In a world with screens dominating our lives but the value of tangible printed objects hasn't waned. If it's to aid in education as well as creative projects or simply adding some personal flair to your home, printables for free are now a vital source. In this article, we'll take a dive to the depths of "Cyber Security Incident Reporting Procedure," exploring their purpose, where to locate them, and how they can enhance various aspects of your lives.
Get Latest Cyber Security Incident Reporting Procedure Below
Cyber Security Incident Reporting Procedure
Cyber Security Incident Reporting Procedure - Cyber Security Incident Reporting Procedure, Cyber Security Incident Response Procedure, Information Security Incident Reporting Procedure, Cyber Security Incident Reporting Process, Cyber Security Incident Reporting Policy, Information Security Incident Response Procedure, Information Security Event Reporting Procedure, Cyber Security Incident Response Process, Cyber Security Incident Response Policy, Cyber Security Incident Response Policy Template
This guide to national cybersecurity incident reporting provides input to national cybersecurity authorities NCAs and legislative bodies as they consider implementing a range of mandates
HIPAA mandates that to meet compliance organizations have to create and maintain security incident reports and security incident logs for all security incidents that affect
Printables for free cover a broad range of downloadable, printable documents that can be downloaded online at no cost. These materials come in a variety of forms, like worksheets templates, coloring pages, and much more. The appealingness of Cyber Security Incident Reporting Procedure is in their versatility and accessibility.
More of Cyber Security Incident Reporting Procedure
Computer Incident Response Team Roles And Responsibilities
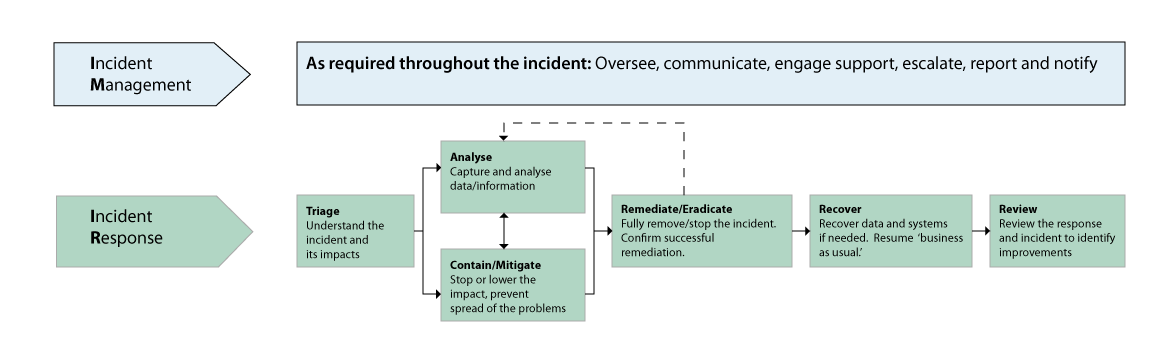
Computer Incident Response Team Roles And Responsibilities
Cyber incident reporting is the process of notifying relevant authorities about suspected or confirmed cyber threats Failure to report cyber incidents can lead to legal implications financial loss or reputational damage
Incident Reporting A cornerstone of European Union cybersecurity legislation mandatory is the reporting of cybersecurity incidents In the EU there are several different laws on incident
Printables for free have gained immense popularity due to a variety of compelling reasons:
-
Cost-Efficiency: They eliminate the need to buy physical copies or costly software.
-
customization: The Customization feature lets you tailor print-ready templates to your specific requirements such as designing invitations to organize your schedule or even decorating your house.
-
Educational Impact: Educational printables that can be downloaded for free offer a wide range of educational content for learners of all ages. This makes them a great tool for teachers and parents.
-
Convenience: Fast access a variety of designs and templates cuts down on time and efforts.
Where to Find more Cyber Security Incident Reporting Procedure
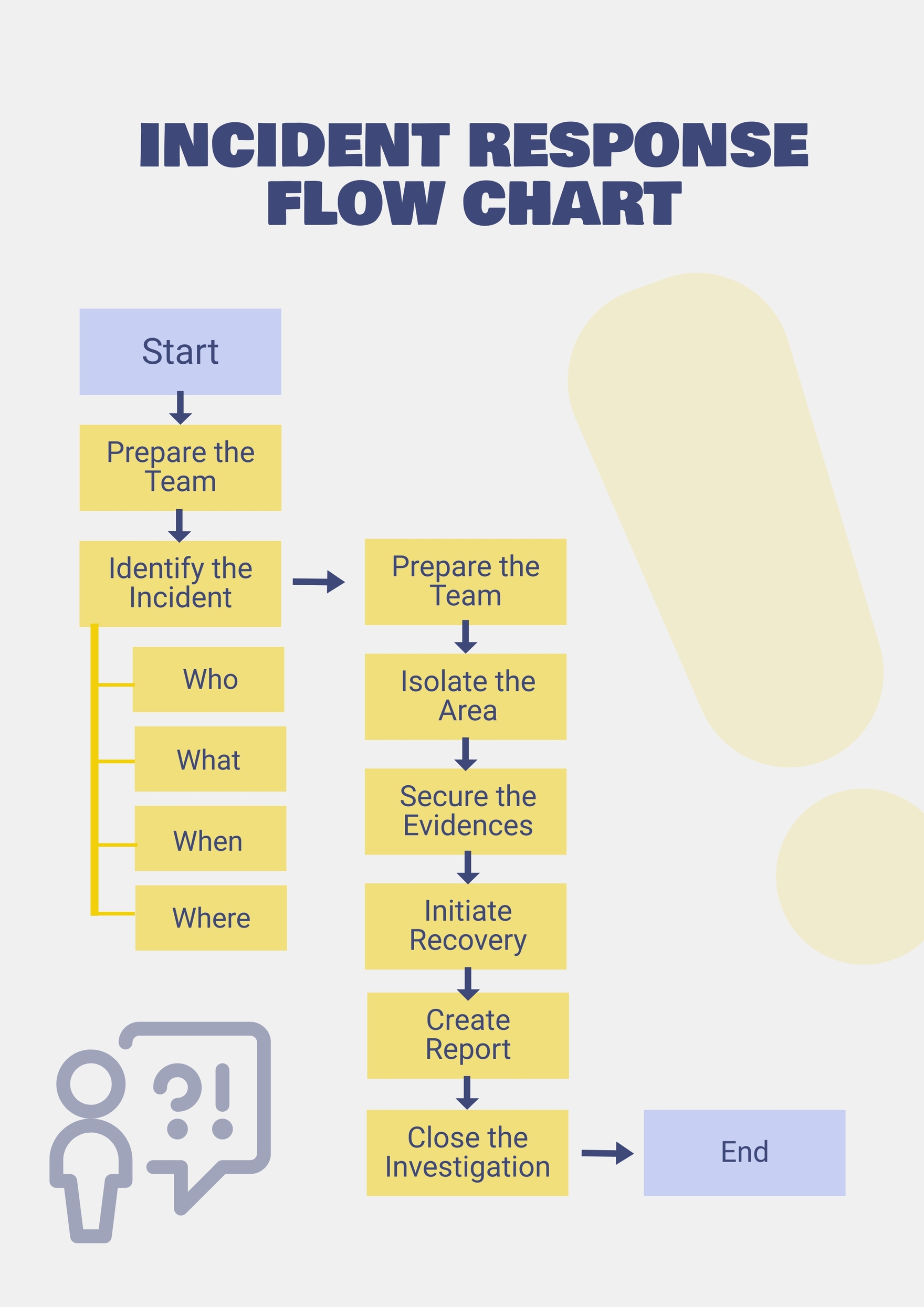
Cyber Incident Flow Chart
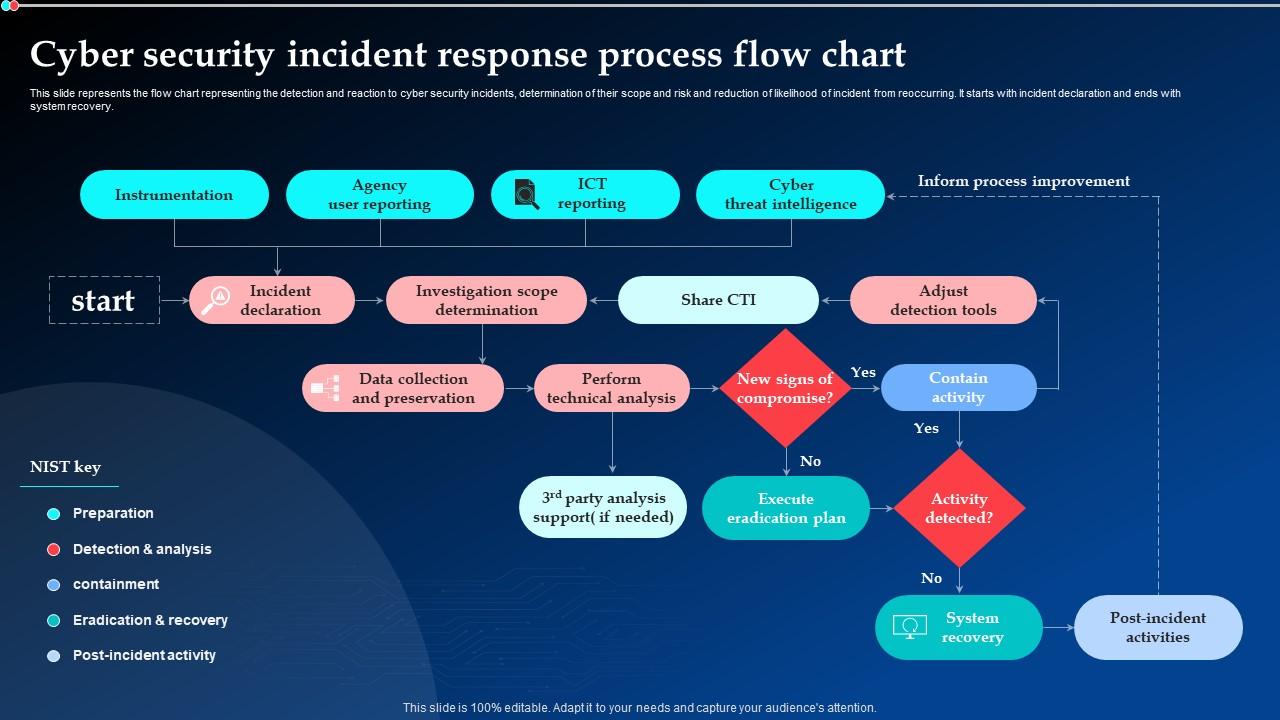
Cyber Incident Flow Chart
An incident response plan IRP is a group of policies that dictate an organizations reaction to a cyber attack Once an security breach has been identified for example by network intrusion
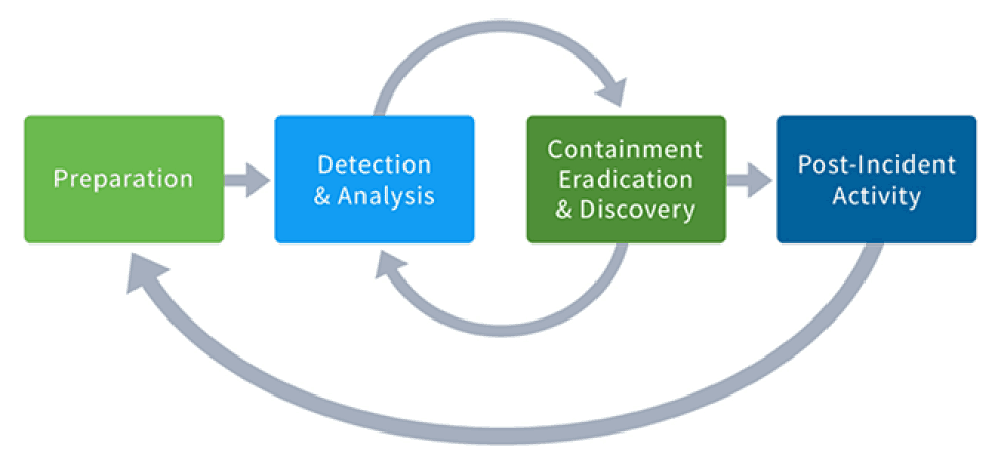
To create a cyber security incident report you can follow either the NIST or SANS framework with both generally requiring you to outline the steps for preparation detection and analysis containment eradication and
We hope we've stimulated your curiosity about Cyber Security Incident Reporting Procedure Let's look into where you can find these gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy offer an extensive collection in Cyber Security Incident Reporting Procedure for different goals.
- Explore categories such as design, home decor, management, and craft.
2. Educational Platforms
- Forums and websites for education often offer free worksheets and worksheets for printing or flashcards as well as learning materials.
- This is a great resource for parents, teachers and students looking for additional resources.
3. Creative Blogs
- Many bloggers post their original designs and templates, which are free.
- The blogs covered cover a wide selection of subjects, that range from DIY projects to party planning.
Maximizing Cyber Security Incident Reporting Procedure
Here are some ways of making the most of printables that are free:
1. Home Decor
- Print and frame gorgeous artwork, quotes and seasonal decorations, to add a touch of elegance to your living areas.
2. Education
- Print worksheets that are free for teaching at-home as well as in the class.
3. Event Planning
- Design invitations for banners, invitations and decorations for special occasions like weddings or birthdays.
4. Organization
- Get organized with printable calendars, to-do lists, and meal planners.
Conclusion
Cyber Security Incident Reporting Procedure are a treasure trove of practical and imaginative resources for a variety of needs and interests. Their accessibility and versatility make them a great addition to every aspect of your life, both professional and personal. Explore the many options that is Cyber Security Incident Reporting Procedure today, and discover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables for free really free?
- Yes they are! You can print and download these materials for free.
-
Can I use free printables to make commercial products?
- It depends on the specific conditions of use. Always review the terms of use for the creator before using any printables on commercial projects.
-
Do you have any copyright violations with Cyber Security Incident Reporting Procedure?
- Certain printables could be restricted concerning their use. Be sure to review these terms and conditions as set out by the designer.
-
How do I print Cyber Security Incident Reporting Procedure?
- Print them at home using any printer or head to an area print shop for better quality prints.
-
What program must I use to open printables for free?
- The majority of printed documents are in the format of PDF, which can be opened with free programs like Adobe Reader.
Cyber Security Incident Response Process Flow Chart Deploying Computer
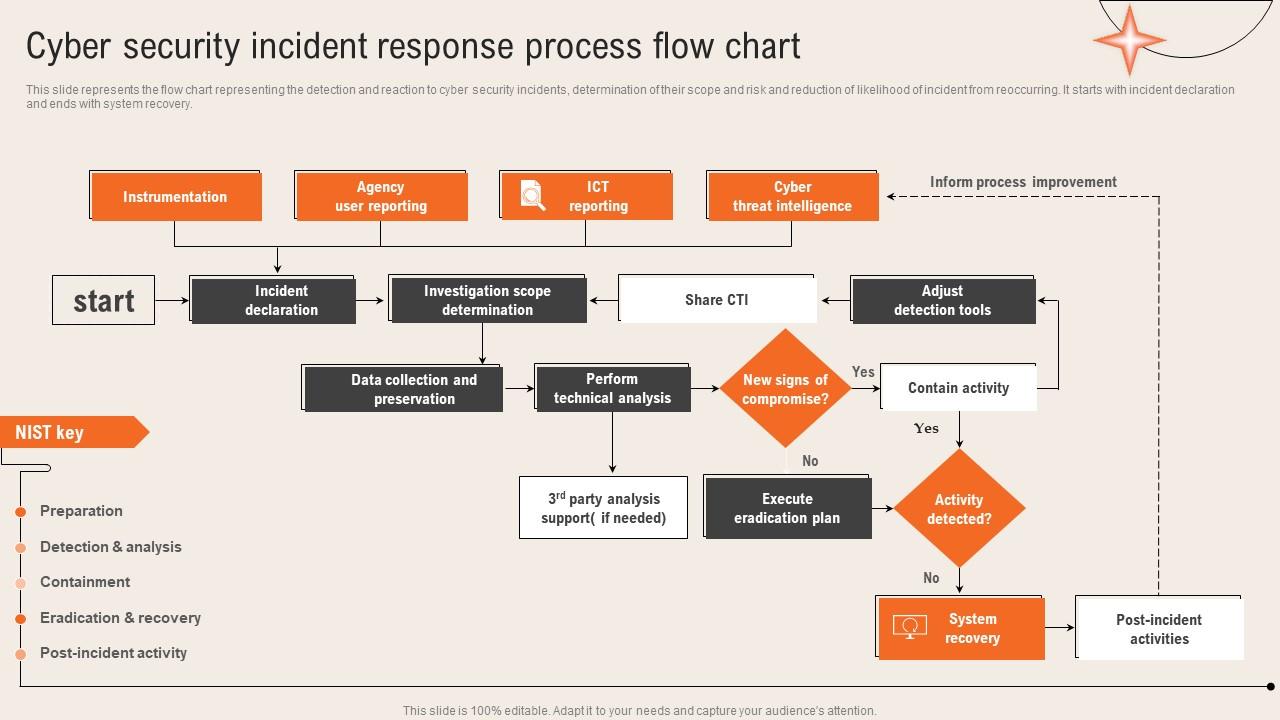
When How To Report Security Incidents ENISA
Check more sample of Cyber Security Incident Reporting Procedure below
What Step Is Part Of Reporting Of Security Incidents Josiah has Leonard
Cyber Security Incident Report How To Report And When

How To Set Up Incident Reporting 1 2
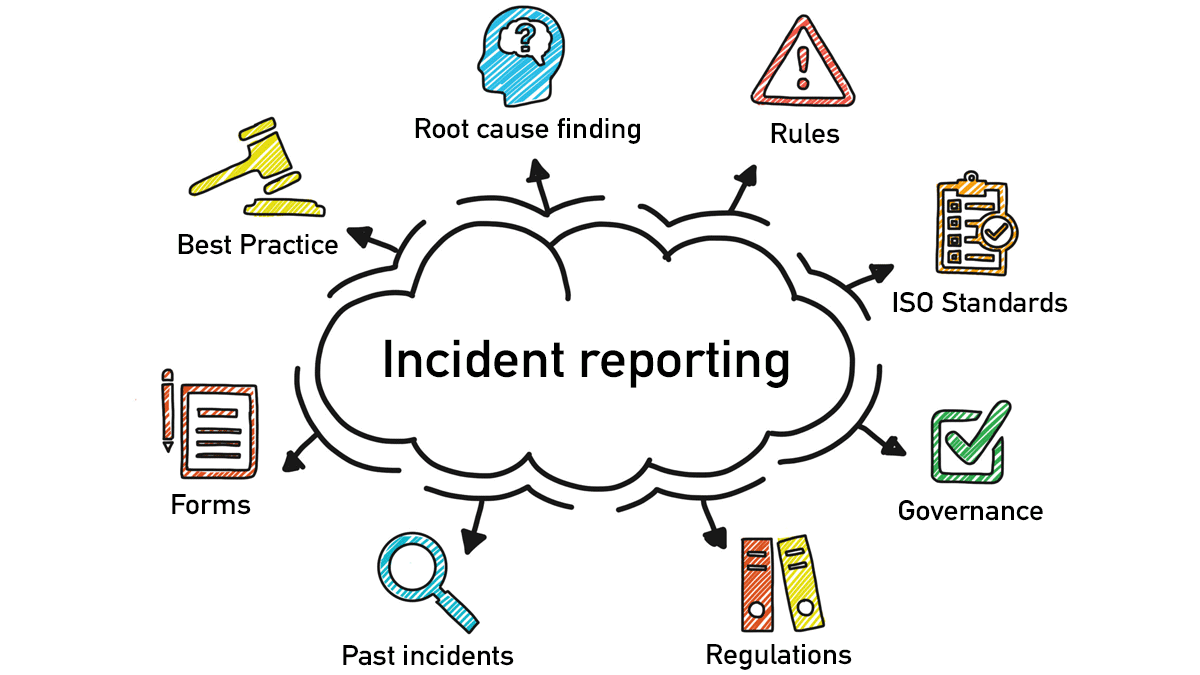
Free Cybersecurity IT Incident Report Template PDF Word EForms

Cyber Security Breach Response Plan Template
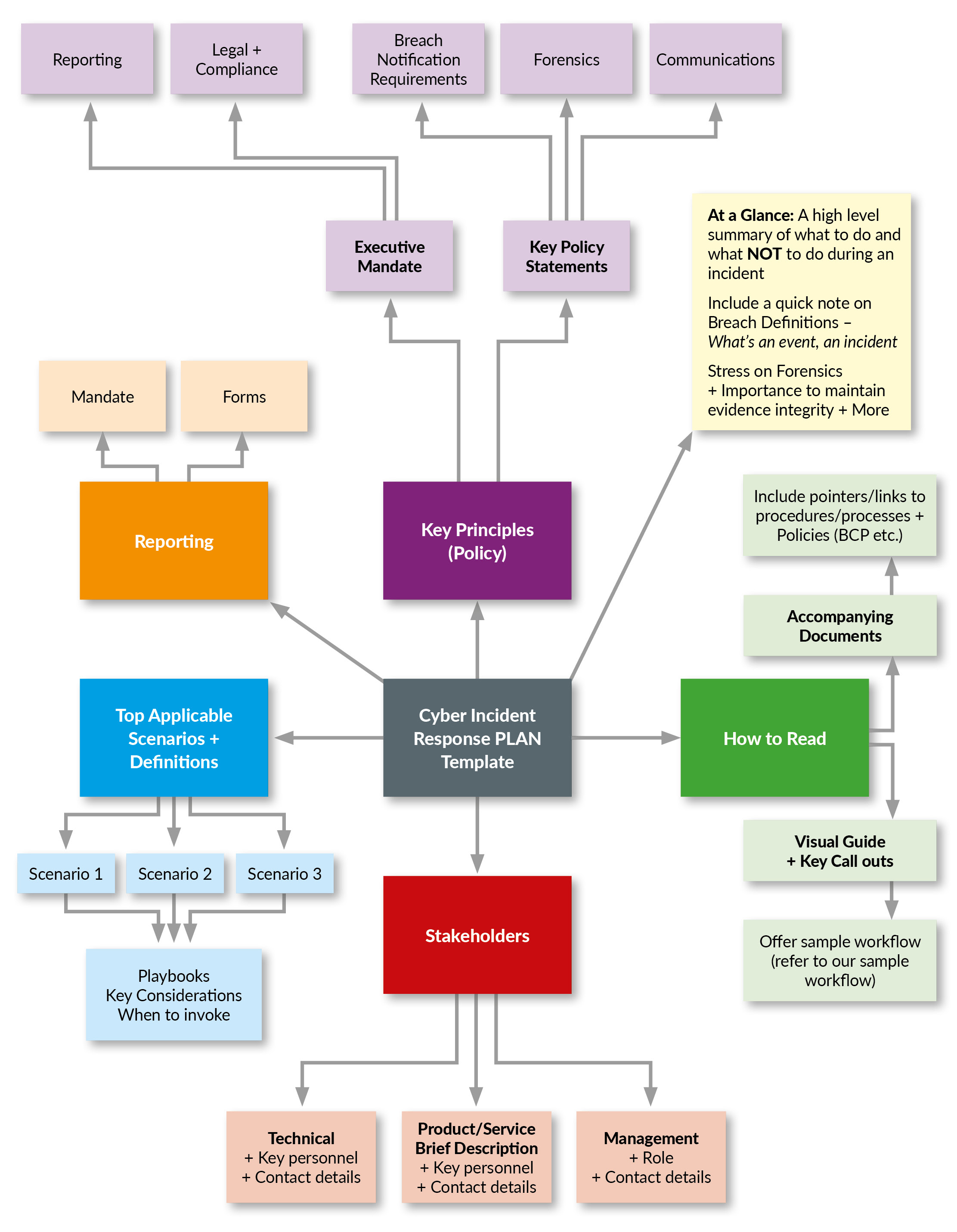
Sample Incident Response Plan Template
https://www.infosecinstitute.com/resources/...
HIPAA mandates that to meet compliance organizations have to create and maintain security incident reports and security incident logs for all security incidents that affect
https://nvlpubs.nist.gov/nistpubs/special...
This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively This revision of the publication
HIPAA mandates that to meet compliance organizations have to create and maintain security incident reports and security incident logs for all security incidents that affect
This publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively This revision of the publication

Free Cybersecurity IT Incident Report Template PDF Word EForms

Cyber Security Incident Report How To Report And When

Cyber Security Breach Response Plan Template

Sample Incident Response Plan Template
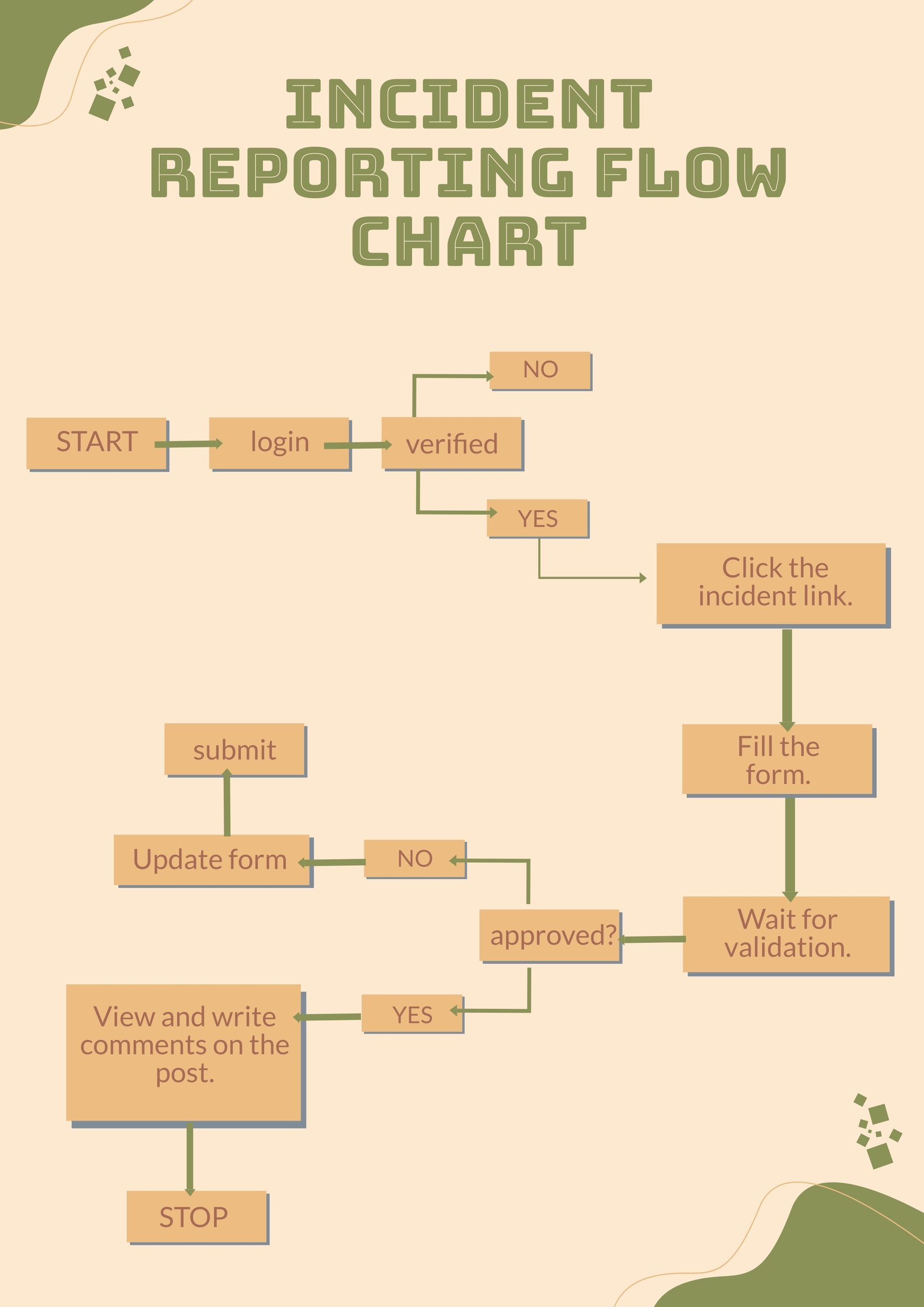
Flowchart Incident Report Process Flow Diagram Information Png The
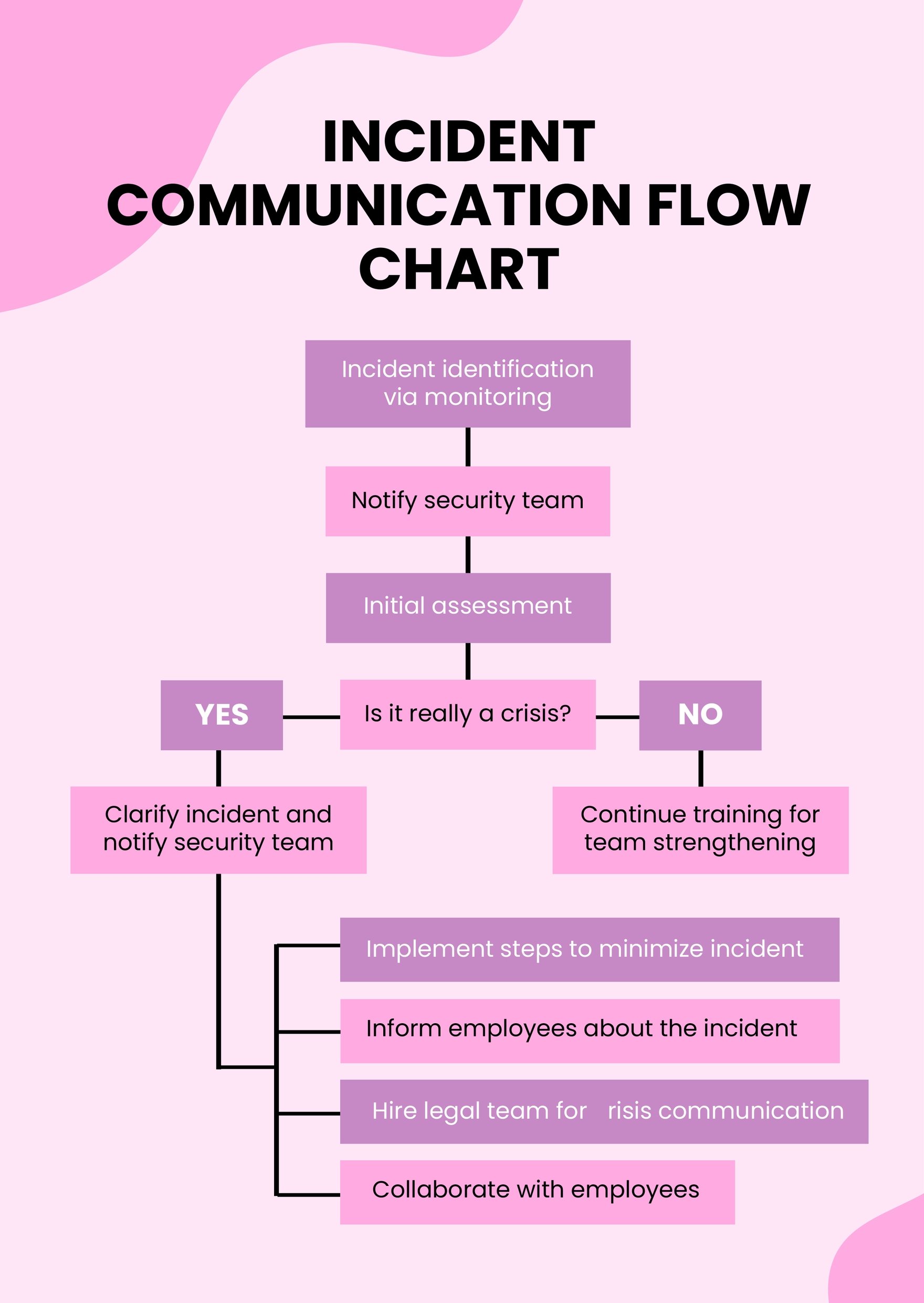
Communication Flow Chart Template

Communication Flow Chart Template

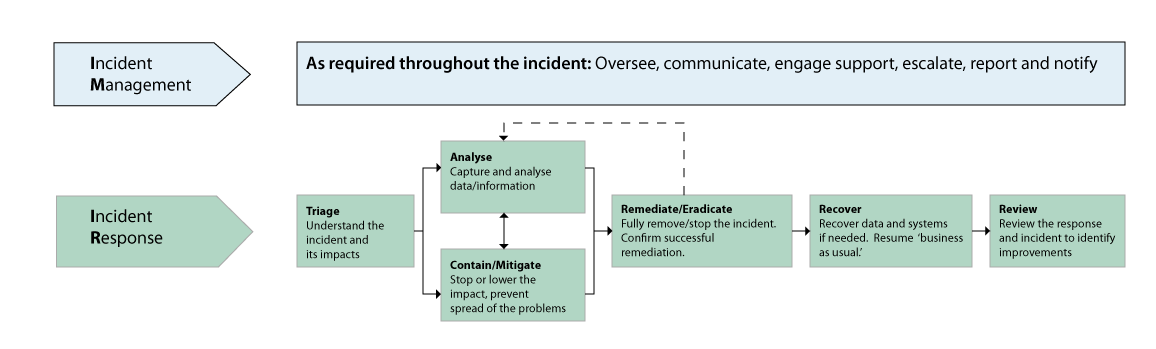
Incident Management Workflow Diagram