In this age of electronic devices, where screens dominate our lives The appeal of tangible printed materials hasn't faded away. If it's to aid in education in creative or artistic projects, or simply to add the personal touch to your home, printables for free have proven to be a valuable resource. This article will take a dive into the sphere of "Security Architecture Best Practices," exploring the different types of printables, where they can be found, and how they can improve various aspects of your lives.
Get Latest Security Architecture Best Practices Below

Security Architecture Best Practices
Security Architecture Best Practices - Security Architecture Best Practices, Security Architect Best Practices, Azure Security Architecture Best Practices, Aws Security Architecture Best Practices, Network Security Architecture Best Practices, Cloud Security Architecture Best Practices, Cyber Security Architecture Best Practices, Microservices Architecture Security Best Practices, Web Application Security Architecture Best Practices, Network Security Best Practices Checklist
This article explores network security architecture components goals best practices frameworks implementation and benefits as well as where you can learn more about network security
COBIT principles and enablers provide best practices and guidance on business alignment maximum delivery and benefits The COBIT Process Assessment Model PAM provides a complete view of requirement processes and controls for enterprise grade security architecture
Printables for free include a vast array of printable material that is available online at no cost. They come in many types, like worksheets, coloring pages, templates and more. One of the advantages of Security Architecture Best Practices is their flexibility and accessibility.
More of Security Architecture Best Practices
5 Top Network Design Considerations For Security Integrators 2019 01

5 Top Network Design Considerations For Security Integrators 2019 01
Security architecture is the strategic design of systems policies and technologies to protect IT and business assets from cyberthreats A well designed security architecture aligns cybersecurity with the unique business goals and risk management profile of
In the security category of the Architecture Framework you learn to do the following Review shared responsibility and shared fate on Google Cloud Understand security principles Manage
Printables that are free have gained enormous popularity for several compelling reasons:
-
Cost-Efficiency: They eliminate the requirement to purchase physical copies of the software or expensive hardware.
-
Modifications: The Customization feature lets you tailor printables to your specific needs whether it's making invitations planning your schedule or decorating your home.
-
Educational Value: Printables for education that are free offer a wide range of educational content for learners of all ages. This makes them a valuable aid for parents as well as educators.
-
Simple: You have instant access a plethora of designs and templates, which saves time as well as effort.
Where to Find more Security Architecture Best Practices
Security Architecture

Security Architecture
Best practices Next steps This article contains security best practices to use when you re designing deploying and managing your cloud solutions by using Azure These best practices come from our experience with Azure security and the experiences of customers like you Best practices
These principles should guide the security of your architecture design choices and operational processes Start with the recommended approaches and justify the benefits for a set of security requirements After you set your strategy drive actions by using the Security checklist as your next step
Since we've got your interest in printables for free we'll explore the places you can find these treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide a variety of Security Architecture Best Practices suitable for many goals.
- Explore categories like furniture, education, crafting, and organization.
2. Educational Platforms
- Educational websites and forums often offer free worksheets and worksheets for printing Flashcards, worksheets, and other educational tools.
- Ideal for teachers, parents as well as students who require additional sources.
3. Creative Blogs
- Many bloggers post their original designs as well as templates for free.
- These blogs cover a wide array of topics, ranging starting from DIY projects to planning a party.
Maximizing Security Architecture Best Practices
Here are some fresh ways ensure you get the very most of Security Architecture Best Practices:
1. Home Decor
- Print and frame stunning artwork, quotes or other seasonal decorations to fill your living spaces.
2. Education
- Print worksheets that are free for reinforcement of learning at home (or in the learning environment).
3. Event Planning
- Designs invitations, banners and other decorations for special occasions like weddings and birthdays.
4. Organization
- Keep track of your schedule with printable calendars along with lists of tasks, and meal planners.
Conclusion
Security Architecture Best Practices are a treasure trove with useful and creative ideas that satisfy a wide range of requirements and needs and. Their accessibility and flexibility make them a wonderful addition to the professional and personal lives of both. Explore the vast array of Security Architecture Best Practices to discover new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free available for download?
- Yes, they are! You can print and download these resources at no cost.
-
Can I download free printouts for commercial usage?
- It's all dependent on the conditions of use. Always consult the author's guidelines prior to printing printables for commercial projects.
-
Do you have any copyright concerns when using printables that are free?
- Certain printables might have limitations in use. Make sure you read the terms and conditions offered by the creator.
-
How do I print printables for free?
- Print them at home with printing equipment or visit the local print shop for top quality prints.
-
What program is required to open printables free of charge?
- The majority of printed documents are in PDF format. These can be opened with free software like Adobe Reader.
Network Topology Best Practices FortiDeceptor 5 2 0 Fortinet

Industrial Network Design Best Practices Agilix Solutions
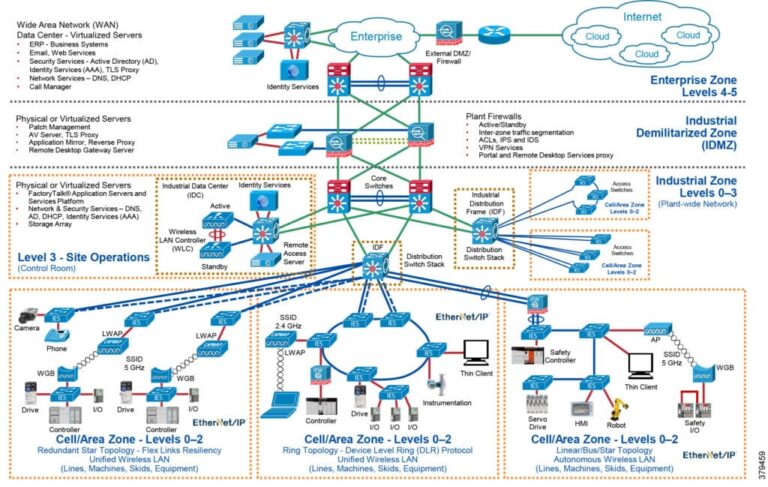
Check more sample of Security Architecture Best Practices below
Splunk Splunk Architecture Will s Ideas
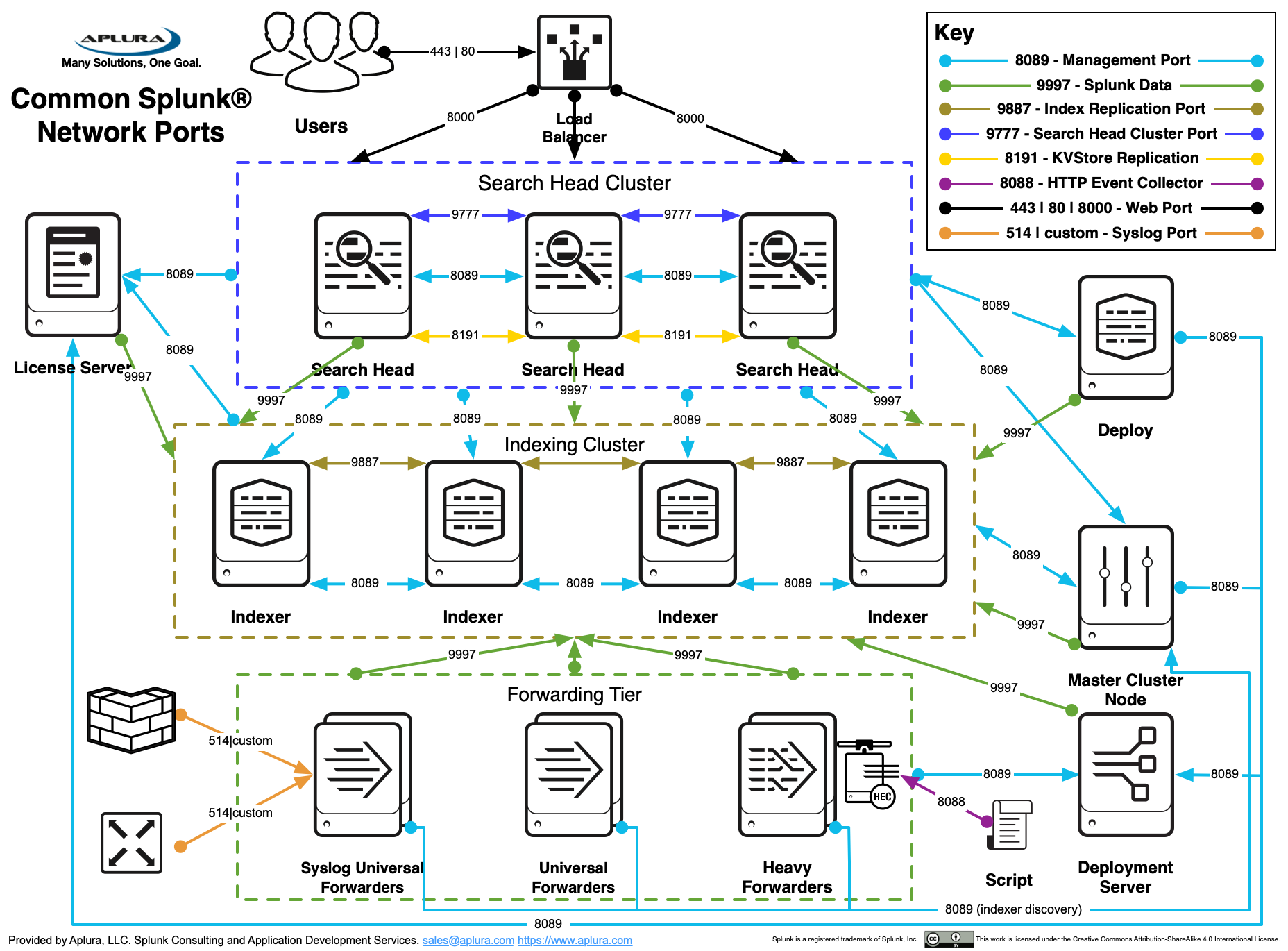
Top Security Architecture Best Practices For Maximum Protection Dig8ital

Intrusion Prevention System Architecture The Architect

What Is Network Security Definition Types Attacks And Tools 2023
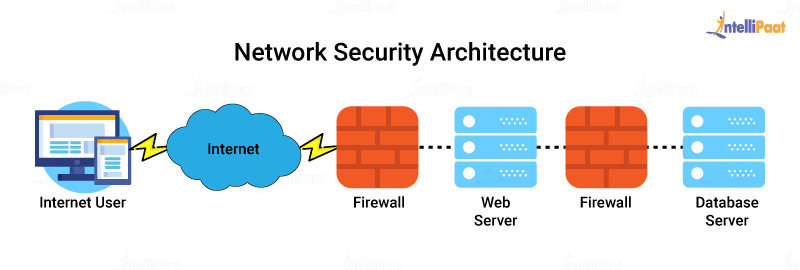
Security Architecture Defined IT Architecture Journal

Using Azure Blueprints Implementation Best Practices To Put Security


https://www.isaca.org › resources › isaca-journal › ...
COBIT principles and enablers provide best practices and guidance on business alignment maximum delivery and benefits The COBIT Process Assessment Model PAM provides a complete view of requirement processes and controls for enterprise grade security architecture

https://cyberpandit.org › security-architecture-essential-principles
Architecting for Cybersecurity Best Practices Highlighting Key Security Architecture Frameworks Benefits of Implementing Strong Security Architecture How Does Security Architecture Contribute to Risk Management Why is Continuous Learning and Training Important in Security Architecture
COBIT principles and enablers provide best practices and guidance on business alignment maximum delivery and benefits The COBIT Process Assessment Model PAM provides a complete view of requirement processes and controls for enterprise grade security architecture
Architecting for Cybersecurity Best Practices Highlighting Key Security Architecture Frameworks Benefits of Implementing Strong Security Architecture How Does Security Architecture Contribute to Risk Management Why is Continuous Learning and Training Important in Security Architecture

What Is Network Security Definition Types Attacks And Tools 2023

Top Security Architecture Best Practices For Maximum Protection Dig8ital

Security Architecture Defined IT Architecture Journal

Using Azure Blueprints Implementation Best Practices To Put Security
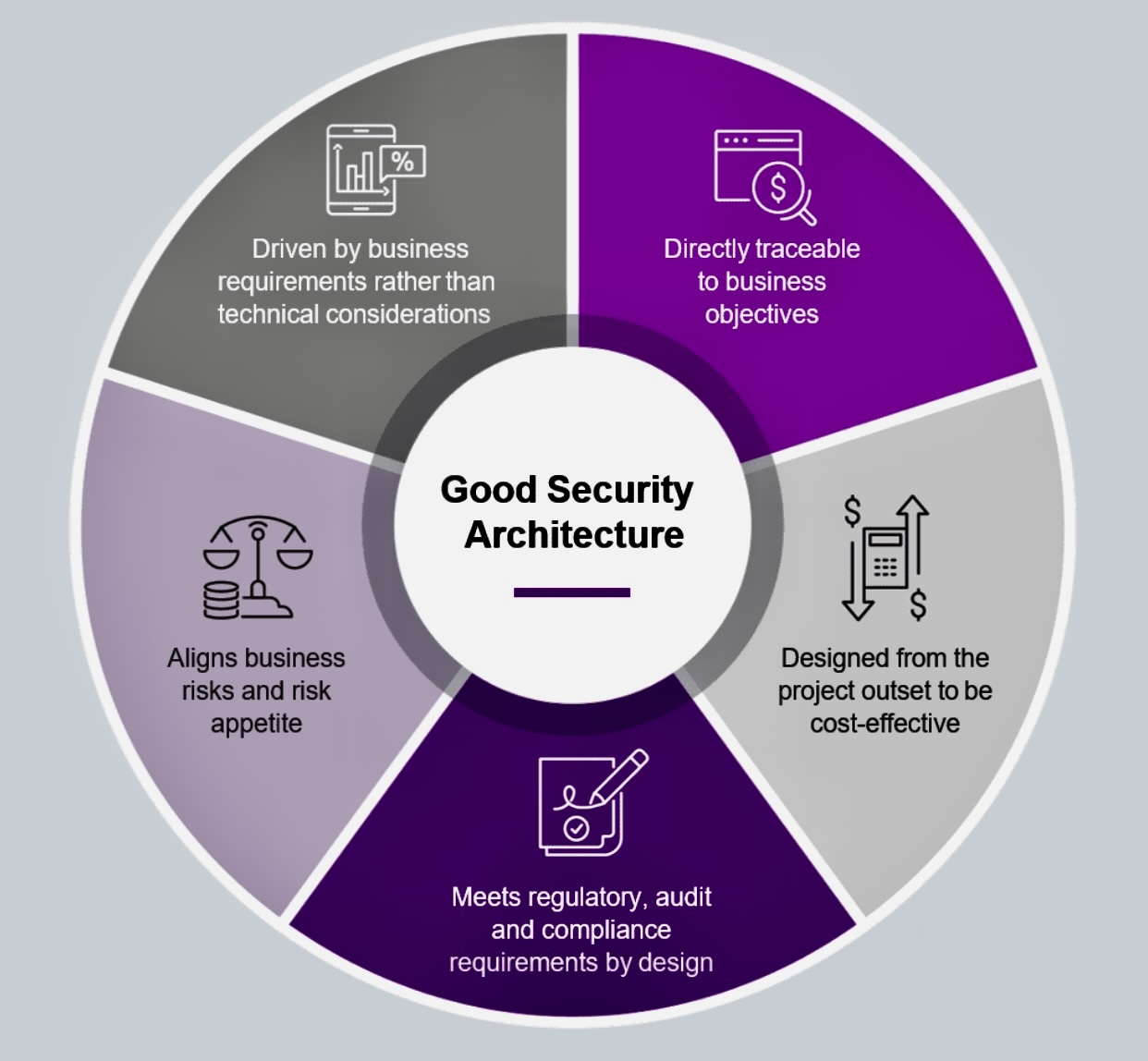
Good Security Architecture Consultia

Agile Security Architecture Masterclass Credly

Agile Security Architecture Masterclass Credly
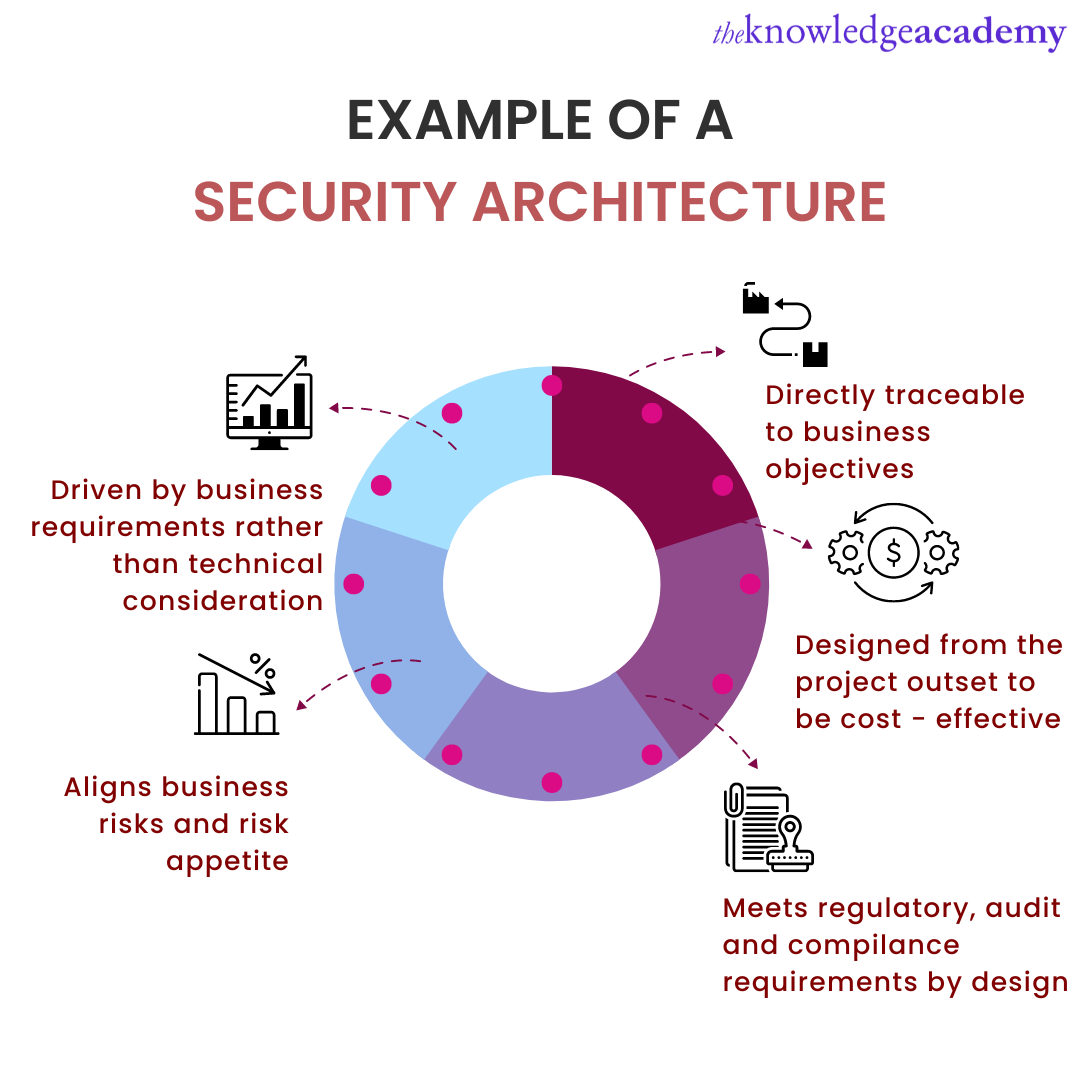
Cyber Security Architecture And Its Benefits