In this day and age with screens dominating our lives however, the attraction of tangible printed materials isn't diminishing. In the case of educational materials as well as creative projects or simply adding a personal touch to your space, What Is Encryption In Cyber Security With Example are now an essential resource. With this guide, you'll take a dive deeper into "What Is Encryption In Cyber Security With Example," exploring what they are, how to get them, as well as the ways that they can benefit different aspects of your daily life.
Get Latest What Is Encryption In Cyber Security With Example Below

What Is Encryption In Cyber Security With Example
What Is Encryption In Cyber Security With Example - What Is Encryption In Cyber Security With Example, What Is Cryptography In Cyber Security With Example, What Is Cryptography In Network Security With Example, What Is Encryption In Cyber Security, Types Of Encryption In Cyber Security, What Is Encryption In Information Security, What Is Encryption And Decryption In Cyber Security, What Is Encryption In Network Security
CSDN opengauss warning opengauss warning
ESP32 pico D4 ESP IDF IDF monitor WARNING GDB cannot open serial ports accessed as COMx
What Is Encryption In Cyber Security With Example cover a large range of printable, free materials that are accessible online for free cost. They are available in numerous styles, from worksheets to coloring pages, templates and many more. The beauty of What Is Encryption In Cyber Security With Example lies in their versatility and accessibility.
More of What Is Encryption In Cyber Security With Example
What Is Encryption YouTube

What Is Encryption YouTube
CSDN matlab matlab matlab
oracle19c demand ORA 28365 23315889 New Datafile is not Encrypted After Offline Tablespace Encryption with compatibility of 11 2 11 2 0 4 170718
What Is Encryption In Cyber Security With Example have garnered immense popularity due to numerous compelling reasons:
-
Cost-Efficiency: They eliminate the necessity of purchasing physical copies or costly software.
-
Personalization This allows you to modify printables to fit your particular needs when it comes to designing invitations making your schedule, or even decorating your home.
-
Educational Benefits: Printing educational materials for no cost are designed to appeal to students of all ages, which makes them a valuable instrument for parents and teachers.
-
The convenience of You have instant access the vast array of design and templates cuts down on time and efforts.
Where to Find more What Is Encryption In Cyber Security With Example
What Is PGP Encryption And How Does It Work 53 OFF
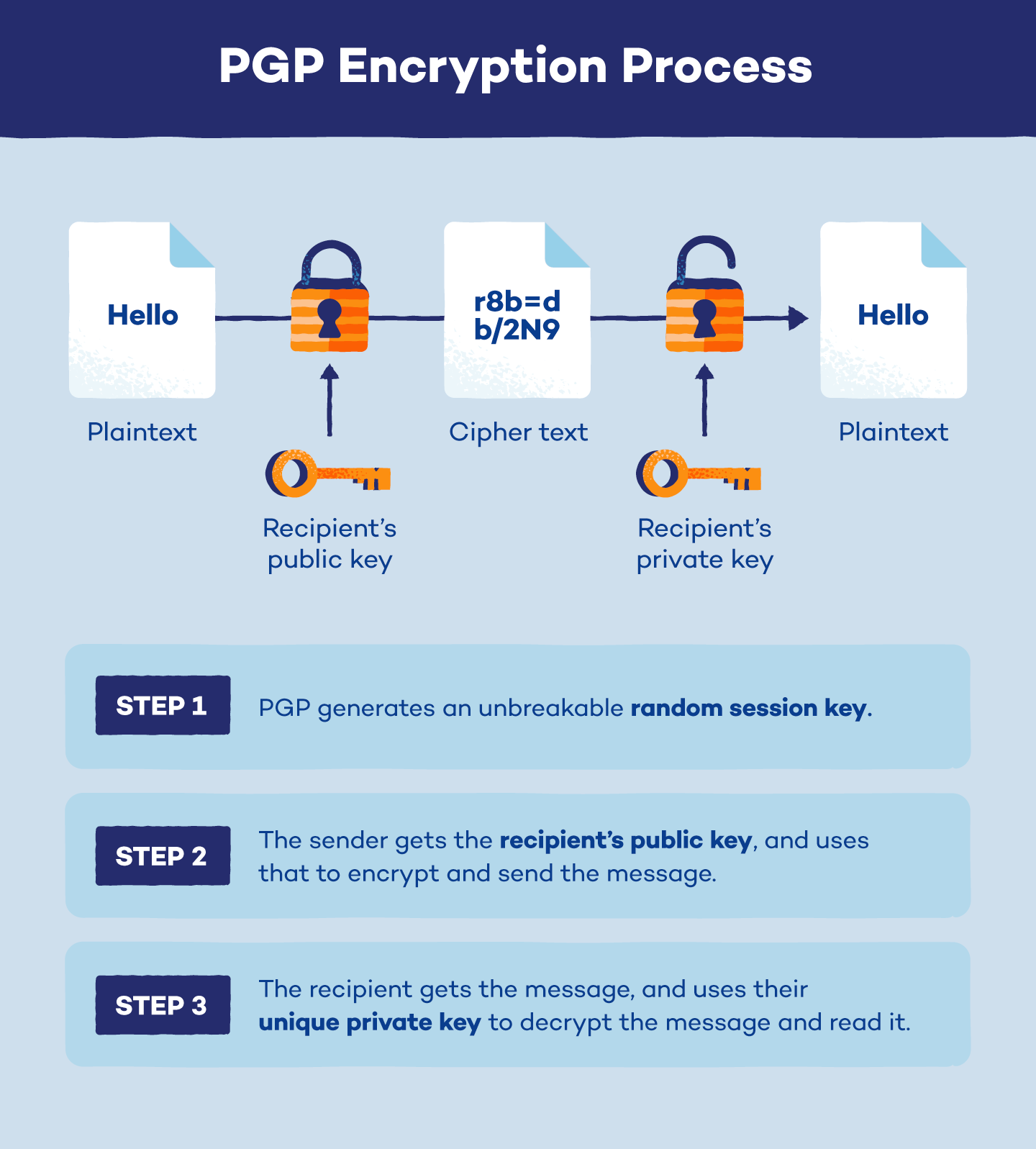
What Is PGP Encryption And How Does It Work 53 OFF
[desc-9]
CSDN OpenSSH KexAlgorithms key exchange algorithm not found
Now that we've ignited your interest in What Is Encryption In Cyber Security With Example Let's take a look at where you can find these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide a wide selection of What Is Encryption In Cyber Security With Example for various purposes.
- Explore categories like decorating your home, education, organizational, and arts and crafts.
2. Educational Platforms
- Forums and websites for education often provide worksheets that can be printed for free with flashcards and other teaching tools.
- This is a great resource for parents, teachers and students looking for extra sources.
3. Creative Blogs
- Many bloggers share their imaginative designs and templates, which are free.
- These blogs cover a broad range of interests, everything from DIY projects to planning a party.
Maximizing What Is Encryption In Cyber Security With Example
Here are some creative ways in order to maximize the use of printables that are free:
1. Home Decor
- Print and frame beautiful art, quotes, as well as seasonal decorations, to embellish your living spaces.
2. Education
- Print worksheets that are free to enhance learning at home or in the classroom.
3. Event Planning
- Designs invitations, banners and other decorations for special occasions like weddings and birthdays.
4. Organization
- Stay organized with printable calendars along with lists of tasks, and meal planners.
Conclusion
What Is Encryption In Cyber Security With Example are a treasure trove of useful and creative resources catering to different needs and hobbies. Their access and versatility makes these printables a useful addition to both professional and personal life. Explore the plethora of What Is Encryption In Cyber Security With Example today and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free cost-free?
- Yes you can! You can print and download these resources at no cost.
-
Do I have the right to use free printables for commercial use?
- It's determined by the specific rules of usage. Always read the guidelines of the creator before using any printables on commercial projects.
-
Do you have any copyright issues when you download printables that are free?
- Some printables may contain restrictions in use. Check the conditions and terms of use provided by the creator.
-
How do I print printables for free?
- You can print them at home with your printer or visit an area print shop for more high-quality prints.
-
What program will I need to access printables that are free?
- Most PDF-based printables are available in PDF format. They can be opened with free software like Adobe Reader.
Rumah Tulisan

Lesson 11 FINAL PROJECT
Check more sample of What Is Encryption In Cyber Security With Example below
Cryptographic Computation Let s Tech It Easy

Cyber Security Board Report Template Prntbl concejomunicipaldechinu
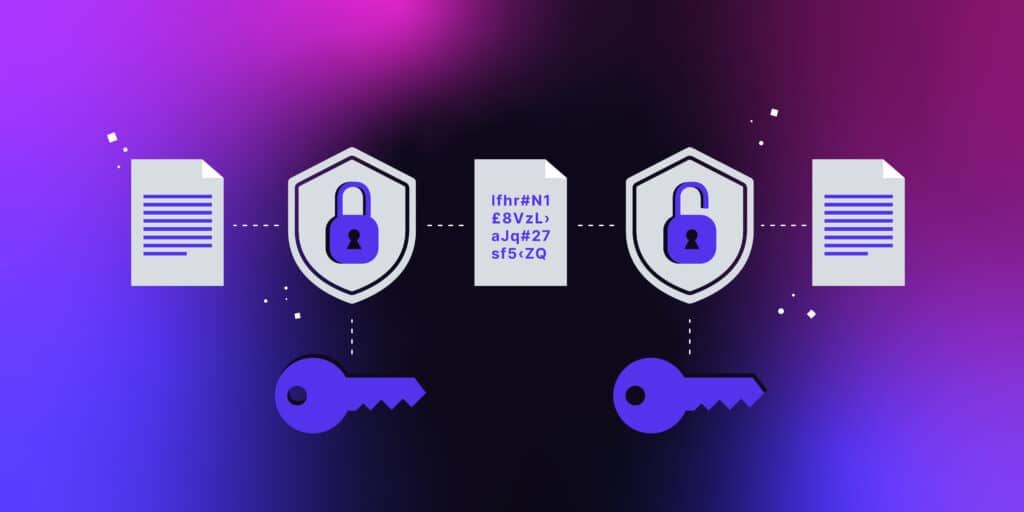
What Is The Role Of Encryption In E Commerce Explain Encryption E
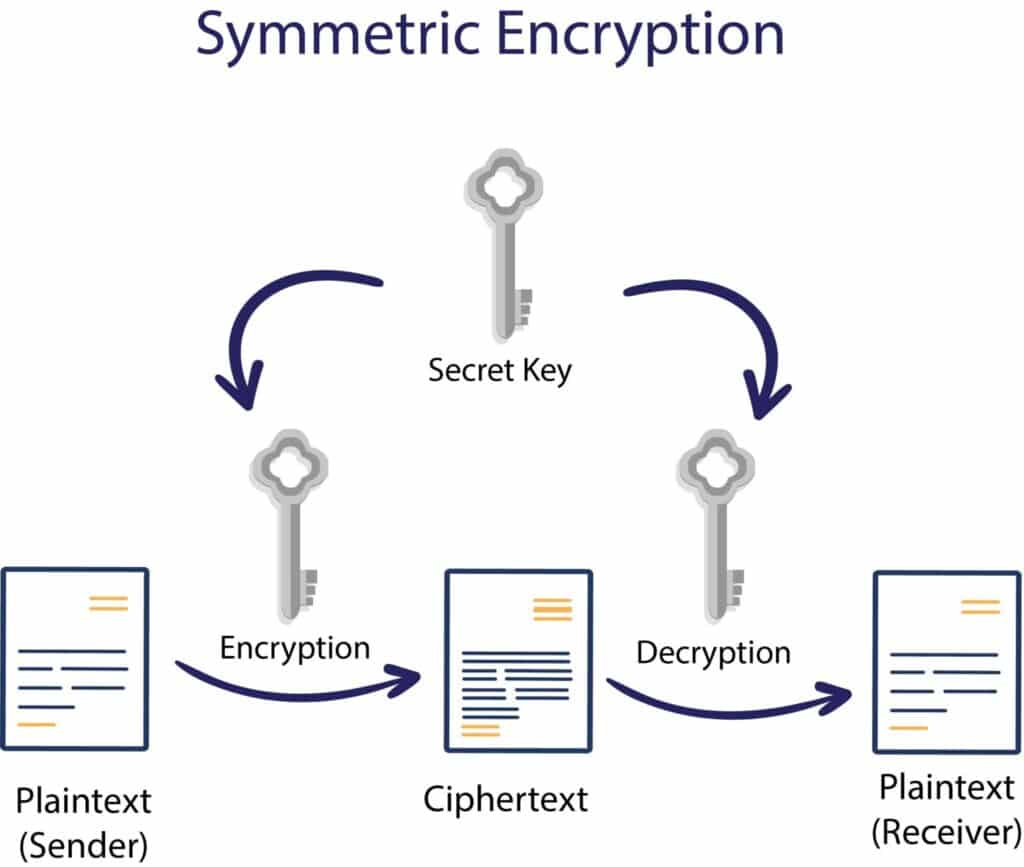
Types And Uses Of Encryption Vrogue co
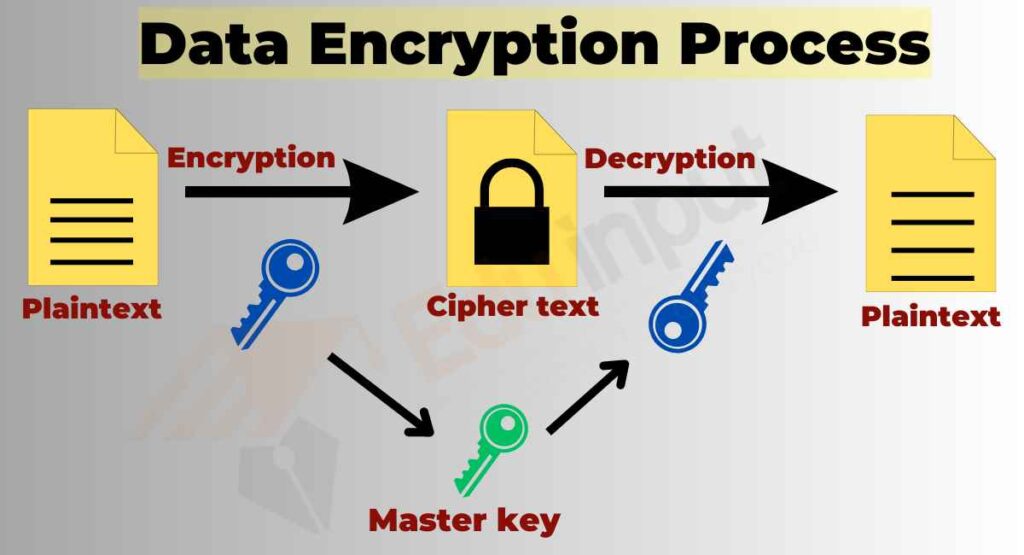
A Beginner s Guide To Understanding Private Keys Helenix

What Types Of Encryption Are There Ico Vrogue co


https://ask.csdn.net › questions
ESP32 pico D4 ESP IDF IDF monitor WARNING GDB cannot open serial ports accessed as COMx

ESP32 pico D4 ESP IDF IDF monitor WARNING GDB cannot open serial ports accessed as COMx
skidrow d empress skidrow unity skidrow

Types And Uses Of Encryption Vrogue co

Cyber Security Board Report Template Prntbl concejomunicipaldechinu

A Beginner s Guide To Understanding Private Keys Helenix

What Types Of Encryption Are There Ico Vrogue co
What Is Encryption How It Works Importance And Types

Affiche De Sensibilisation La Cybers curit Vecteur Premium

Affiche De Sensibilisation La Cybers curit Vecteur Premium

What Is A Red Team In Cyber Security GoGet Secure