In the digital age, where screens rule our lives but the value of tangible printed items hasn't gone away. Be it for educational use for creative projects, just adding a personal touch to your area, Public Key Cryptography Algorithms List have become a valuable resource. In this article, we'll take a dive into the world of "Public Key Cryptography Algorithms List," exploring the benefits of them, where to find them and how they can be used to enhance different aspects of your life.
What Are Public Key Cryptography Algorithms List?
Printables for free include a vast assortment of printable, downloadable material that is available online at no cost. These printables come in different forms, like worksheets templates, coloring pages and much more. The appeal of printables for free is their versatility and accessibility.
Public Key Cryptography Algorithms List

Public Key Cryptography Algorithms List
Public Key Cryptography Algorithms List -
[desc-5]
[desc-1]
What Is Symmetric Key Cryptography Encryption Security Wiki

What Is Symmetric Key Cryptography Encryption Security Wiki
[desc-4]
[desc-6]
What Is Symmetric Key Cryptography Elements Of Symmetric Key

What Is Symmetric Key Cryptography Elements Of Symmetric Key
[desc-9]
[desc-7]

How Public Key Encryption Ensures Data Integrity
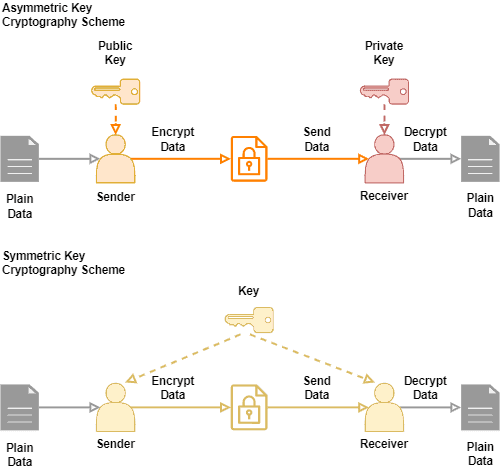
What Is Cryptography Cryptographic Algorithms Types Of
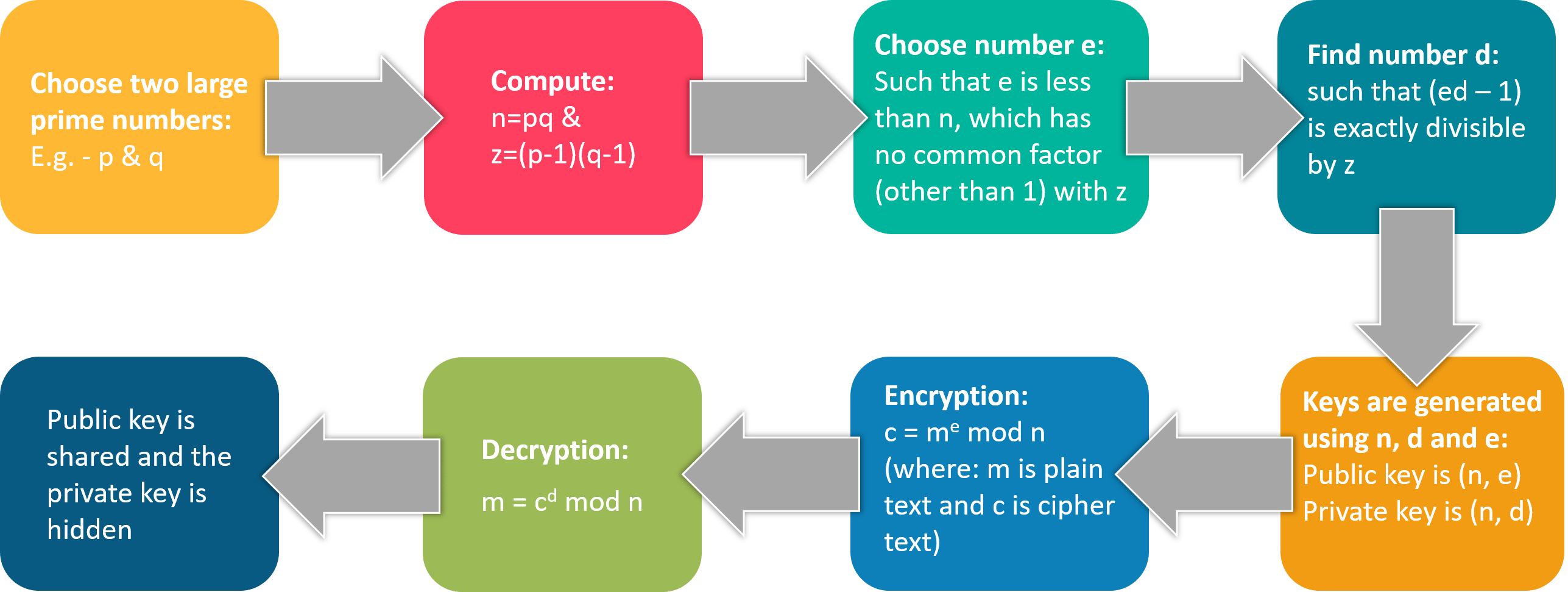
Public Key Cryptography Algorithms

RSA Algorithm In Cryptography Rivest Shamir Adleman Explained Splunk

Asymmetric Encryption How Asymmetric Encryption Works
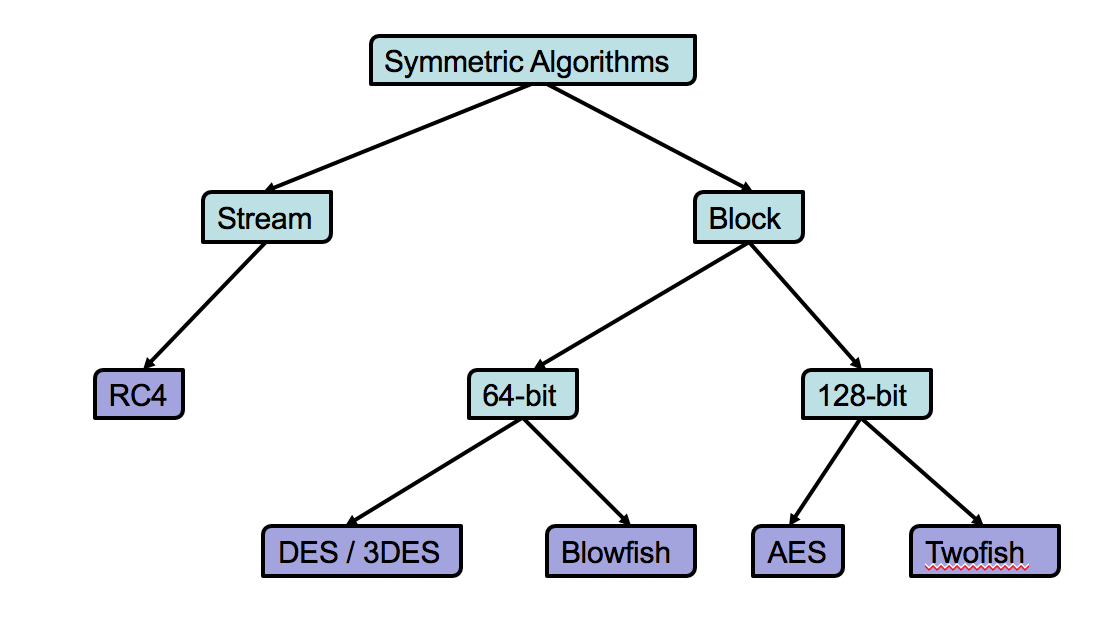
Cryptography CyberSecurity Studio

Cryptography CyberSecurity Studio

What Is Asymmetric Encryption