In the digital age, where screens have become the dominant feature of our lives yet the appeal of tangible printed materials hasn't faded away. In the case of educational materials project ideas, artistic or simply to add an extra personal touch to your home, printables for free can be an excellent source. Here, we'll dive in the world of "What Is Encryption And Decryption In Cyber Security," exploring the different types of printables, where to locate them, and how they can enhance various aspects of your lives.
Get Latest What Is Encryption And Decryption In Cyber Security Below
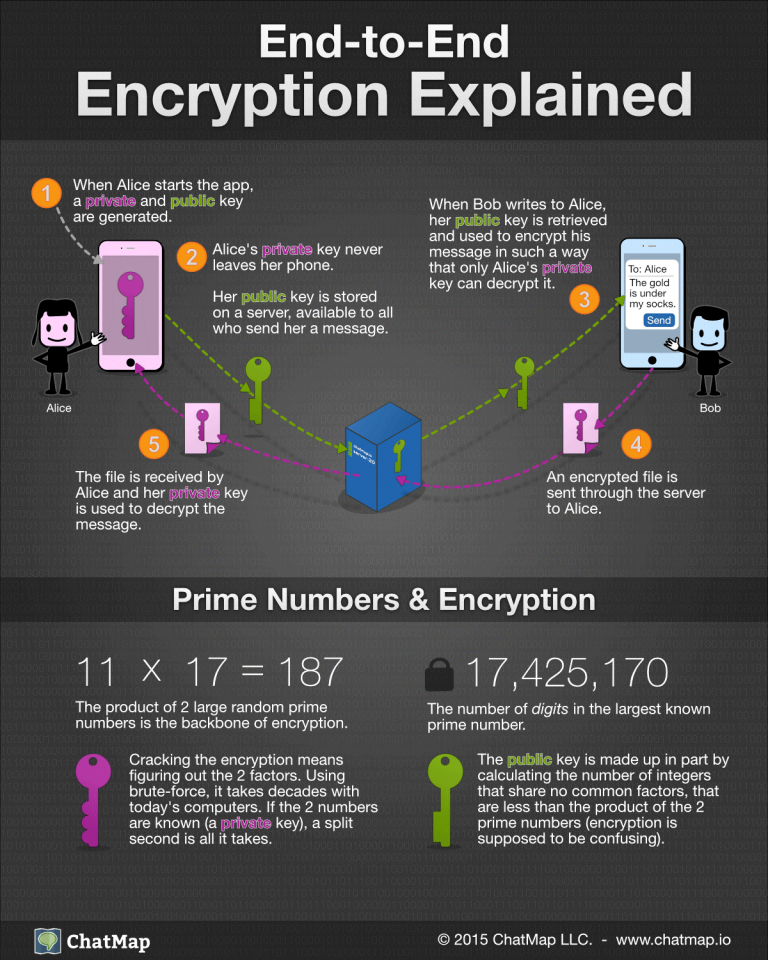
What Is Encryption And Decryption In Cyber Security
What Is Encryption And Decryption In Cyber Security - What Is Encryption And Decryption In Cyber Security, What Is Encryption And Decryption In Computer Security, What Do You Mean By Encryption And Decryption In Cyber Security, Encryption And Decryption In Cyber Security Javatpoint, What Is Encrypt In Cyber Security, What Is Encryption And Decryption In Network Security, What Is Encryption And Decryption In Information Security
CSDN opengauss warning opengauss warning
ESP32 pico D4 ESP IDF IDF monitor WARNING GDB cannot open serial ports accessed as COMx
What Is Encryption And Decryption In Cyber Security provide a diverse variety of printable, downloadable resources available online for download at no cost. These materials come in a variety of forms, like worksheets templates, coloring pages, and many more. The appealingness of What Is Encryption And Decryption In Cyber Security lies in their versatility as well as accessibility.
More of What Is Encryption And Decryption In Cyber Security
Cryptographic Computation Let s Tech It Easy

Cryptographic Computation Let s Tech It Easy
CSDN matlab matlab matlab
oracle19c demand ORA 28365 23315889 New Datafile is not Encrypted After Offline Tablespace Encryption with compatibility of 11 2 11 2 0 4 170718
Printables that are free have gained enormous popularity due to a variety of compelling reasons:
-
Cost-Effective: They eliminate the need to purchase physical copies or costly software.
-
Customization: They can make printed materials to meet your requirements, whether it's designing invitations, organizing your schedule, or even decorating your house.
-
Educational value: Printing educational materials for no cost offer a wide range of educational content for learners from all ages, making them a vital device for teachers and parents.
-
Simple: immediate access an array of designs and templates is time-saving and saves effort.
Where to Find more What Is Encryption And Decryption In Cyber Security
Australia Firms Should Help Authorities Hack Encrypted Messages

Australia Firms Should Help Authorities Hack Encrypted Messages
[desc-9]
CSDN OpenSSH KexAlgorithms key exchange algorithm not found
In the event that we've stirred your curiosity about What Is Encryption And Decryption In Cyber Security, let's explore where you can find these elusive gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a large collection of What Is Encryption And Decryption In Cyber Security for various uses.
- Explore categories like decorating your home, education, organizing, and crafts.
2. Educational Platforms
- Educational websites and forums frequently provide free printable worksheets along with flashcards, as well as other learning materials.
- Ideal for teachers, parents as well as students who require additional sources.
3. Creative Blogs
- Many bloggers are willing to share their original designs and templates free of charge.
- The blogs are a vast spectrum of interests, starting from DIY projects to planning a party.
Maximizing What Is Encryption And Decryption In Cyber Security
Here are some inventive ways that you can make use of printables for free:
1. Home Decor
- Print and frame gorgeous images, quotes, or festive decorations to decorate your living areas.
2. Education
- Use printable worksheets for free for reinforcement of learning at home and in class.
3. Event Planning
- Create invitations, banners, and decorations for special events like birthdays and weddings.
4. Organization
- Keep track of your schedule with printable calendars checklists for tasks, as well as meal planners.
Conclusion
What Is Encryption And Decryption In Cyber Security are an abundance of fun and practical tools that meet a variety of needs and desires. Their access and versatility makes them an invaluable addition to both personal and professional life. Explore the vast array of What Is Encryption And Decryption In Cyber Security now and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables actually absolutely free?
- Yes, they are! You can download and print these files for free.
-
Can I use the free printables for commercial uses?
- It's based on specific conditions of use. Make sure you read the guidelines for the creator before using printables for commercial projects.
-
Do you have any copyright rights issues with What Is Encryption And Decryption In Cyber Security?
- Certain printables may be subject to restrictions regarding their use. Be sure to review these terms and conditions as set out by the designer.
-
How do I print printables for free?
- You can print them at home using either a printer or go to a local print shop to purchase superior prints.
-
What software do I need in order to open printables free of charge?
- The majority are printed as PDF files, which is open with no cost programs like Adobe Reader.
Rsa
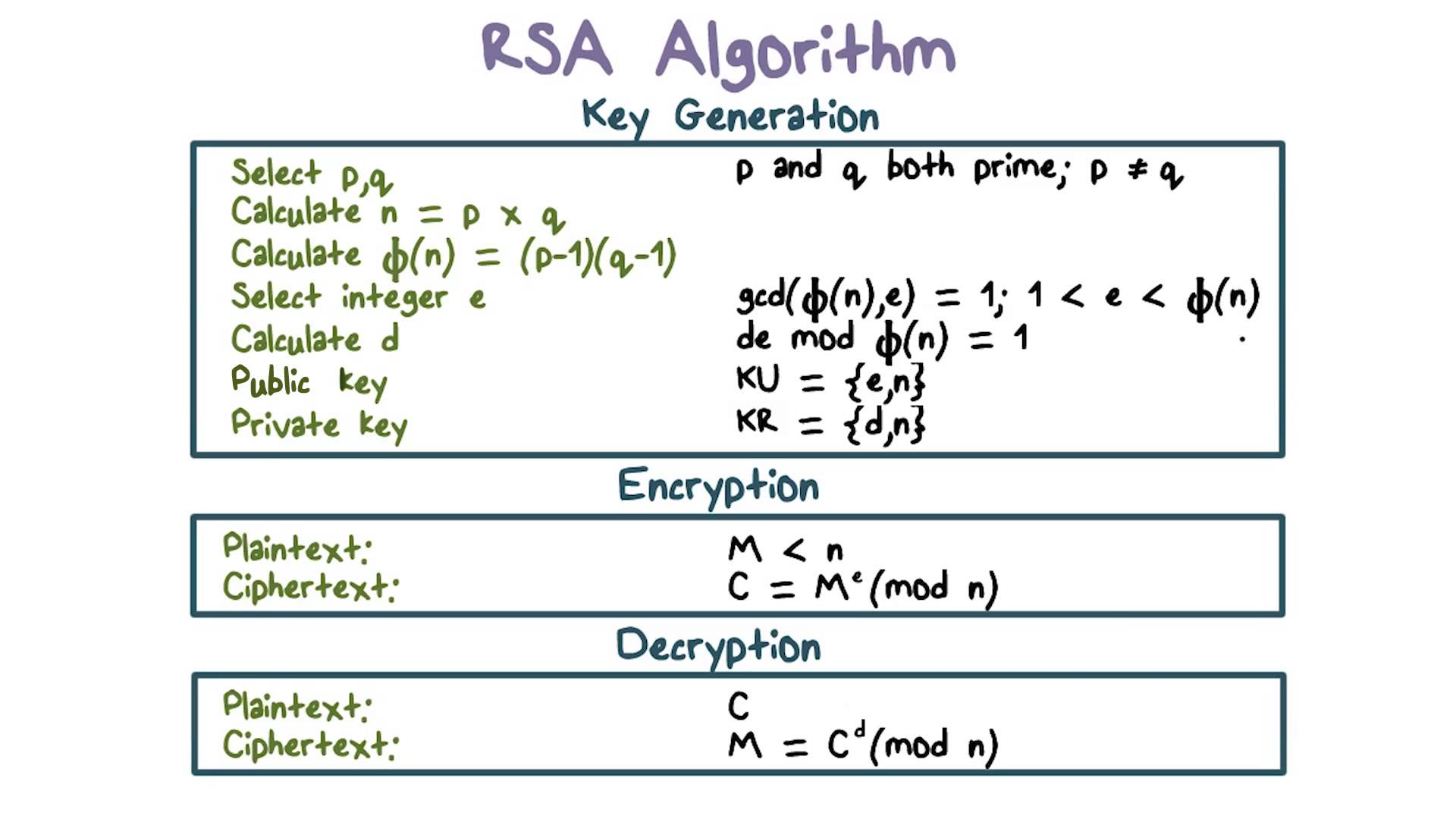
Beginner s Guide To Encryption

Check more sample of What Is Encryption And Decryption In Cyber Security below
Encryption Decryption What Are These Ideatebox

What Is The Role Of Encryption In E Commerce Explain Encryption E
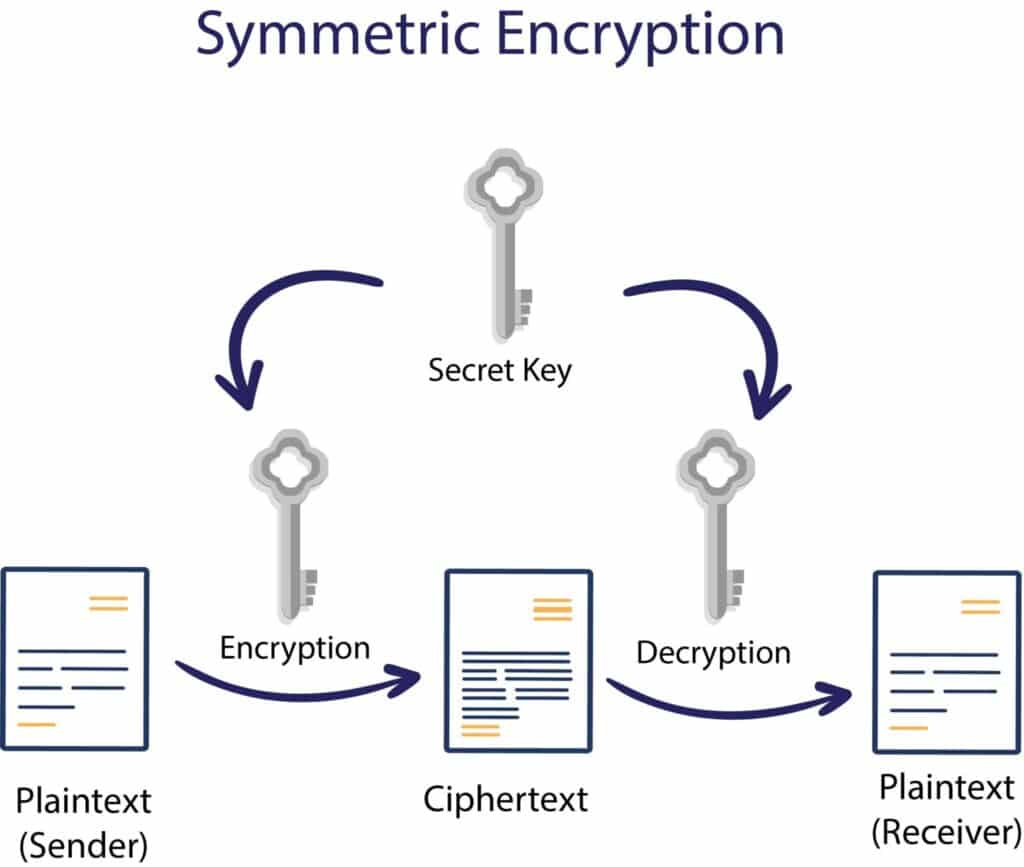
Public Key Cryptography Algorithms

Asymmetric Encryption How Asymmetric Encryption Works

Railway Accounts Department Examinations IREPS
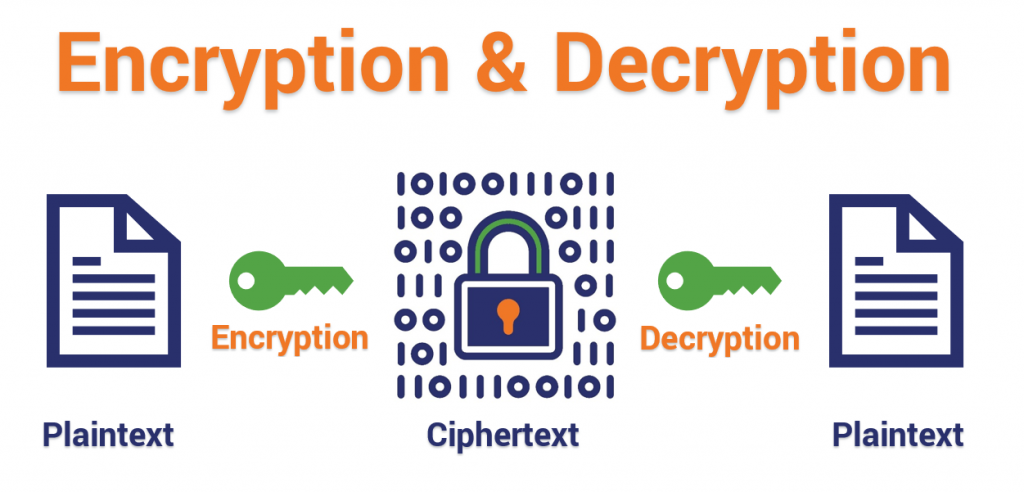
A Beginner s Guide To Understanding Private Keys Helenix

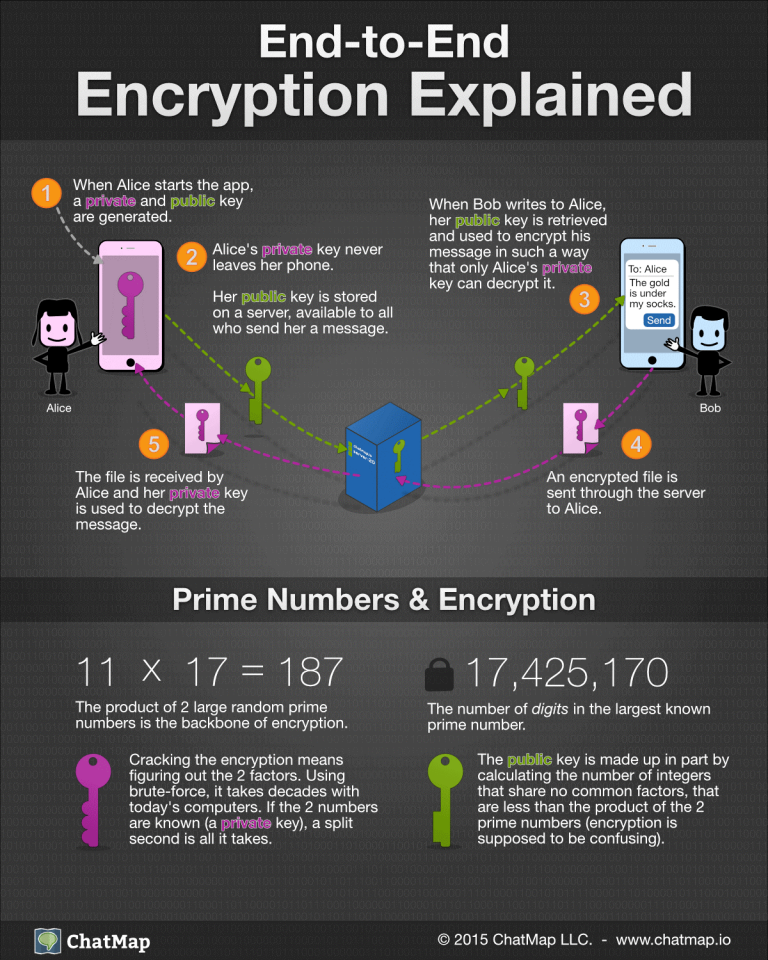
https://ask.csdn.net › questions
ESP32 pico D4 ESP IDF IDF monitor WARNING GDB cannot open serial ports accessed as COMx

ESP32 pico D4 ESP IDF IDF monitor WARNING GDB cannot open serial ports accessed as COMx
skidrow d empress skidrow unity skidrow

Asymmetric Encryption How Asymmetric Encryption Works

What Is The Role Of Encryption In E Commerce Explain Encryption E

Railway Accounts Department Examinations IREPS

A Beginner s Guide To Understanding Private Keys Helenix

What Types Of Encryption Are There Ico Vrogue co
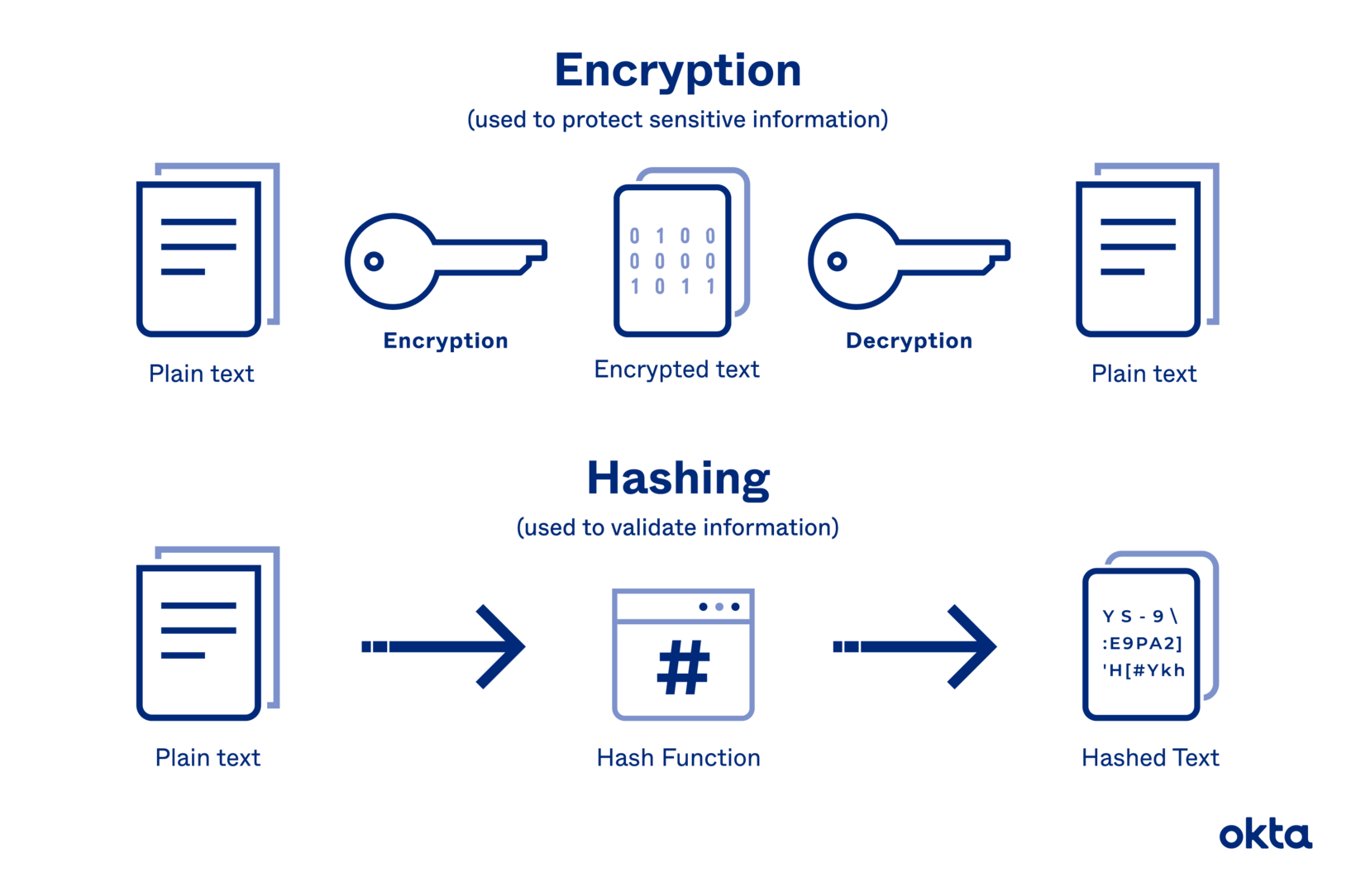
Hashing Vs Encryption Definitions Differences Okta

Hashing Vs Encryption Definitions Differences Okta
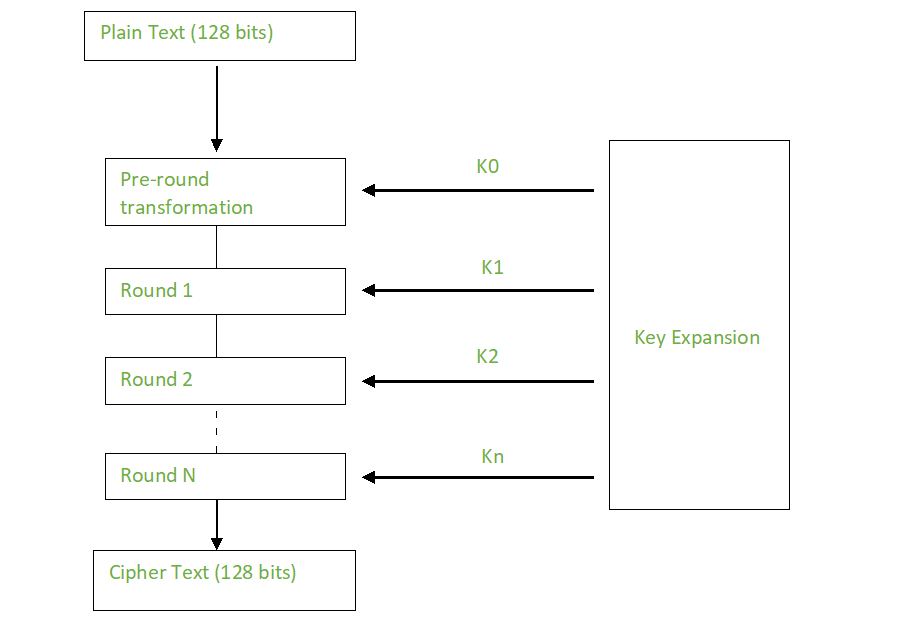
How AES Encryption Is Used In Cybersecurity And Why It Matters AppSealing