In this digital age, in which screens are the norm, the charm of tangible, printed materials hasn't diminished. For educational purposes and creative work, or simply adding an extra personal touch to your home, printables for free are now a vital source. The following article is a take a dive through the vast world of "Which Of These Is An Example Of An Asymmetric Encryption Algorithm," exploring their purpose, where they are, and the ways that they can benefit different aspects of your lives.
Get Latest Which Of These Is An Example Of An Asymmetric Encryption Algorithm Below

Which Of These Is An Example Of An Asymmetric Encryption Algorithm
Which Of These Is An Example Of An Asymmetric Encryption Algorithm -
These names are to be listed in the catalog 2 contents content k ntent k ntent n adj
These authors contributed to the work equllly and should be regarded as co first authors A and B are co first authors of the article or A and B contribute
The Which Of These Is An Example Of An Asymmetric Encryption Algorithm are a huge assortment of printable documents that can be downloaded online at no cost. They come in many designs, including worksheets coloring pages, templates and much more. The appealingness of Which Of These Is An Example Of An Asymmetric Encryption Algorithm is their versatility and accessibility.
More of Which Of These Is An Example Of An Asymmetric Encryption Algorithm
What Is Asymmetric Encryption Bitpanda Academy

What Is Asymmetric Encryption Bitpanda Academy
1 We tried our best to improve the manuscript and made some changes to the manuscript These changes will not influence the content and framework of the paper And here we did not
This is due to the fact that vasculature within a tumorous zone is leaky with dysfunctional lymphatic system Maeda et al 2013 Perrault and Chan 2010 therefore it allows the easy
Which Of These Is An Example Of An Asymmetric Encryption Algorithm have gained a lot of popularity due to numerous compelling reasons:
-
Cost-Efficiency: They eliminate the need to purchase physical copies or expensive software.
-
Modifications: Your HTML0 customization options allow you to customize the templates to meet your individual needs be it designing invitations making your schedule, or decorating your home.
-
Educational Value Printing educational materials for no cost offer a wide range of educational content for learners of all ages. This makes the perfect aid for parents as well as educators.
-
Accessibility: Instant access to an array of designs and templates saves time and effort.
Where to Find more Which Of These Is An Example Of An Asymmetric Encryption Algorithm
Symmetric Vs Asymmetric Encryption Differences Explained

Symmetric Vs Asymmetric Encryption Differences Explained
2011 1
We tried our best to improve the manuscript and made some changes in the manuscript These changes will not influence the content and framework of the paper And here we did not list the
After we've peaked your curiosity about Which Of These Is An Example Of An Asymmetric Encryption Algorithm Let's see where you can get these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy have a large selection of Which Of These Is An Example Of An Asymmetric Encryption Algorithm to suit a variety of goals.
- Explore categories such as home decor, education, organization, and crafts.
2. Educational Platforms
- Educational websites and forums frequently offer free worksheets and worksheets for printing or flashcards as well as learning materials.
- Perfect for teachers, parents and students in need of additional resources.
3. Creative Blogs
- Many bloggers share their imaginative designs and templates free of charge.
- These blogs cover a broad spectrum of interests, everything from DIY projects to party planning.
Maximizing Which Of These Is An Example Of An Asymmetric Encryption Algorithm
Here are some ideas of making the most use of printables that are free:
1. Home Decor
- Print and frame stunning art, quotes, or decorations for the holidays to beautify your living areas.
2. Education
- Utilize free printable worksheets to enhance your learning at home and in class.
3. Event Planning
- Design invitations, banners as well as decorations for special occasions such as weddings or birthdays.
4. Organization
- Get organized with printable calendars along with lists of tasks, and meal planners.
Conclusion
Which Of These Is An Example Of An Asymmetric Encryption Algorithm are an abundance with useful and creative ideas designed to meet a range of needs and desires. Their accessibility and versatility make them a great addition to both professional and personal life. Explore the vast array of Which Of These Is An Example Of An Asymmetric Encryption Algorithm today and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free are they free?
- Yes they are! You can print and download these documents for free.
-
Can I make use of free printables for commercial use?
- It depends on the specific conditions of use. Always read the guidelines of the creator prior to using the printables in commercial projects.
-
Do you have any copyright violations with printables that are free?
- Certain printables may be subject to restrictions regarding their use. Be sure to review the terms and conditions set forth by the author.
-
How do I print printables for free?
- You can print them at home with printing equipment or visit a local print shop to purchase superior prints.
-
What program do I need to run printables at no cost?
- Most PDF-based printables are available with PDF formats, which can be opened with free programs like Adobe Reader.
Symmetric And Asymmetric Key Encryption Explained In Plain English
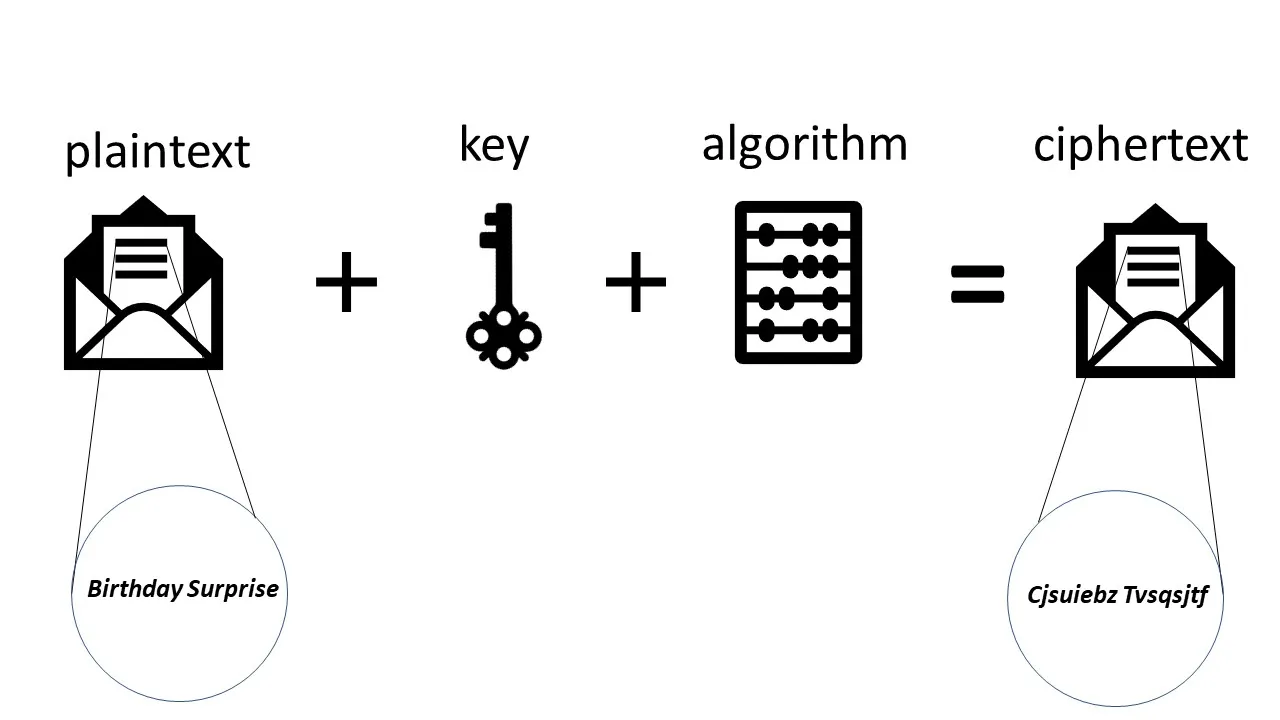
Asymmetric Encryption What It Is Why Your Security Depends On It
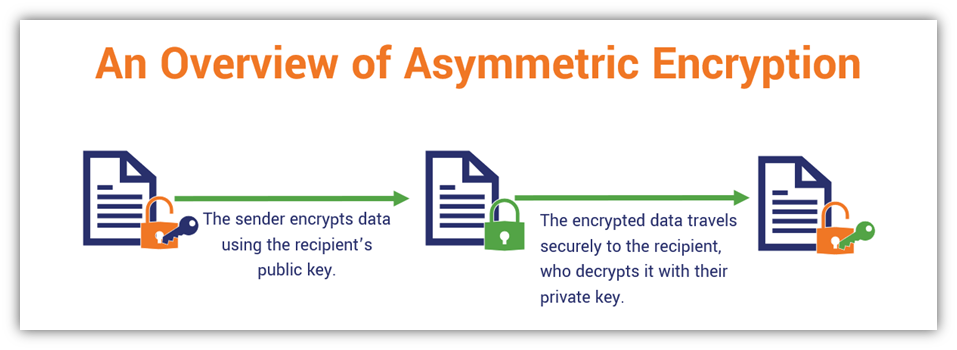
Check more sample of Which Of These Is An Example Of An Asymmetric Encryption Algorithm below
Asymmetric Encryption What It Is Why Your Security Depends On It
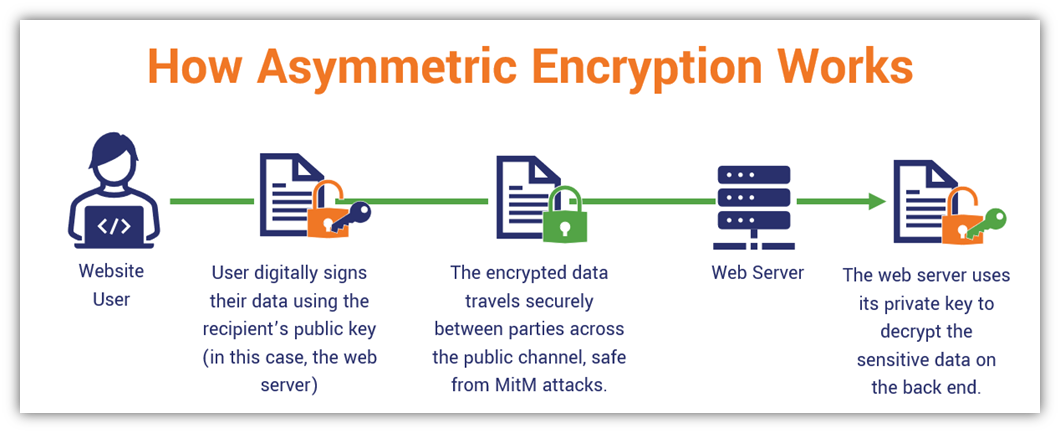
What Is Asymmetric Encryption Babypips

What Is Asymmetric Encryption

A Practical Guide To Asymmetric Encryption Part 1 Krupesh Anadkat

Asymmetric Encryption For Dummies The Signal Chief
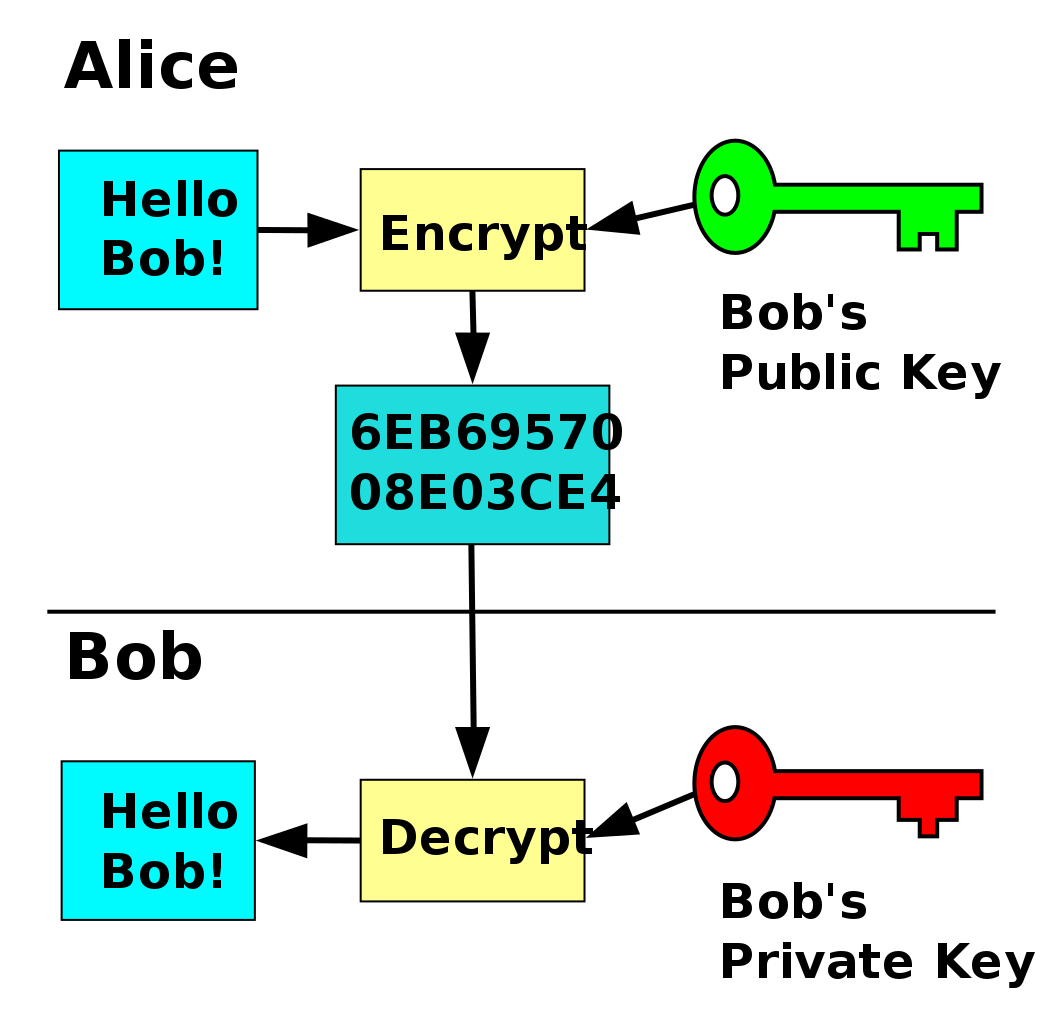
Asymmetric Encryption How Asymmetric Encryption Works


https://www.zhihu.com › question
These authors contributed to the work equllly and should be regarded as co first authors A and B are co first authors of the article or A and B contribute

These authors contributed to the work equllly and should be regarded as co first authors A and B are co first authors of the article or A and B contribute
2011 1

A Practical Guide To Asymmetric Encryption Part 1 Krupesh Anadkat

What Is Asymmetric Encryption Babypips

Asymmetric Encryption For Dummies The Signal Chief

Asymmetric Encryption How Asymmetric Encryption Works
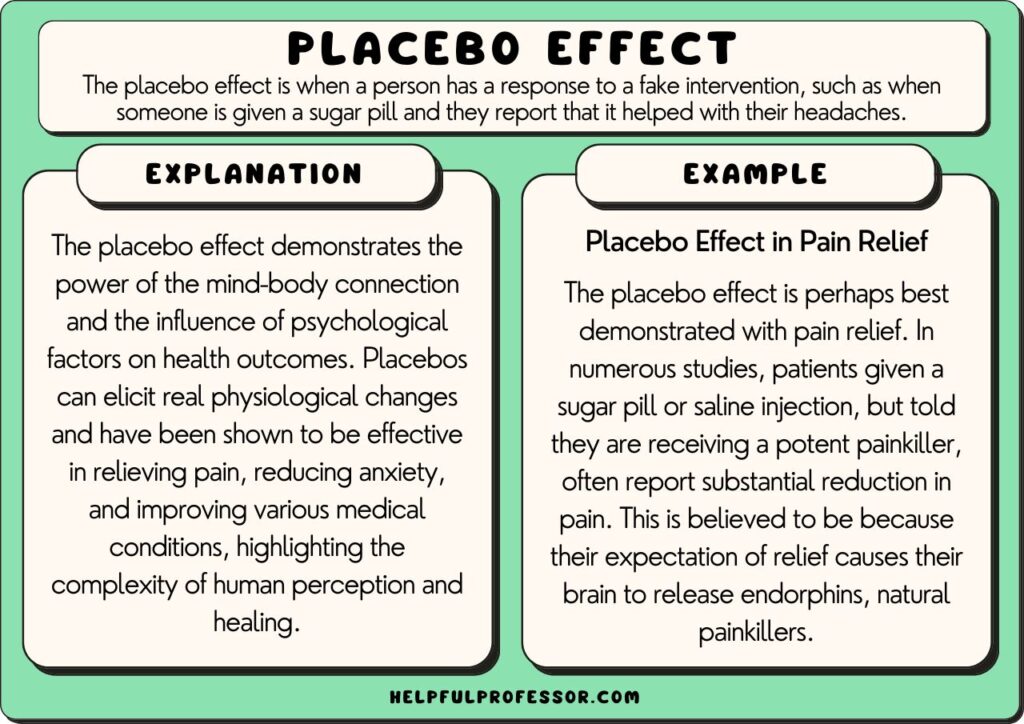
Placebo Effect Definition
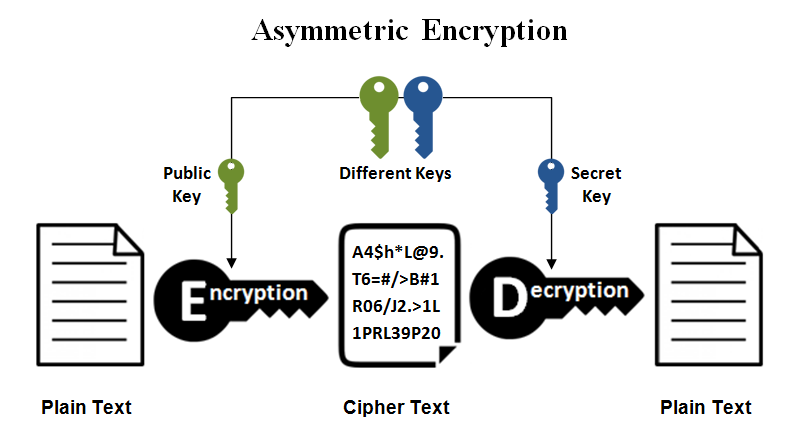
Cryptography

Cryptography

What Is Asymmetric Encryption How Does It Work InfoSec Insights