In this age of electronic devices, with screens dominating our lives however, the attraction of tangible printed products hasn't decreased. No matter whether it's for educational uses such as creative projects or just adding an element of personalization to your home, printables for free are a great source. We'll take a dive through the vast world of "What Is Vulnerabilities," exploring the benefits of them, where to find them, and the ways that they can benefit different aspects of your daily life.
Get Latest What Is Vulnerabilities Below

What Is Vulnerabilities
What Is Vulnerabilities -
A security vulnerability is a software code flaw or a system misconfiguration such as Log4Shell through which attackers can directly gain unauthorized access to a system or network Once inside the attacker can leverage authorizations and privileges to compromise systems and assets
A security vulnerability is defined as an unintended characteristic of a computing component or system configuration that multiplies the risk of an adverse event or a loss occurring either due to accidental exposure deliberate attack or conflict with new system components
What Is Vulnerabilities include a broad array of printable content that can be downloaded from the internet at no cost. These materials come in a variety of types, such as worksheets coloring pages, templates and more. The beauty of What Is Vulnerabilities is their flexibility and accessibility.
More of What Is Vulnerabilities
What Is The Importance Of Vulnerability Assessment

What Is The Importance Of Vulnerability Assessment
Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data Our guide explores the different types of vulnerabilities their potential impact on organizations and the importance of
A vulnerability is a hole or a weakness in the application which can be a design flaw or an implementation bug that allows an attacker to cause harm to the stakeholders of an application Stakeholders include the application owner application users and other entities that rely on the application
What Is Vulnerabilities have gained a lot of popularity due to several compelling reasons:
-
Cost-Efficiency: They eliminate the need to buy physical copies or costly software.
-
The ability to customize: They can make printed materials to meet your requirements such as designing invitations making your schedule, or even decorating your house.
-
Educational Impact: Downloads of educational content for free can be used by students from all ages, making them a vital resource for educators and parents.
-
Affordability: Quick access to a variety of designs and templates will save you time and effort.
Where to Find more What Is Vulnerabilities
Components Of Vulnerability U S Climate Resilience Toolkit
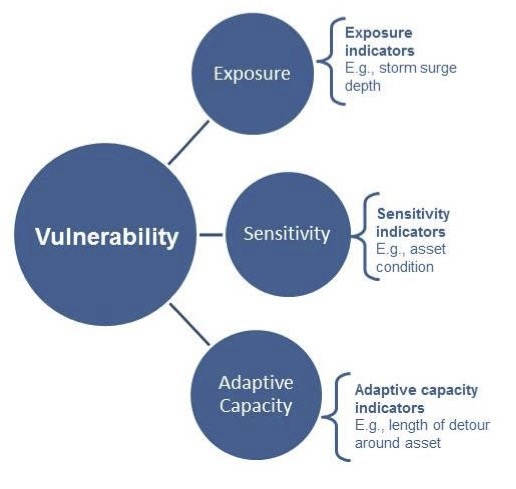
Components Of Vulnerability U S Climate Resilience Toolkit
What is a Vulnerability Mistakes happen even in the process of building and coding technology What s left behind from these mistakes is commonly referred to as a bug While bugs aren t inherently harmful except to the potential performance of the technology many can be taken advantage of by nefarious actors these are known as vulnerabilities
What is a vulnerability in cybersecurity A vulnerability in cybersecurity is a weakness in a host or system such as a missed software update or system misconfiguration that can be exploited by cybercriminals to compromise an IT resource and advance the attack path
Now that we've ignited your curiosity about What Is Vulnerabilities Let's look into where they are hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy have a large selection of What Is Vulnerabilities suitable for many motives.
- Explore categories like the home, decor, organizational, and arts and crafts.
2. Educational Platforms
- Educational websites and forums often provide worksheets that can be printed for free Flashcards, worksheets, and other educational materials.
- Great for parents, teachers, and students seeking supplemental sources.
3. Creative Blogs
- Many bloggers offer their unique designs and templates for free.
- These blogs cover a broad spectrum of interests, all the way from DIY projects to planning a party.
Maximizing What Is Vulnerabilities
Here are some ways for you to get the best of printables that are free:
1. Home Decor
- Print and frame beautiful artwork, quotes, or even seasonal decorations to decorate your living areas.
2. Education
- Use these printable worksheets free of charge to enhance learning at home as well as in the class.
3. Event Planning
- Designs invitations, banners and decorations for special events like weddings and birthdays.
4. Organization
- Keep track of your schedule with printable calendars with to-do lists, planners, and meal planners.
Conclusion
What Is Vulnerabilities are an abundance of fun and practical tools catering to different needs and passions. Their accessibility and flexibility make them a valuable addition to both professional and personal life. Explore the wide world of What Is Vulnerabilities now and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are What Is Vulnerabilities really gratis?
- Yes, they are! You can print and download these materials for free.
-
Can I download free printouts for commercial usage?
- It's based on the terms of use. Always verify the guidelines of the creator prior to printing printables for commercial projects.
-
Do you have any copyright issues with What Is Vulnerabilities?
- Some printables could have limitations in their usage. Be sure to review the terms and conditions set forth by the designer.
-
How do I print What Is Vulnerabilities?
- Print them at home using an printer, or go to any local print store for top quality prints.
-
What software do I need to open printables for free?
- A majority of printed materials are in PDF format. These is open with no cost software, such as Adobe Reader.
Vulnerability Lanworks

What Are The 4 Main Types Of Vulnerability Cloudshareinfo

Check more sample of What Is Vulnerabilities below
Spotting Vulnerabilities Is Vulnerability Scanning Antiquated

Understanding The Common Vulnerability Scoring System

Fakecineaste Cyber Security

WHAT ARE THE 4 MAIN TYPES OF VULNERABILITY

How To Find And Fix Security Vulnerabilities Using Snyk

TOP 9 Most Common Security Vulnerabilities In Websites TechinPost


https://www.spiceworks.com/it-security/...
A security vulnerability is defined as an unintended characteristic of a computing component or system configuration that multiplies the risk of an adverse event or a loss occurring either due to accidental exposure deliberate attack or conflict with new system components

https://www.balbix.com/insights/what-is-a-vulnerability
A vulnerability in cybersecurity is a flaw or weakness in a system that cybercriminals exploit to gain unauthorized access or cause harm These vulnerabilities often stem from coding errors or misconfigurations and can be leveraged to disrupt operations steal data or compromise security
A security vulnerability is defined as an unintended characteristic of a computing component or system configuration that multiplies the risk of an adverse event or a loss occurring either due to accidental exposure deliberate attack or conflict with new system components
A vulnerability in cybersecurity is a flaw or weakness in a system that cybercriminals exploit to gain unauthorized access or cause harm These vulnerabilities often stem from coding errors or misconfigurations and can be leveraged to disrupt operations steal data or compromise security

WHAT ARE THE 4 MAIN TYPES OF VULNERABILITY

Understanding The Common Vulnerability Scoring System

How To Find And Fix Security Vulnerabilities Using Snyk

TOP 9 Most Common Security Vulnerabilities In Websites TechinPost
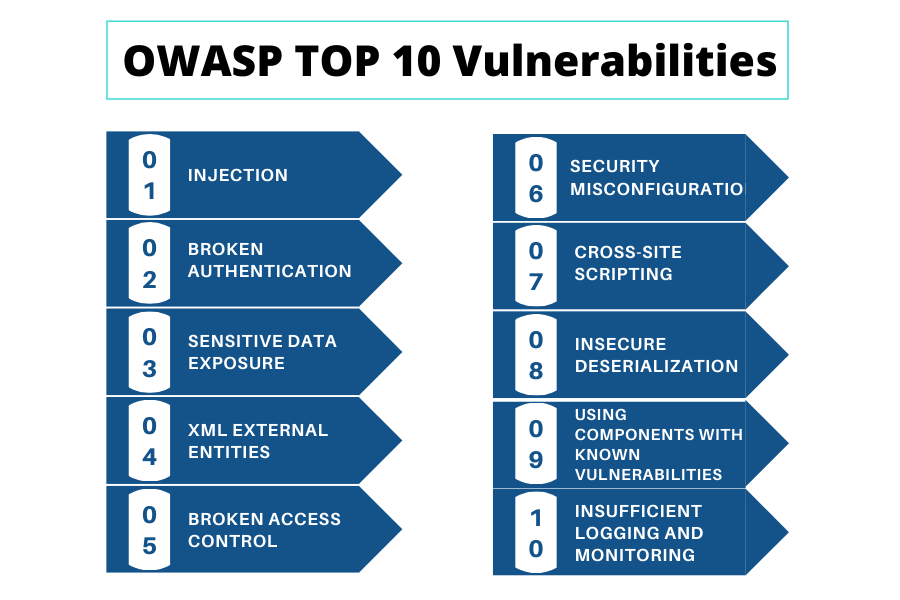
What Is OWASP Latest Top 10 OWASP Vulnerabilities
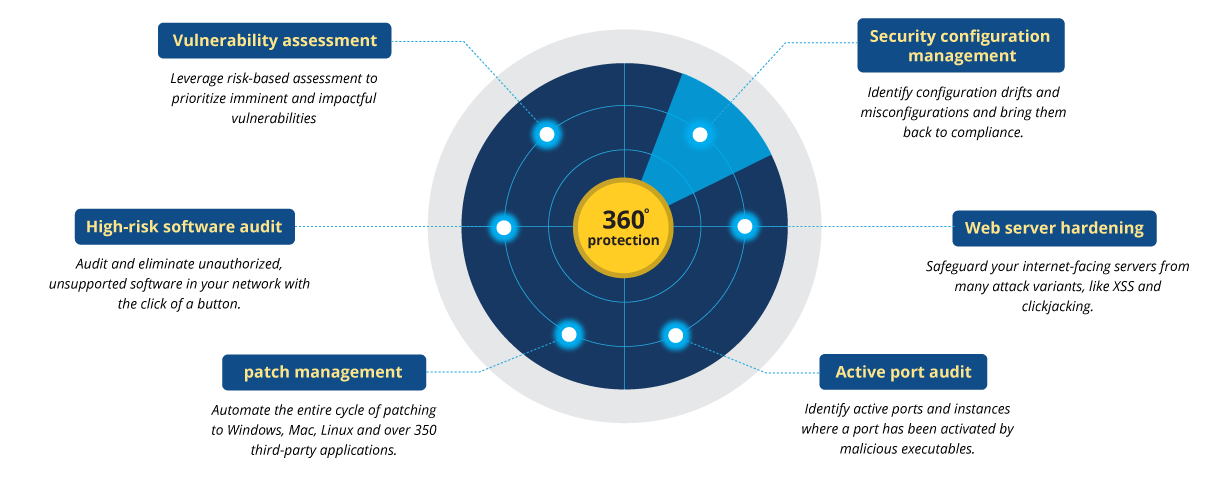
What Is Vulnerability Management Vulnerability Management Process

What Is Vulnerability Management Vulnerability Management Process

What Are The Types Of Cyber Security Vulnerabilities Global Tech Council