In this day and age where screens rule our lives and our lives are dominated by screens, the appeal of tangible printed materials isn't diminishing. It doesn't matter if it's for educational reasons, creative projects, or just adding an element of personalization to your area, Network Security Best Practices Checklist are a great source. Through this post, we'll take a dive into the world of "Network Security Best Practices Checklist," exploring what they are, where to find them, and how they can add value to various aspects of your lives.
Get Latest Network Security Best Practices Checklist Below

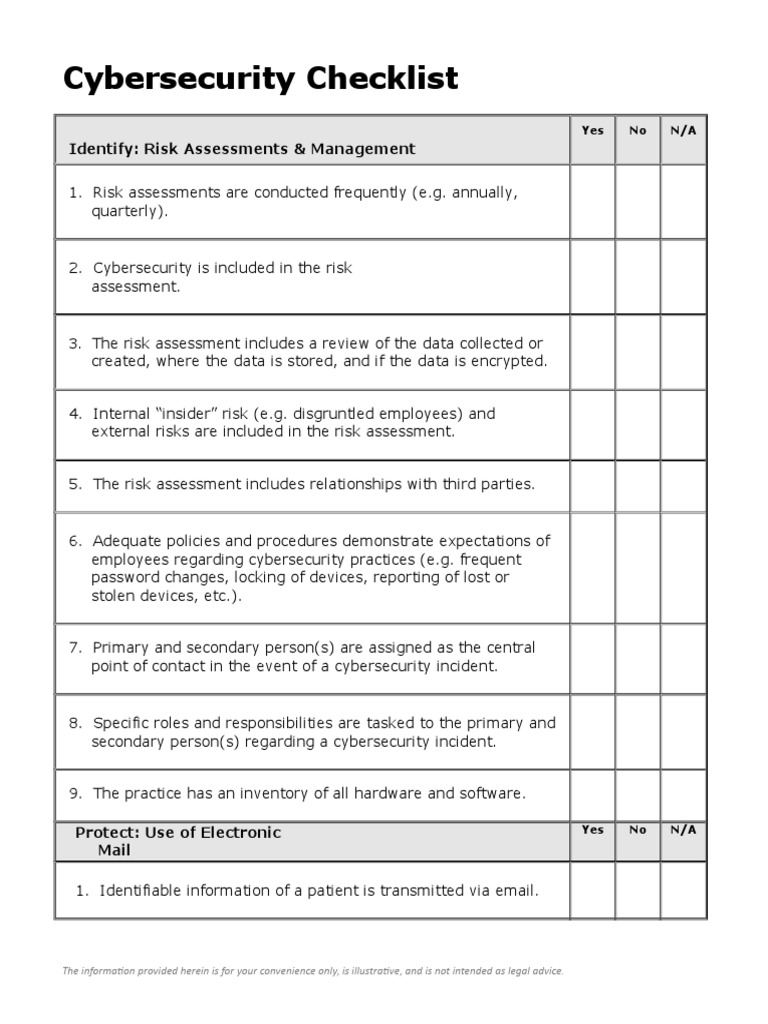
Network Security Best Practices Checklist
Network Security Best Practices Checklist - Network Security Best Practices Checklist, Network Security Best Practices
If you are unsure if you meet the required prerequisites contact us for a quick network security training skill check Start training immediately Prepare for your boot camp with immediate access to the Infosec Skills on demand training library Learn by doing in the cyber range Put what you ve learned into practice with 100s of
OT ICS Certified Security Professional ICSP Boot Camp Learn the best practices for securing Operational Technologies OT including Industrial Control Systems ICS and SCADA networks This boot camp teaches you how to defend against both internal and external attackers to provide holistic security for critical industrial automation systems
Printables for free include a vast range of downloadable, printable material that is available online at no cost. They are available in a variety of designs, including worksheets templates, coloring pages and much more. The appeal of printables for free is their flexibility and accessibility.
More of Network Security Best Practices Checklist
Network Security Best Practices A Complete Checklist RSI Security
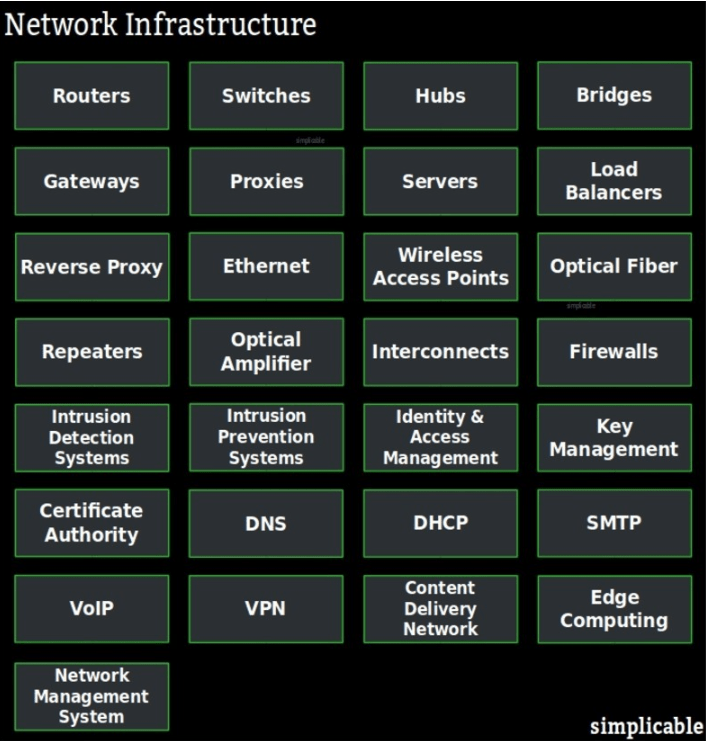
Network Security Best Practices A Complete Checklist RSI Security
U S federal regulation of marketing practices TSR DNC CAN SPAM TCPA and JFPA U S state data breach notification California SB 1386 and select state laws Regulation of privacy in the U S workplace FCRA EPP ADA and ECPA plus best practices for privacy and background screening employee testing workplace monitoring employee
Grasping the best practices for authentication and permissions as well as the management of firewalls and files Crafting basic shell scripts running elementary BASH scripts utilizing Git for version control and understanding orchestration processes Learn more about what s on the latest version of the CompTIA Linux exam
Network Security Best Practices Checklist have risen to immense popularity due to a myriad of compelling factors:
-
Cost-Effective: They eliminate the requirement of buying physical copies of the software or expensive hardware.
-
Modifications: This allows you to modify designs to suit your personal needs whether it's making invitations planning your schedule or even decorating your house.
-
Educational Impact: The free educational worksheets are designed to appeal to students from all ages, making them a vital tool for teachers and parents.
-
Easy to use: You have instant access numerous designs and templates is time-saving and saves effort.
Where to Find more Network Security Best Practices Checklist
Palo Alto Networks Security Best Practices Checklist PDF Transport

Palo Alto Networks Security Best Practices Checklist PDF Transport
[desc-9]
Additional information to the class and knows the field of security inside and out I was very pleased with his knowledge and instructional skills I went to West Point for my bachelor s Columbia for my master s and had multiple Army led courses and this ranks as one of the best most engaging courses that I have ever had Sheree Moore
We've now piqued your curiosity about Network Security Best Practices Checklist Let's find out where you can find these gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a large collection of Network Security Best Practices Checklist suitable for many applications.
- Explore categories like decorations for the home, education and organisation, as well as crafts.
2. Educational Platforms
- Educational websites and forums frequently provide worksheets that can be printed for free as well as flashcards and other learning materials.
- The perfect resource for parents, teachers and students who are in need of supplementary resources.
3. Creative Blogs
- Many bloggers offer their unique designs and templates at no cost.
- These blogs cover a wide range of interests, including DIY projects to planning a party.
Maximizing Network Security Best Practices Checklist
Here are some creative ways that you can make use use of Network Security Best Practices Checklist:
1. Home Decor
- Print and frame gorgeous artwork, quotes, or festive decorations to decorate your living areas.
2. Education
- Use free printable worksheets to help reinforce your learning at home either in the schoolroom or at home.
3. Event Planning
- Designs invitations, banners and decorations for special occasions such as weddings and birthdays.
4. Organization
- Make sure you are organized with printable calendars, to-do lists, and meal planners.
Conclusion
Network Security Best Practices Checklist are an abundance with useful and creative ideas that satisfy a wide range of requirements and passions. Their accessibility and versatility make them an invaluable addition to both personal and professional life. Explore the world of Network Security Best Practices Checklist to explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are Network Security Best Practices Checklist truly gratis?
- Yes, they are! You can download and print these materials for free.
-
Can I download free printables for commercial uses?
- It's based on specific conditions of use. Always review the terms of use for the creator prior to printing printables for commercial projects.
-
Do you have any copyright rights issues with printables that are free?
- Some printables could have limitations in use. Make sure to read the terms and conditions offered by the author.
-
How can I print printables for free?
- You can print them at home using your printer or visit any local print store for higher quality prints.
-
What software is required to open printables that are free?
- The majority of printed documents are in PDF format. These can be opened with free software such as Adobe Reader.
FREE 5 Network Security Checklist Templates In PDF
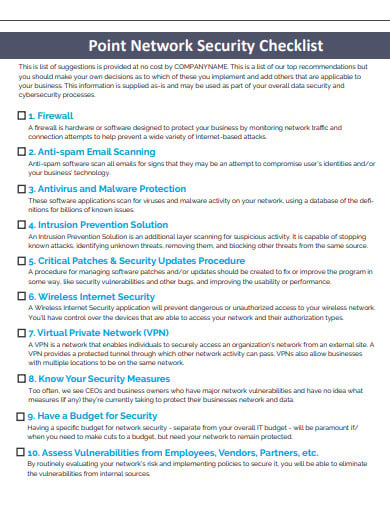
Cyber Security Cheat Sheet Pdf Cheat Sheet Images Vrogue co
Check more sample of Network Security Best Practices Checklist below
The Ultimate Guide To Active Directory Best Practices DNSstuff
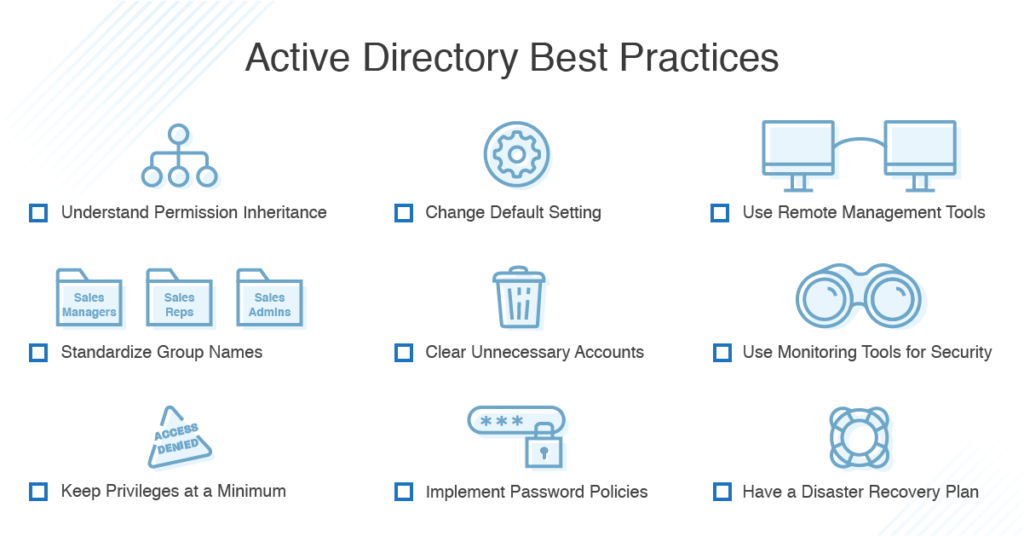
Business Network Security Best Practices Checklist Resolute
Checklist API Security Best Practices

OT Security Best Practices Checklist IANS Research

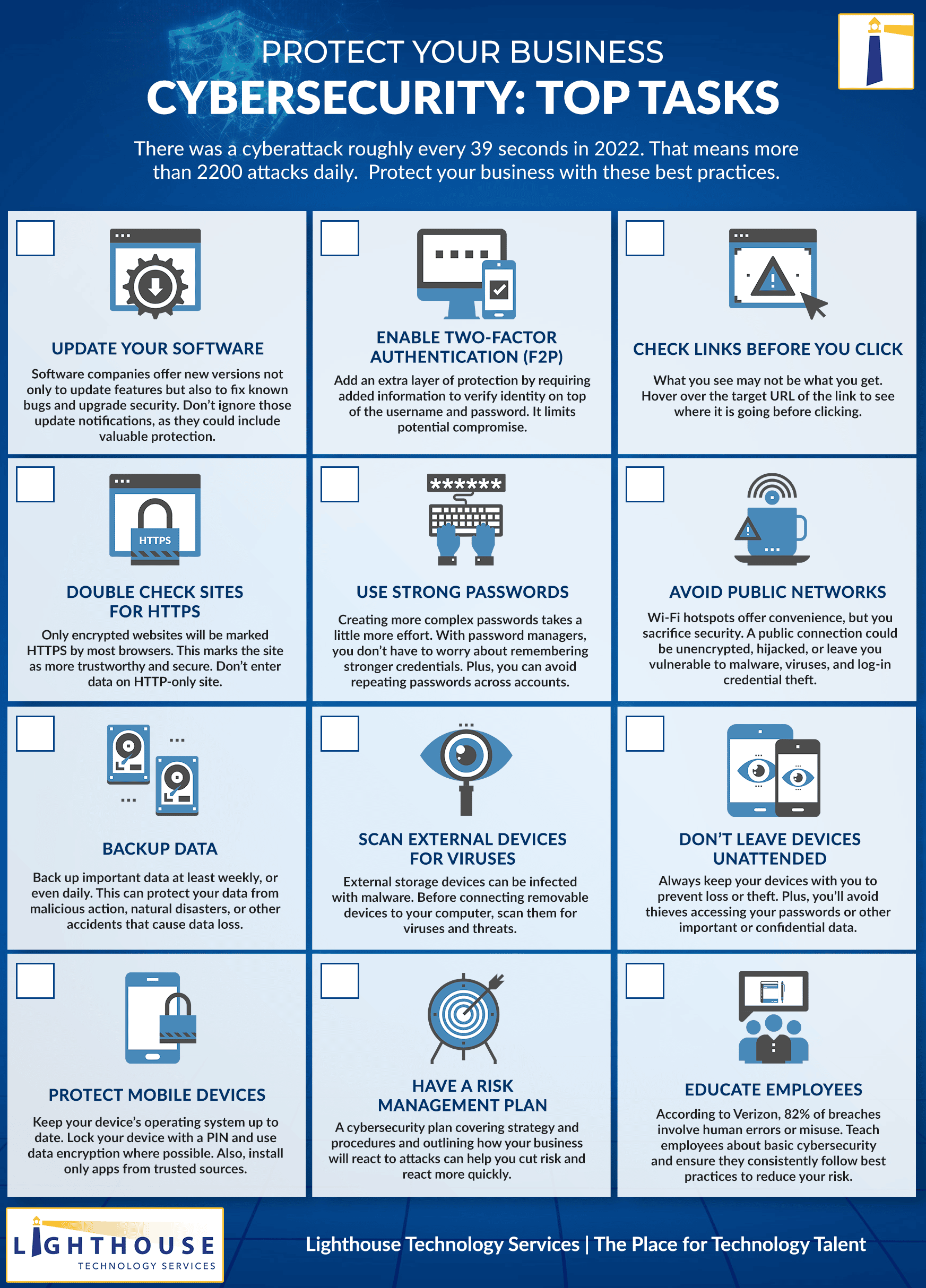
Checklist 12 Top Tasks To Build A Business Cybersecurity Foundation
Network Security Best Practices A 15 Point Checklist


https://resources.infosecinstitute.com › globalassets › boo…
OT ICS Certified Security Professional ICSP Boot Camp Learn the best practices for securing Operational Technologies OT including Industrial Control Systems ICS and SCADA networks This boot camp teaches you how to defend against both internal and external attackers to provide holistic security for critical industrial automation systems

https://resources.infosecinstitute.com › globalassets › docu…
Explain the security implications of embedded and specialized systems 2 5 2 6 Redundancy Geographic dispersal Disk Redundant array of inexpensive disks RAID levels Multipath Network Load balancers Network interface card NIC teaming Power Uninterruptible power supply UPS Generator Dual supply Managed power
OT ICS Certified Security Professional ICSP Boot Camp Learn the best practices for securing Operational Technologies OT including Industrial Control Systems ICS and SCADA networks This boot camp teaches you how to defend against both internal and external attackers to provide holistic security for critical industrial automation systems
Explain the security implications of embedded and specialized systems 2 5 2 6 Redundancy Geographic dispersal Disk Redundant array of inexpensive disks RAID levels Multipath Network Load balancers Network interface card NIC teaming Power Uninterruptible power supply UPS Generator Dual supply Managed power

OT Security Best Practices Checklist IANS Research

Business Network Security Best Practices Checklist Resolute

Checklist 12 Top Tasks To Build A Business Cybersecurity Foundation

Network Security Best Practices A 15 Point Checklist

10 Cybersecurity Best Practices For Small Businesses

Assessing The Security Risks Of Cloud Computing Maknanews

Assessing The Security Risks Of Cloud Computing Maknanews

Top 10 Best Practices For Network Security Management