In the digital age, where screens have become the dominant feature of our lives it's no wonder that the appeal of tangible printed material hasn't diminished. Whether it's for educational purposes for creative projects, simply adding some personal flair to your space, What Is Symmetric Key In Cyber Security have proven to be a valuable source. For this piece, we'll take a dive in the world of "What Is Symmetric Key In Cyber Security," exploring what they are, how you can find them, and what they can do to improve different aspects of your daily life.
Get Latest What Is Symmetric Key In Cyber Security Below

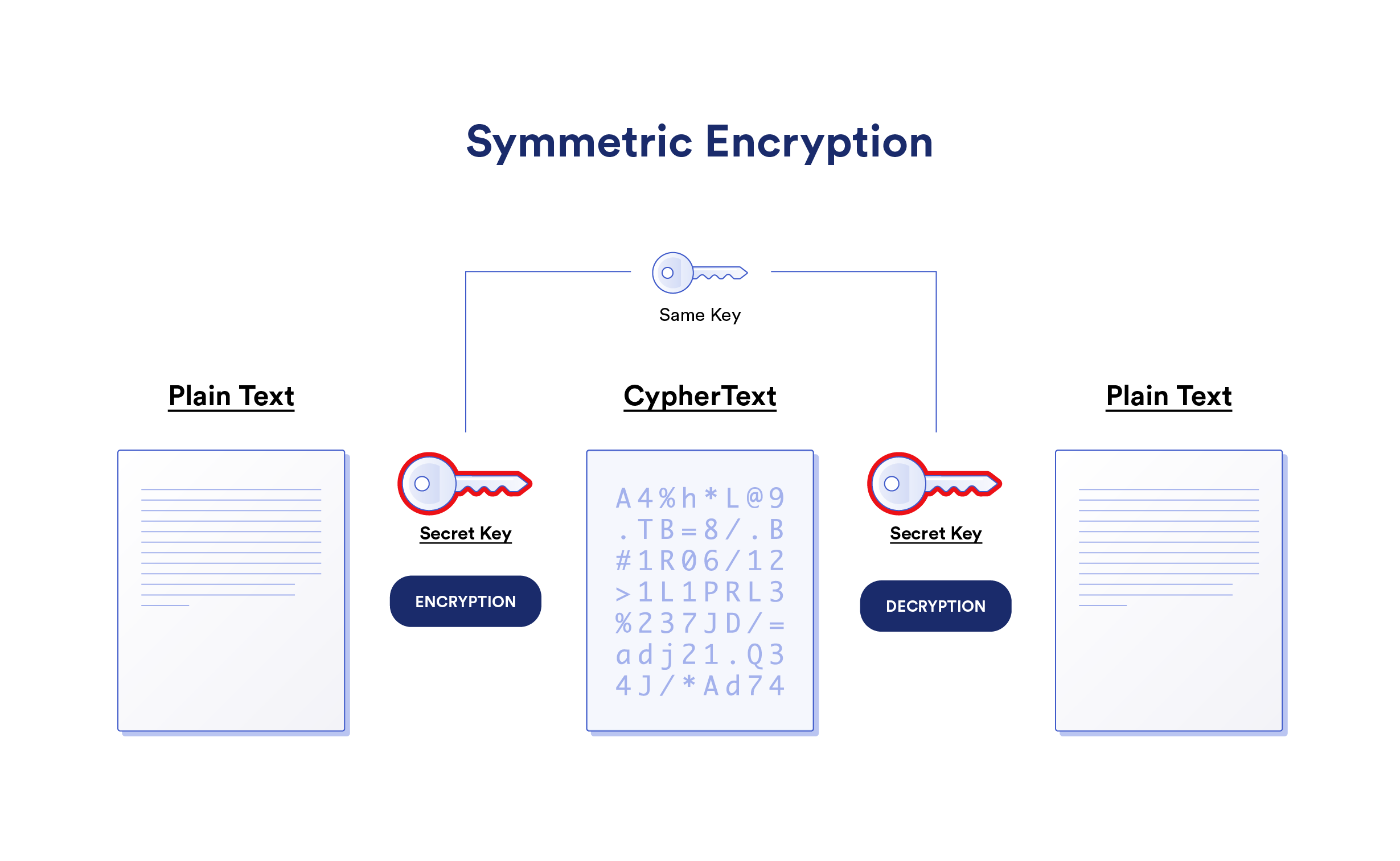
What Is Symmetric Key In Cyber Security
What Is Symmetric Key In Cyber Security - What Is Symmetric Key In Cyber Security, What Is Symmetric Encryption In Cyber Security, What Is Symmetric Key In Information Security, What Is Symmetric Key In Network Security, What Is Symmetric Key Cryptography In Cyber Security, What Is Symmetric Encryption In Network Security, What Is Symmetric Key Distribution In Network Security, What Is Symmetric Key Cryptography In Information Security, What Is Symmetric Key Cryptography, What Is Symmetric Key
Symmetrical symmetric symetric symetrical
Symmetric symmetrical symmetrical
What Is Symmetric Key In Cyber Security include a broad assortment of printable materials available online at no cost. They are available in numerous formats, such as worksheets, templates, coloring pages, and many more. The appealingness of What Is Symmetric Key In Cyber Security is in their versatility and accessibility.
More of What Is Symmetric Key In Cyber Security
What Is Zero Knowledge Encryption Chainlink Blog
What Is Zero Knowledge Encryption Chainlink Blog
portA portA portA symmetric NAT symmetric
Udp Symmetric NAT udp Symmetric
Printables that are free have gained enormous popularity because of a number of compelling causes:
-
Cost-Efficiency: They eliminate the need to purchase physical copies or costly software.
-
Customization: Your HTML0 customization options allow you to customize printed materials to meet your requirements be it designing invitations and schedules, or even decorating your house.
-
Educational value: Printables for education that are free offer a wide range of educational content for learners from all ages, making them a vital resource for educators and parents.
-
The convenience of Access to the vast array of design and templates reduces time and effort.
Where to Find more What Is Symmetric Key In Cyber Security
Symmetric And Asymmetric Key Cryptography The Key Differences Explained

Symmetric And Asymmetric Key Cryptography The Key Differences Explained
2 Transactions on Symmetric Cryptology IACR FSE 2016 ToSC 3 Transactions on Cryptographic Hardware and Embedded
webster symmetrical
Since we've got your curiosity about What Is Symmetric Key In Cyber Security and other printables, let's discover where you can find these elusive treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy offer a huge selection and What Is Symmetric Key In Cyber Security for a variety applications.
- Explore categories such as the home, decor, management, and craft.
2. Educational Platforms
- Forums and websites for education often provide free printable worksheets with flashcards and other teaching tools.
- Ideal for teachers, parents and students who are in need of supplementary resources.
3. Creative Blogs
- Many bloggers share their innovative designs or templates for download.
- These blogs cover a broad variety of topics, all the way from DIY projects to party planning.
Maximizing What Is Symmetric Key In Cyber Security
Here are some unique ways that you can make use of printables for free:
1. Home Decor
- Print and frame gorgeous images, quotes, as well as seasonal decorations, to embellish your living spaces.
2. Education
- Print out free worksheets and activities to enhance your learning at home, or even in the classroom.
3. Event Planning
- Design invitations, banners, as well as decorations for special occasions such as weddings or birthdays.
4. Organization
- Keep your calendars organized by printing printable calendars or to-do lists. meal planners.
Conclusion
What Is Symmetric Key In Cyber Security are an abundance of fun and practical tools that satisfy a wide range of requirements and pursuits. Their availability and versatility make them an invaluable addition to any professional or personal life. Explore the plethora of What Is Symmetric Key In Cyber Security today and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables actually available for download?
- Yes you can! You can print and download these files for free.
-
Are there any free printables for commercial purposes?
- It's dependent on the particular usage guidelines. Always review the terms of use for the creator prior to printing printables for commercial projects.
-
Are there any copyright concerns with What Is Symmetric Key In Cyber Security?
- Some printables could have limitations concerning their use. Always read the terms and regulations provided by the author.
-
How do I print printables for free?
- Print them at home using either a printer or go to any local print store for better quality prints.
-
What software must I use to open printables at no cost?
- A majority of printed materials are with PDF formats, which can be opened using free software, such as Adobe Reader.
The Ultimate Guide To Symmetric Encryption
What Is Symmetric Key Cryptography Encryption Security Wiki

Check more sample of What Is Symmetric Key In Cyber Security below
The Key Differences Between Symmetric VS Asymmetric Encryption Cyber

Symmetric Encryption How To Ensure Security At A Faster Pace
DAY 4 IT IT

Encryption A Beginner s Guide Start Learning With StorMagic
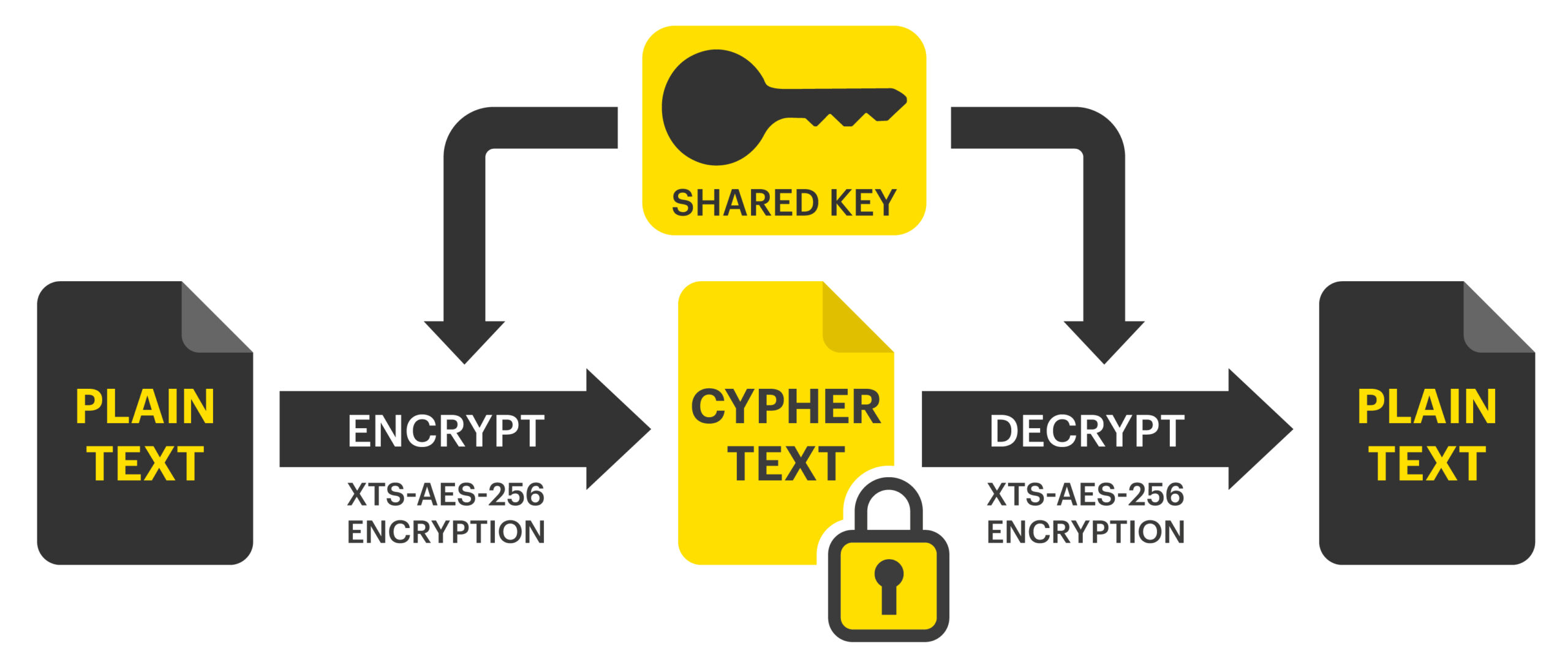
Encryption And Decryption Jean s Blog

Symmetric Vs Asymmetric Encryption Differences Explained


https://zhidao.baidu.com › question
Symmetric symmetrical symmetrical
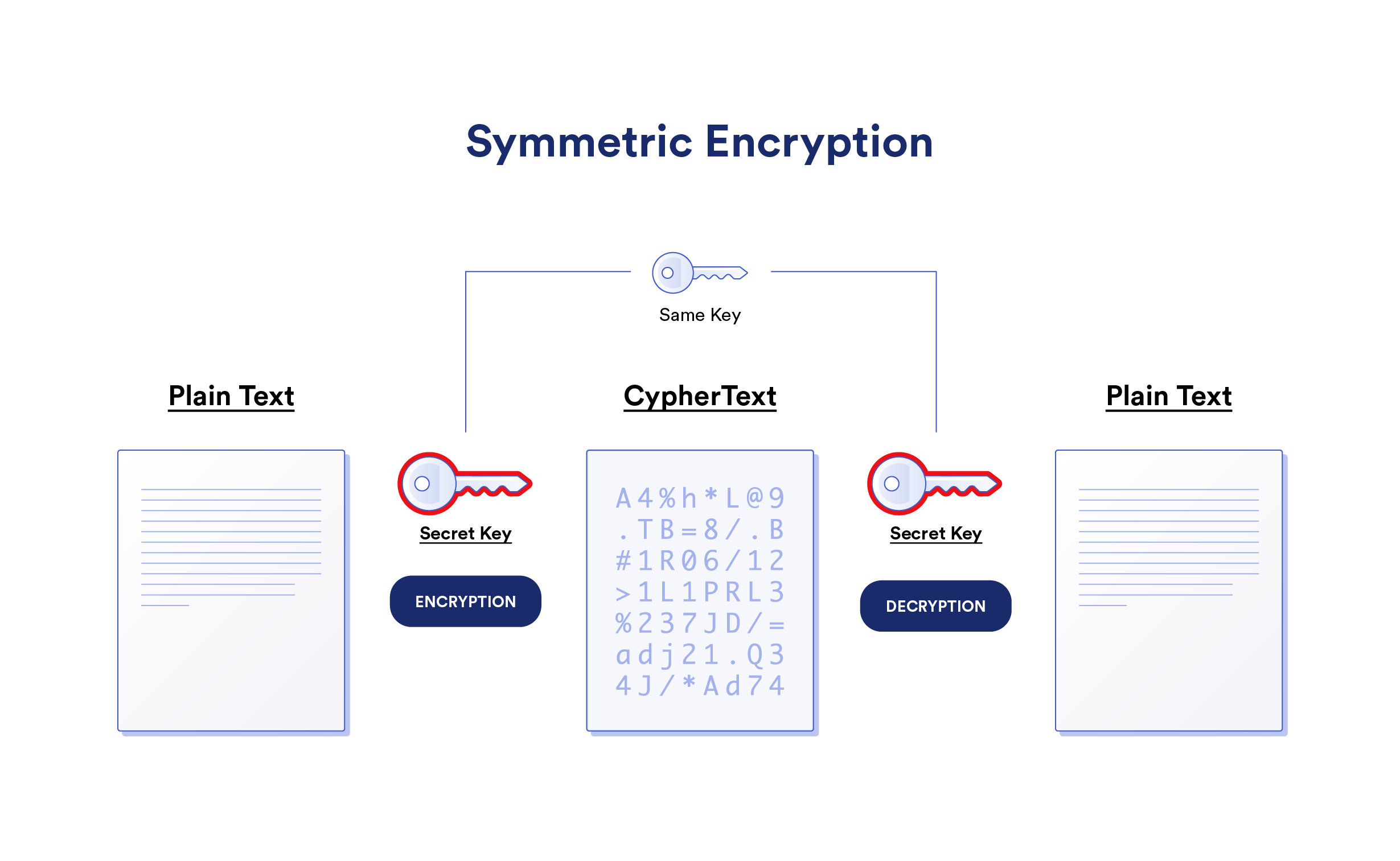
https://www.zhihu.com › question
NAPT Cone Symmetric NAT Client A Client A 1235 NAT
Symmetric symmetrical symmetrical
NAPT Cone Symmetric NAT Client A Client A 1235 NAT

Encryption A Beginner s Guide Start Learning With StorMagic

Symmetric Encryption How To Ensure Security At A Faster Pace

Encryption And Decryption Jean s Blog

Symmetric Vs Asymmetric Encryption Differences Explained
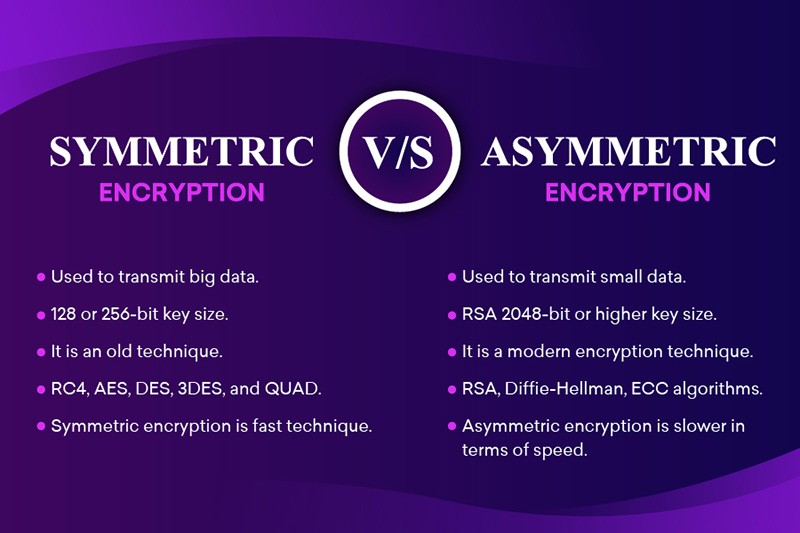
Symmetric And Asymmetric Encryption
What Is Cryptography In Security What Are The Different Types Of

What Is Cryptography In Security What Are The Different Types Of

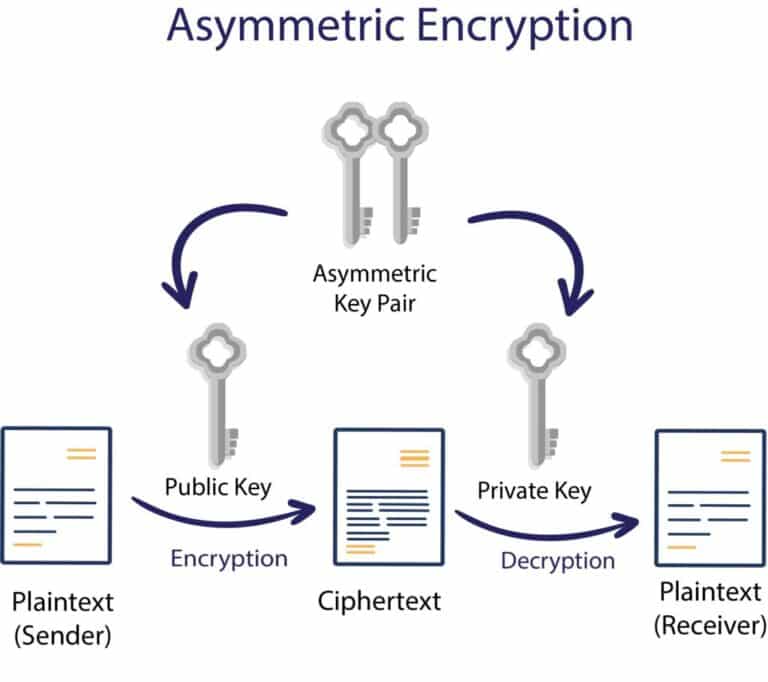
Asymmetric Encryption How Asymmetric Encryption Works