In the digital age, when screens dominate our lives, the charm of tangible printed objects isn't diminished. For educational purposes, creative projects, or simply to add an individual touch to the home, printables for free are now a useful source. This article will take a dive deeper into "Information Security Best Practices," exploring the different types of printables, where they are available, and how they can improve various aspects of your daily life.
Get Latest Information Security Best Practices Below
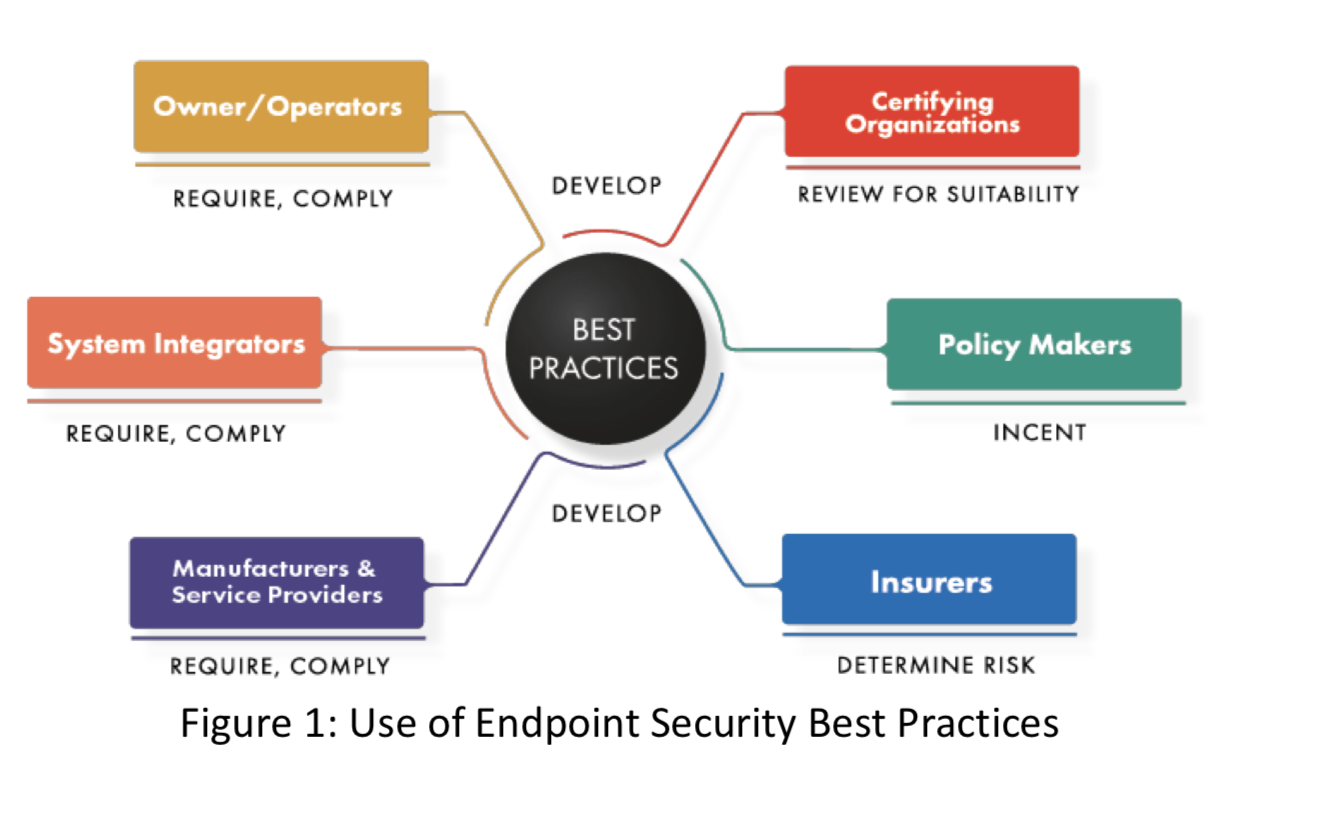
Information Security Best Practices
Information Security Best Practices -
mc java ConnectException Connection refused no further information notch
I ve used the structure search information or search for information for a long time And the most common sentences are to combine search for information with the
Printables for free cover a broad range of downloadable, printable materials online, at no cost. They are available in a variety of types, such as worksheets templates, coloring pages, and many more. The attraction of printables that are free is their versatility and accessibility.
More of Information Security Best Practices
Online Essay Help Amazonia fiocruz br

Online Essay Help Amazonia fiocruz br
I haven t got the requested information yet I haven t got the information requested yet She has not been able to get the dump information requested yet Two agencies provided
System Volume Information U
Printables that are free have gained enormous recognition for a variety of compelling motives:
-
Cost-Efficiency: They eliminate the requirement of buying physical copies or expensive software.
-
Individualization They can make printed materials to meet your requirements such as designing invitations and schedules, or even decorating your house.
-
Educational Impact: Printing educational materials for no cost are designed to appeal to students of all ages, making them an essential tool for parents and teachers.
-
An easy way to access HTML0: instant access many designs and templates reduces time and effort.
Where to Find more Information Security Best Practices
Orphan Additionally Can Canceling Respective Employ A Programming

Orphan Additionally Can Canceling Respective Employ A Programming
Mc no further information mc mc
I requested some information from a friend received it and now I am writing to her again I have passed the information or should I write I passed the information I am
Now that we've ignited your curiosity about Information Security Best Practices Let's find out where you can discover these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy offer a vast selection of Information Security Best Practices designed for a variety reasons.
- Explore categories like the home, decor, organization, and crafts.
2. Educational Platforms
- Educational websites and forums usually provide free printable worksheets, flashcards, and learning tools.
- Perfect for teachers, parents and students looking for additional sources.
3. Creative Blogs
- Many bloggers are willing to share their original designs and templates, which are free.
- The blogs covered cover a wide array of topics, ranging ranging from DIY projects to planning a party.
Maximizing Information Security Best Practices
Here are some ideas ensure you get the very most of printables for free:
1. Home Decor
- Print and frame gorgeous images, quotes, and seasonal decorations, to add a touch of elegance to your living spaces.
2. Education
- Print out free worksheets and activities to build your knowledge at home as well as in the class.
3. Event Planning
- Invitations, banners as well as decorations for special occasions like birthdays and weddings.
4. Organization
- Stay organized with printable calendars for to-do list, lists of chores, and meal planners.
Conclusion
Information Security Best Practices are a treasure trove of practical and imaginative resources designed to meet a range of needs and preferences. Their accessibility and flexibility make these printables a useful addition to any professional or personal life. Explore the world of Information Security Best Practices right now and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables available for download really for free?
- Yes you can! You can print and download these materials for free.
-
Are there any free printing templates for commercial purposes?
- It's all dependent on the usage guidelines. Always check the creator's guidelines before using printables for commercial projects.
-
Are there any copyright concerns when using printables that are free?
- Certain printables might have limitations in use. Be sure to review the terms and conditions offered by the designer.
-
How do I print Information Security Best Practices?
- You can print them at home with printing equipment or visit the local print shop for more high-quality prints.
-
What software do I require to view printables for free?
- Most PDF-based printables are available in the format of PDF, which is open with no cost software like Adobe Reader.
4 Security Best Practices For Every Small Business Infographic

5 Essential Data Security Best Practices For Keeping Your Data Safe
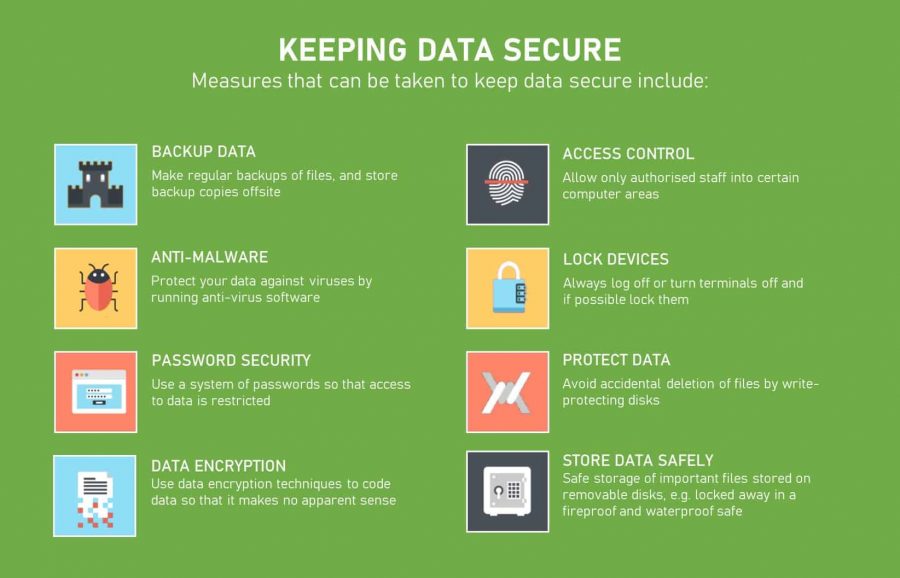
Check more sample of Information Security Best Practices below
The Beginner s Guide To Cybersecurity University Of Kansas Boot Camps

Best Practices To Secure Windows10 With Already Inclu Vrogue co
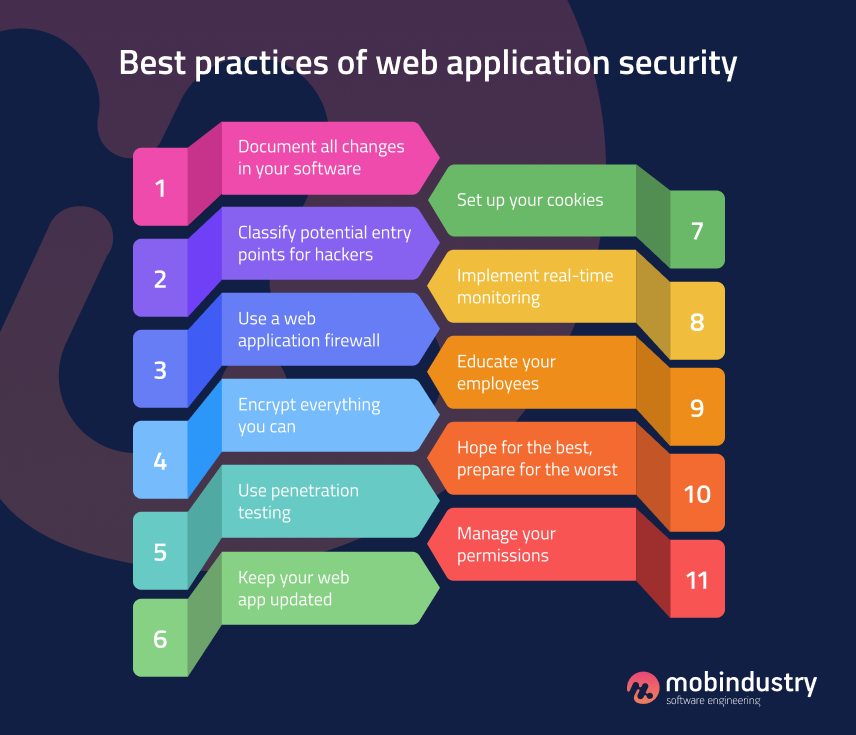
Data Security Best Practices Detailed Guide Updated 2024 Unichrone
Chef pouvanter Continuez It Security Tips Atteindre Remplir Efficace
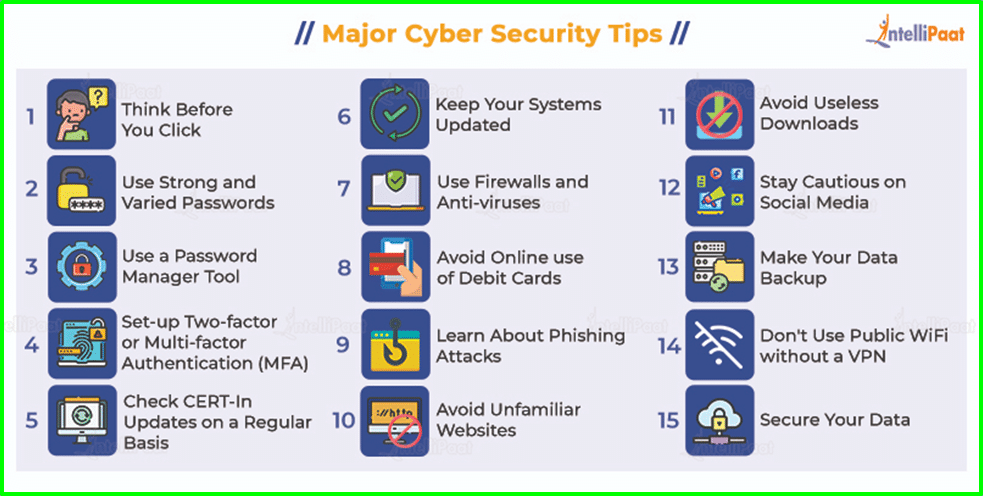
Information Security Best Practices Every Organization Should Keep In

Information Security Best Practices For Employees

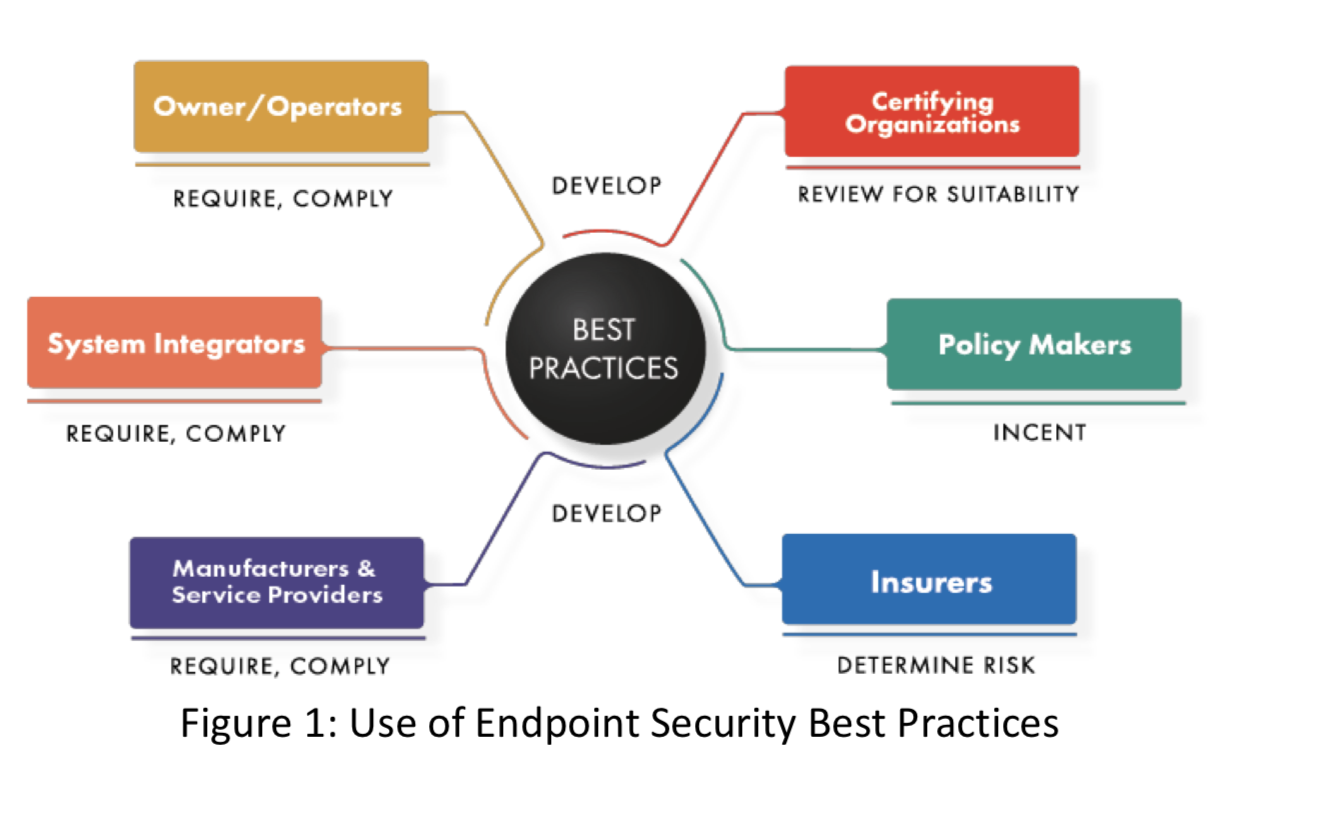
https://forum.wordreference.com › threads
I ve used the structure search information or search for information for a long time And the most common sentences are to combine search for information with the

https://forum.wordreference.com › threads › nel-caso-doveste-avere-nec…
Molte persone invece aggiungono una s a information e questo perch nella nostra lingua normalmente si usa il vocabolo plurale informazioni I need informations on
I ve used the structure search information or search for information for a long time And the most common sentences are to combine search for information with the
Molte persone invece aggiungono una s a information e questo perch nella nostra lingua normalmente si usa il vocabolo plurale informazioni I need informations on

Chef pouvanter Continuez It Security Tips Atteindre Remplir Efficace

Best Practices To Secure Windows10 With Already Inclu Vrogue co

Information Security Best Practices Every Organization Should Keep In

Information Security Best Practices For Employees

Best Information Security Practices According To PCI INFOGRAPHIC

The Heart Of A Network Is Network Security Polyphonichmi

The Heart Of A Network Is Network Security Polyphonichmi
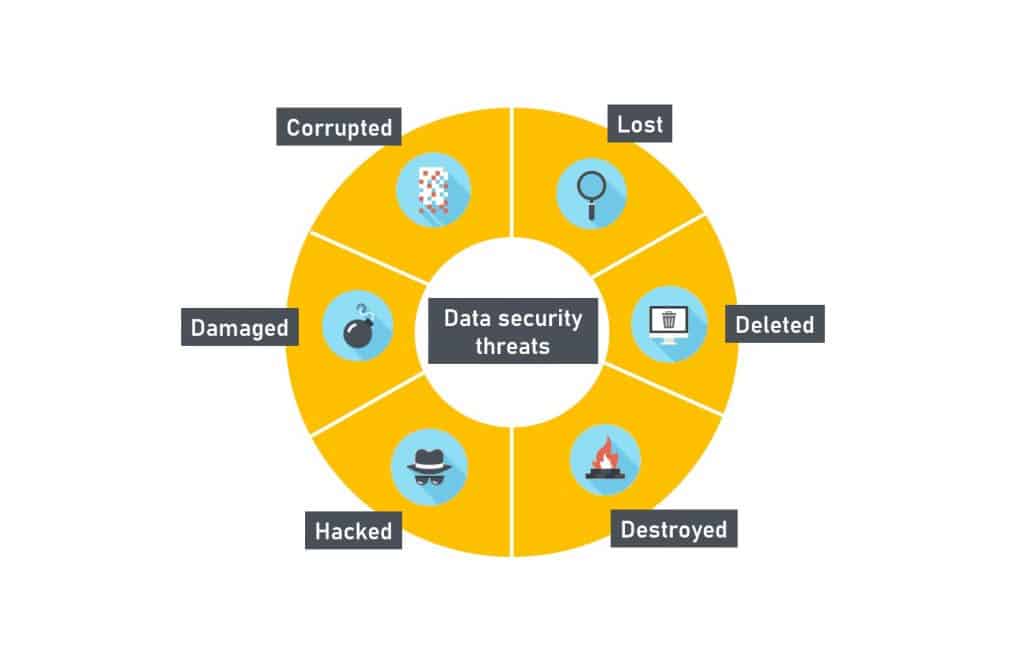
5 Essential Data Security Best Practices For Keeping Your Data Safe