In the age of digital, where screens rule our lives it's no wonder that the appeal of tangible printed material hasn't diminished. Whether it's for educational purposes in creative or artistic projects, or just adding an extra personal touch to your home, printables for free have proven to be a valuable resource. We'll take a dive deeper into "What Is Symmetric Key Cryptography In Information Security," exploring their purpose, where they are available, and what they can do to improve different aspects of your daily life.
Get Latest What Is Symmetric Key Cryptography In Information Security Below
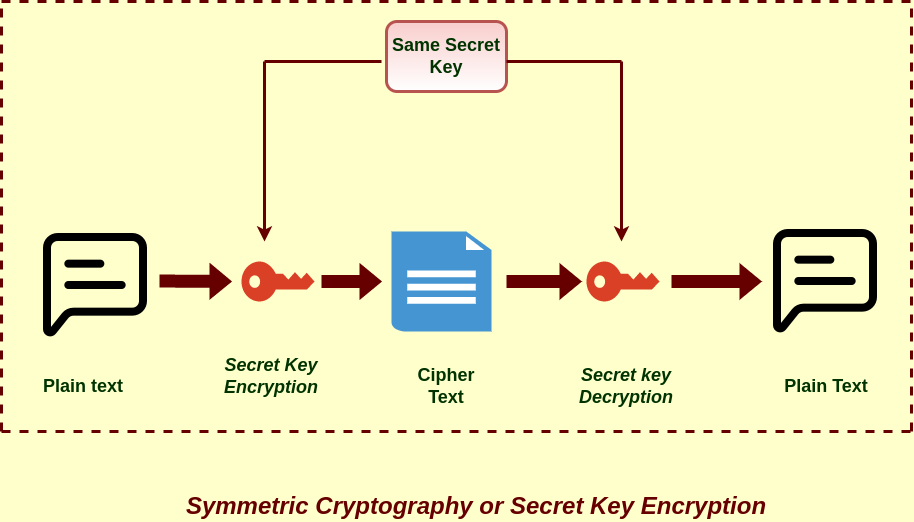
What Is Symmetric Key Cryptography In Information Security
What Is Symmetric Key Cryptography In Information Security - What Is Symmetric Key Cryptography In Information Security, What Is Symmetric Key Cryptography In Cyber Security, Symmetric Key Cryptography In Network Security, What Is Symmetric Encryption In Cyber Security, What Is Symmetric Encryption In Network Security, What Is Symmetric Key Cryptography, How Many Keys Are Used In Symmetric Cryptography
Symmetrical symmetric symetric symetrical
Symmetric symmetrical symmetrical
Printables for free cover a broad collection of printable materials online, at no cost. They come in many kinds, including worksheets templates, coloring pages and more. The value of What Is Symmetric Key Cryptography In Information Security is their flexibility and accessibility.
More of What Is Symmetric Key Cryptography In Information Security
An Exploration Of Symmetric Key Cryptography History Working And

An Exploration Of Symmetric Key Cryptography History Working And
portA portA portA symmetric NAT symmetric
Udp Symmetric NAT udp Symmetric
What Is Symmetric Key Cryptography In Information Security have gained immense popularity because of a number of compelling causes:
-
Cost-Effective: They eliminate the necessity to purchase physical copies or costly software.
-
Modifications: We can customize printables to your specific needs whether you're designing invitations planning your schedule or even decorating your house.
-
Educational Value: These What Is Symmetric Key Cryptography In Information Security offer a wide range of educational content for learners from all ages, making these printables a powerful tool for parents and educators.
-
Convenience: immediate access numerous designs and templates helps save time and effort.
Where to Find more What Is Symmetric Key Cryptography In Information Security
What Is Symmetric Key Cryptography Encryption Security Wiki

What Is Symmetric Key Cryptography Encryption Security Wiki
2 Transactions on Symmetric Cryptology IACR FSE 2016 ToSC 3 Transactions on Cryptographic Hardware and Embedded
webster symmetrical
Now that we've ignited your curiosity about What Is Symmetric Key Cryptography In Information Security we'll explore the places you can get these hidden gems:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy offer a huge selection of printables that are free for a variety of goals.
- Explore categories like design, home decor, management, and craft.
2. Educational Platforms
- Educational websites and forums frequently provide free printable worksheets with flashcards and other teaching tools.
- Perfect for teachers, parents and students looking for extra sources.
3. Creative Blogs
- Many bloggers share their creative designs with templates and designs for free.
- The blogs covered cover a wide spectrum of interests, including DIY projects to planning a party.
Maximizing What Is Symmetric Key Cryptography In Information Security
Here are some creative ways of making the most of printables that are free:
1. Home Decor
- Print and frame stunning art, quotes, as well as seasonal decorations, to embellish your living areas.
2. Education
- Use printable worksheets for free to build your knowledge at home, or even in the classroom.
3. Event Planning
- Create invitations, banners, and other decorations for special occasions such as weddings, birthdays, and other special occasions.
4. Organization
- Stay organized by using printable calendars checklists for tasks, as well as meal planners.
Conclusion
What Is Symmetric Key Cryptography In Information Security are a treasure trove of fun and practical tools catering to different needs and passions. Their accessibility and flexibility make they a beneficial addition to both personal and professional life. Explore the vast array of What Is Symmetric Key Cryptography In Information Security today to open up new possibilities!
Frequently Asked Questions (FAQs)
-
Are What Is Symmetric Key Cryptography In Information Security really are they free?
- Yes they are! You can download and print these tools for free.
-
Can I use the free printouts for commercial usage?
- It is contingent on the specific usage guidelines. Be sure to read the rules of the creator before using any printables on commercial projects.
-
Are there any copyright concerns when using printables that are free?
- Certain printables may be subject to restrictions concerning their use. Make sure to read the terms and conditions offered by the creator.
-
How can I print What Is Symmetric Key Cryptography In Information Security?
- You can print them at home using your printer or visit a local print shop to purchase more high-quality prints.
-
What software will I need to access printables free of charge?
- A majority of printed materials are in PDF format. These is open with no cost software like Adobe Reader.
Concept Of Cryptography In Blockchain

Encryption Choices Rsa Vs Aes Explained Prey

Check more sample of What Is Symmetric Key Cryptography In Information Security below
What Is Zero Knowledge Encryption Chainlink Blog
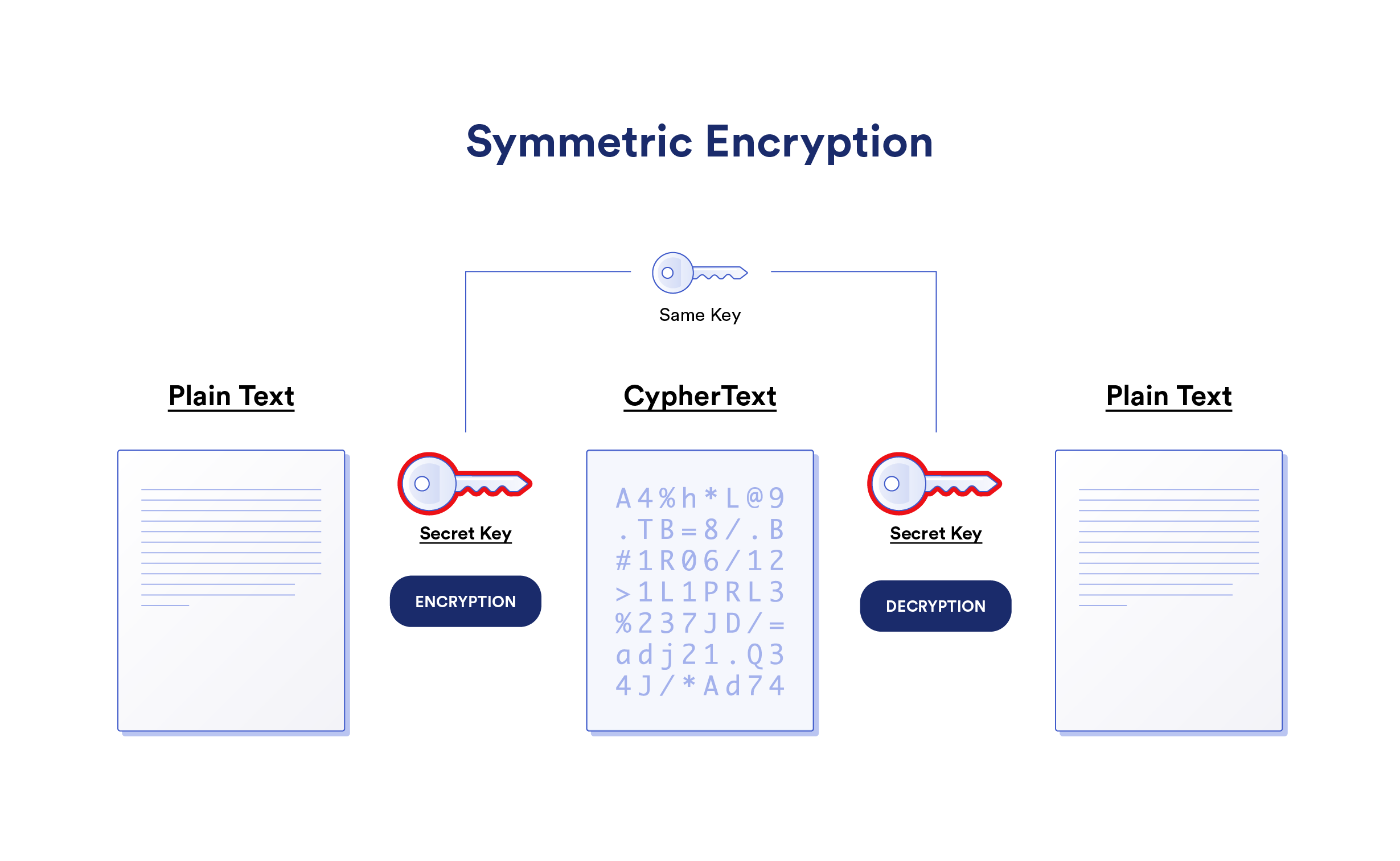
Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Chirag s Blog Difference Between Symmetric And Asymmetric Key

Public Key Cryptography Basics Site Reliability Engineering

What Is Cryptography In Security What Are The Different Types Of
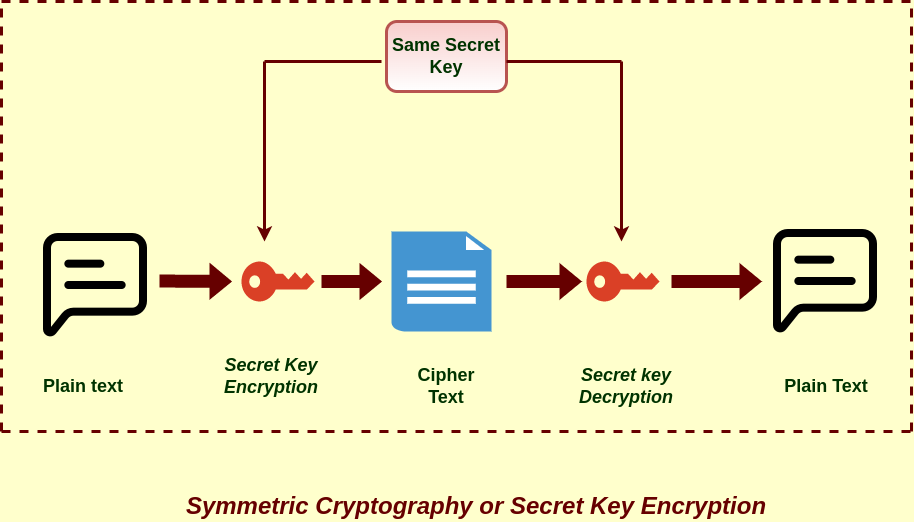
Symmetric Key Encryption Complete Guide To Symmetric Key Encryption

https://zhidao.baidu.com › question
Symmetric symmetrical symmetrical

https://www.zhihu.com › question
NAPT Cone Symmetric NAT Client A Client A 1235 NAT
Symmetric symmetrical symmetrical
NAPT Cone Symmetric NAT Client A Client A 1235 NAT

Public Key Cryptography Basics Site Reliability Engineering

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

What Is Cryptography In Security What Are The Different Types Of

Symmetric Key Encryption Complete Guide To Symmetric Key Encryption

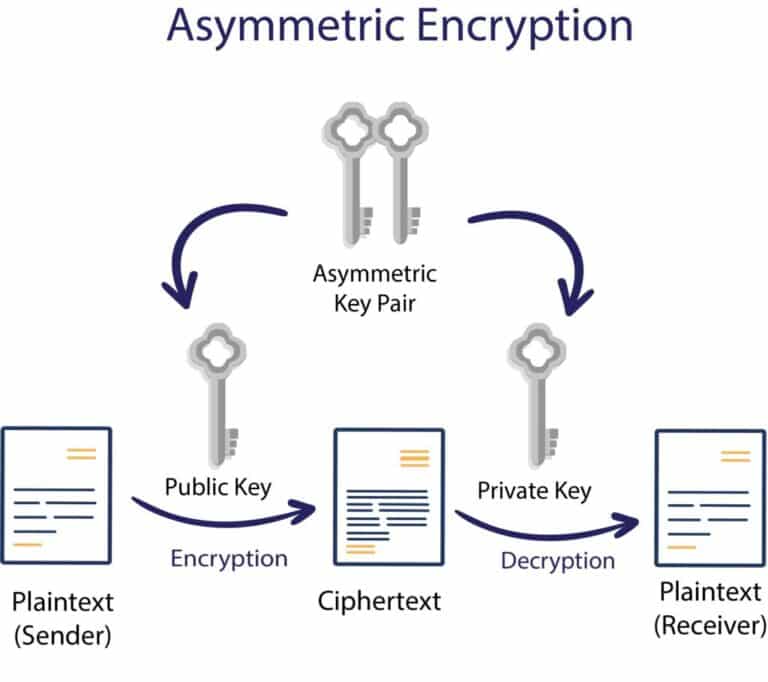
Asymmetric Encryption How Asymmetric Encryption Works

The Complete Cryptography Guide Asymmetric Vs Symmetric Encryption

The Complete Cryptography Guide Asymmetric Vs Symmetric Encryption

Symmetric Key Cryptography Stream Cipher Block Cipher Explained