In the digital age, where screens have become the dominant feature of our lives however, the attraction of tangible, printed materials hasn't diminished. If it's to aid in education for creative projects, just adding an individual touch to the area, Encryption And Decryption In Cyber Security Javatpoint are now an essential source. Through this post, we'll take a dive deeper into "Encryption And Decryption In Cyber Security Javatpoint," exploring what they are, how you can find them, and how they can add value to various aspects of your life.
Get Latest Encryption And Decryption In Cyber Security Javatpoint Below
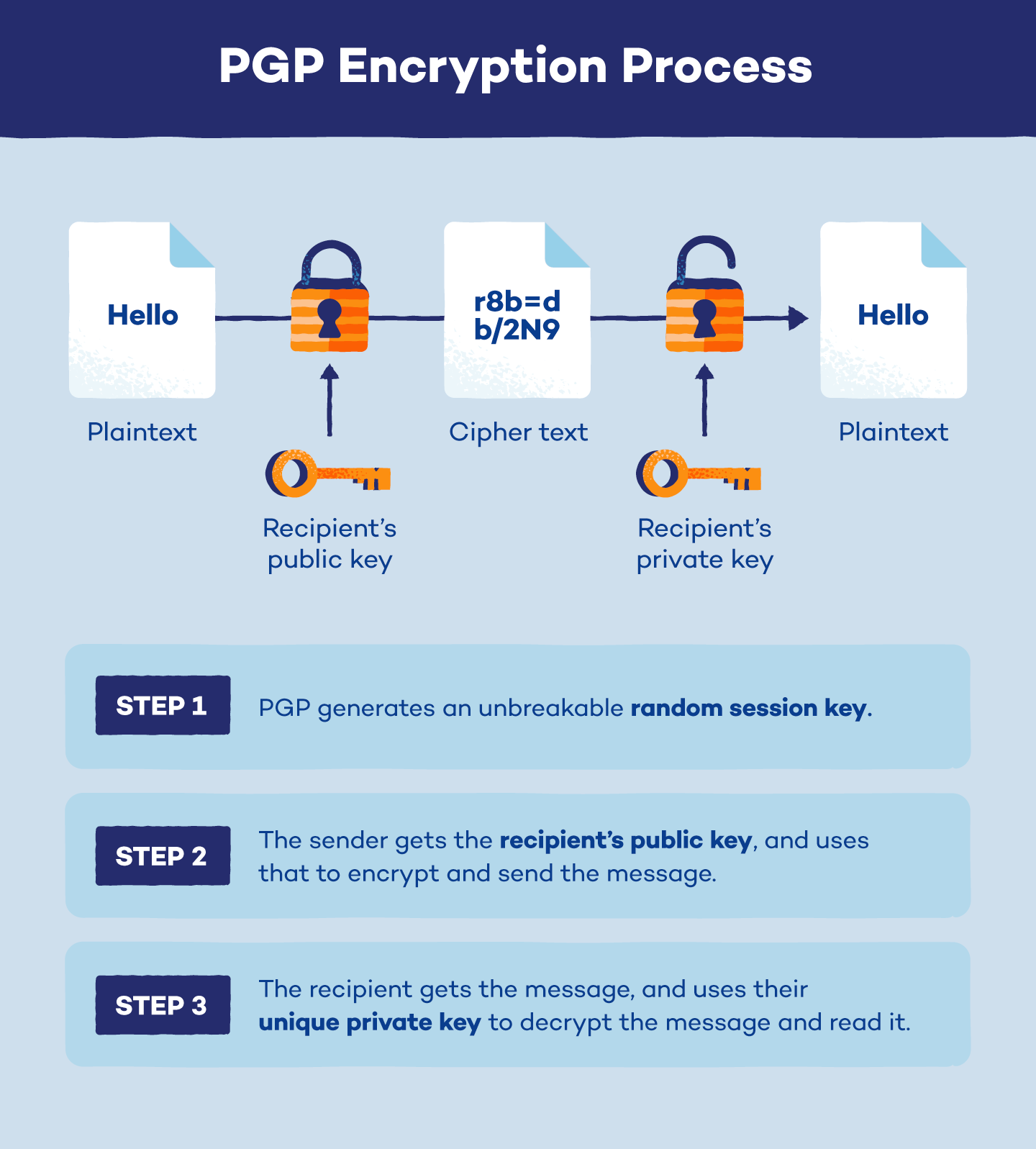
Encryption And Decryption In Cyber Security Javatpoint
Encryption And Decryption In Cyber Security Javatpoint -
CSDN stun v2 dat tvdlps dat stun v2 dat tvdlps dat CSDN
CSDN matlab matlab matlab
The Encryption And Decryption In Cyber Security Javatpoint are a huge range of downloadable, printable materials that are accessible online for free cost. The resources are offered in a variety kinds, including worksheets templates, coloring pages, and many more. The appealingness of Encryption And Decryption In Cyber Security Javatpoint is their flexibility and accessibility.
More of Encryption And Decryption In Cyber Security Javatpoint
Lesson 11 FINAL PROJECT
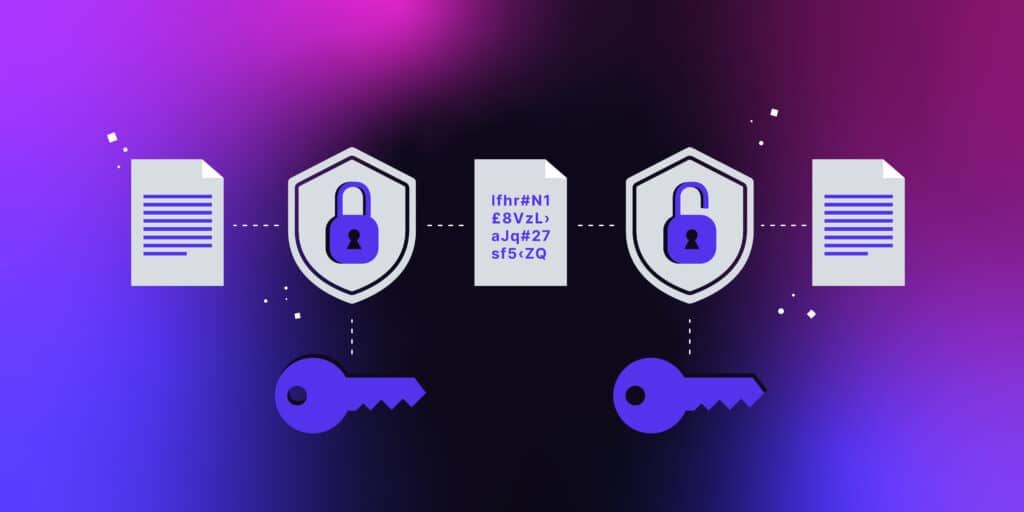
Lesson 11 FINAL PROJECT
CSDN sqlite attach database 26 sqlite attach database
oracle19c demand ORA 28365 23315889 New Datafile is not Encrypted After Offline Tablespace Encryption with compatibility of 11 2 11 2 0 4 170718
Encryption And Decryption In Cyber Security Javatpoint have garnered immense popularity due to a variety of compelling reasons:
-
Cost-Effective: They eliminate the need to buy physical copies or costly software.
-
The ability to customize: There is the possibility of tailoring printing templates to your own specific requirements such as designing invitations as well as organizing your calendar, or decorating your home.
-
Educational Worth: Education-related printables at no charge provide for students from all ages, making them an invaluable device for teachers and parents.
-
Convenience: You have instant access a variety of designs and templates is time-saving and saves effort.
Where to Find more Encryption And Decryption In Cyber Security Javatpoint
Flowchart Of Encryption Process Decryption Download Scientific Diagram

Flowchart Of Encryption Process Decryption Download Scientific Diagram
[desc-9]
CSDN OpenSSH KexAlgorithms key exchange algorithm not found
After we've peaked your interest in Encryption And Decryption In Cyber Security Javatpoint We'll take a look around to see where you can get these hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy have a large selection of Encryption And Decryption In Cyber Security Javatpoint to suit a variety of objectives.
- Explore categories such as design, home decor, craft, and organization.
2. Educational Platforms
- Educational websites and forums frequently offer free worksheets and worksheets for printing for flashcards, lessons, and worksheets. materials.
- Great for parents, teachers or students in search of additional sources.
3. Creative Blogs
- Many bloggers offer their unique designs with templates and designs for free.
- These blogs cover a wide range of topics, from DIY projects to party planning.
Maximizing Encryption And Decryption In Cyber Security Javatpoint
Here are some creative ways for you to get the best use of printables that are free:
1. Home Decor
- Print and frame stunning artwork, quotes, or other seasonal decorations to fill your living areas.
2. Education
- Use these printable worksheets free of charge to help reinforce your learning at home either in the schoolroom or at home.
3. Event Planning
- Designs invitations, banners and other decorations for special occasions like weddings and birthdays.
4. Organization
- Make sure you are organized with printable calendars checklists for tasks, as well as meal planners.
Conclusion
Encryption And Decryption In Cyber Security Javatpoint are a treasure trove of useful and creative resources catering to different needs and passions. Their availability and versatility make they a beneficial addition to your professional and personal life. Explore the endless world that is Encryption And Decryption In Cyber Security Javatpoint today, and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free gratis?
- Yes, they are! You can print and download these resources at no cost.
-
Does it allow me to use free templates for commercial use?
- It's determined by the specific terms of use. Always review the terms of use for the creator before using printables for commercial projects.
-
Do you have any copyright violations with printables that are free?
- Some printables could have limitations on their use. Always read the terms and condition of use as provided by the designer.
-
How can I print Encryption And Decryption In Cyber Security Javatpoint?
- Print them at home with any printer or head to a local print shop for high-quality prints.
-
What software do I need in order to open printables free of charge?
- The majority of PDF documents are provided in the PDF format, and can be opened using free software like Adobe Reader.
Encryption Techniques

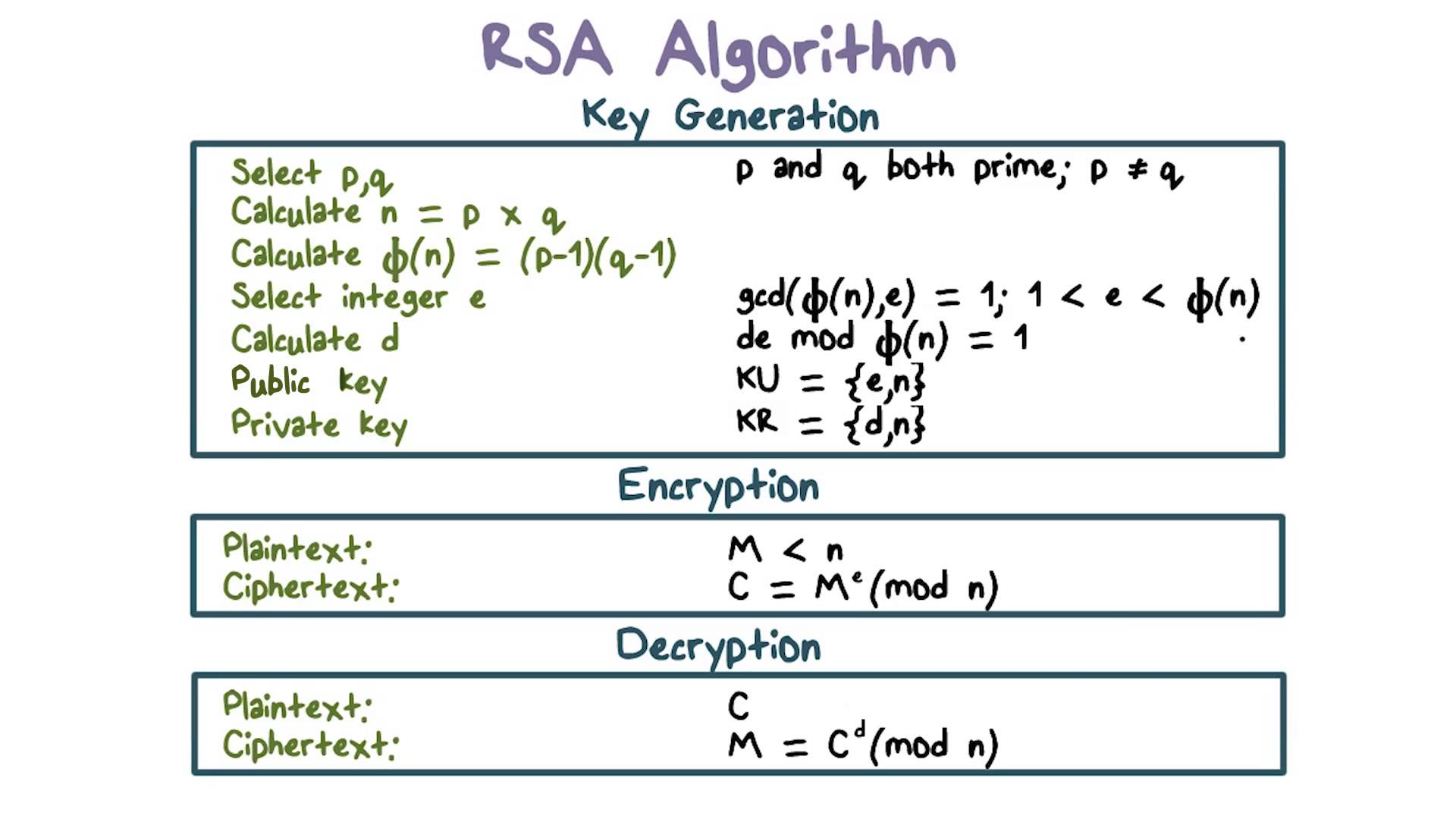
Rsa
Check more sample of Encryption And Decryption In Cyber Security Javatpoint below
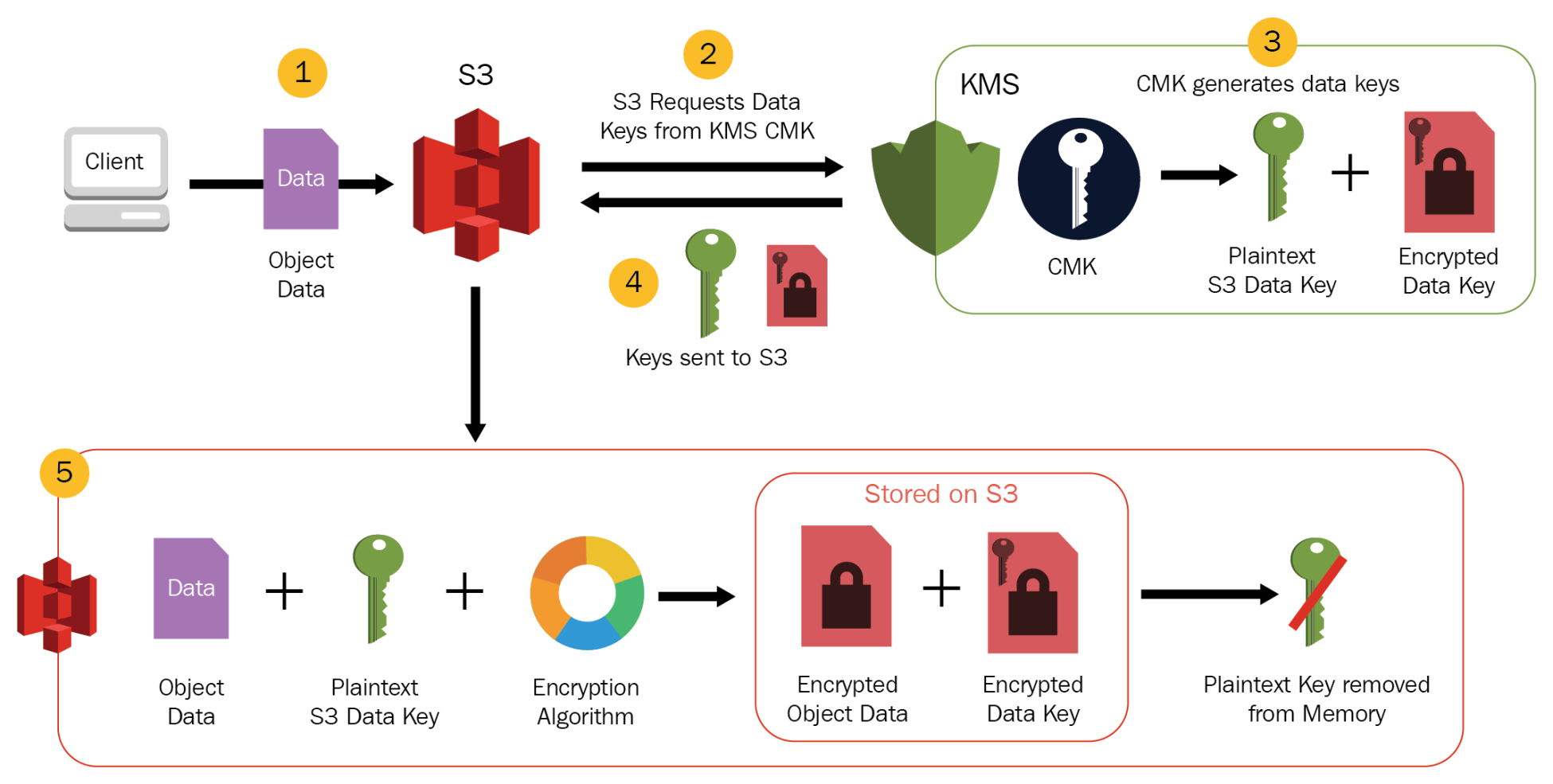
AWS SAA S3 Encryption
Encryption Decryption What Are These Ideatebox

Types And Uses Of Encryption Vrogue co
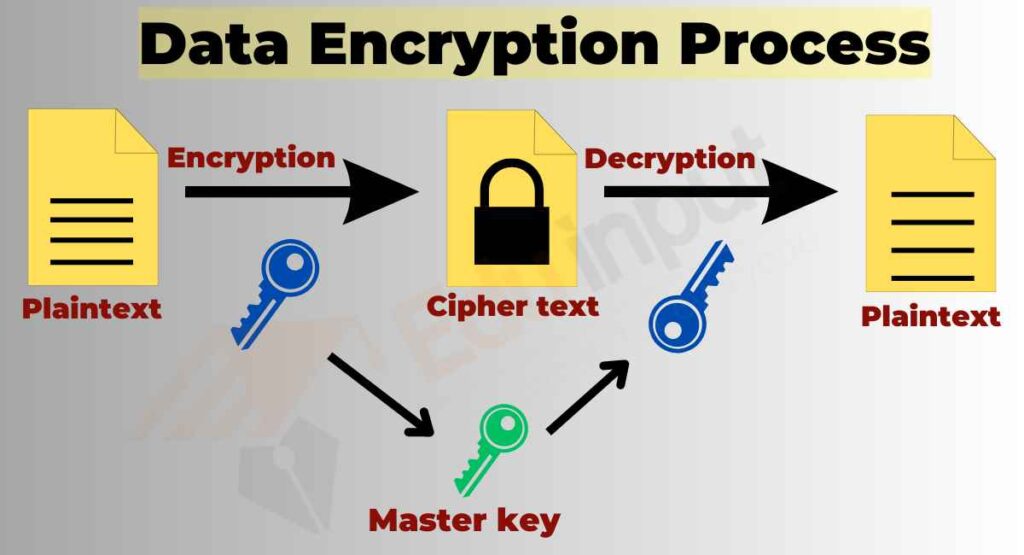
Asymmetric Encryption How Asymmetric Encryption Works

A Beginner s Guide To Understanding Private Keys Helenix

Information Security Vs Cybersecurity Which Should Districts Prioritize
/AL_14-Blog02-4.jpg?width=1350&height=1350&name=AL_14-Blog02-4.jpg)
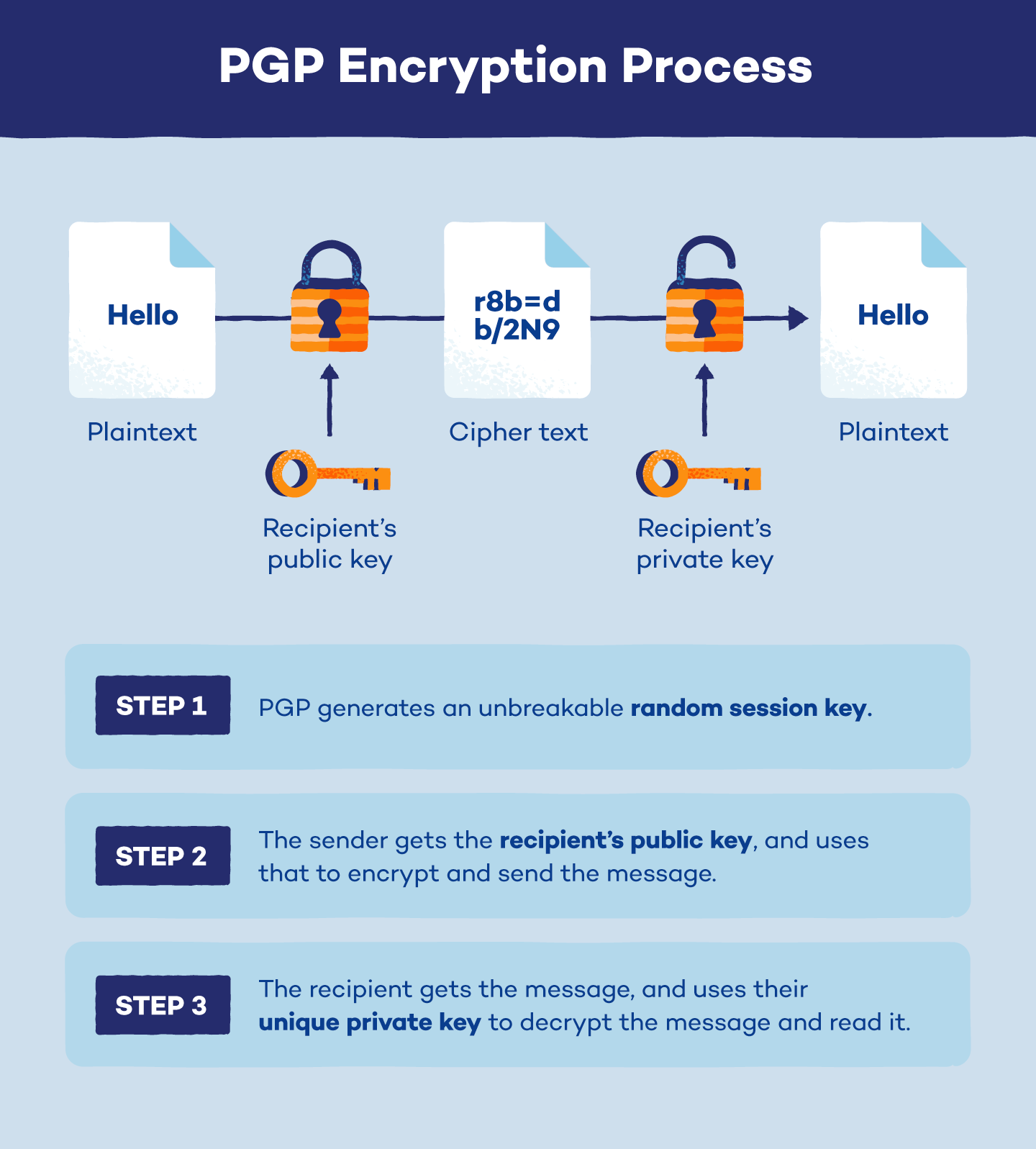
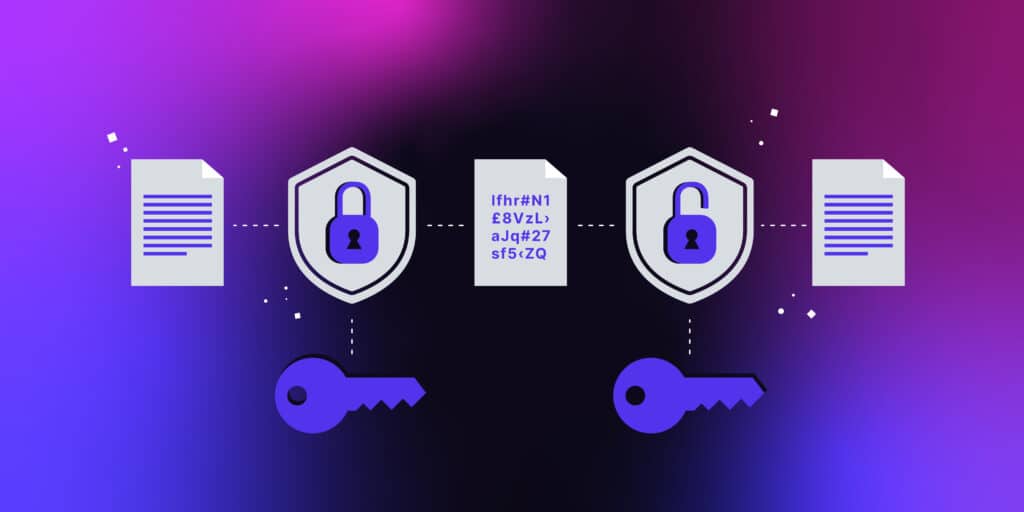
https://ask.csdn.net › questions
ESP32 pico D4 ESP IDF IDF monitor WARNING GDB cannot open serial ports accessed as COMx
CSDN matlab matlab matlab
ESP32 pico D4 ESP IDF IDF monitor WARNING GDB cannot open serial ports accessed as COMx

Asymmetric Encryption How Asymmetric Encryption Works

Encryption Decryption What Are These Ideatebox

A Beginner s Guide To Understanding Private Keys Helenix
/AL_14-Blog02-4.jpg?width=1350&height=1350&name=AL_14-Blog02-4.jpg)
Information Security Vs Cybersecurity Which Should Districts Prioritize

What Is Secret Key Cryptography A Complete Guide Helenix

What Types Of Encryption Are There Ico Vrogue co

What Types Of Encryption Are There Ico Vrogue co
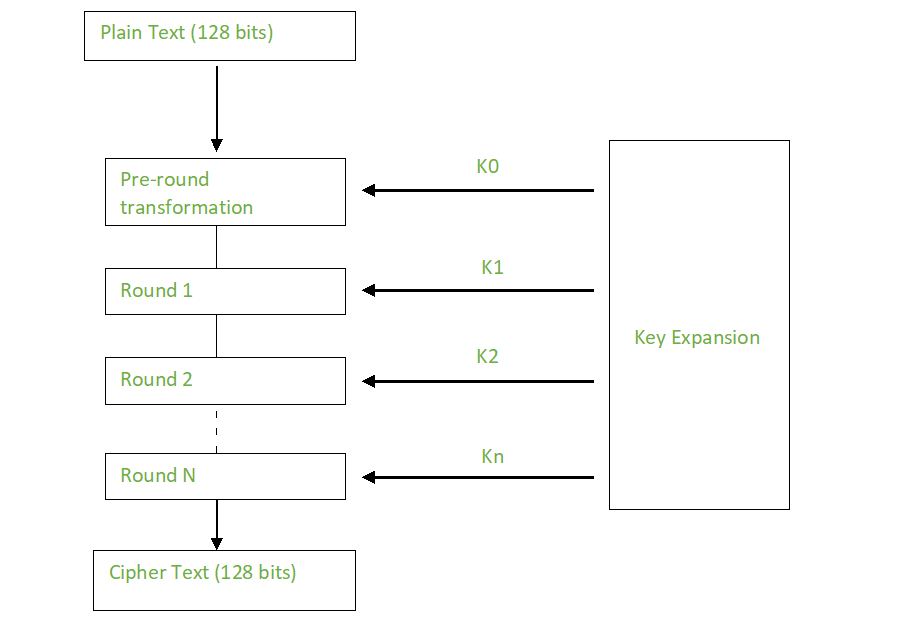
How AES Encryption Is Used In Cybersecurity And Why It Matters AppSealing