In the age of digital, with screens dominating our lives yet the appeal of tangible, printed materials hasn't diminished. It doesn't matter if it's for educational reasons, creative projects, or just adding an individual touch to your area, Network Security Best Practices Guide can be an excellent source. With this guide, you'll take a dive deep into the realm of "Network Security Best Practices Guide," exploring what they are, how to find them, and how they can improve various aspects of your life.
Get Latest Network Security Best Practices Guide Below
Network Security Best Practices Guide
Network Security Best Practices Guide -
LAN A Local Area Network LAN is a network that covers a small area such as an office or a home LANs are typically used to connect computers and other devices within a
A computer network is a group of interconnected nodes or computing devices that exchange data and resources with each other A network connection between these devices
Network Security Best Practices Guide offer a wide variety of printable, downloadable documents that can be downloaded online at no cost. These resources come in various styles, from worksheets to templates, coloring pages, and much more. The appeal of printables for free is their flexibility and accessibility.
More of Network Security Best Practices Guide
Network Security Best Practices GBHackers Security 1 Globally
Network Security Best Practices GBHackers Security 1 Globally
A network consists of multiple devices that communicate with one another It can be as small as two computers or as large as billions of devices While a traditional network is
List the different types of network devices used in a network Describe network communication principles like TCP IP DNS and ports Describe how these core components map to Azure
Network Security Best Practices Guide have garnered immense popularity because of a number of compelling causes:
-
Cost-Effective: They eliminate the need to purchase physical copies or costly software.
-
customization This allows you to modify the templates to meet your individual needs for invitations, whether that's creating them making your schedule, or even decorating your home.
-
Educational Worth: The free educational worksheets offer a wide range of educational content for learners of all ages, which makes them a great resource for educators and parents.
-
An easy way to access HTML0: Fast access a plethora of designs and templates saves time and effort.
Where to Find more Network Security Best Practices Guide
Network Security Best Practices

Network Security Best Practices
Switches routers and wireless access points perform very different functions in a network Switches Switches are the foundation of most business networks A switch acts as a
A computer network is made up of four essential components These components are End devices Media Protocols and Networking devices Let s discuss these components
We hope we've stimulated your curiosity about Network Security Best Practices Guide we'll explore the places you can get these hidden gems:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy offer a vast selection and Network Security Best Practices Guide for a variety applications.
- Explore categories like design, home decor, organizing, and crafts.
2. Educational Platforms
- Forums and websites for education often offer free worksheets and worksheets for printing for flashcards, lessons, and worksheets. materials.
- Great for parents, teachers and students who are in need of supplementary sources.
3. Creative Blogs
- Many bloggers share their innovative designs with templates and designs for free.
- These blogs cover a broad selection of subjects, from DIY projects to party planning.
Maximizing Network Security Best Practices Guide
Here are some ideas to make the most use of printables for free:
1. Home Decor
- Print and frame stunning images, quotes, or festive decorations to decorate your living spaces.
2. Education
- Use free printable worksheets to aid in learning at your home and in class.
3. Event Planning
- Design invitations, banners and decorations for special occasions such as weddings and birthdays.
4. Organization
- Get organized with printable calendars, to-do lists, and meal planners.
Conclusion
Network Security Best Practices Guide are a treasure trove of fun and practical tools that cater to various needs and interest. Their accessibility and flexibility make them a wonderful addition to any professional or personal life. Explore the world that is Network Security Best Practices Guide today, and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables that are free truly free?
- Yes, they are! You can print and download the resources for free.
-
Does it allow me to use free printables to make commercial products?
- It's determined by the specific usage guidelines. Be sure to read the rules of the creator prior to utilizing the templates for commercial projects.
-
Are there any copyright concerns when using Network Security Best Practices Guide?
- Some printables may come with restrictions regarding their use. Make sure you read the terms and regulations provided by the creator.
-
How do I print Network Security Best Practices Guide?
- You can print them at home with an printer, or go to a local print shop for high-quality prints.
-
What software do I need to run printables for free?
- Most PDF-based printables are available in the PDF format, and is open with no cost programs like Adobe Reader.
Enhancing Network Security Best Practices And Strategies By Paritosh

3 Network Security Best Practices To Follow Inception Network Strategies

Check more sample of Network Security Best Practices Guide below
AWS Security Best Practices Infosyte

Network Security Best Practices A 15 Point Checklist

Need Of Secure Protocols

Top 10 Best Practices For Network Security Management

API Security Best Practices Data Breach Security Tips Best Practice

Buy Microsoft Azure Security Technologies AZ 500 A Certification

https://www.techtarget.com › searchnetworking › definition › network
A computer network is a group of interconnected nodes or computing devices that exchange data and resources with each other A network connection between these devices
https://www.ionos.com › ... › know-how › what-is-a-network
In information technology a network is defined as the connection of at least two computer systems either by a cable or a wireless connection The simplest network is a
A computer network is a group of interconnected nodes or computing devices that exchange data and resources with each other A network connection between these devices
In information technology a network is defined as the connection of at least two computer systems either by a cable or a wireless connection The simplest network is a

Top 10 Best Practices For Network Security Management

Network Security Best Practices A 15 Point Checklist

API Security Best Practices Data Breach Security Tips Best Practice

Buy Microsoft Azure Security Technologies AZ 500 A Certification

Network Security Best Practices 2023 Aluria Tech

Salesforce Data Security Best Practices Protecto

Salesforce Data Security Best Practices Protecto
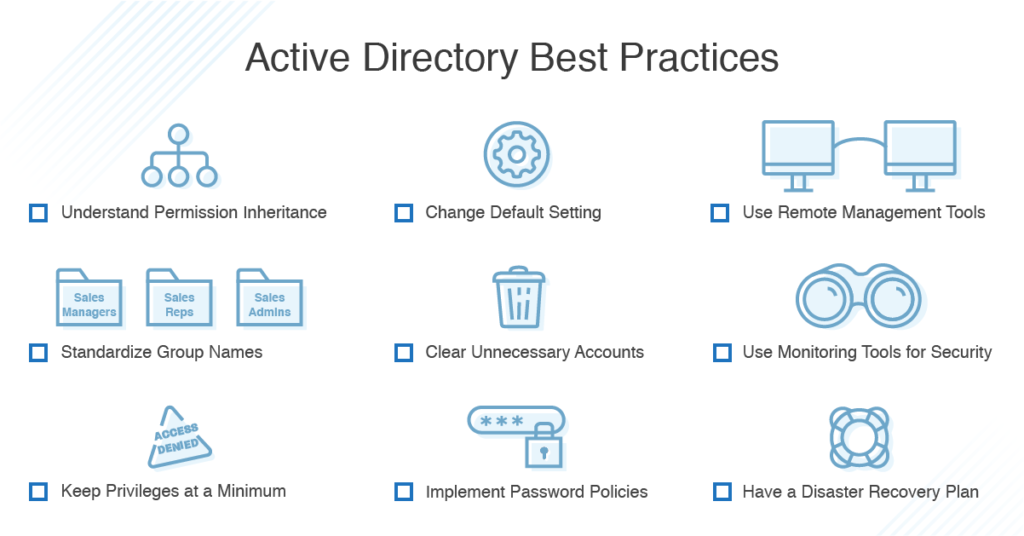
What Is A Domain Controller What Is Active Directory