In this age of technology, when screens dominate our lives however, the attraction of tangible printed objects hasn't waned. No matter whether it's for educational uses for creative projects, simply adding the personal touch to your area, Symmetric Key Distribution In Cryptography And Network Security have proven to be a valuable resource. We'll dive deeper into "Symmetric Key Distribution In Cryptography And Network Security," exploring the different types of printables, where to find them, and how they can enhance various aspects of your life.
Get Latest Symmetric Key Distribution In Cryptography And Network Security Below
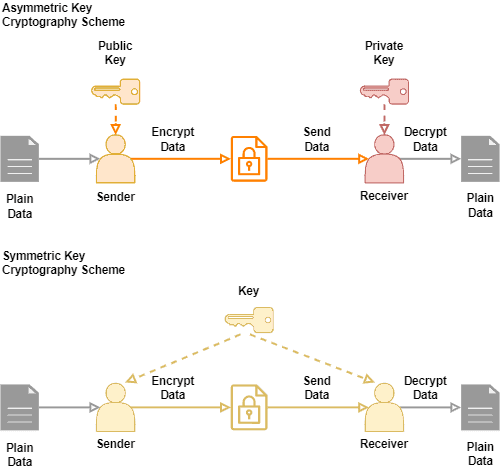
Symmetric Key Distribution In Cryptography And Network Security
Symmetric Key Distribution In Cryptography And Network Security - Symmetric Key Distribution In Cryptography And Network Security
Chat GPT un chatbot AI sviluppato da OpenAI per dialogare in italiano Utilizza un modello di intelligenza artificiale generativa e apprendimento automatico In questa guida scopriremo
Utilizza la rete neurale OpenAI gratuitamente e senza registrazione ChatGPT un chatbot con intelligenza artificiale Pu generare testi di qualsiasi complessit e argomento comporre
Symmetric Key Distribution In Cryptography And Network Security include a broad assortment of printable resources available online for download at no cost. The resources are offered in a variety forms, including worksheets, coloring pages, templates and more. One of the advantages of Symmetric Key Distribution In Cryptography And Network Security lies in their versatility as well as accessibility.
More of Symmetric Key Distribution In Cryptography And Network Security
What Is Symmetric Key Cryptography Encryption Security Wiki

What Is Symmetric Key Cryptography Encryption Security Wiki
Come alternativa c l app Microsoft Copilot che propone un assistente di chat alimentato dai pi recenti modelli OpenAI GPT 4 e DALL E 3 con risultati davvero interessanti disponibile per
ChatGPT un intelligenza artificiale sviluppata da OpenAI che sa fare un sacco di cose interessanti Immaginala come un assistente virtuale super intelligente che pu rispondere alle
Print-friendly freebies have gained tremendous popularity due to several compelling reasons:
-
Cost-Efficiency: They eliminate the requirement to purchase physical copies or costly software.
-
Modifications: This allows you to modify printed materials to meet your requirements such as designing invitations making your schedule, or even decorating your home.
-
Educational Benefits: The free educational worksheets can be used by students of all ages, making them a useful tool for teachers and parents.
-
Accessibility: immediate access the vast array of design and templates helps save time and effort.
Where to Find more Symmetric Key Distribution In Cryptography And Network Security
HTTPs
HTTPs
In questo articolo esplorerai come funziona ChatGPT un modello di linguaggio avanzato sviluppato da OpenAI Scoprirai come utilizzarlo in italiano beneficiando delle sue
Chat GPT Plus una versione premium del chatbot Chat GPT progettato per fornire risposte pi precise e contestualizzate Utilizza un modello di linguaggio avanzato sviluppato da OpenAI
If we've already piqued your curiosity about Symmetric Key Distribution In Cryptography And Network Security, let's explore where you can find these hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a variety of Symmetric Key Distribution In Cryptography And Network Security suitable for many uses.
- Explore categories such as design, home decor, craft, and organization.
2. Educational Platforms
- Forums and educational websites often offer worksheets with printables that are free Flashcards, worksheets, and other educational tools.
- Great for parents, teachers or students in search of additional resources.
3. Creative Blogs
- Many bloggers share their imaginative designs and templates, which are free.
- These blogs cover a broad array of topics, ranging starting from DIY projects to party planning.
Maximizing Symmetric Key Distribution In Cryptography And Network Security
Here are some innovative ways for you to get the best use of printables that are free:
1. Home Decor
- Print and frame beautiful images, quotes, or other seasonal decorations to fill your living spaces.
2. Education
- Use printable worksheets for free to aid in learning at your home also in the classes.
3. Event Planning
- Create invitations, banners, and decorations for special events such as weddings or birthdays.
4. Organization
- Stay organized with printable calendars or to-do lists. meal planners.
Conclusion
Symmetric Key Distribution In Cryptography And Network Security are an abundance of practical and innovative resources for a variety of needs and preferences. Their availability and versatility make them a great addition to both professional and personal lives. Explore the vast collection of Symmetric Key Distribution In Cryptography And Network Security to open up new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables available for download really are they free?
- Yes, they are! You can print and download these files for free.
-
Can I make use of free printables for commercial use?
- It's based on specific conditions of use. Always verify the guidelines provided by the creator before using any printables on commercial projects.
-
Do you have any copyright concerns with Symmetric Key Distribution In Cryptography And Network Security?
- Some printables could have limitations on use. Check the terms and conditions set forth by the designer.
-
How do I print Symmetric Key Distribution In Cryptography And Network Security?
- You can print them at home with a printer or visit a local print shop for high-quality prints.
-
What software do I need to run printables that are free?
- The majority of printed documents are in PDF format, which can be opened using free programs like Adobe Reader.
Cryptography 101 Sandfield
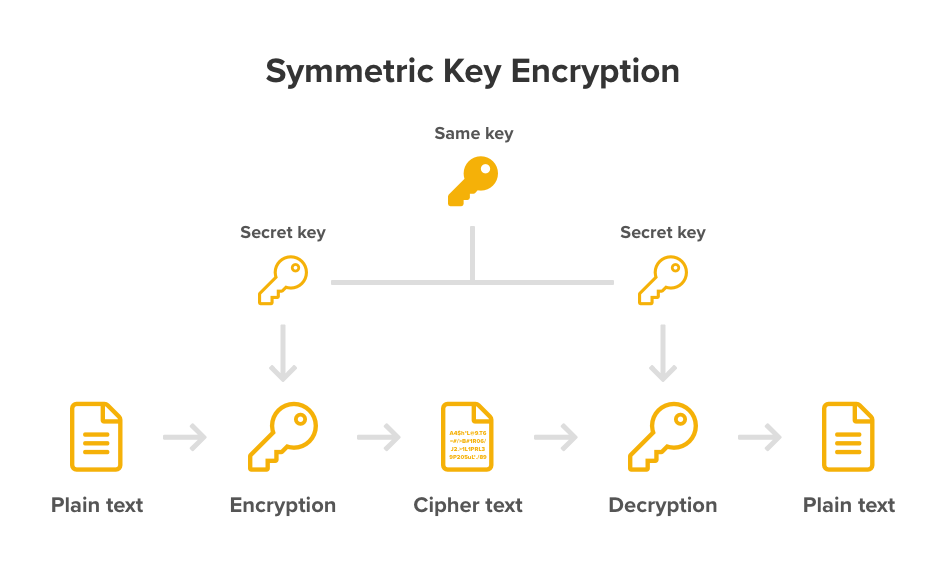
HTTPS HTTP Secure
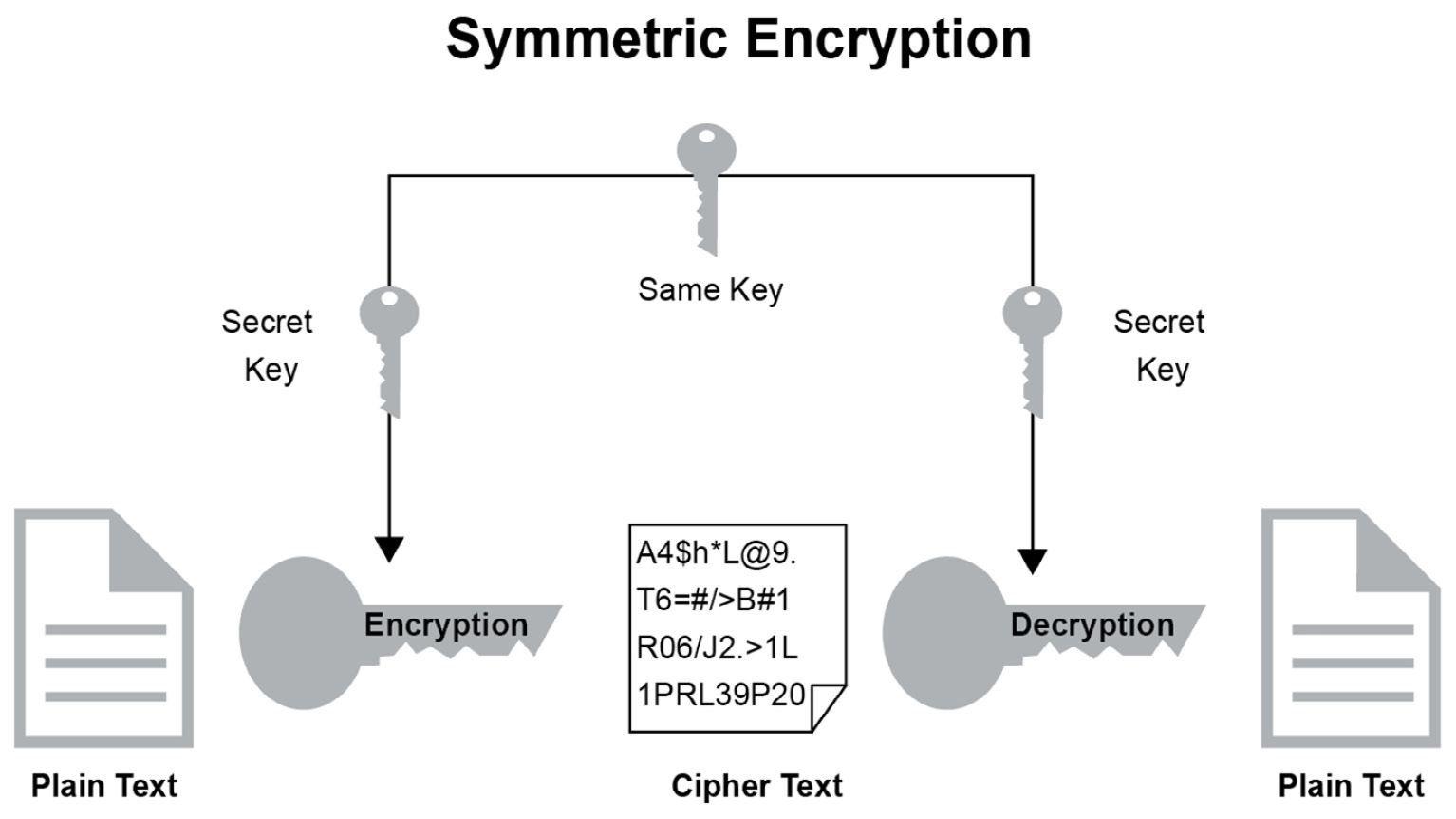
Check more sample of Symmetric Key Distribution In Cryptography And Network Security below
Unlocking Blockchain s Fort Knox The Power Of Cryptography For

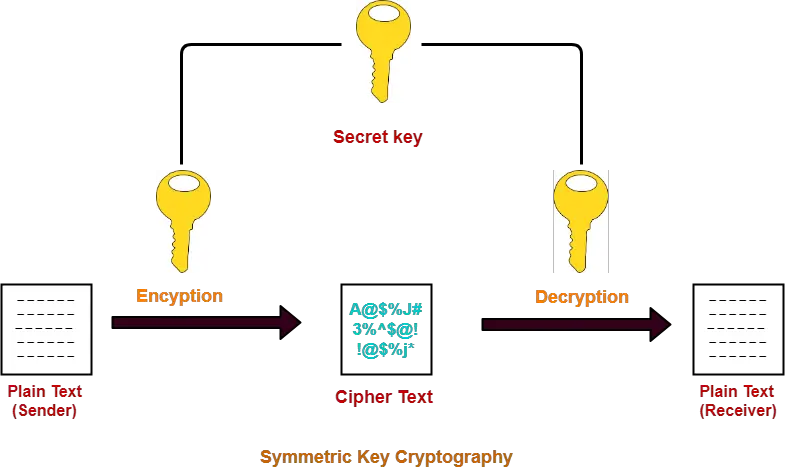
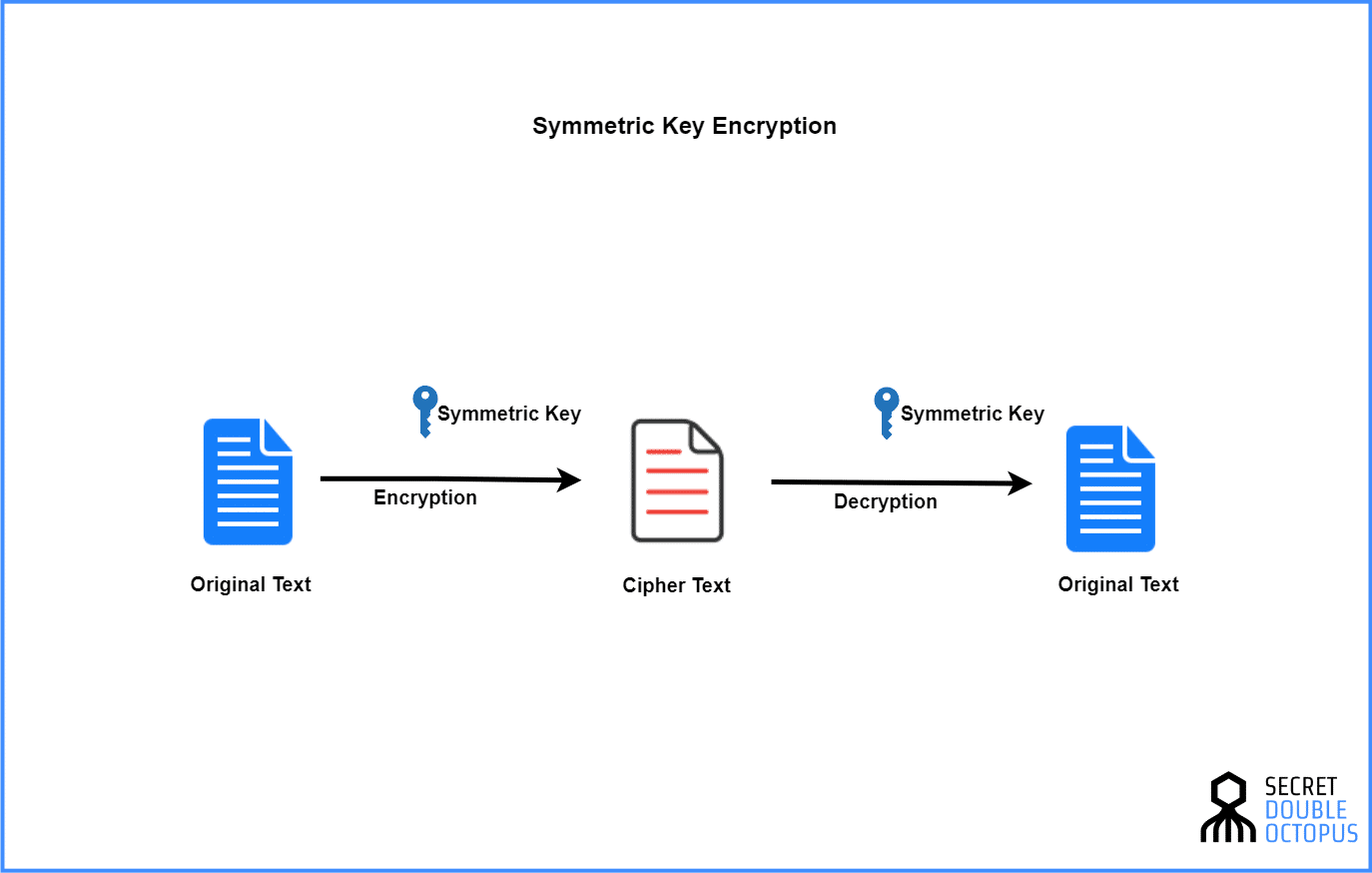
Symmetric Key Encryption Complete Guide To Symmetric Key Encryption

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Asymmetric Encryption How Asymmetric Encryption Works

Cryptography Introduction 5OBIT
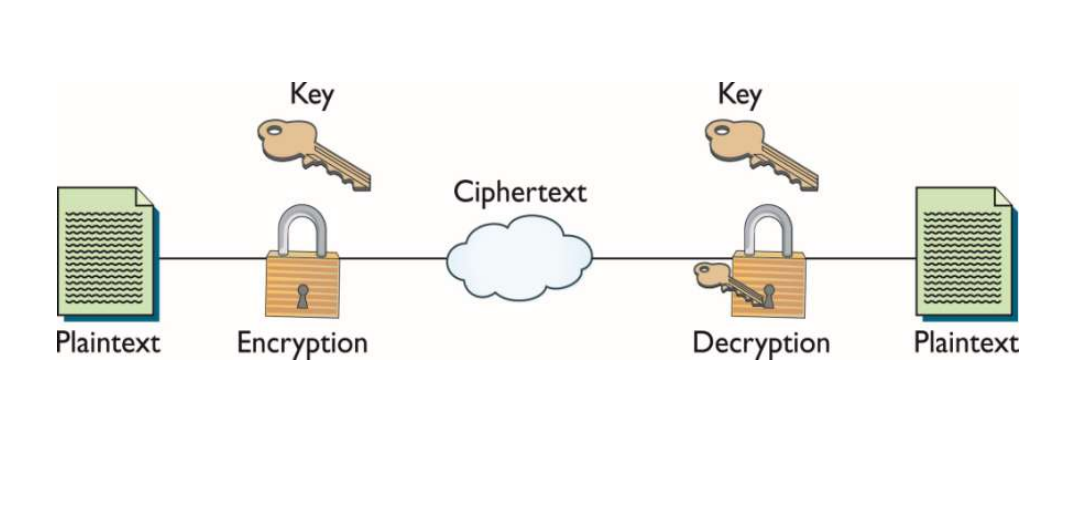
Symmetric Key Cryptography Cryptography Techniques Gate Vidyalay

https://talkai.info › it
Utilizza la rete neurale OpenAI gratuitamente e senza registrazione ChatGPT un chatbot con intelligenza artificiale Pu generare testi di qualsiasi complessit e argomento comporre
https://chat-gpt.org › it › chat
Usa ChatGPT online e senza registrazione Basta fornire al chatbot AI qualsiasi richiesta di testo e ottenere una risposta dettagliata da ChatGPT
Utilizza la rete neurale OpenAI gratuitamente e senza registrazione ChatGPT un chatbot con intelligenza artificiale Pu generare testi di qualsiasi complessit e argomento comporre
Usa ChatGPT online e senza registrazione Basta fornire al chatbot AI qualsiasi richiesta di testo e ottenere una risposta dettagliata da ChatGPT

Asymmetric Encryption How Asymmetric Encryption Works

Symmetric Key Encryption Complete Guide To Symmetric Key Encryption

Cryptography Introduction 5OBIT

Symmetric Key Cryptography Cryptography Techniques Gate Vidyalay

How Does Blockchain Use Public Key Cryptography
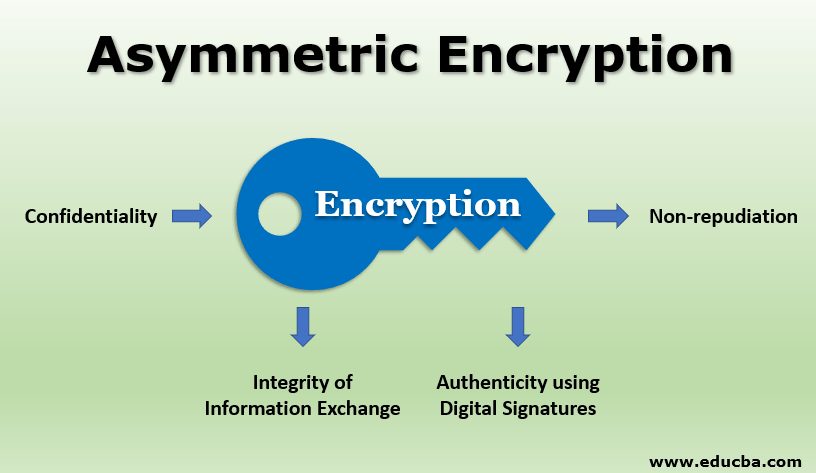
Asymmetric Encryption Explained Strong Password Generator

Asymmetric Encryption Explained Strong Password Generator

RSA Algorithm In Cryptography Rivest Shamir Adleman Explained Splunk