In this age of technology, with screens dominating our lives and the appeal of physical printed materials isn't diminishing. If it's to aid in education and creative work, or simply adding a personal touch to your area, Public Key Encryption Algorithm List are now an essential source. This article will take a dive deeper into "Public Key Encryption Algorithm List," exploring the different types of printables, where to locate them, and how they can improve various aspects of your daily life.
Get Latest Public Key Encryption Algorithm List Below

Public Key Encryption Algorithm List
Public Key Encryption Algorithm List - Public Key Encryption Algorithm List, Public Key Cryptography Algorithms List, Public Key Encryption Example, Public Key Encryption Algorithms, Public Key Algorithm Example
Must bring your own device SIM cards can cost 5 or 10 through Public Mobile Overall read the pros and cons and decide if it s something which suits you In my opinion it s
Il semble que pour les abonn s de public mobile le forfait 19 est bonifi au niveau de l utilisation de donn es Pouvez vous me confirmer que les r compenses accumul sur mon
Public Key Encryption Algorithm List offer a wide assortment of printable, downloadable materials available online at no cost. These resources come in many types, like worksheets, coloring pages, templates and much more. The value of Public Key Encryption Algorithm List lies in their versatility and accessibility.
More of Public Key Encryption Algorithm List
Difference Between Symmetric Key Cryptography And Asymmetric Key

Difference Between Symmetric Key Cryptography And Asymmetric Key
Hey Community We are excited to announce that starting today we re introducing eSIM availability to both new and existing subscribers along with the rollout of multiple
Je ne suis pas capable de me connecter mon compte PublicMobile J ai essay mes 3 nom de boites courriel j ai aussi chang mon mot de passe et rien ne fonctionne Je
Public Key Encryption Algorithm List have risen to immense recognition for a variety of compelling motives:
-
Cost-Effective: They eliminate the necessity of purchasing physical copies or expensive software.
-
Personalization The Customization feature lets you tailor designs to suit your personal needs for invitations, whether that's creating them as well as organizing your calendar, or even decorating your house.
-
Educational Impact: The free educational worksheets are designed to appeal to students of all ages, making them an invaluable resource for educators and parents.
-
Simple: Quick access to a plethora of designs and templates will save you time and effort.
Where to Find more Public Key Encryption Algorithm List
Cryptography CyberSecurity Studio
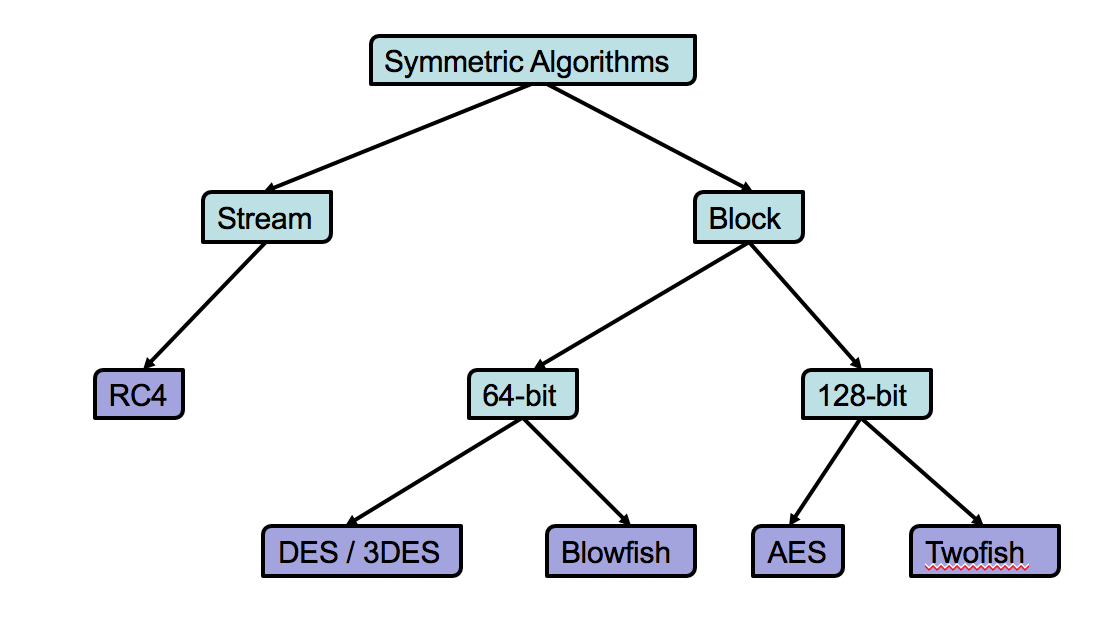
Cryptography CyberSecurity Studio
Hi all just wanted to clear up some confusion If you re already with Public Mobile and are looking to transfer your Public Mobile eSIM to a new device you ve purchased it will
You will be required to login to your Public Mobile Community Account to contact CS Agent Once you are finished making the ticket with CS Agent please ensure that you monitor for
After we've peaked your curiosity about Public Key Encryption Algorithm List Let's look into where you can find these elusive treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide an extensive selection of Public Key Encryption Algorithm List suitable for many objectives.
- Explore categories such as interior decor, education, organisation, as well as crafts.
2. Educational Platforms
- Educational websites and forums often offer free worksheets and worksheets for printing including flashcards, learning tools.
- This is a great resource for parents, teachers or students in search of additional sources.
3. Creative Blogs
- Many bloggers share their innovative designs or templates for download.
- The blogs covered cover a wide array of topics, ranging from DIY projects to planning a party.
Maximizing Public Key Encryption Algorithm List
Here are some inventive ways for you to get the best of printables that are free:
1. Home Decor
- Print and frame gorgeous artwork, quotes, or even seasonal decorations to decorate your living areas.
2. Education
- Use printable worksheets from the internet to enhance your learning at home also in the classes.
3. Event Planning
- Design invitations, banners as well as decorations for special occasions such as weddings, birthdays, and other special occasions.
4. Organization
- Be organized by using printable calendars along with lists of tasks, and meal planners.
Conclusion
Public Key Encryption Algorithm List are a treasure trove of fun and practical tools catering to different needs and hobbies. Their accessibility and flexibility make them an essential part of both professional and personal lives. Explore the vast collection of Public Key Encryption Algorithm List now and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables that are free truly are they free?
- Yes they are! You can print and download these materials for free.
-
Can I make use of free printables for commercial uses?
- It's based on the conditions of use. Be sure to read the rules of the creator before using their printables for commercial projects.
-
Are there any copyright violations with Public Key Encryption Algorithm List?
- Some printables may come with restrictions concerning their use. You should read the terms and regulations provided by the creator.
-
How do I print printables for free?
- Print them at home using the printer, or go to an area print shop for high-quality prints.
-
What program do I require to view printables that are free?
- The majority of printables are in the format PDF. This can be opened using free software such as Adobe Reader.
Cryptography CyberSecurity Studio
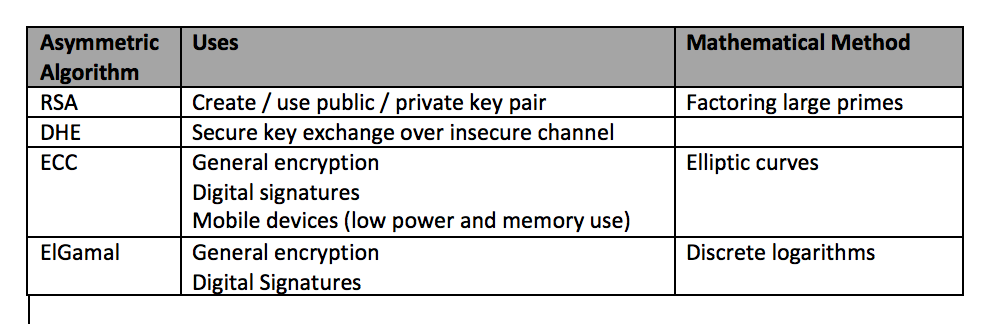
Cryptography CyberSecurity Studio
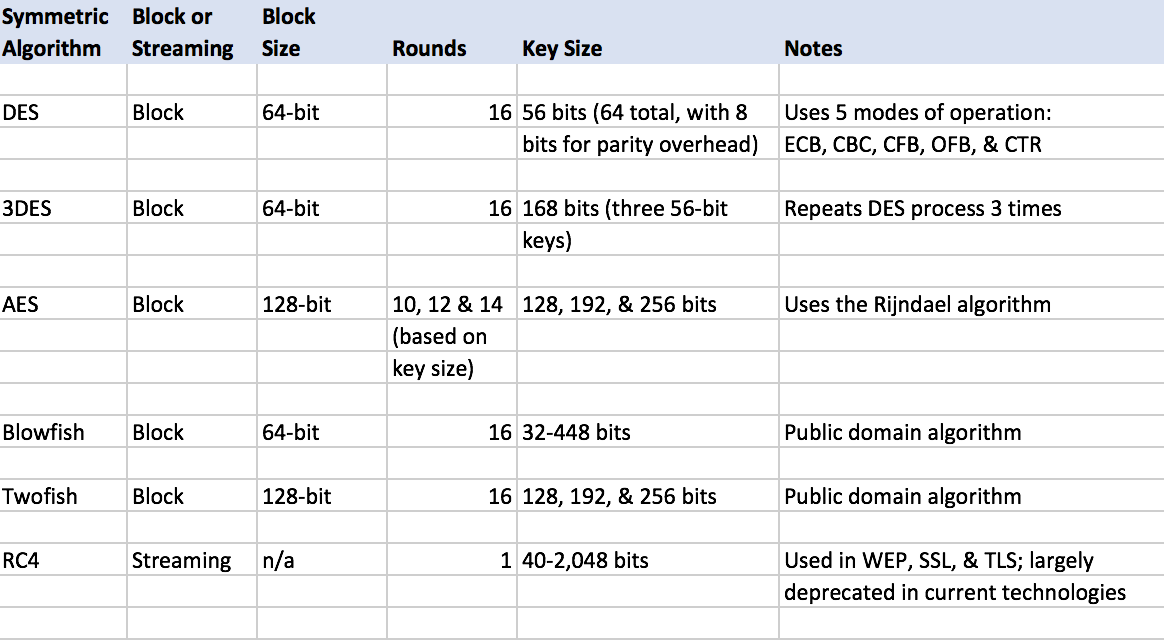
Check more sample of Public Key Encryption Algorithm List below
GitHub DarshAsawa Cryptography Implementing Various Cipher

Data Encryption Standard DES NETWORK ENCYCLOPEDIA
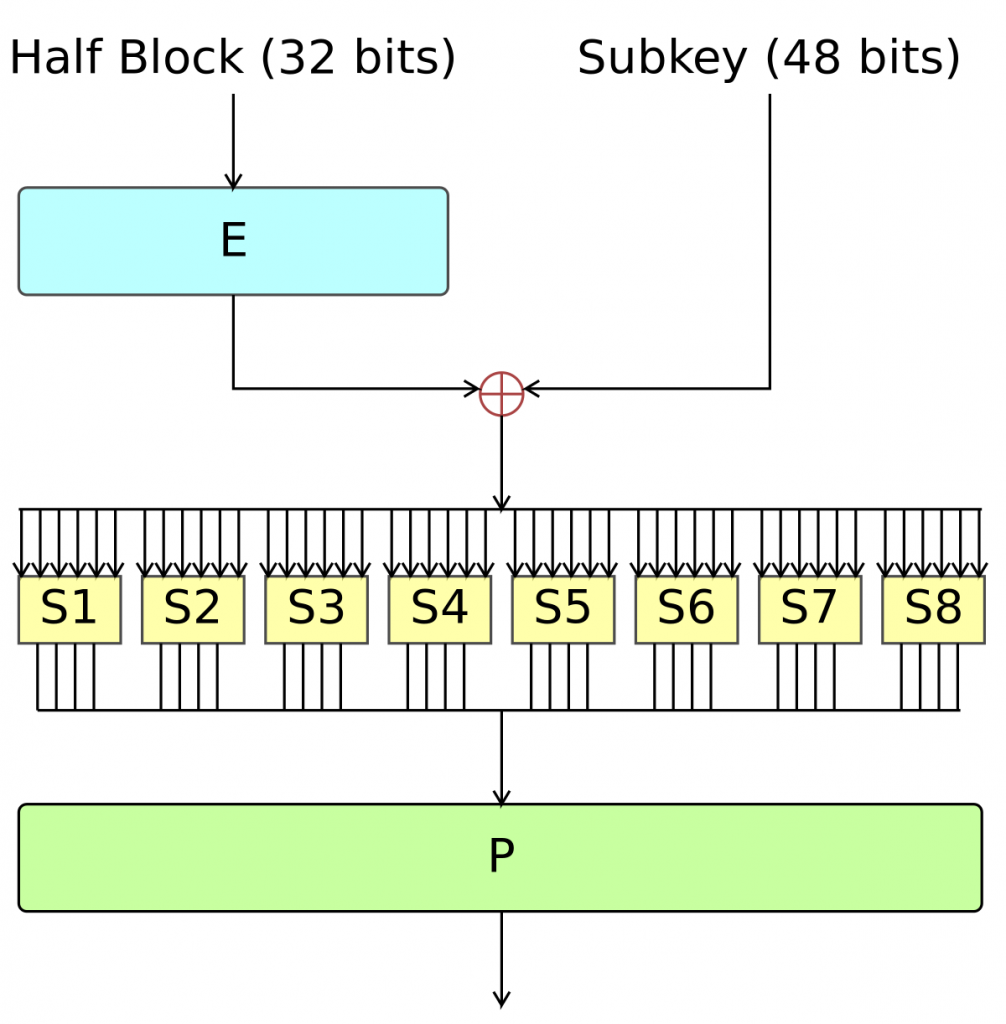
Encryption Internet Security
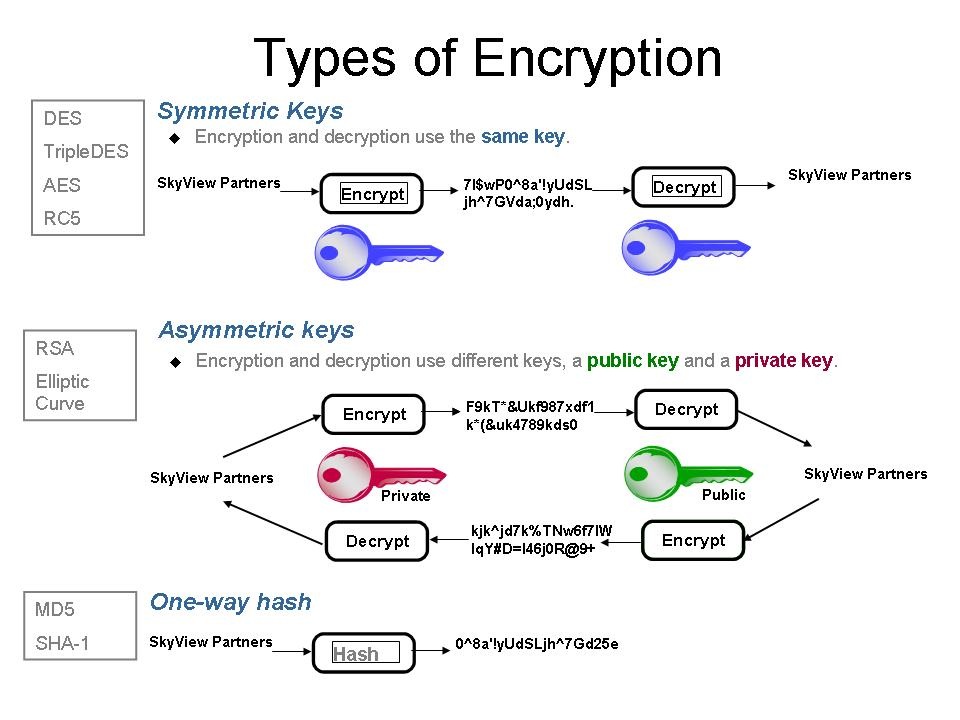
Beginners Guide To Cryptography Quick

Encryption And Decryption Jean s Blog

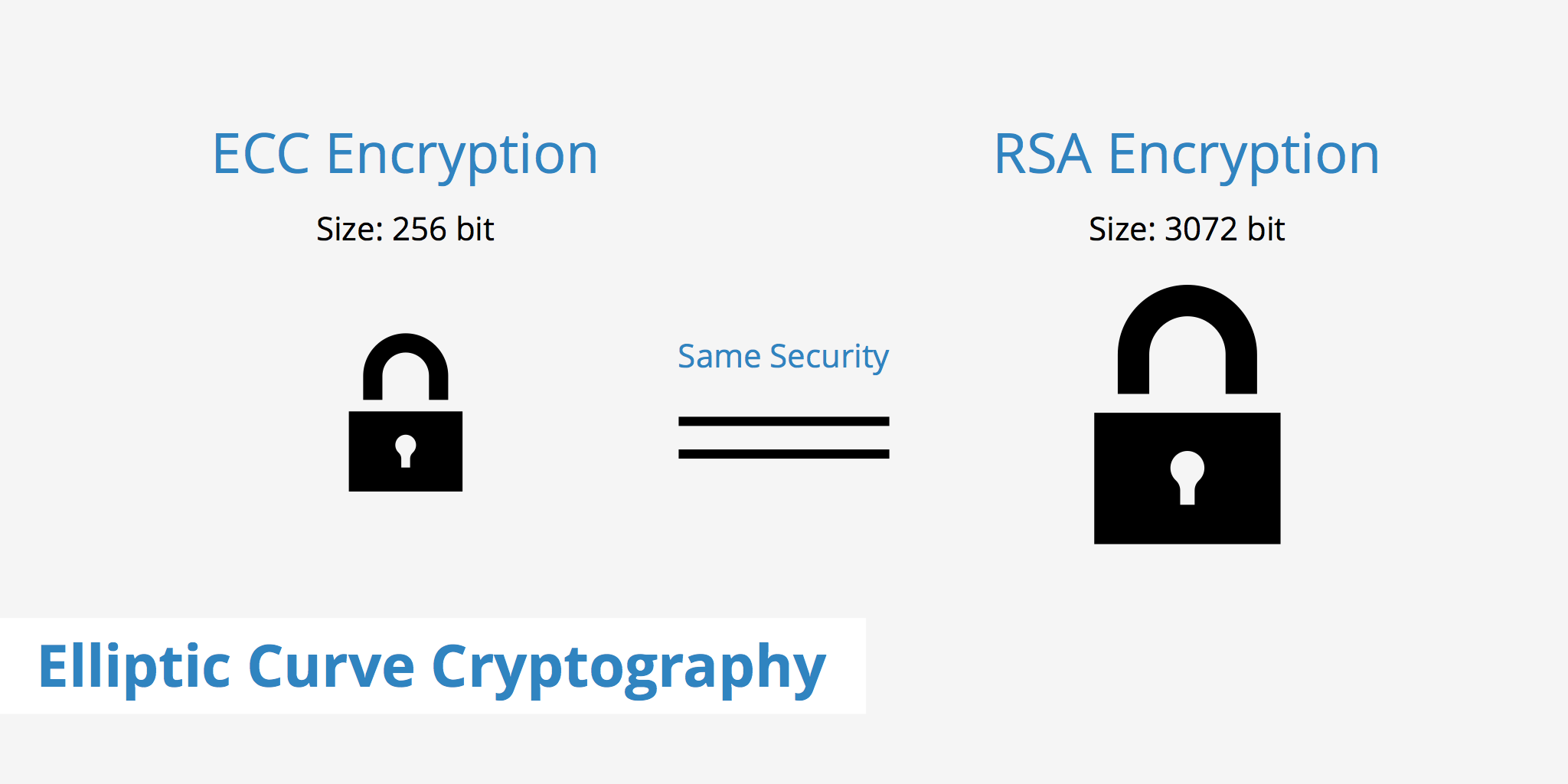
Elliptic Curve Cryptography KeyCDN Support

https://productioncommunity.publicmobile.ca › Communauté-Public-Mob…
Il semble que pour les abonn s de public mobile le forfait 19 est bonifi au niveau de l utilisation de donn es Pouvez vous me confirmer que les r compenses accumul sur mon

https://productioncommunity.publicmobile.ca › Get-Support › bd-p › get-…
Pack Your Bags Public Mobile s Trip to Mexico Contest is Here Hello Community We re thrilled to announce an exciting contest to celebrate our new CAN US MEX plans Get ready to spice
Il semble que pour les abonn s de public mobile le forfait 19 est bonifi au niveau de l utilisation de donn es Pouvez vous me confirmer que les r compenses accumul sur mon
Pack Your Bags Public Mobile s Trip to Mexico Contest is Here Hello Community We re thrilled to announce an exciting contest to celebrate our new CAN US MEX plans Get ready to spice

Beginners Guide To Cryptography Quick

Data Encryption Standard DES NETWORK ENCYCLOPEDIA

Encryption And Decryption Jean s Blog

Elliptic Curve Cryptography KeyCDN Support
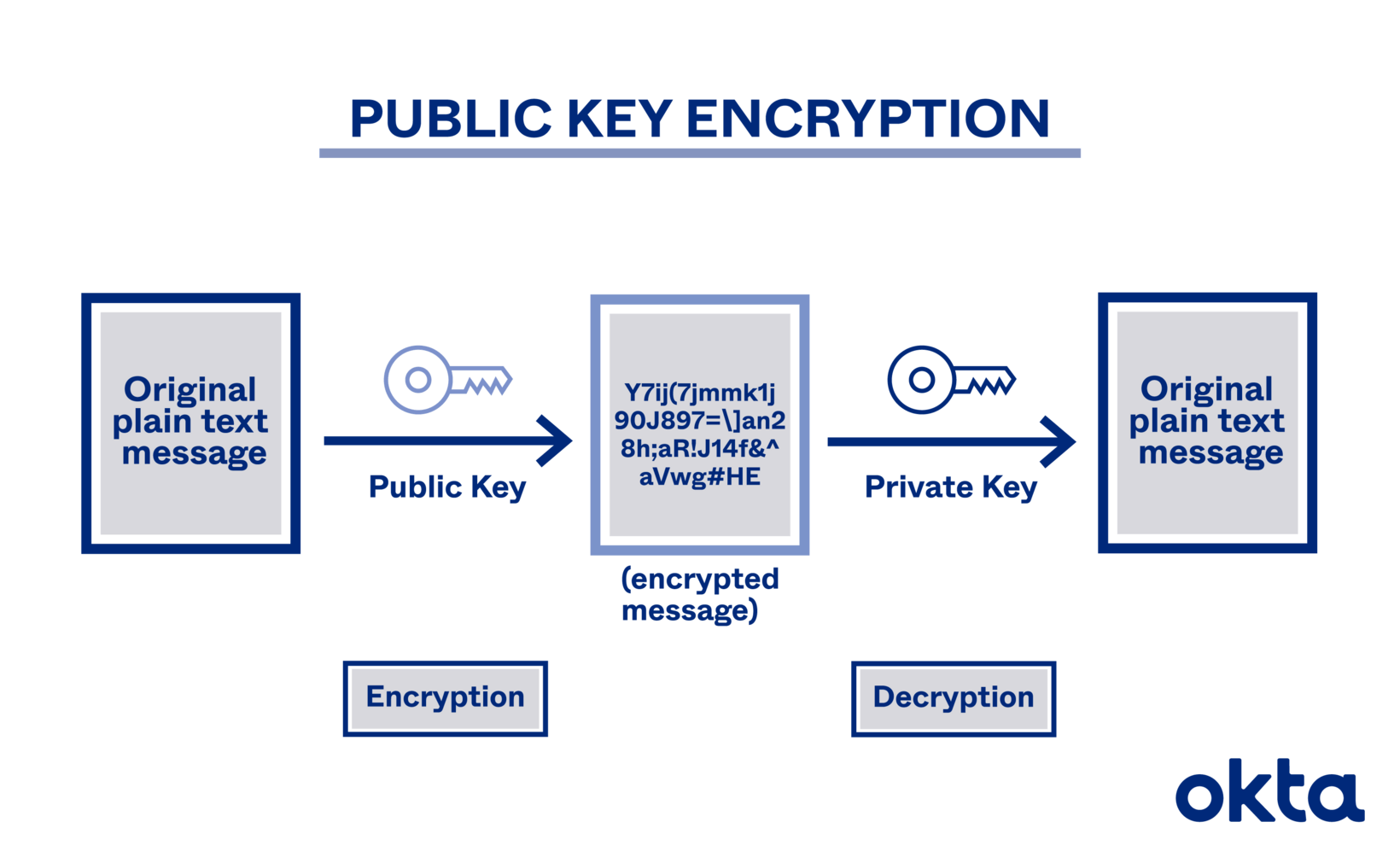
Public And Private Key Encryption System News Com

Public Key Cryptography Algorithms

Public Key Cryptography Algorithms

Encryption Algorithms Explained With Examples Vrogue co