In the digital age, with screens dominating our lives but the value of tangible printed objects isn't diminished. It doesn't matter if it's for educational reasons or creative projects, or just adding a personal touch to your area, Symmetric Key Cryptography Example are a great source. We'll dive deep into the realm of "Symmetric Key Cryptography Example," exploring what they are, how they are available, and what they can do to improve different aspects of your life.
Get Latest Symmetric Key Cryptography Example Below

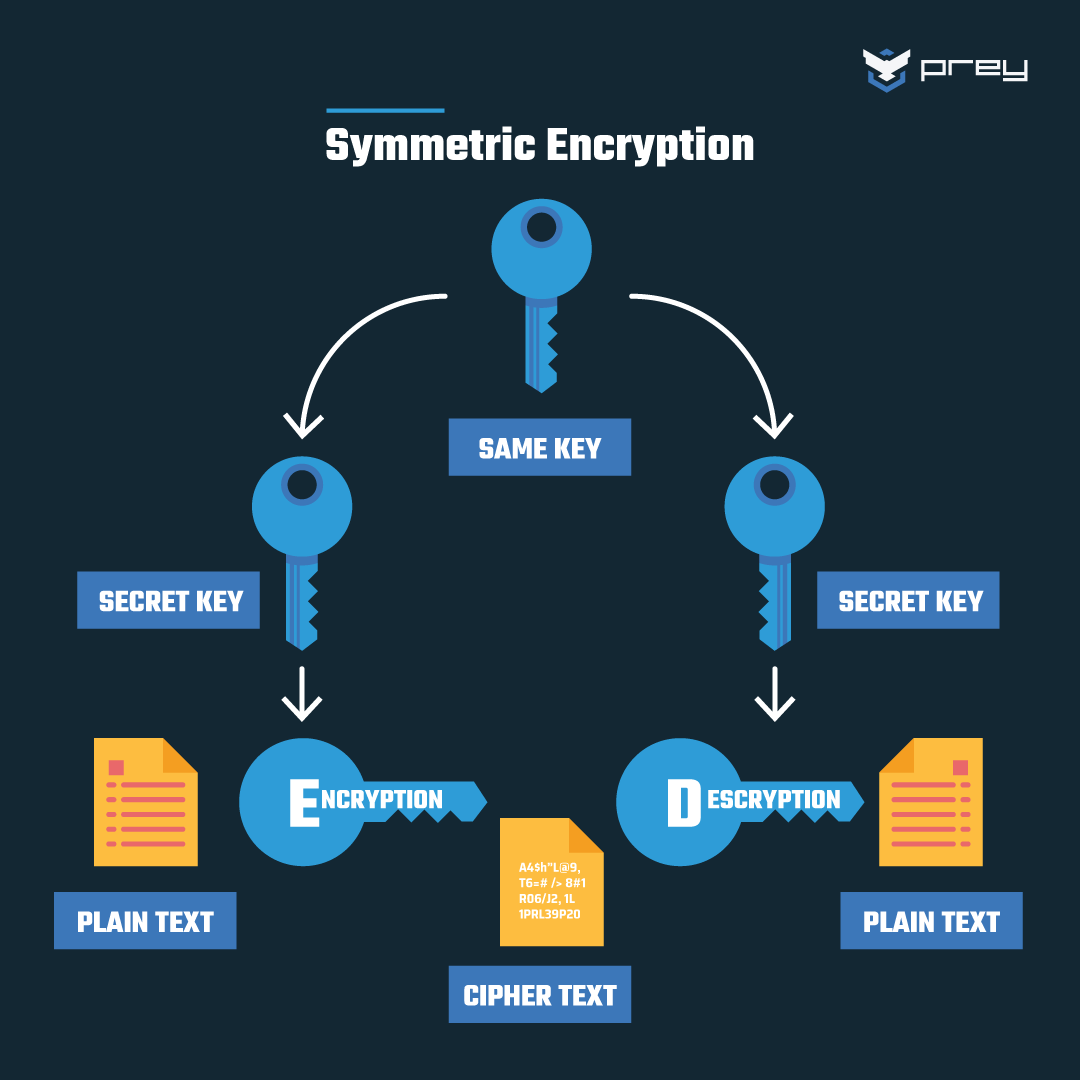
Symmetric Key Cryptography Example
Symmetric Key Cryptography Example - Symmetric Key Cryptography Example, Symmetric Key Crypto Example, Symmetric Key Encryption Example, Symmetric Key Cipher Example, Symmetric Key Encryption Example Java, Symmetric Key Encryption Algorithm Example, Python Symmetric Key Encryption Example, What Is Symmetric Key Cryptography, Types Of Symmetric Key Cryptography, What Is The Difference Between Symmetric Key Cryptography And Asymmetric Key Cryptography
ChatGPT is an AI model that uses deep learning to generate human like text based on prompts from users like you It works by predicting the next word in a given text based on the patterns
ChatGPT helps you get answers find inspiration and be more productive It is free to use and easy to try Just ask and ChatGPT can help with writing learning brainstorming and more
Symmetric Key Cryptography Example encompass a wide selection of printable and downloadable materials available online at no cost. These materials come in a variety of forms, like worksheets coloring pages, templates and more. The benefit of Symmetric Key Cryptography Example lies in their versatility as well as accessibility.
More of Symmetric Key Cryptography Example
What Is Symmetric And Asymmetric Encryption Examples

What Is Symmetric And Asymmetric Encryption Examples
Anyone can utilize ChatGPT for free on the web and via the mobile apps for Android and iOS or using the ChatGPT Mac app Our beginner tips for the platform will help
ChatGPT is a chatbot created by OpenAI that can process text image audio and video data to answer questions solve problems and more Here s how it works its use cases
Print-friendly freebies have gained tremendous recognition for a variety of compelling motives:
-
Cost-Efficiency: They eliminate the need to purchase physical copies of the software or expensive hardware.
-
customization You can tailor the templates to meet your individual needs for invitations, whether that's creating them and schedules, or even decorating your home.
-
Educational Value Educational printables that can be downloaded for free are designed to appeal to students of all ages. This makes them a valuable tool for parents and educators.
-
Easy to use: instant access a myriad of designs as well as templates cuts down on time and efforts.
Where to Find more Symmetric Key Cryptography Example
What Is Public Key Cryptography Twilio

What Is Public Key Cryptography Twilio
More than 100 million people across 185 countries use ChatGPT weekly to learn something new find creative inspiration and get answers to their questions Starting today
The GPT stands for Generative Pre trained Transformer which refers to how ChatGPT processes requests and formulates responses ChatGPT is trained with
Since we've got your curiosity about Symmetric Key Cryptography Example and other printables, let's discover where they are hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy offer an extensive collection of Symmetric Key Cryptography Example for various uses.
- Explore categories such as interior decor, education, organizing, and crafts.
2. Educational Platforms
- Forums and educational websites often provide worksheets that can be printed for free, flashcards, and learning tools.
- The perfect resource for parents, teachers and students who are in need of supplementary sources.
3. Creative Blogs
- Many bloggers post their original designs and templates for no cost.
- The blogs are a vast selection of subjects, starting from DIY projects to party planning.
Maximizing Symmetric Key Cryptography Example
Here are some innovative ways how you could make the most use of printables for free:
1. Home Decor
- Print and frame stunning art, quotes, and seasonal decorations, to add a touch of elegance to your living areas.
2. Education
- Use printable worksheets for free to enhance learning at home either in the schoolroom or at home.
3. Event Planning
- Make invitations, banners as well as decorations for special occasions like birthdays and weddings.
4. Organization
- Get organized with printable calendars as well as to-do lists and meal planners.
Conclusion
Symmetric Key Cryptography Example are an abundance filled with creative and practical information that can meet the needs of a variety of people and hobbies. Their availability and versatility make them an invaluable addition to any professional or personal life. Explore the wide world of Symmetric Key Cryptography Example right now and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables that are free truly completely free?
- Yes they are! You can download and print these tools for free.
-
Can I make use of free printables for commercial purposes?
- It's based on specific rules of usage. Always review the terms of use for the creator prior to printing printables for commercial projects.
-
Are there any copyright concerns with printables that are free?
- Some printables may contain restrictions in their usage. Check the terms and conditions provided by the designer.
-
How can I print printables for free?
- Print them at home using an printer, or go to a print shop in your area for high-quality prints.
-
What program do I need in order to open printables at no cost?
- The majority of printed documents are with PDF formats, which is open with no cost software such as Adobe Reader.
Symmetric Key Cryptography Cryptography Techniques Gate Vidyalay
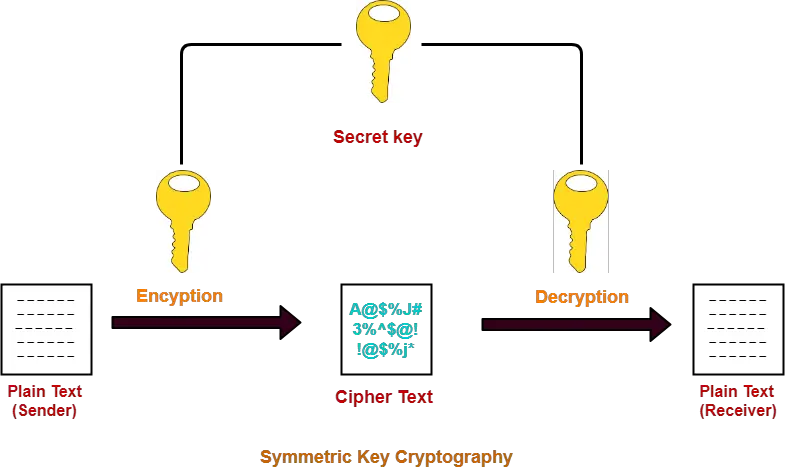
Symmetric Key Encryption Complete Guide To Symmetric Key Encryption

Check more sample of Symmetric Key Cryptography Example below
Asymmetric Vs Symmetric Encryption Graphic Illustrates The Symmetric

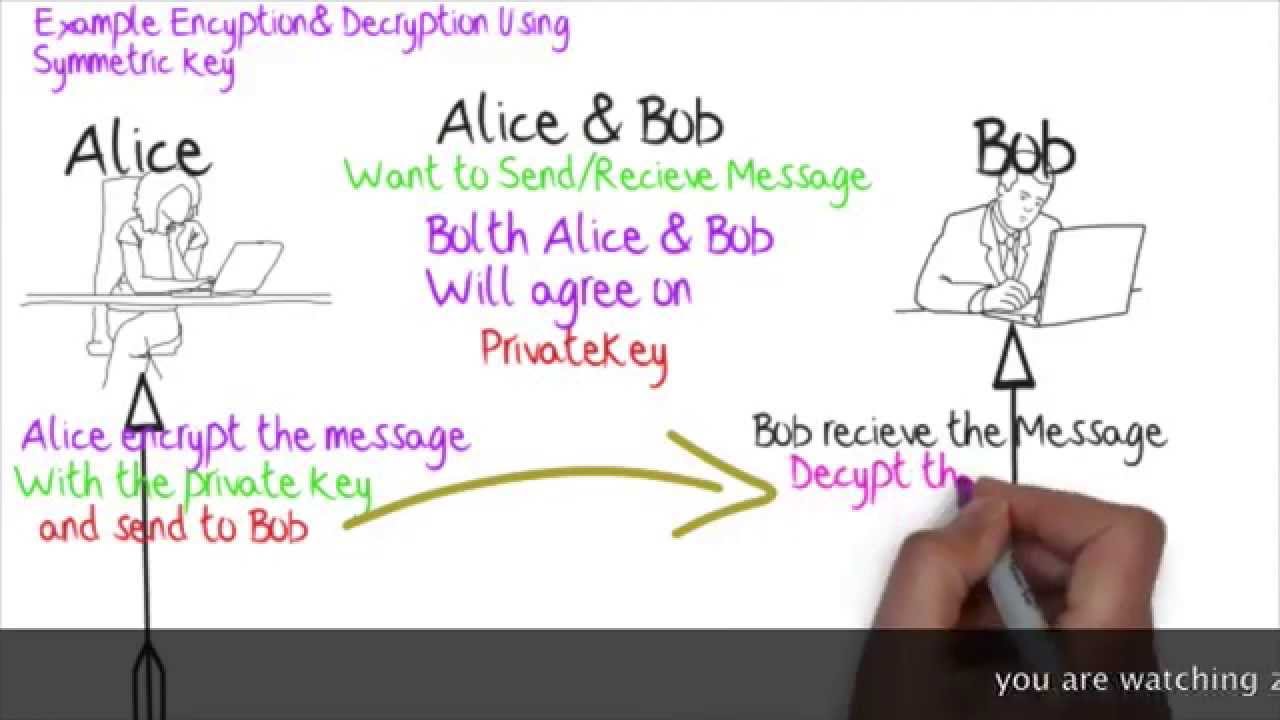
Symmetric Key Cryptography YouTube
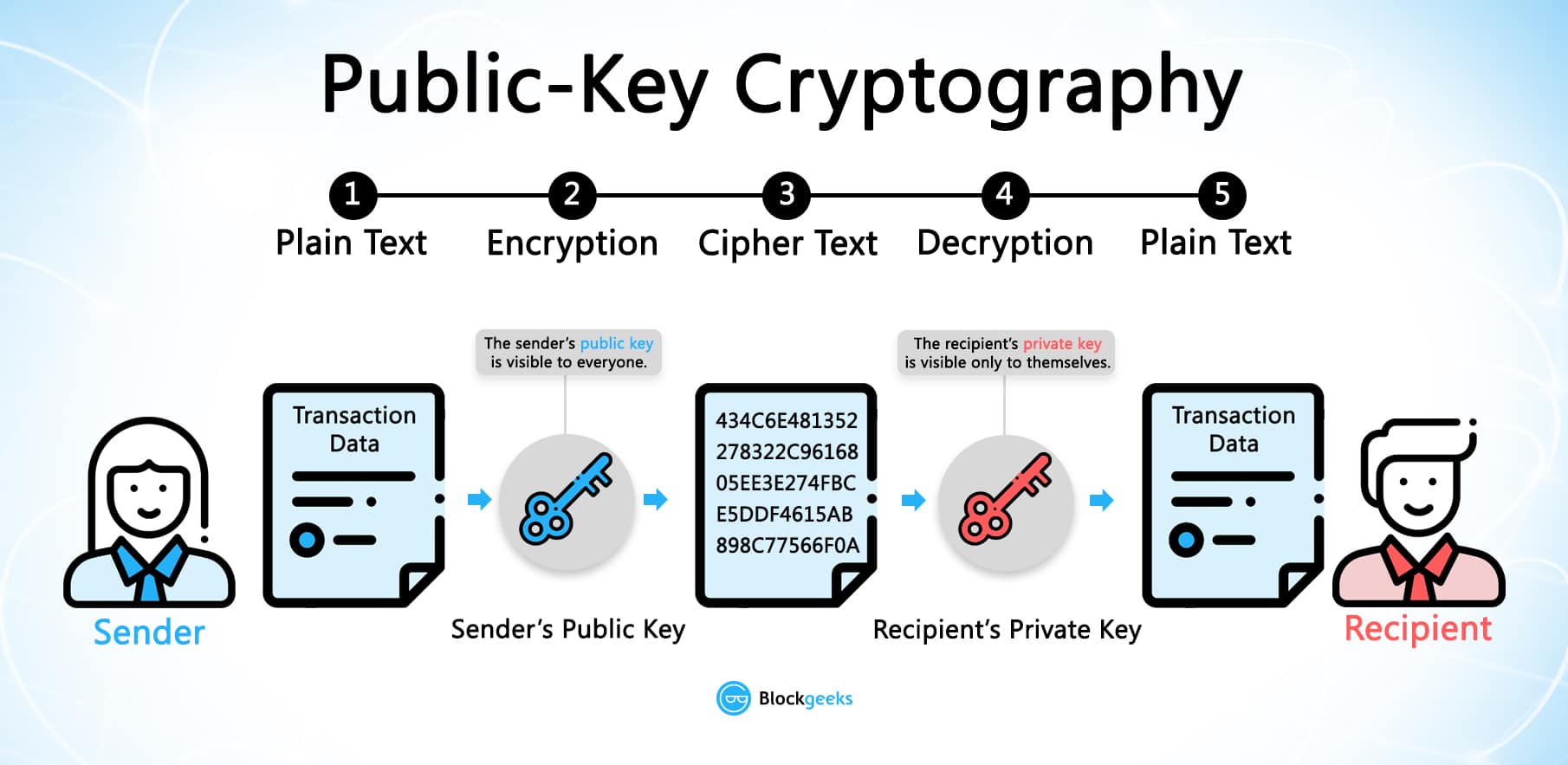
What Is Cryptoeconomics The Ultimate Beginners Guide Blockgeeks
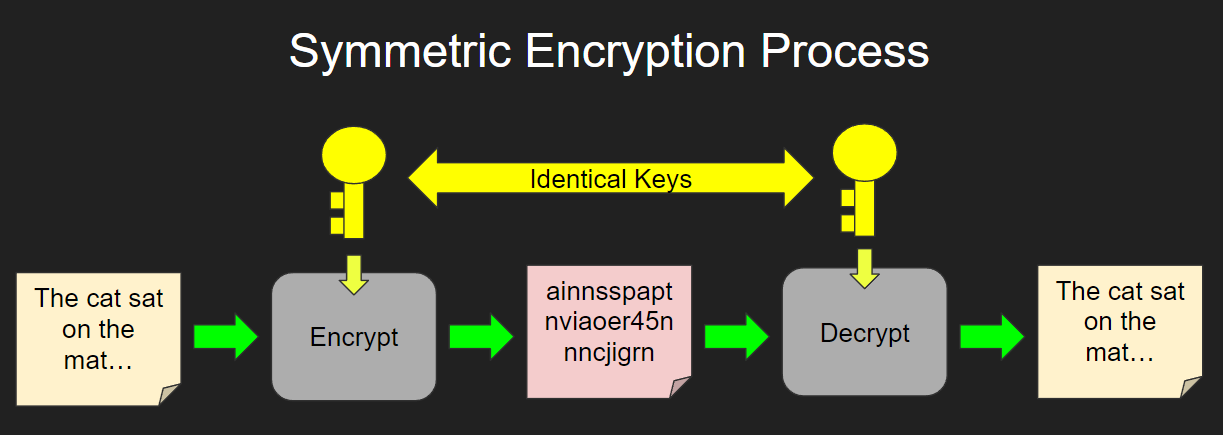
The Ultimate Guide To Symmetric Encryption
Symmetric Encryption IB Computer Science
An Exploration Of Symmetric Key Cryptography History Working And

https://chatgpt.com
ChatGPT helps you get answers find inspiration and be more productive It is free to use and easy to try Just ask and ChatGPT can help with writing learning brainstorming and more

https://www.pcmag.com › explainers › what-is-chatgpt-everything-you …
In the most basic sense ChatGPT is a conversational website or mobile app that fields requests from humans People have found many creative uses for it including writing
ChatGPT helps you get answers find inspiration and be more productive It is free to use and easy to try Just ask and ChatGPT can help with writing learning brainstorming and more
In the most basic sense ChatGPT is a conversational website or mobile app that fields requests from humans People have found many creative uses for it including writing
The Ultimate Guide To Symmetric Encryption

Symmetric Key Cryptography YouTube

Symmetric Encryption IB Computer Science

An Exploration Of Symmetric Key Cryptography History Working And

Symmetric Key Cryptography Download Scientific Diagram

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023
The Ultimate Guide To Symmetric Encryption