benefits of public speaking CompTIA Data certification Opening doors to new careers Surviving cybersecurity burnout Tips from industry experts How to make a mid career change to cybersecurity 7 top security certifications you should have in 2024
Network and cloud engineers IT auditors Security officers and managers IT project managers DevOps teams Software developers Anyone looking to learn a baseline of security concepts Essential information security concepts Threats and attack vectors used by malicious actors Network security monitoring access control

Security Best Practices Checklist For Palo Alto Networks

12 Network Security Best Practices To Secure Your Business InfoSec

Network Security Best Practices YouTube

3 Network Security Best Practices To Follow Inception Network Strategies
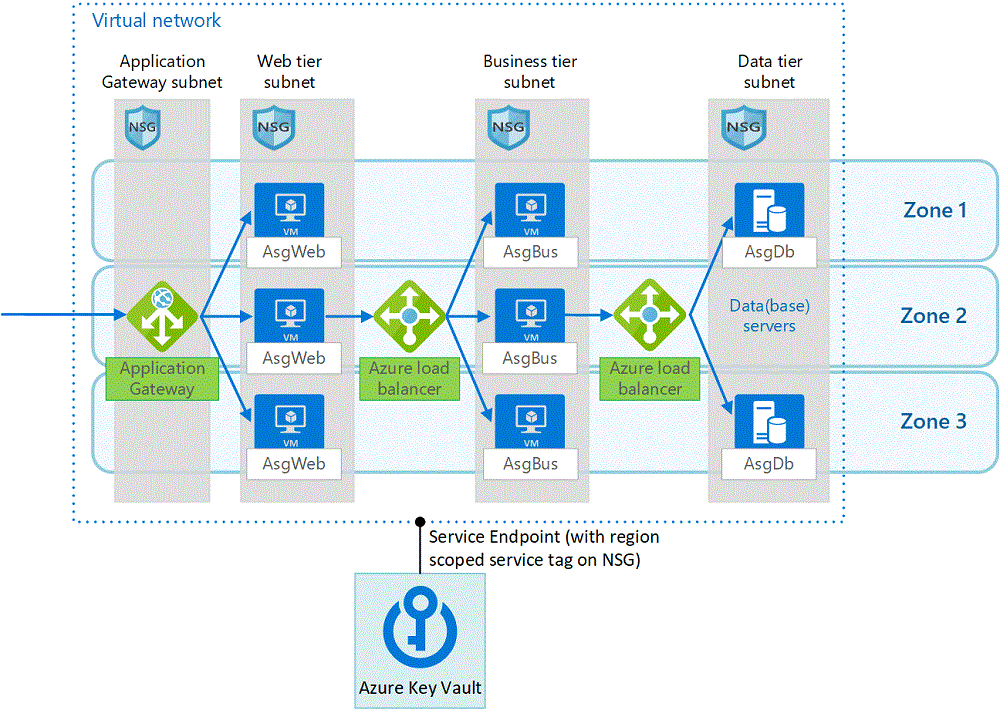
Security Considerations For Highly Sensitive IaaS Apps In Azure Azure

Top 10 Best Practices For Network Security Management

Top 10 Best Practices For Network Security Management
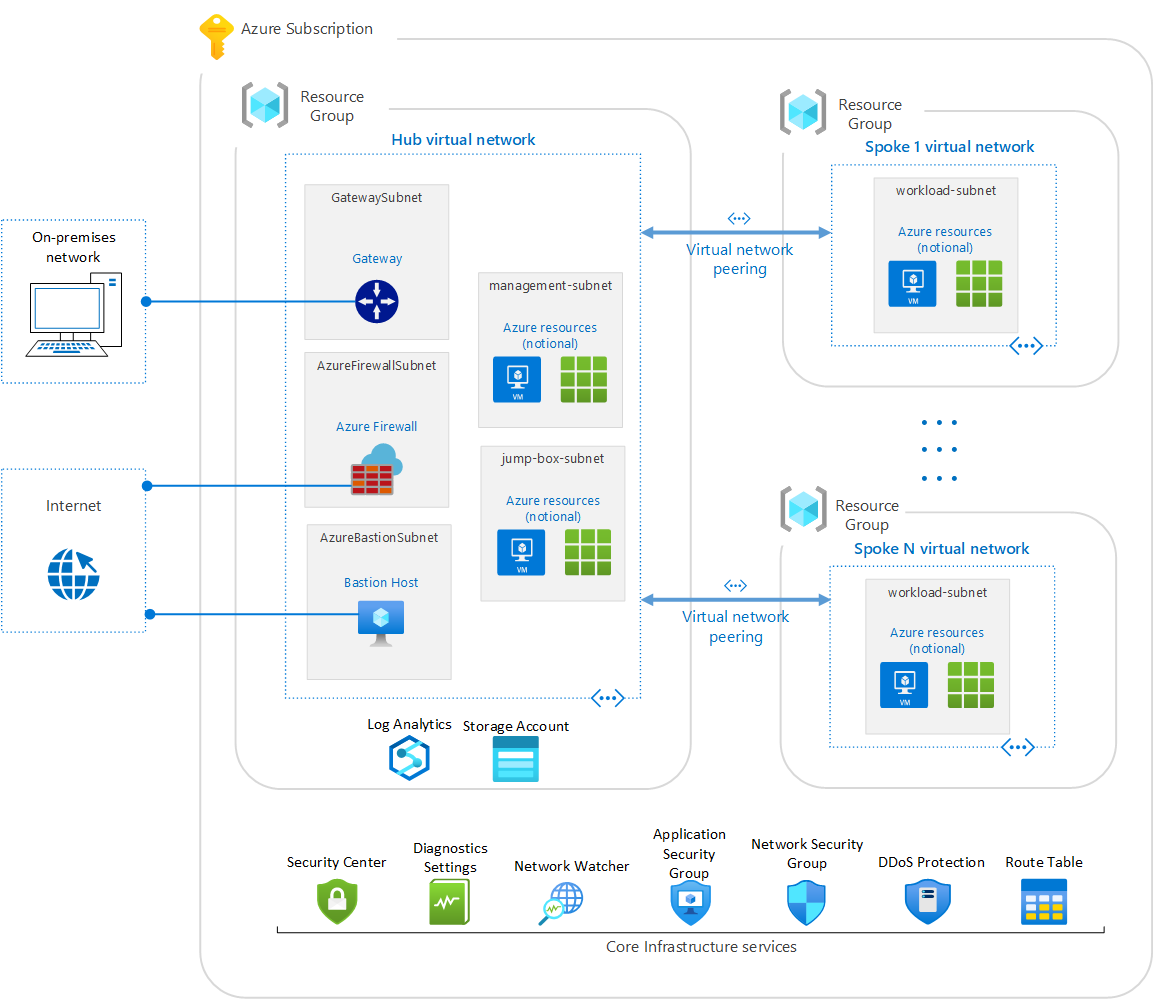
Azure Security Benchmark Foundation Blueprint Sample Overview Azure