Today, in which screens are the norm and the appeal of physical printed items hasn't gone away. No matter whether it's for educational uses and creative work, or simply to add the personal touch to your space, It Security Risk Assessment Example are now an essential source. Through this post, we'll take a dive to the depths of "It Security Risk Assessment Example," exploring what they are, where they are available, and what they can do to improve different aspects of your lives.
Get Latest It Security Risk Assessment Example Below
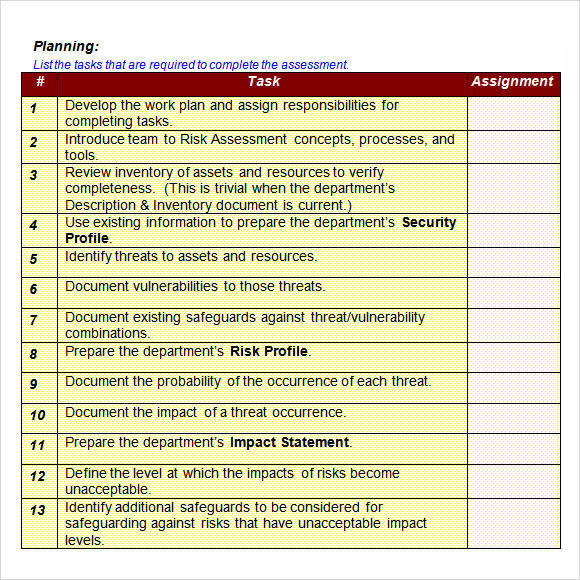
It Security Risk Assessment Example
It Security Risk Assessment Example - It Security Risk Assessment Example, Cyber Security Risk Assessment Example, Cyber Security Risk Assessment Example Pdf, Data Security Risk Assessment Example, It Security Risk Assessment Template, It Security Risk Assessment Template Excel, Cyber Security Risk Assessment Template Excel, Cyber Security Risk Assessment Sample, Cyber Security Risk Assessment Document, Cyber Security Risk Assessment Template Nist
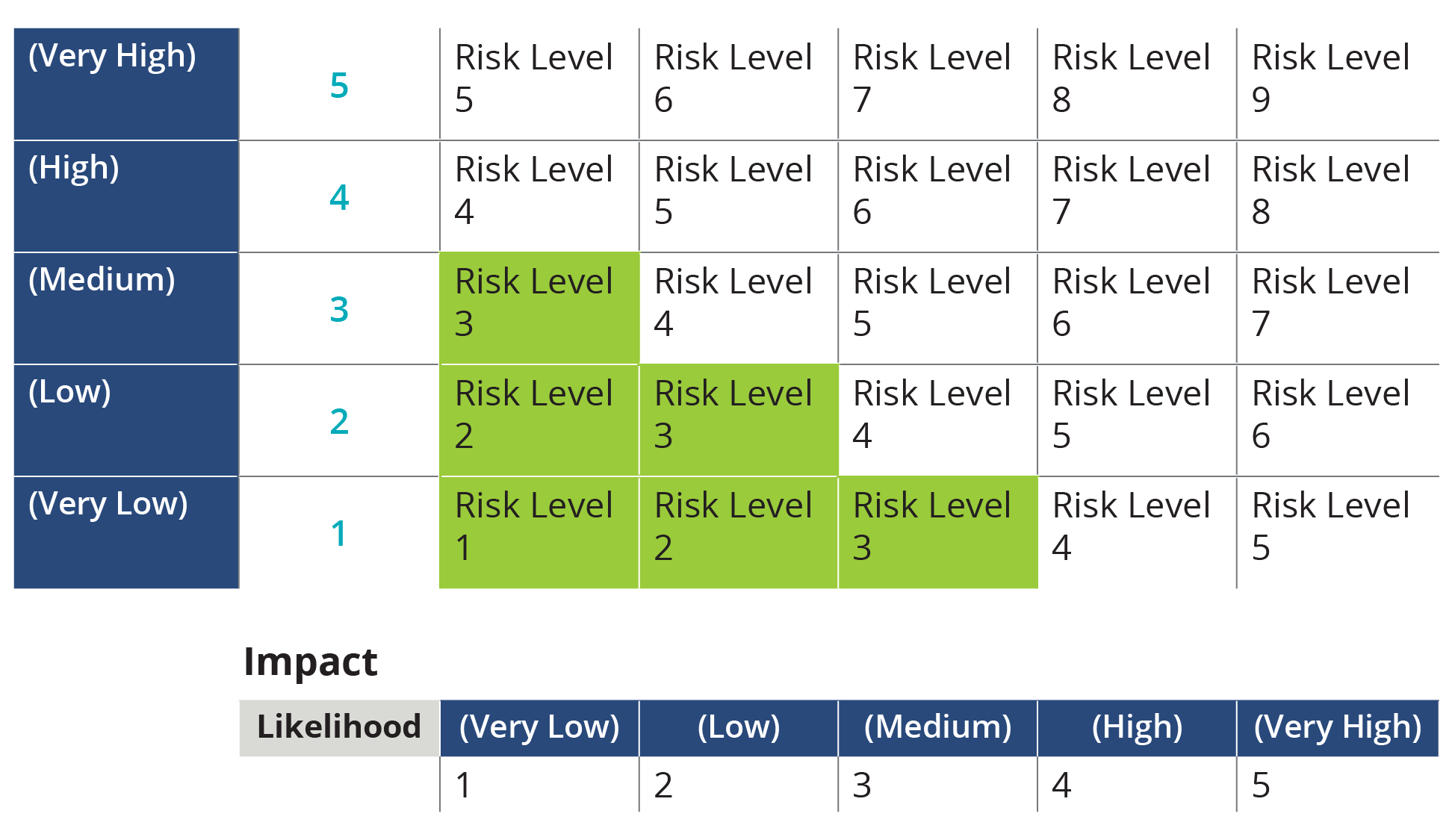
A risk matrix can also summarize your risk exposure at a third party vendor level Here s an example of a risk matrix representing the distribution of critical third party vendors requiring greater cybersecurity attention
In this article you ll find the most effective cybersecurity risk assessment templates for project managers security analysts security incident responders intrusion detection personnel vulnerability assessors and cryptologists
It Security Risk Assessment Example provide a diverse selection of printable and downloadable items that are available online at no cost. These printables come in different types, like worksheets, templates, coloring pages and more. The attraction of printables that are free is their versatility and accessibility.
More of It Security Risk Assessment Example
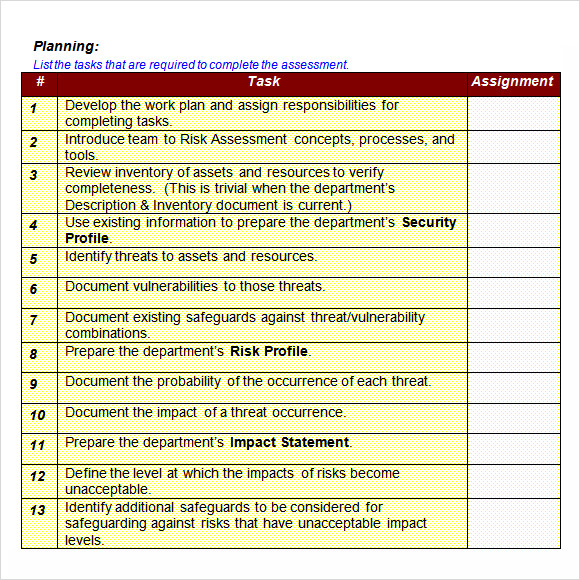
13 Information Security Risk Assessment Procedure Example docx
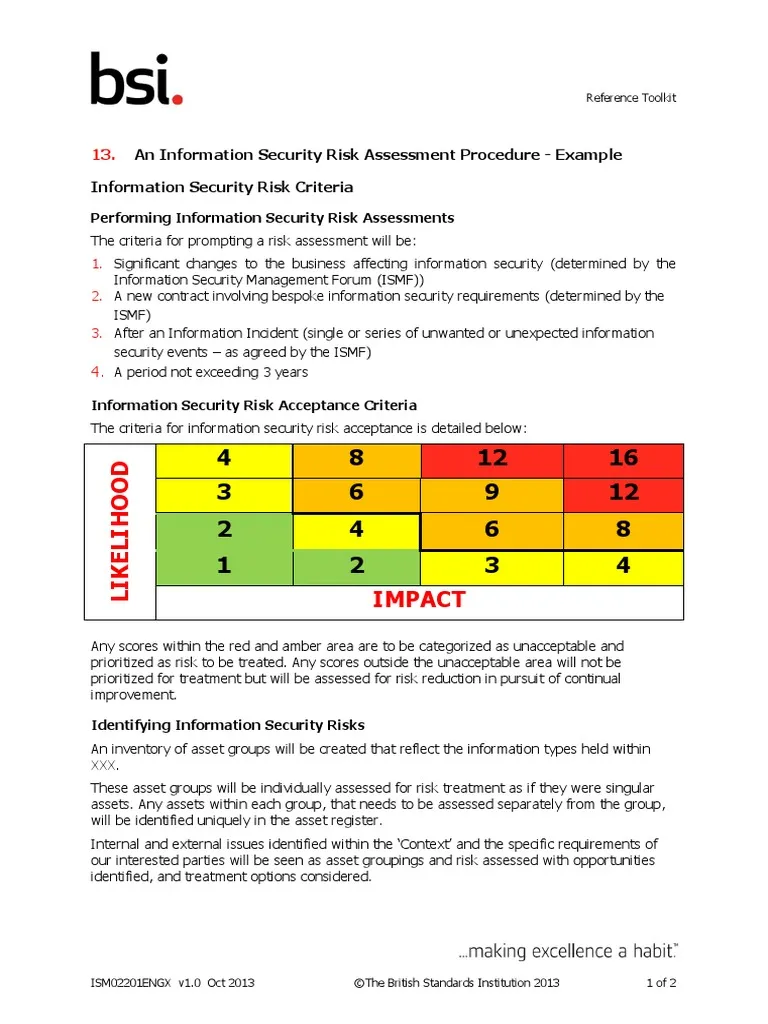
13 Information Security Risk Assessment Procedure Example docx
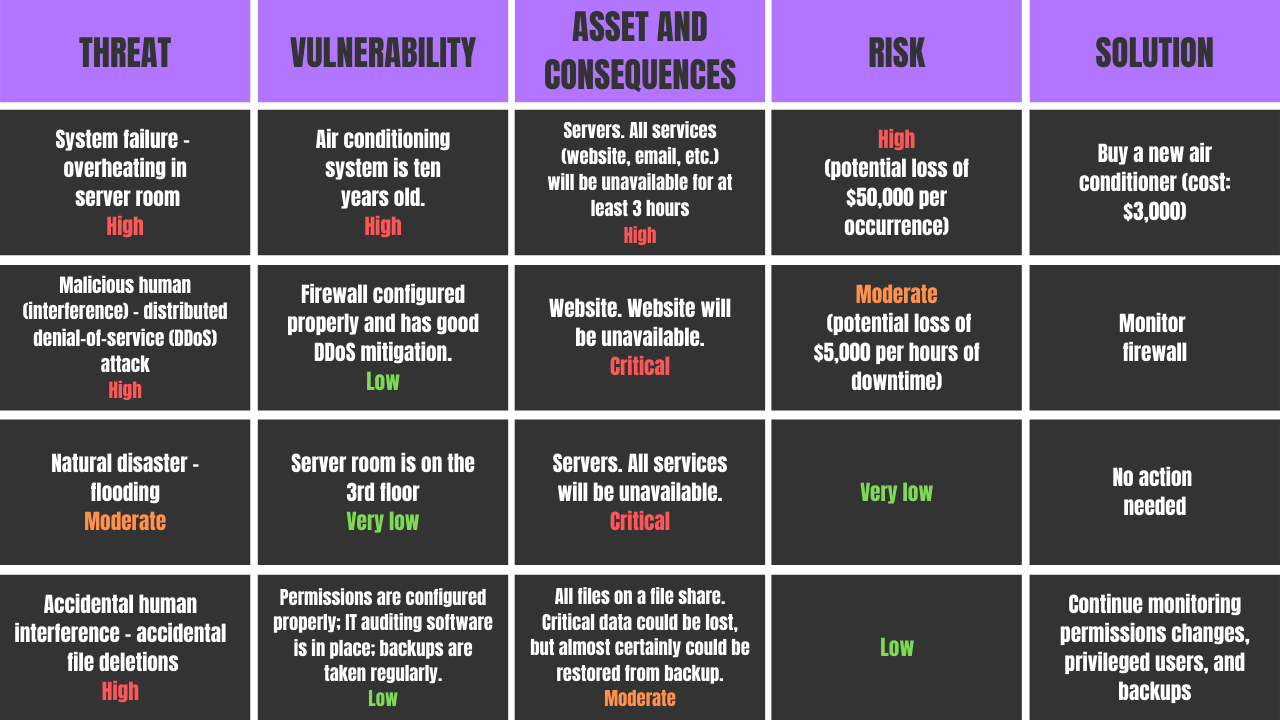
IT risk assessments are a crucial part of any successful security program Risk assessments allow you to see how your organization s risks and vulnerabilities are changing over time so decision makers can put appropriate measures and safeguards in place to respond to risks appropriately
Each of these resources provides examples of vendor risk assessments and include a series of questions that can help probe your third parties governance and approach to cybersecurity What is a cybersecurity IT risk assessment When you onboard new vendors you also assume any cyber risk associated with that organization And
The It Security Risk Assessment Example have gained huge popularity due to a myriad of compelling factors:
-
Cost-Efficiency: They eliminate the necessity to purchase physical copies or costly software.
-
The ability to customize: They can make the templates to meet your individual needs such as designing invitations or arranging your schedule or decorating your home.
-
Educational Worth: Free educational printables cater to learners of all ages. This makes the perfect device for teachers and parents.
-
Simple: Quick access to an array of designs and templates reduces time and effort.
Where to Find more It Security Risk Assessment Example
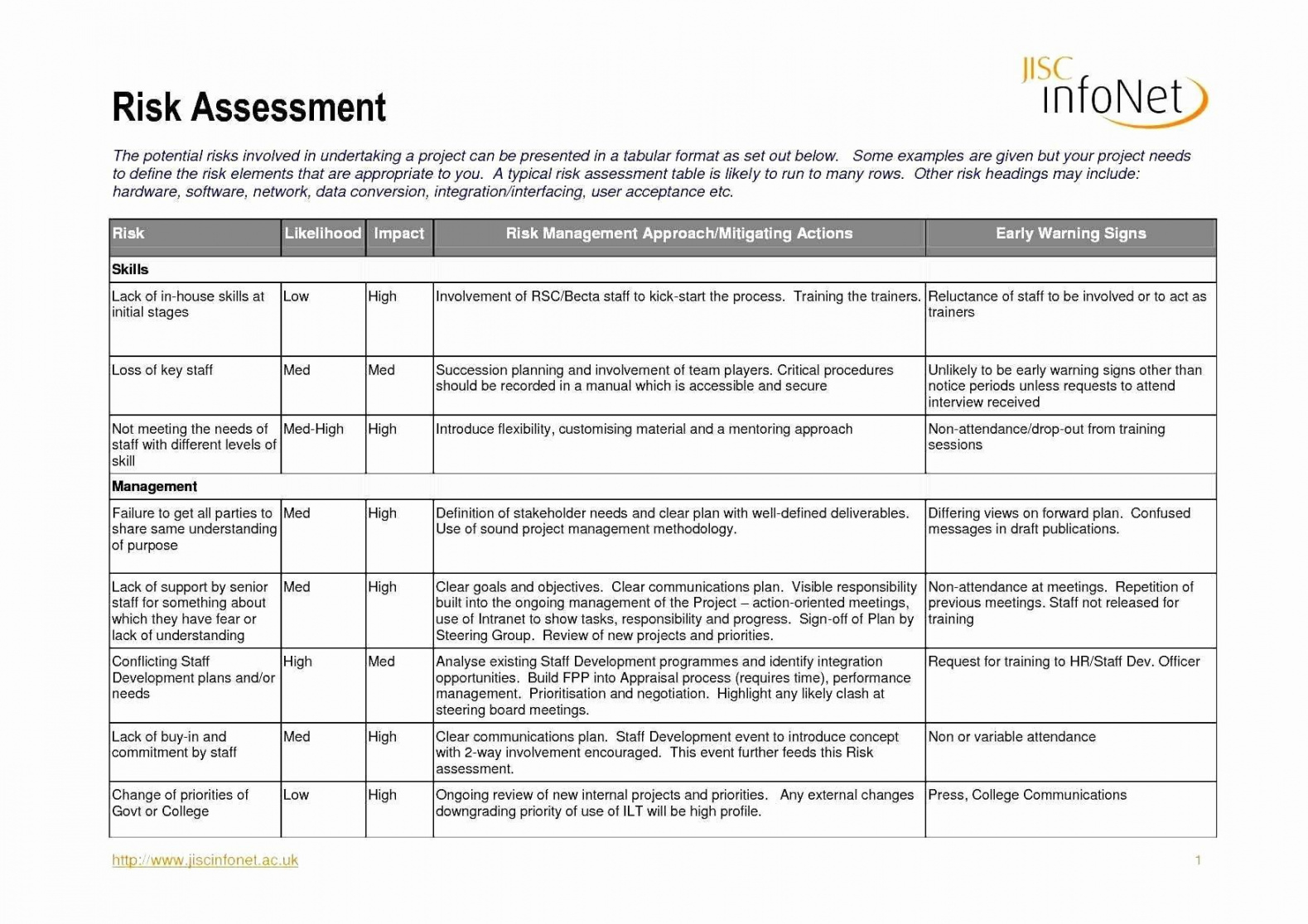
Network Security Risk Assessment Template SampleTemplatess

Network Security Risk Assessment Template SampleTemplatess
Performing the Risk Assessment The risk assessment both in the context of ISO 31000 and the DPIA ISO 29134 2017 can be based on the risk assessment model of ISO 31000 Following the application of the proposed controls or lack thereof the person responsible for the system observes the result of exposure to the
Developed to support the NIST Risk Management Framework and NIST Cybersecurity Framework SP 800 30 is a management template best suited for organizations required to meet standards built from the NIST CSF or other NIST publications i e defense and aerospace organizations federal organizations and contractors etc
We hope we've stimulated your curiosity about It Security Risk Assessment Example Let's find out where you can find these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide an extensive selection of It Security Risk Assessment Example to suit a variety of reasons.
- Explore categories such as interior decor, education, crafting, and organization.
2. Educational Platforms
- Forums and websites for education often offer worksheets with printables that are free along with flashcards, as well as other learning tools.
- Perfect for teachers, parents or students in search of additional resources.
3. Creative Blogs
- Many bloggers offer their unique designs and templates at no cost.
- The blogs are a vast selection of subjects, starting from DIY projects to planning a party.
Maximizing It Security Risk Assessment Example
Here are some inventive ways that you can make use use of printables for free:
1. Home Decor
- Print and frame stunning artwork, quotes, or even seasonal decorations to decorate your living areas.
2. Education
- Utilize free printable worksheets to aid in learning at your home and in class.
3. Event Planning
- Make invitations, banners and other decorations for special occasions like weddings or birthdays.
4. Organization
- Stay organized with printable planners as well as to-do lists and meal planners.
Conclusion
It Security Risk Assessment Example are a treasure trove of useful and creative resources which cater to a wide range of needs and interests. Their availability and versatility make them a wonderful addition to every aspect of your life, both professional and personal. Explore the vast collection of It Security Risk Assessment Example today to uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are It Security Risk Assessment Example really absolutely free?
- Yes you can! You can download and print these materials for free.
-
Are there any free printables to make commercial products?
- It's based on specific usage guidelines. Be sure to read the rules of the creator before using their printables for commercial projects.
-
Do you have any copyright problems with printables that are free?
- Some printables may contain restrictions in their usage. Be sure to review the terms and regulations provided by the author.
-
How do I print printables for free?
- Print them at home with an printer, or go to an in-store print shop to get more high-quality prints.
-
What software do I need in order to open It Security Risk Assessment Example?
- Most printables come in PDF format. They can be opened with free software such as Adobe Reader.
Physical Security Risk Assessment Report Template 3 TEMPLATES

Cyber Security Risk Assessment Template Excel
Check more sample of It Security Risk Assessment Example below
Security Risk Assessment Template In 2020 Mission Statement Template

PHP Fusion Powered Website Articles How To Conduct A Security Risk

Information Security Risk Assessment Template Fresh 10 Sample Security

Security Risk Assessment
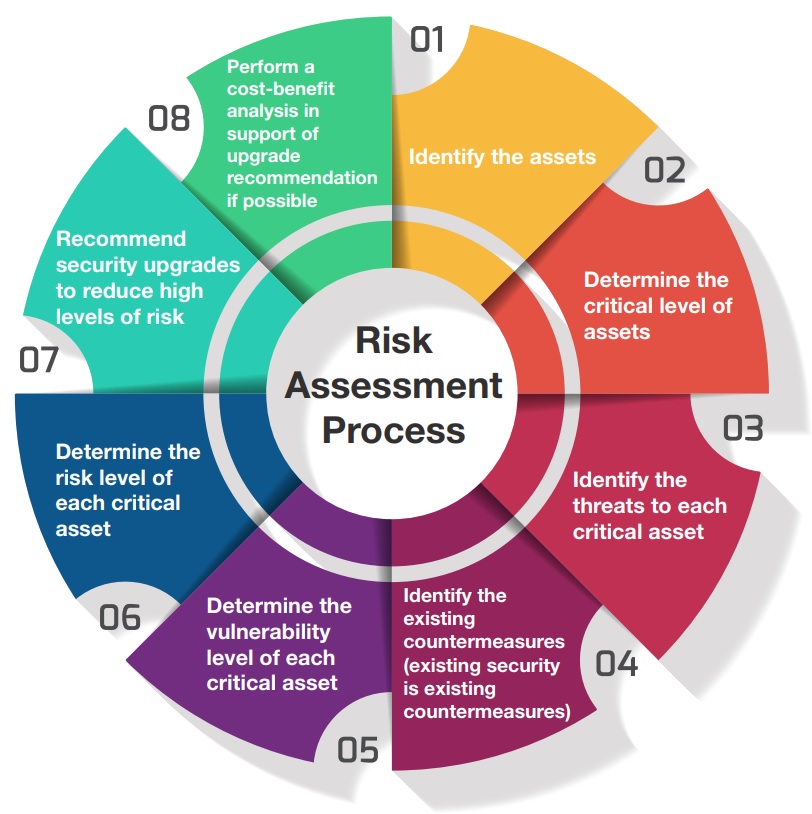
Conducting A Successful Security Risk Assessment
PHP Fusion Powered Website Articles How To Conduct A Security Risk
https://www.smartsheet.com/content/cyber-security...
In this article you ll find the most effective cybersecurity risk assessment templates for project managers security analysts security incident responders intrusion detection personnel vulnerability assessors and cryptologists

https://www.smartsheet.com/content/it-risk-templates
Try Smartsheet for Free By Kate Eby November 21 2022 We ve compiled free IT risk assessment and management templates for information security analysts network security engineers cryptographers and chief information security officers Use these templates to better assess and manage IT risks
In this article you ll find the most effective cybersecurity risk assessment templates for project managers security analysts security incident responders intrusion detection personnel vulnerability assessors and cryptologists
Try Smartsheet for Free By Kate Eby November 21 2022 We ve compiled free IT risk assessment and management templates for information security analysts network security engineers cryptographers and chief information security officers Use these templates to better assess and manage IT risks

Security Risk Assessment

PHP Fusion Powered Website Articles How To Conduct A Security Risk

Conducting A Successful Security Risk Assessment

PHP Fusion Powered Website Articles How To Conduct A Security Risk
Free 30 Nist Security Assessment Plan Template In 2020 Security

Building Security Risk Assessment Template Elegant Home Building

Building Security Risk Assessment Template Elegant Home Building

Information Security Risk Assessment Example AnahirilMccarty