In this digital age, in which screens are the norm yet the appeal of tangible printed material hasn't diminished. In the case of educational materials as well as creative projects or simply adding an extra personal touch to your area, Bootstrapmade Vulnerabilities are a great resource. Through this post, we'll dive into the world "Bootstrapmade Vulnerabilities," exploring the benefits of them, where they are, and what they can do to improve different aspects of your life.
Get Latest Bootstrapmade Vulnerabilities Below

Bootstrapmade Vulnerabilities
Bootstrapmade Vulnerabilities - Bootstrapmade Vulnerabilities, Vulnerability Vs Malware, What Is Exploitable Vulnerability, What Is Vulnerabilities
Issue description After the execution of command npm install save bootstrap 4 1 1 I got the following error bootstrap 4 1 1 added 202 packages from 89 contributors removed 165 packages and
Bootstrap v3 1 11 and v3 3 7 contain a cross site scripting XSS vulnerability via the Title parameter in vendor views add product php The NVD provides CVSS scores CWE ID
Bootstrapmade Vulnerabilities include a broad variety of printable, downloadable resources available online for download at no cost. These resources come in many designs, including worksheets templates, coloring pages, and many more. The appeal of printables for free lies in their versatility as well as accessibility.
More of Bootstrapmade Vulnerabilities
Salesforce Is Investigating Impact Of Spring4Shell Vulnerabilities DYDC

Salesforce Is Investigating Impact Of Spring4Shell Vulnerabilities DYDC
Bootstrap versions prior to 3 4 1 and 4 3 1 are vulnerable to Cross Site Scripting XSS due to missing input sanitization The advisory provides details
Snyk scans for vulnerabilities in both your packages their dependencies and provides automated fixes for free Scan for indirect vulnerabilities Go back to all versions of this
Bootstrapmade Vulnerabilities have garnered immense recognition for a variety of compelling motives:
-
Cost-Effective: They eliminate the need to buy physical copies or costly software.
-
Flexible: We can customize the templates to meet your individual needs when it comes to designing invitations for your guests, organizing your schedule or even decorating your house.
-
Educational Worth: The free educational worksheets are designed to appeal to students of all ages, making the perfect tool for parents and educators.
-
Affordability: Fast access an array of designs and templates reduces time and effort.
Where to Find more Bootstrapmade Vulnerabilities
How To Use GitLab Security Features To Detect Log4j Vulnerabilities
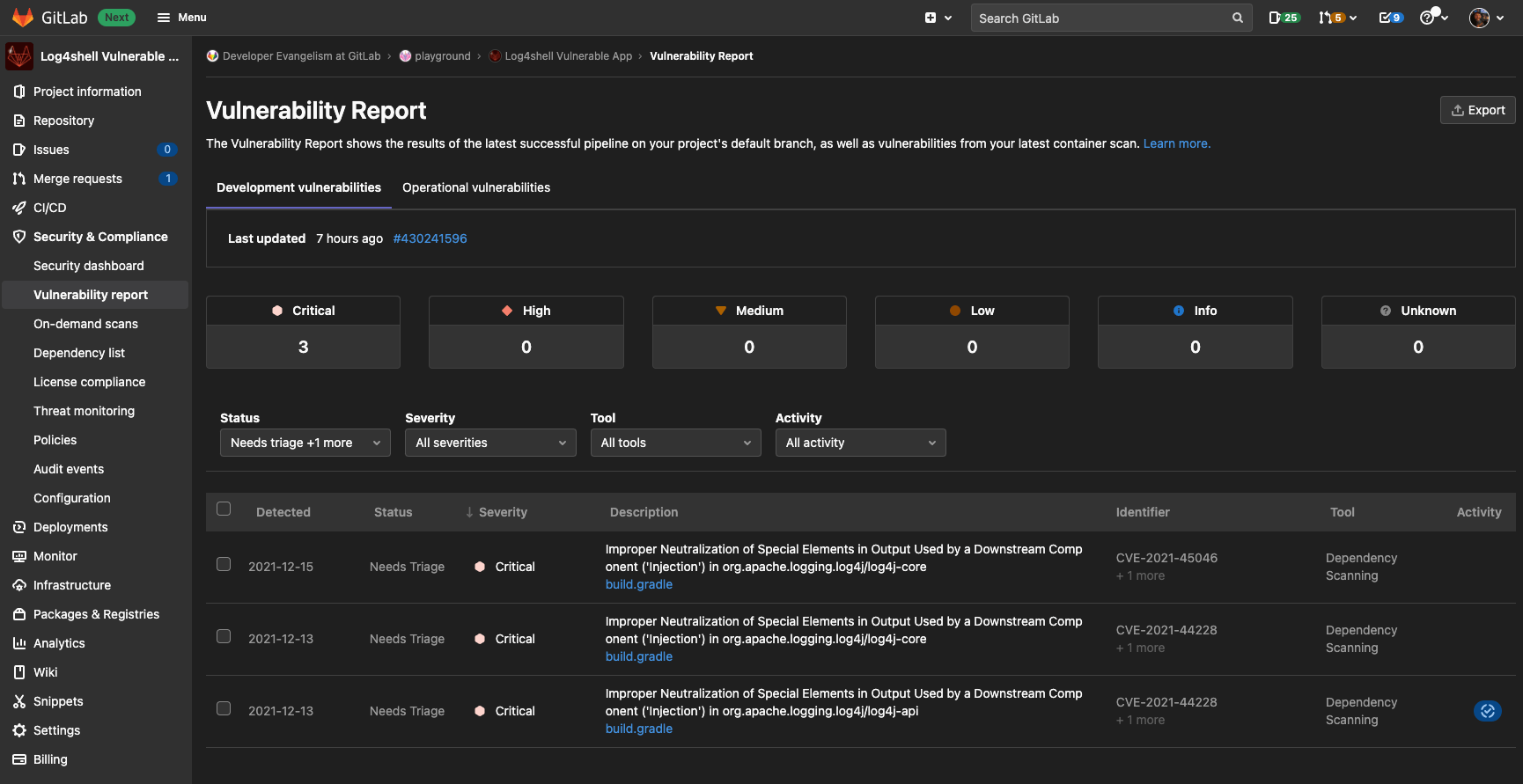
How To Use GitLab Security Features To Detect Log4j Vulnerabilities
Find public repositories that use bootstrapmade templates or frameworks for web development Browse code issues pull requests and stars for various projects
A cross site scripting XSS vulnerability in Bootstrap before 3 4 1 and 4 3 x before 4 3 1 allows an attacker to inject malicious code into the tooltip or popover data
We hope we've stimulated your interest in printables for free Let's take a look at where you can discover these hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide an extensive selection with Bootstrapmade Vulnerabilities for all objectives.
- Explore categories such as the home, decor, organisation, as well as crafts.
2. Educational Platforms
- Educational websites and forums frequently offer worksheets with printables that are free with flashcards and other teaching tools.
- Perfect for teachers, parents or students in search of additional sources.
3. Creative Blogs
- Many bloggers share their creative designs and templates free of charge.
- These blogs cover a broad selection of subjects, from DIY projects to party planning.
Maximizing Bootstrapmade Vulnerabilities
Here are some ways that you can make use use of printables for free:
1. Home Decor
- Print and frame beautiful art, quotes, or decorations for the holidays to beautify your living areas.
2. Education
- Use printable worksheets for free to reinforce learning at home, or even in the classroom.
3. Event Planning
- Create invitations, banners, and decorations for special occasions like weddings or birthdays.
4. Organization
- Stay organized with printable planners along with lists of tasks, and meal planners.
Conclusion
Bootstrapmade Vulnerabilities are a treasure trove of creative and practical resources designed to meet a range of needs and pursuits. Their accessibility and versatility make them an invaluable addition to the professional and personal lives of both. Explore the many options of Bootstrapmade Vulnerabilities right now and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free cost-free?
- Yes you can! You can print and download these files for free.
-
Can I use free printables for commercial purposes?
- It's based on specific rules of usage. Make sure you read the guidelines for the creator before using any printables on commercial projects.
-
Do you have any copyright issues with printables that are free?
- Some printables may contain restrictions regarding their use. Check the terms of service and conditions provided by the creator.
-
How do I print Bootstrapmade Vulnerabilities?
- Print them at home with either a printer or go to a print shop in your area for better quality prints.
-
What software do I need to open printables free of charge?
- Most printables come as PDF files, which can be opened using free programs like Adobe Reader.
GFI SOFTWARE 2021 WILL BE THE YEAR WITH THE MOST VULNERABILITIES
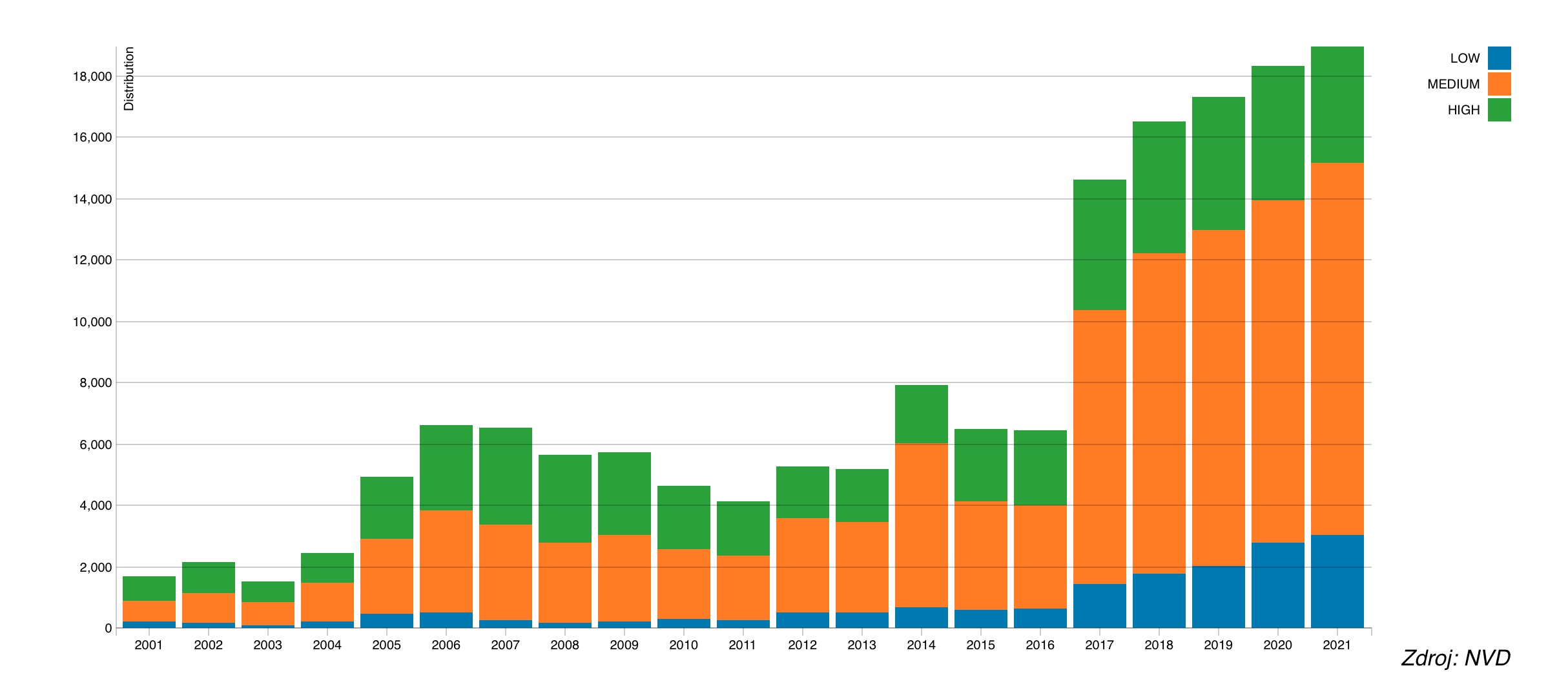
CISA s Known Exploited Vulnerabilities Catalog Expert Interview Series
Check more sample of Bootstrapmade Vulnerabilities below
GitHub Houssameehsain CutnFill DeepRL Positioning A Building Mass On
CISA Warns For Vulnerabilities In Industrial Control Systems ICS

Log4shell Full Picture All The Vulnerabilities Affecting Log4j

Understanding Wireless Vulnerabilities Jamming Attacks

GitHub Aminyazdanpanah Rush Hour Solver Rush Hour Solver In PHP
Influencers Vulnerabilities Found To Be A Double edged Sword Techno


https://nvd.nist.gov/vuln/detail/CVE-2022-26624
Bootstrap v3 1 11 and v3 3 7 contain a cross site scripting XSS vulnerability via the Title parameter in vendor views add product php The NVD provides CVSS scores CWE ID

https://medium.com/@haydengpt/addressing-new...
HeroDevs has just released patches for three medium risk vulnerabilities that were discovered in Bootstrap 3 and 4 in July 2024 These issues identified as CVE
Bootstrap v3 1 11 and v3 3 7 contain a cross site scripting XSS vulnerability via the Title parameter in vendor views add product php The NVD provides CVSS scores CWE ID
HeroDevs has just released patches for three medium risk vulnerabilities that were discovered in Bootstrap 3 and 4 in July 2024 These issues identified as CVE

Understanding Wireless Vulnerabilities Jamming Attacks

CISA Warns For Vulnerabilities In Industrial Control Systems ICS
GitHub Aminyazdanpanah Rush Hour Solver Rush Hour Solver In PHP

Influencers Vulnerabilities Found To Be A Double edged Sword Techno

Hidden Vulnerabilities In Clinical Workflow Put PHI At Risk

Web3 Industry Faces 1 7 Billion In Losses Salus Reveals Trends And

Web3 Industry Faces 1 7 Billion In Losses Salus Reveals Trends And

How To Find And Fix API Vulnerabilities Noname Security