In this age of technology, when screens dominate our lives and our lives are dominated by screens, the appeal of tangible, printed materials hasn't diminished. Whether it's for educational purposes project ideas, artistic or simply adding an element of personalization to your home, printables for free are now a vital resource. Through this post, we'll take a dive through the vast world of "What Is Encryption Cyber Security," exploring the benefits of them, where you can find them, and how they can be used to enhance different aspects of your daily life.
Get Latest What Is Encryption Cyber Security Below
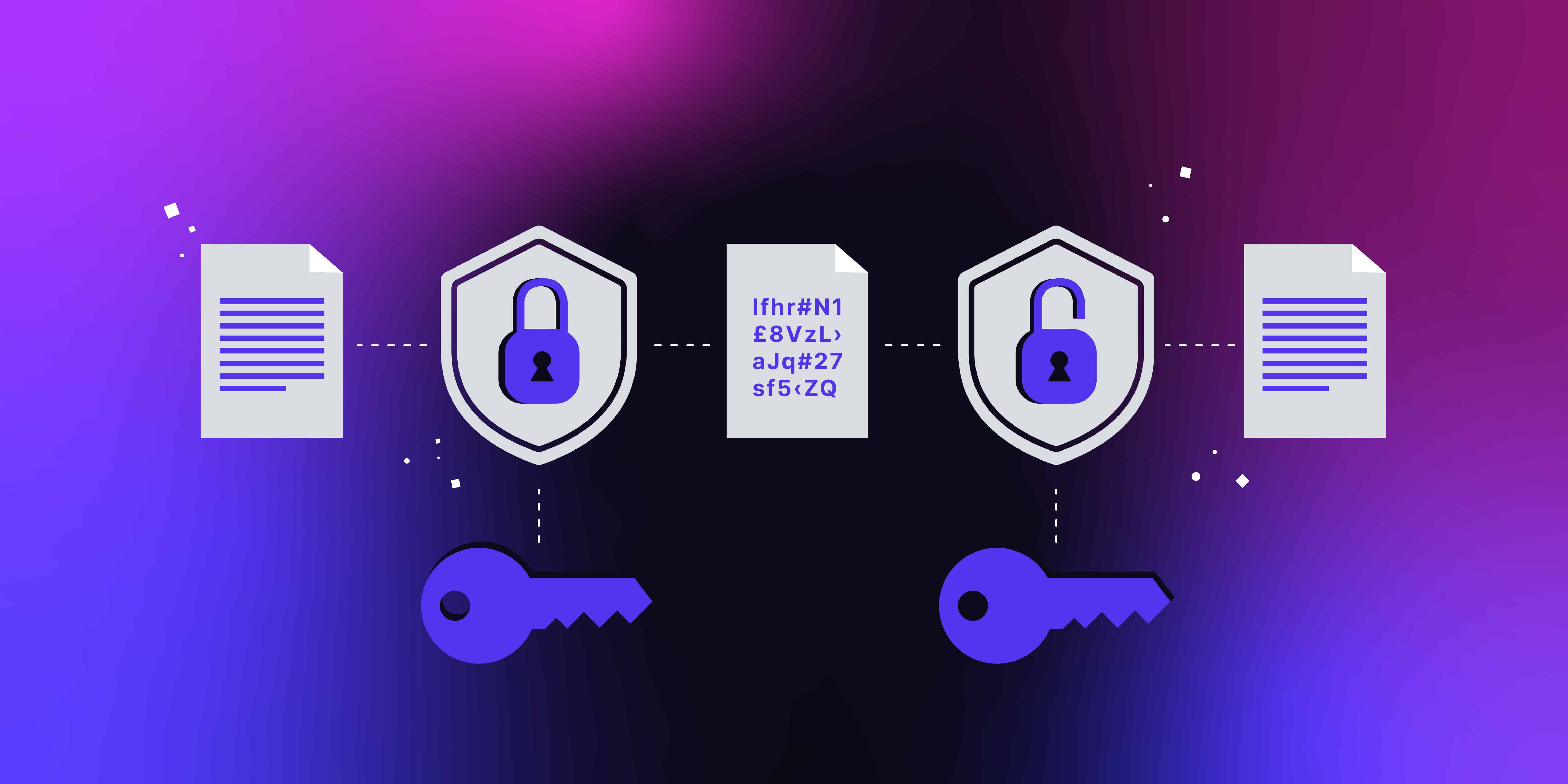
What Is Encryption Cyber Security
What Is Encryption Cyber Security - What Is Encryption Cyber Security, What Is Cryptography Cyber Security, What Is Encryption Network Security, What Is Cryptography Network Security, What Is Encryption Algorithm In Cyber Security, What Is Cryptography In Cyber Security In Hindi, What Is Cryptography In Cyber Security With Example, What Is Symmetric Encryption In Cyber Security, What Is Encryption And Decryption In Cyber Security, What Is Asymmetric Encryption In Cyber Security
CSDN Pads Logic Pads Logic
CSDN matlab matlab matlab
What Is Encryption Cyber Security offer a wide variety of printable, downloadable materials available online at no cost. They come in many kinds, including worksheets coloring pages, templates and many more. The beauty of What Is Encryption Cyber Security is their flexibility and accessibility.
More of What Is Encryption Cyber Security
Encryption Encoding And Hashing Explained

Encryption Encoding And Hashing Explained
Xshell No matching outgoing encryption algorithm found 2019 11 17 22 55 Lanje Wang SSH aes256 ctr
CSDN stun v2 dat tvdlps dat stun v2 dat tvdlps dat CSDN
What Is Encryption Cyber Security have risen to immense popularity due to numerous compelling reasons:
-
Cost-Effective: They eliminate the necessity of purchasing physical copies of the software or expensive hardware.
-
Modifications: It is possible to tailor designs to suit your personal needs such as designing invitations, organizing your schedule, or even decorating your home.
-
Educational Value Education-related printables at no charge are designed to appeal to students from all ages, making them an essential tool for teachers and parents.
-
It's easy: You have instant access various designs and templates helps save time and effort.
Where to Find more What Is Encryption Cyber Security
Encryption Decryption What Are These Ideatebox

Encryption Decryption What Are These Ideatebox
[desc-9]
CSDN Cell not executed due to pending input Cell not executed due to pending input python jupyter
Now that we've ignited your interest in printables for free We'll take a look around to see where you can discover these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide a variety of What Is Encryption Cyber Security to suit a variety of reasons.
- Explore categories like interior decor, education, organization, and crafts.
2. Educational Platforms
- Educational websites and forums usually provide free printable worksheets with flashcards and other teaching tools.
- The perfect resource for parents, teachers and students looking for additional resources.
3. Creative Blogs
- Many bloggers post their original designs and templates free of charge.
- These blogs cover a broad selection of subjects, everything from DIY projects to planning a party.
Maximizing What Is Encryption Cyber Security
Here are some unique ways to make the most of printables for free:
1. Home Decor
- Print and frame gorgeous artwork, quotes or festive decorations to decorate your living areas.
2. Education
- Print out free worksheets and activities for teaching at-home as well as in the class.
3. Event Planning
- Designs invitations, banners and decorations for special occasions such as weddings or birthdays.
4. Organization
- Keep your calendars organized by printing printable calendars checklists for tasks, as well as meal planners.
Conclusion
What Is Encryption Cyber Security are an abundance of fun and practical tools which cater to a wide range of needs and pursuits. Their access and versatility makes them a fantastic addition to each day life. Explore the many options of What Is Encryption Cyber Security today and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables actually gratis?
- Yes they are! You can download and print these resources at no cost.
-
Can I use free printables in commercial projects?
- It's all dependent on the rules of usage. Make sure you read the guidelines for the creator before using their printables for commercial projects.
-
Are there any copyright rights issues with printables that are free?
- Certain printables may be subject to restrictions on usage. Make sure to read the conditions and terms of use provided by the creator.
-
How can I print What Is Encryption Cyber Security?
- You can print them at home using either a printer at home or in a print shop in your area for the highest quality prints.
-
What program do I require to open printables for free?
- A majority of printed materials are in the format PDF. This can be opened with free software, such as Adobe Reader.
Encryption Choices Rsa Vs Aes Explained Prey

What Is Data Encryption Bitdefender Cyberpedia

Check more sample of What Is Encryption Cyber Security below
What Is CRYPTOGRAPHY And Its Types TheCScience

How To Lock And Encrypt Your Personal Data TechStory

What Is Cryptography Cryptographic Algorithms Types Of

How Data Encryption Works Cyber Security Merupakan Teknologi By
Why Hosting Your Own Encryption Keys Is Better For Data Security

10 Tips To Secure Your Personal Data FROMDEV

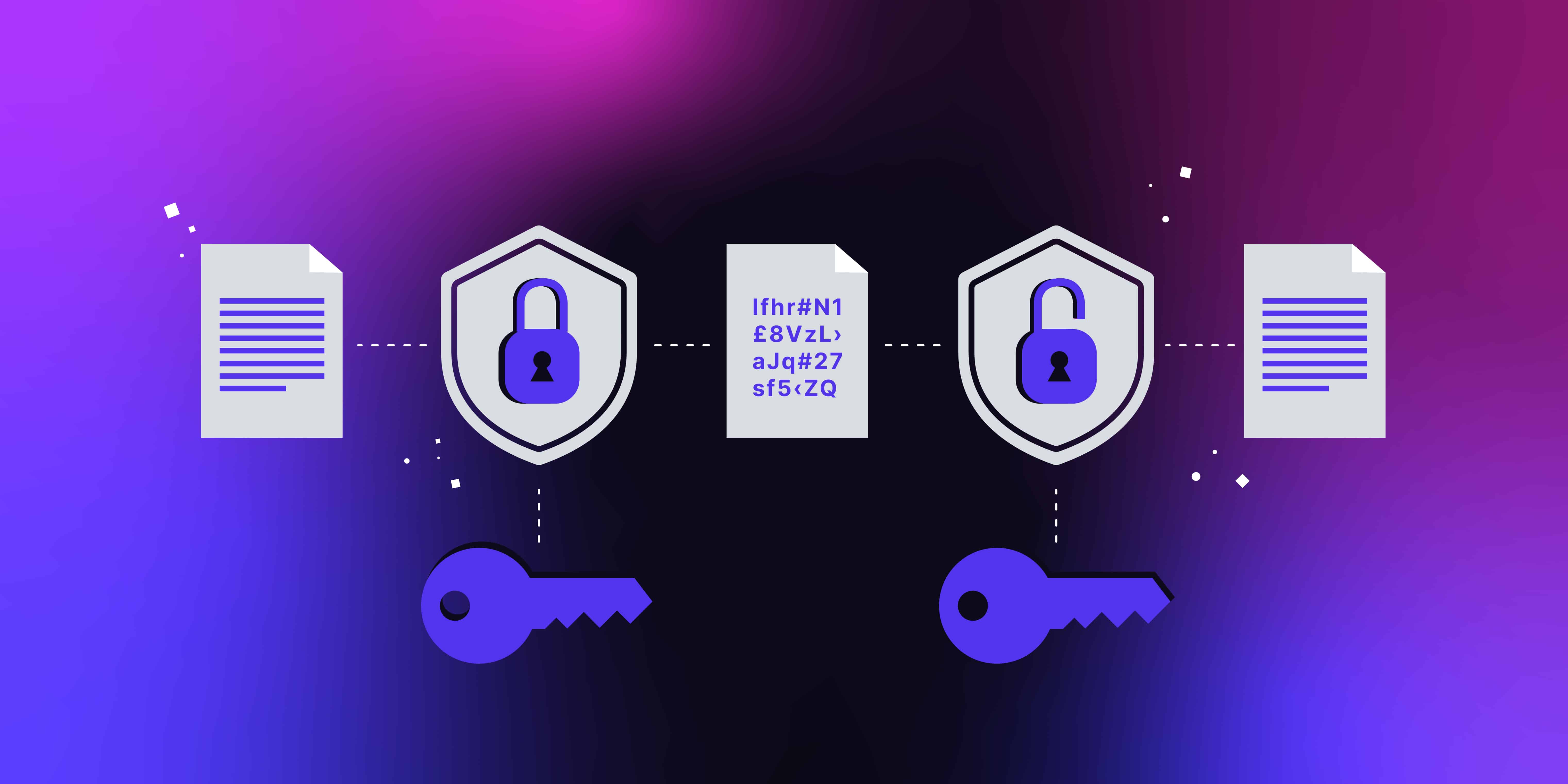

https://ask.csdn.net › questions
ESP32 pico D4 ESP IDF IDF monitor WARNING GDB cannot open serial ports accessed as COMx
CSDN matlab matlab matlab
ESP32 pico D4 ESP IDF IDF monitor WARNING GDB cannot open serial ports accessed as COMx
How Data Encryption Works Cyber Security Merupakan Teknologi By

How To Lock And Encrypt Your Personal Data TechStory

Why Hosting Your Own Encryption Keys Is Better For Data Security

10 Tips To Secure Your Personal Data FROMDEV

What Is Asymmetric Encryption How Does It Work InfoSec Insights
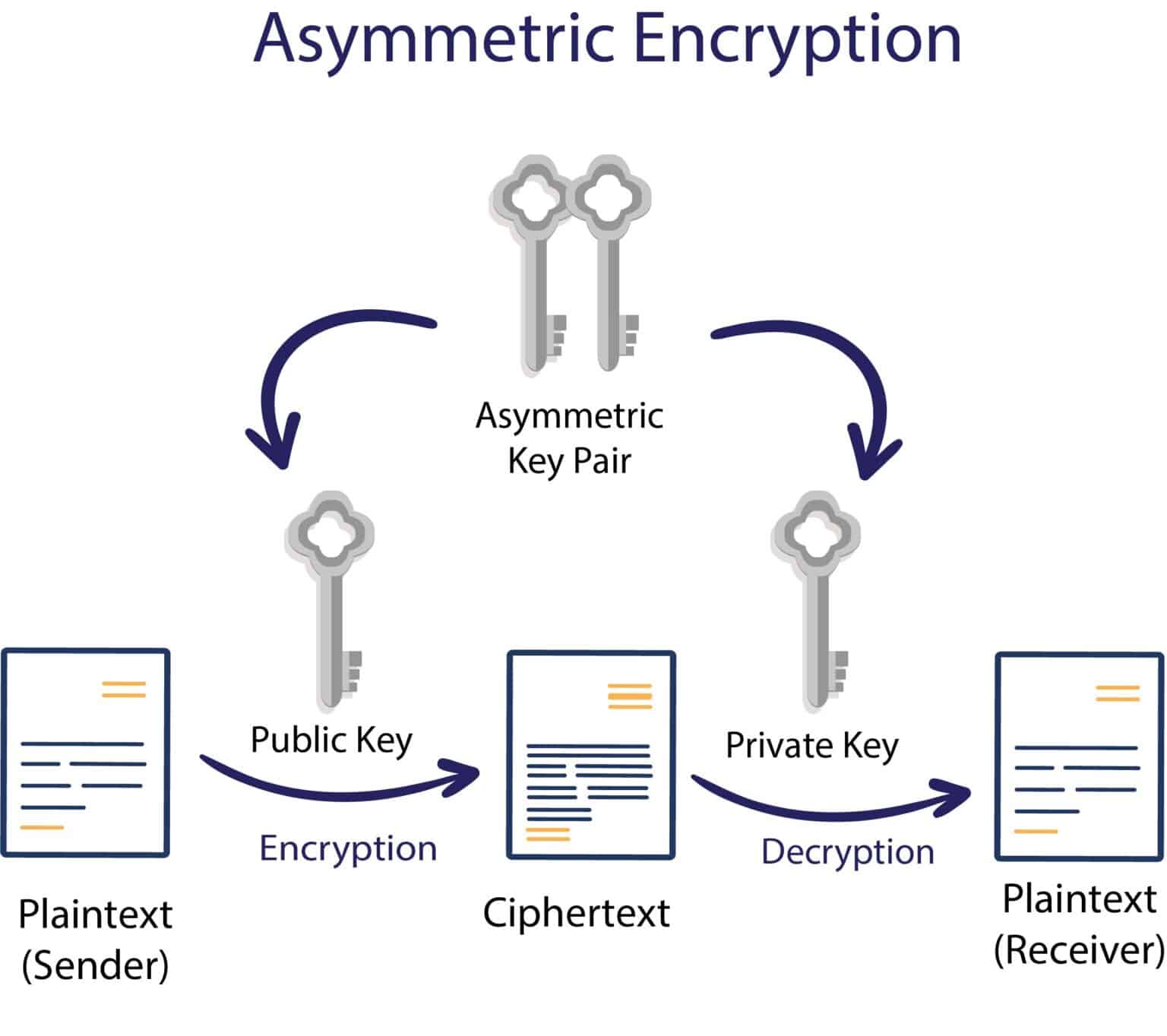
What Is The Difference Between Symmetric And Asymmetric Encryption

What Is The Difference Between Symmetric And Asymmetric Encryption

Importance Of Encryption Inspired Luv