In the age of digital, with screens dominating our lives, the charm of tangible printed materials hasn't faded away. Whatever the reason, whether for education, creative projects, or simply to add the personal touch to your area, Ssh Private Key Example are a great source. With this guide, you'll take a dive into the sphere of "Ssh Private Key Example," exploring what they are, where to find them, and how they can enhance various aspects of your lives.
Get Latest Ssh Private Key Example Below

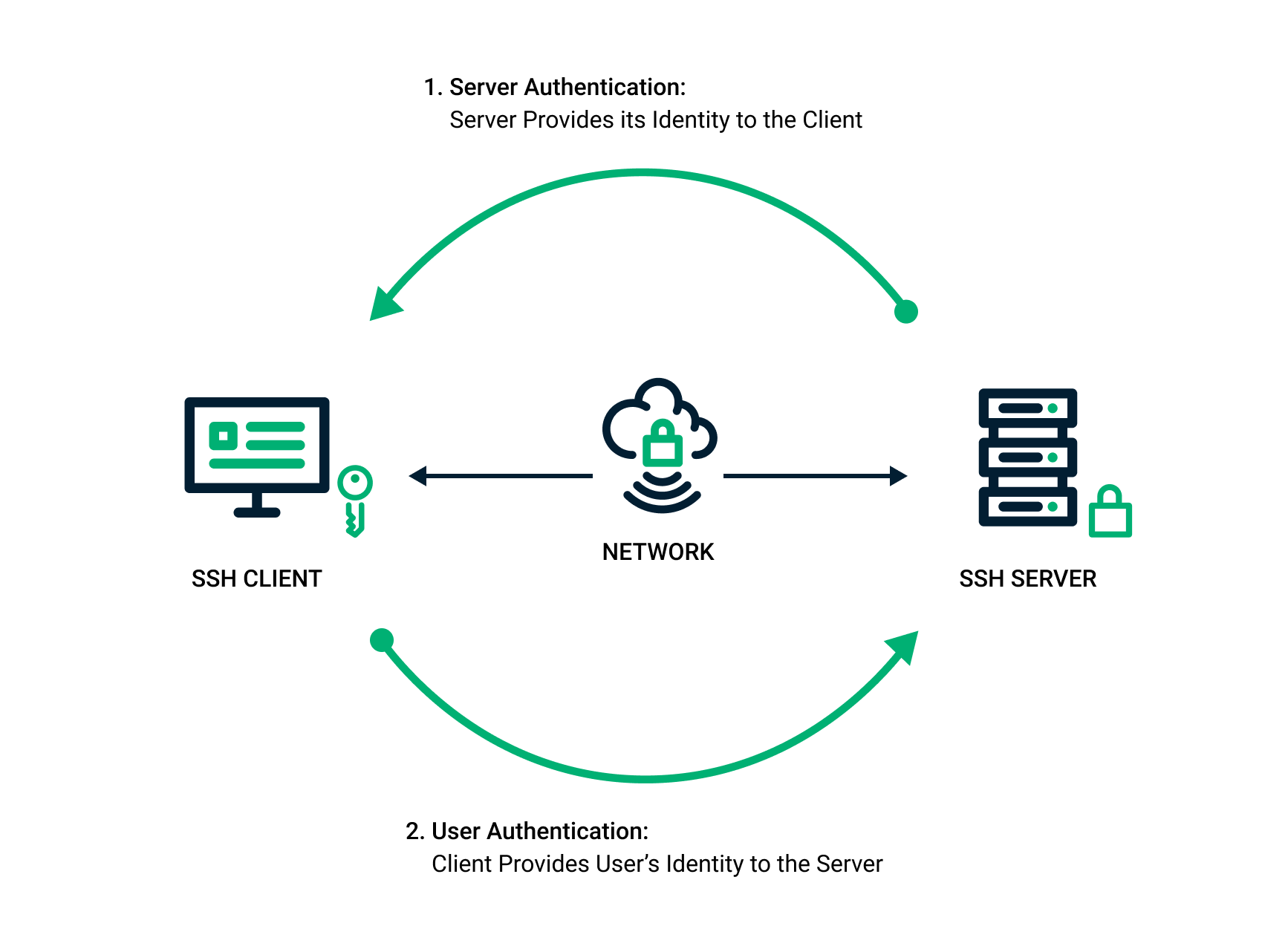
Ssh Private Key Example
Ssh Private Key Example - Ssh Private Key Example, Ssh Public Key Example, Openssh Private Key Example, Ssh Public Key Example Format, Renci Ssh Private Key Example, Paramiko Ssh Private Key Example, Ssh Ed25519 Public Key Example, Ssh Public Key Authentication Example, Begin Openssh Private Key Example, Ssh Public Key File Example
SSH sits on top of TCP When you get connection timed out errors it means that the problem is that the SSH client is not seeing any responses from the server ie the TCP
This symptom also occurs due to an SSH 2 rekey bug which causes PuTTY to report Remote side sent SSH2 MSG EXT INFO after USERAUTH SUCCESS The bug
Ssh Private Key Example encompass a wide selection of printable and downloadable documents that can be downloaded online at no cost. They come in many forms, like worksheets coloring pages, templates and much more. The attraction of printables that are free is their flexibility and accessibility.
More of Ssh Private Key Example
Images Of SSH JapaneseClass jp
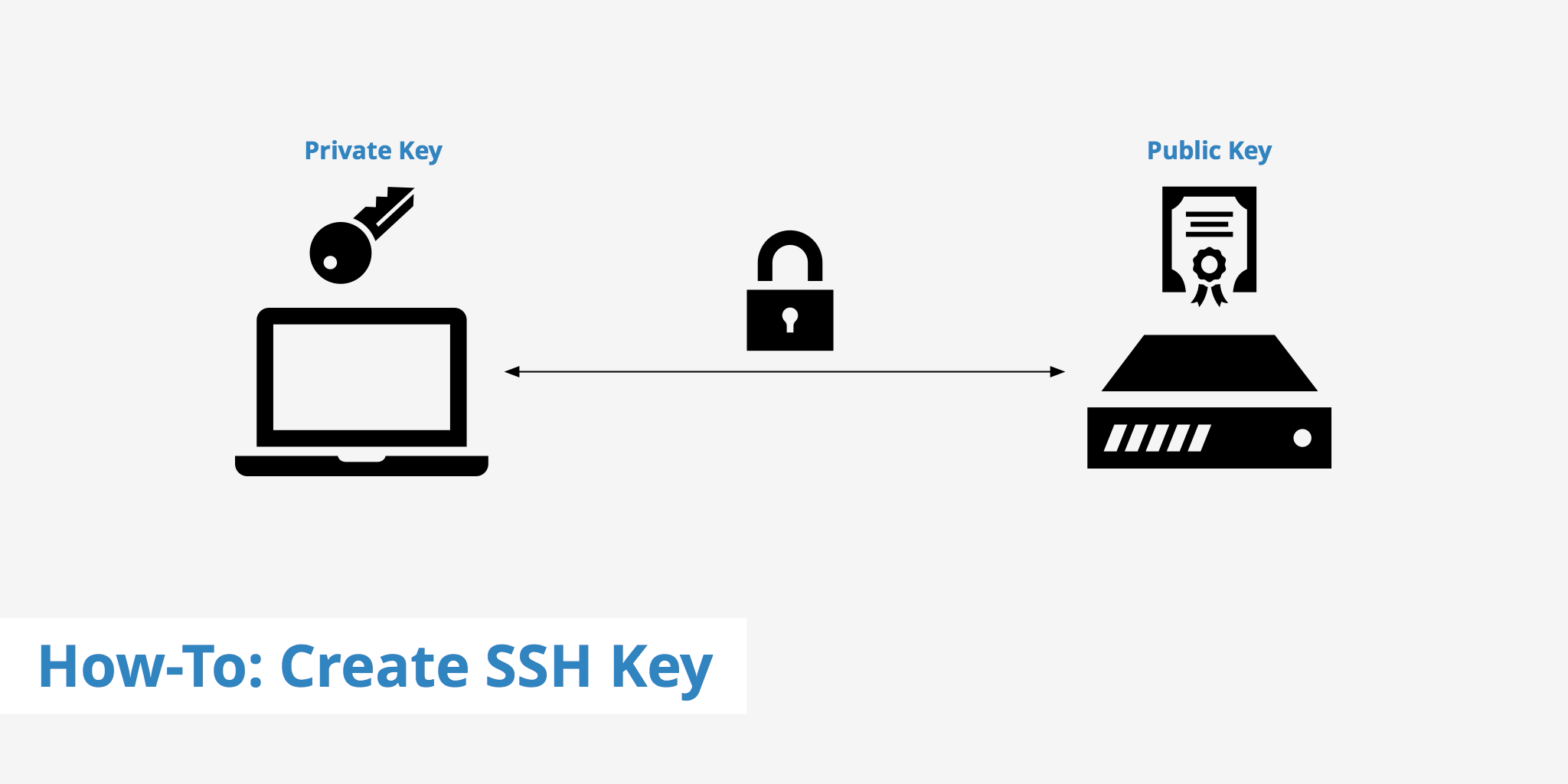
Images Of SSH JapaneseClass jp
No there isn t SSH does not have a client filesystem access channel the way RDP does Though there might be terminals that have built in support for the ancient BBS file
OpenSSH 7 6p1 Ubuntu 4ubuntu0 3 OpenSSL 1 0 2n 7 Dec 2017 debug1 Reading configuration data etc ssh ssh config debug1 etc ssh ssh config line 19 Applying
The Ssh Private Key Example have gained huge appeal due to many compelling reasons:
-
Cost-Efficiency: They eliminate the necessity of purchasing physical copies or costly software.
-
The ability to customize: The Customization feature lets you tailor printables to fit your particular needs, whether it's designing invitations to organize your schedule or decorating your home.
-
Educational Value Education-related printables at no charge offer a wide range of educational content for learners from all ages, making these printables a powerful tool for parents and teachers.
-
Convenience: Access to a plethora of designs and templates will save you time and effort.
Where to Find more Ssh Private Key Example
Configure Ssh Keys Windows
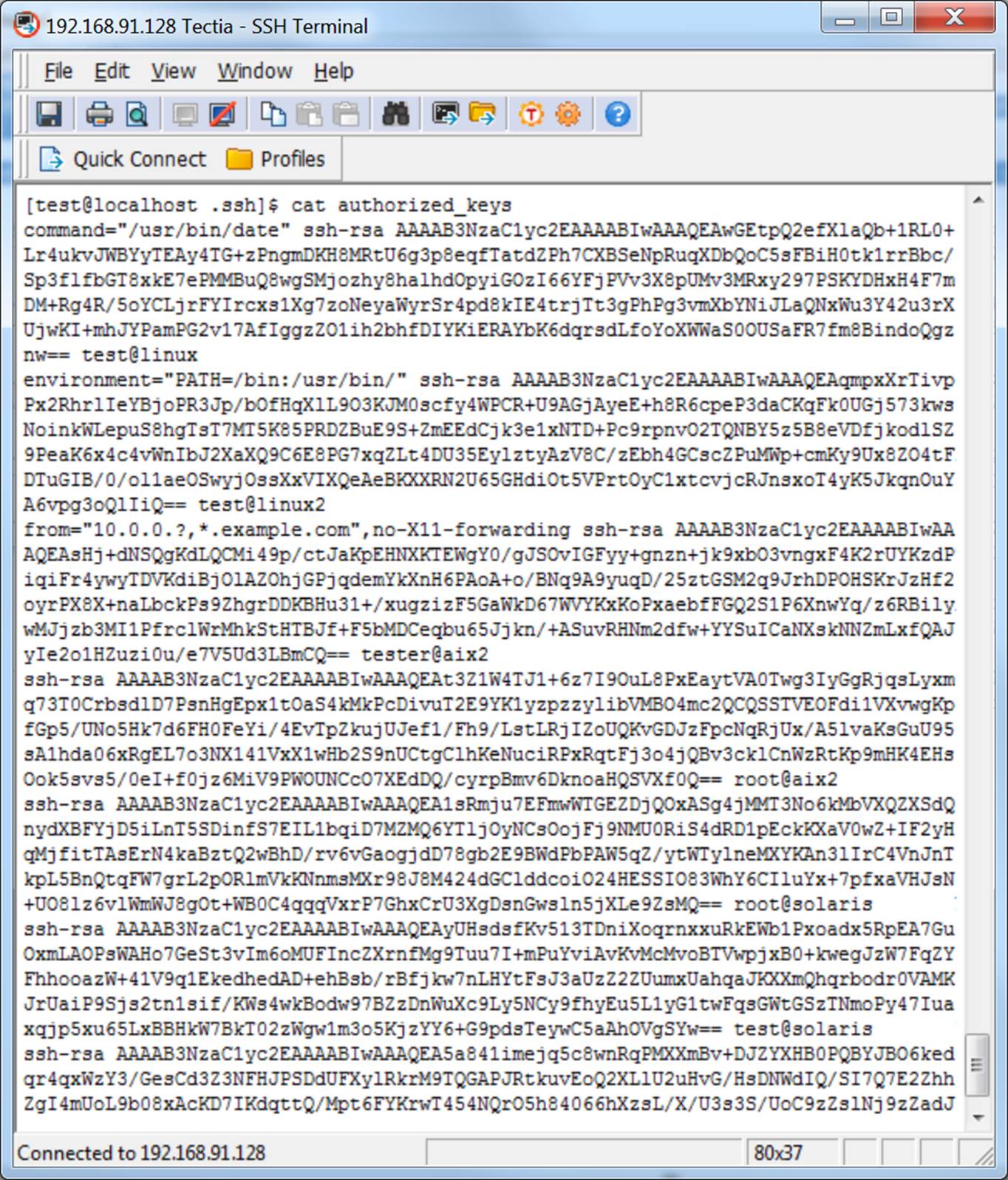
Configure Ssh Keys Windows
For context I ssh to a vast multitude of linux distributions and some Solaris hosts using mostly Ubuntu CentOS and MacOS X as my client systems Almost all of the time the
Normally if you pass a command to ssh like so ssh email protected some command sh You get a non interactive session and ssh exits as soon as the command or
Since we've got your interest in Ssh Private Key Example, let's explore where you can find these treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy offer a huge selection and Ssh Private Key Example for a variety objectives.
- Explore categories like decoration for your home, education, management, and craft.
2. Educational Platforms
- Educational websites and forums usually provide free printable worksheets along with flashcards, as well as other learning tools.
- Ideal for parents, teachers as well as students searching for supplementary sources.
3. Creative Blogs
- Many bloggers share their innovative designs and templates for no cost.
- The blogs are a vast range of topics, including DIY projects to party planning.
Maximizing Ssh Private Key Example
Here are some new ways create the maximum value use of Ssh Private Key Example:
1. Home Decor
- Print and frame beautiful art, quotes, and seasonal decorations, to add a touch of elegance to your living spaces.
2. Education
- Use printable worksheets for free to aid in learning at your home and in class.
3. Event Planning
- Make invitations, banners and decorations for special events like weddings and birthdays.
4. Organization
- Get organized with printable calendars or to-do lists. meal planners.
Conclusion
Ssh Private Key Example are a treasure trove of practical and innovative resources designed to meet a range of needs and interests. Their access and versatility makes they a beneficial addition to every aspect of your life, both professional and personal. Explore the many options of Ssh Private Key Example today and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables for free really for free?
- Yes, they are! You can print and download these documents for free.
-
Can I use the free templates for commercial use?
- It's determined by the specific rules of usage. Make sure you read the guidelines for the creator prior to printing printables for commercial projects.
-
Are there any copyright rights issues with Ssh Private Key Example?
- Some printables may come with restrictions concerning their use. Make sure you read the terms and conditions provided by the designer.
-
How do I print Ssh Private Key Example?
- You can print them at home using your printer or visit the local print shops for higher quality prints.
-
What software is required to open printables for free?
- The majority are printed in PDF format. These can be opened using free software such as Adobe Reader.
Learn SSH Keys In Minutes

Install Ssh Client Mac Os Tidedelivery
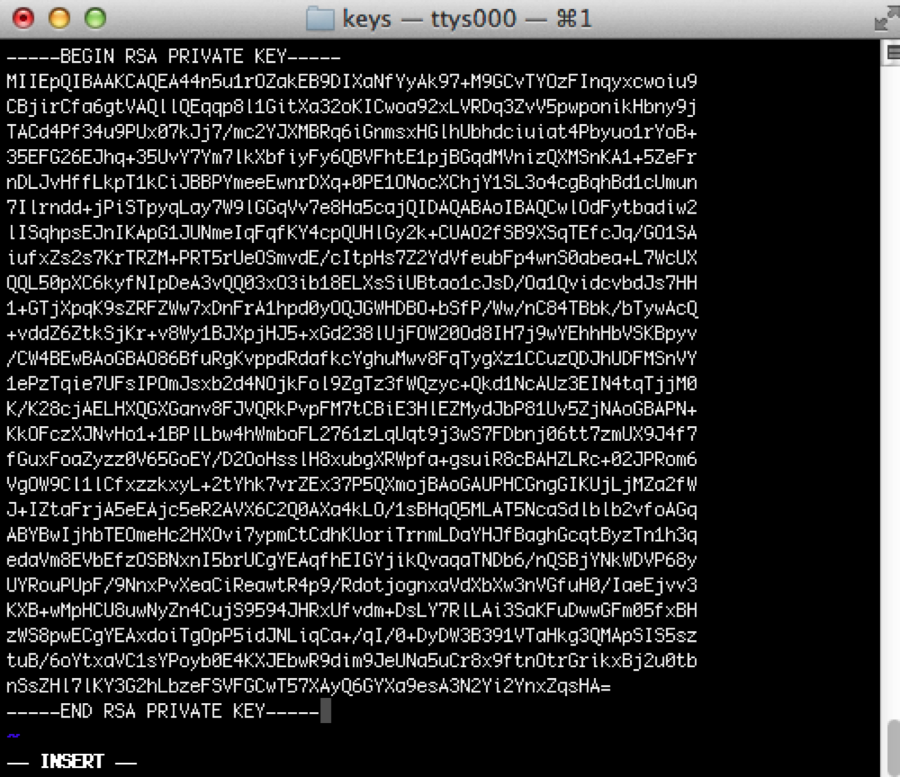
Check more sample of Ssh Private Key Example below
Windows SSH Server Learning Secure Shell Software Engineer

Comparing SSH Keys RSA DSA ECDSA Or EdDSA
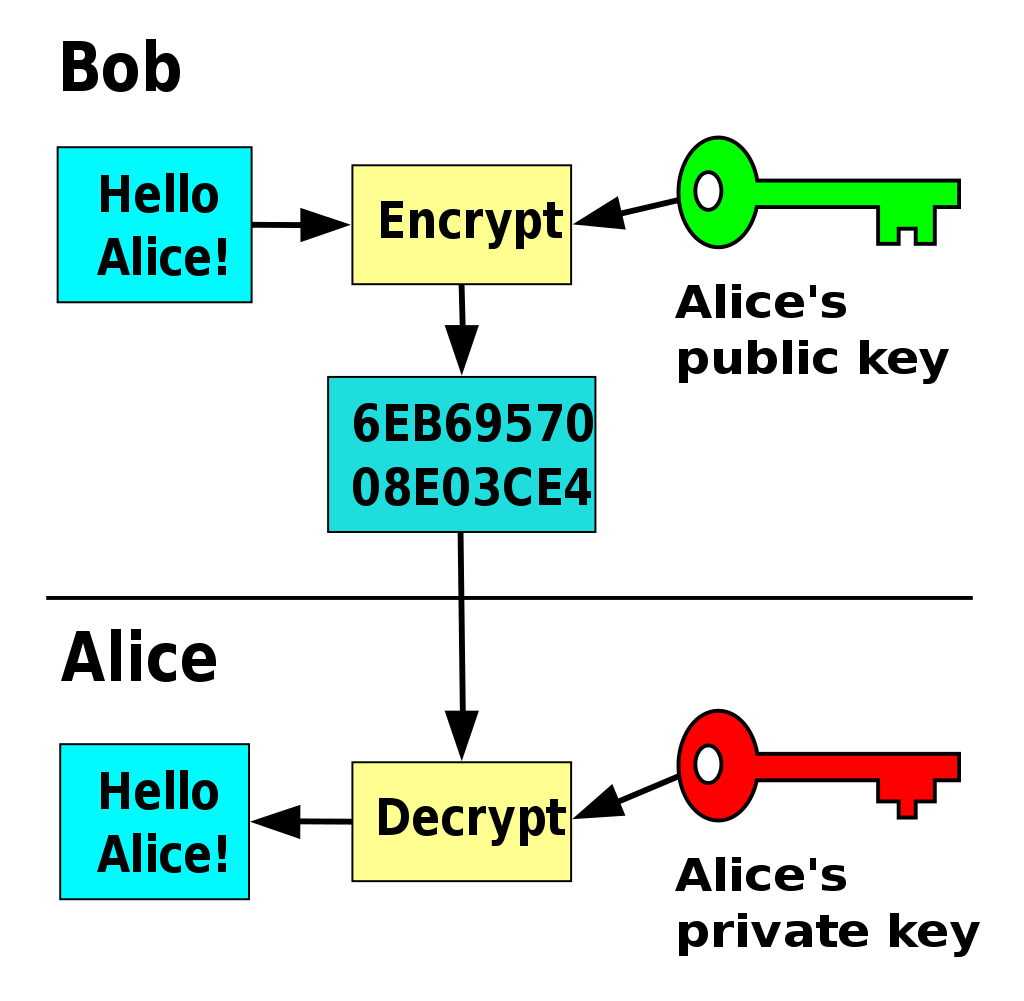
Ssh Copy Key Silopegiga
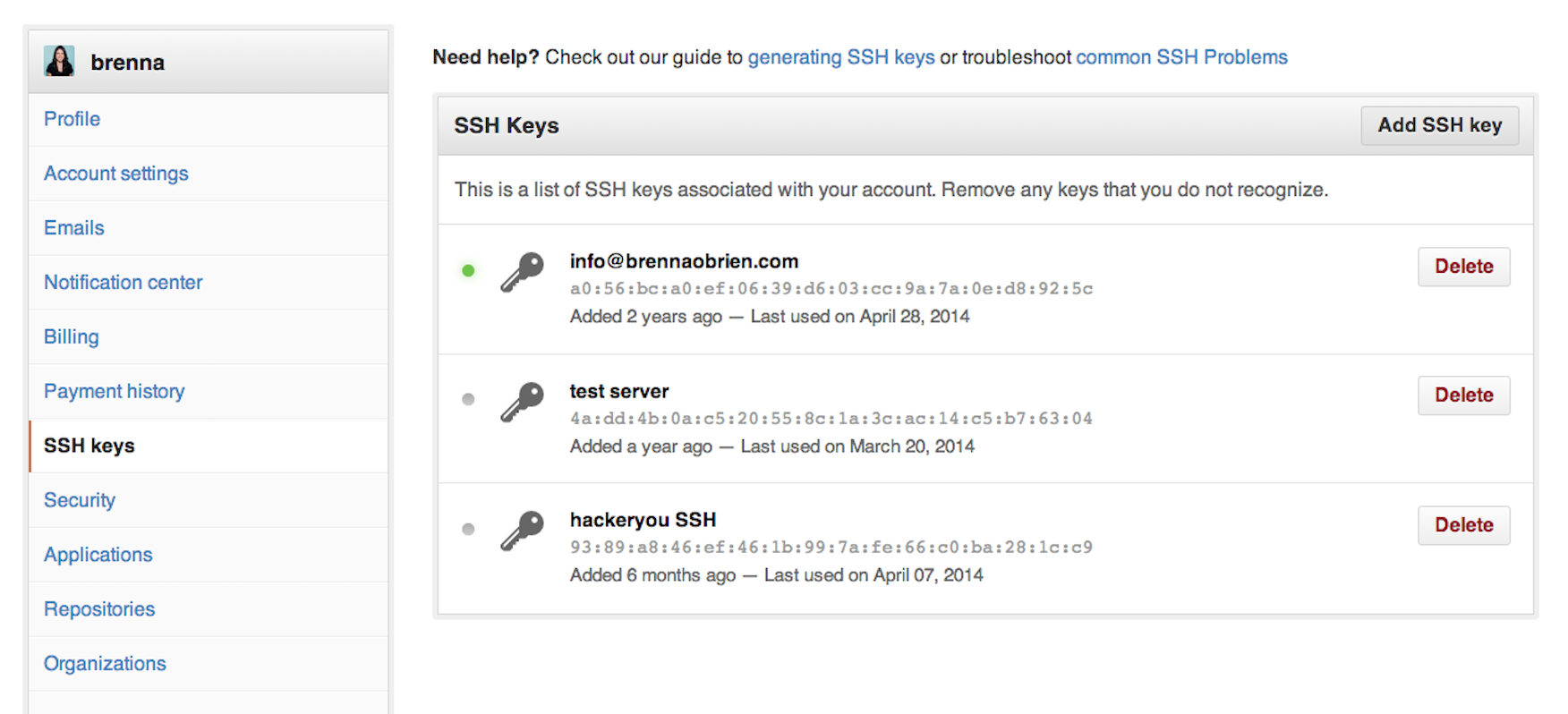
Ssh Private Keys Mikrotik Telegraph

Public Key Vs Private Key Encryption Arqma Coin

Git ssh ChuckLu


https://superuser.com › questions
This symptom also occurs due to an SSH 2 rekey bug which causes PuTTY to report Remote side sent SSH2 MSG EXT INFO after USERAUTH SUCCESS The bug
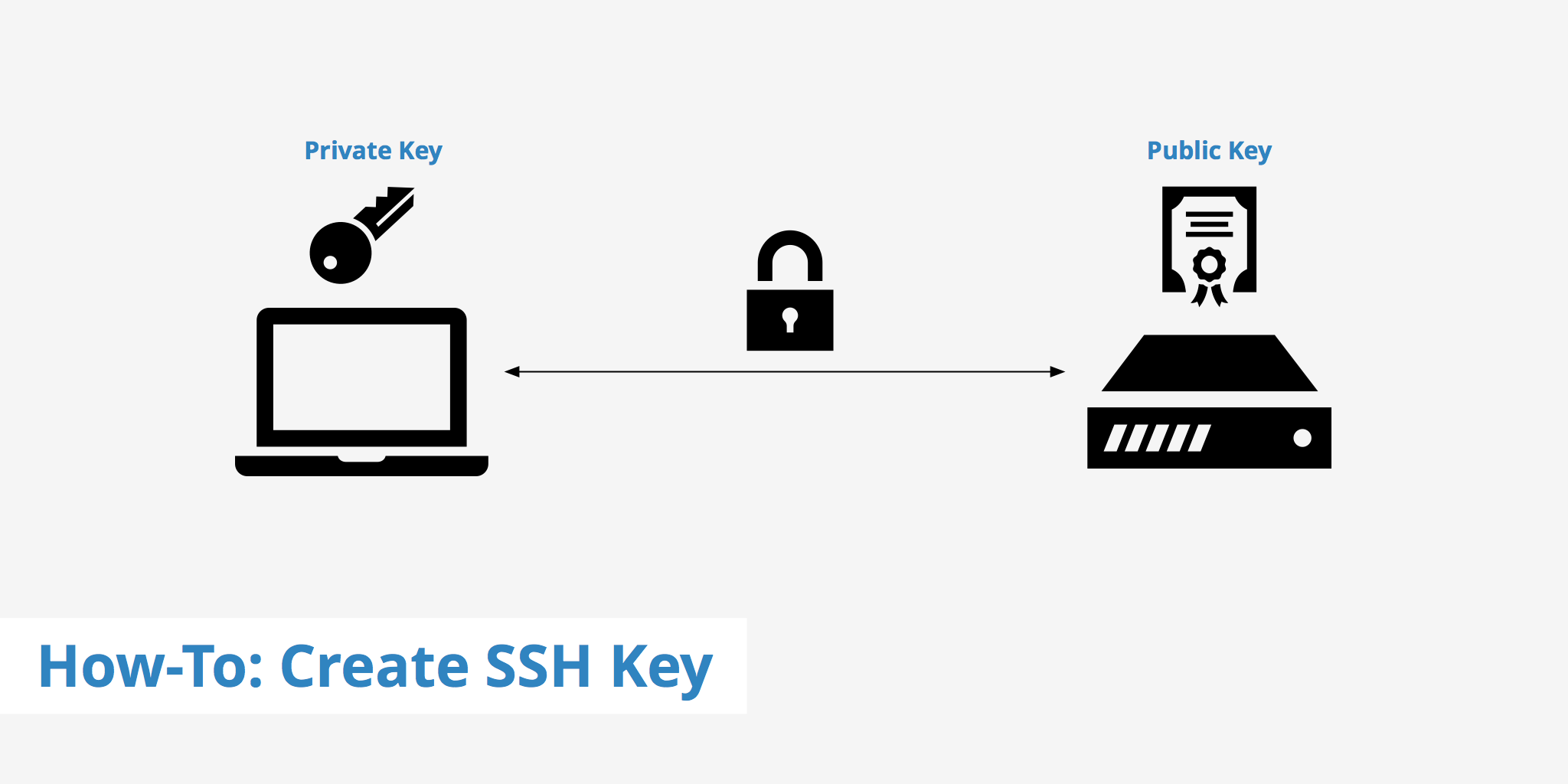
https://superuser.com › questions
Ssh has the i option to tell which private key file to use when authenticating i identity fileSelects a file from which the identity private key for RSA or DSA authentication is read
This symptom also occurs due to an SSH 2 rekey bug which causes PuTTY to report Remote side sent SSH2 MSG EXT INFO after USERAUTH SUCCESS The bug
Ssh has the i option to tell which private key file to use when authenticating i identity fileSelects a file from which the identity private key for RSA or DSA authentication is read

Ssh Private Keys Mikrotik Telegraph

Comparing SSH Keys RSA DSA ECDSA Or EdDSA

Public Key Vs Private Key Encryption Arqma Coin

Git ssh ChuckLu
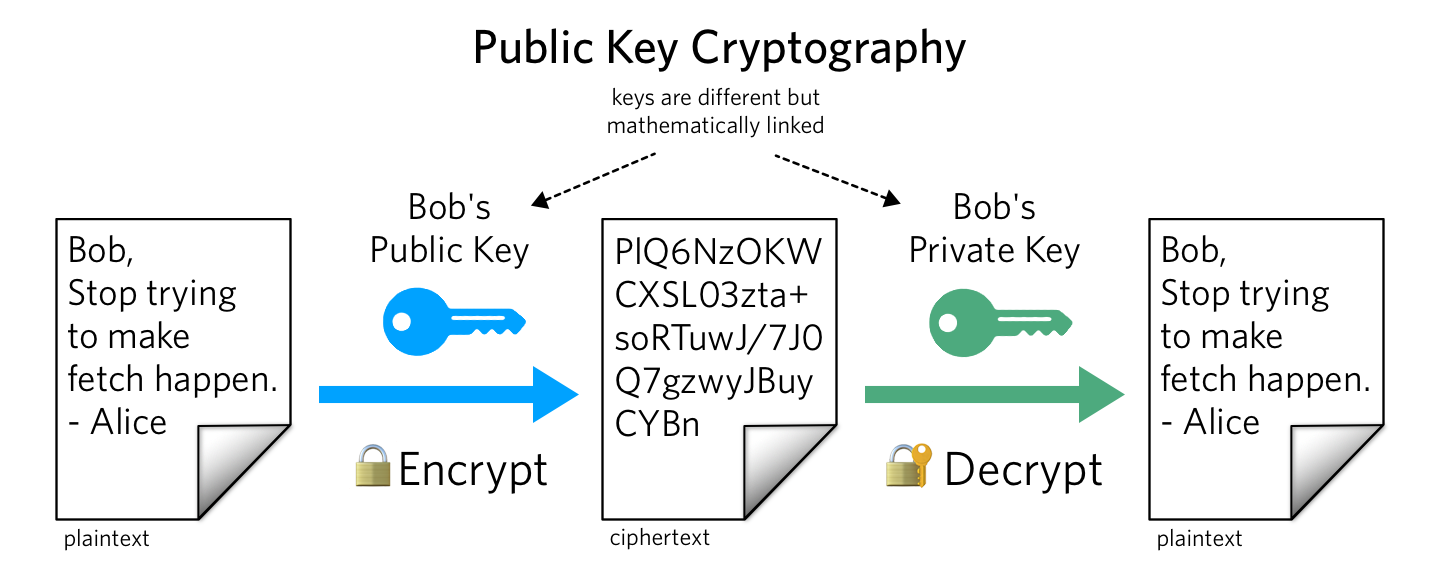
What Is Public Key Cryptography
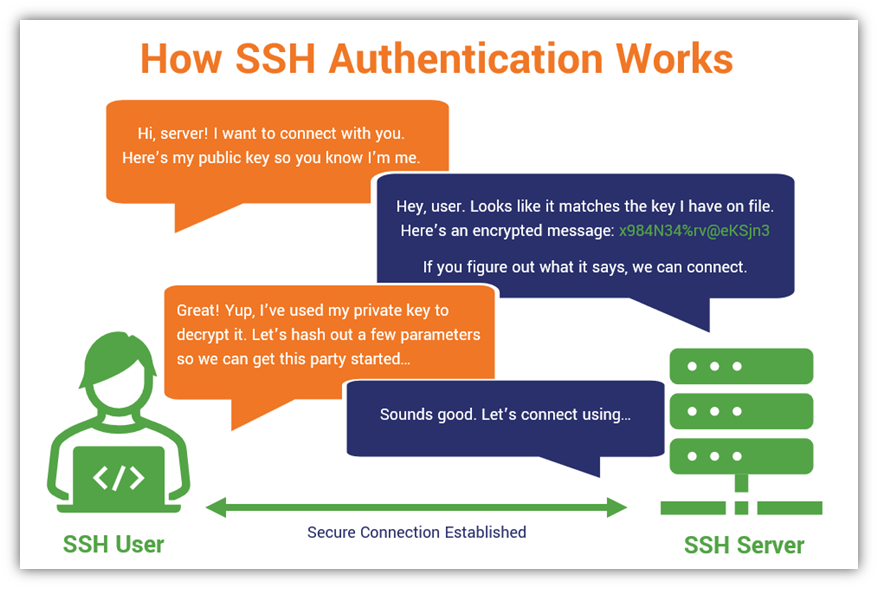
Managing SSH Key Pairs UW Milwaukee Cloud Computing

Managing SSH Key Pairs UW Milwaukee Cloud Computing
Unafraid Your EC2 Cases Easy SSH Keypair Direction With AWS CDK Java