In the age of digital, where screens have become the dominant feature of our lives however, the attraction of tangible printed products hasn't decreased. Whether it's for educational purposes such as creative projects or just adding an individual touch to the space, Which Of The Following Is An Example Of Asymmetric Encryption Algorithm are now a useful source. This article will dive in the world of "Which Of The Following Is An Example Of Asymmetric Encryption Algorithm," exploring the benefits of them, where they are, and what they can do to improve different aspects of your daily life.
Get Latest Which Of The Following Is An Example Of Asymmetric Encryption Algorithm Below

Which Of The Following Is An Example Of Asymmetric Encryption Algorithm
Which Of The Following Is An Example Of Asymmetric Encryption Algorithm -
I read the following paragraph on page3 from the book The year of Billy Miller by Kevin Henkes The next thing Billy remembered was waking up in a hospital His parents whom he called
I looked up the dictionary Merriam Unabridged and it is the following the following the following one or ones used to introduce a list a quotation etc
Which Of The Following Is An Example Of Asymmetric Encryption Algorithm offer a wide variety of printable, downloadable items that are available online at no cost. These printables come in different formats, such as worksheets, templates, coloring pages and much more. The value of Which Of The Following Is An Example Of Asymmetric Encryption Algorithm is in their variety and accessibility.
More of Which Of The Following Is An Example Of Asymmetric Encryption Algorithm
Symmetric Encryption Vs Asymmetric Encryption In 2022 Encryption

Symmetric Encryption Vs Asymmetric Encryption In 2022 Encryption
When using the word which is it necessary to still use one after asking a question or do which and which one have the same meaning
The sentence you gave is talking about following your heart It is saying that your intuition rather than your rational mind will let you know when you ve found what you re
Printables that are free have gained enormous popularity because of a number of compelling causes:
-
Cost-Effective: They eliminate the necessity to purchase physical copies or costly software.
-
Flexible: Your HTML0 customization options allow you to customize printables to fit your particular needs whether it's making invitations, organizing your schedule, or even decorating your house.
-
Educational Use: Education-related printables at no charge offer a wide range of educational content for learners of all ages. This makes them a valuable device for teachers and parents.
-
Convenience: immediate access a myriad of designs as well as templates, which saves time as well as effort.
Where to Find more Which Of The Following Is An Example Of Asymmetric Encryption Algorithm
Asymmetric Encryption What It Is Why Your Security Depends On It
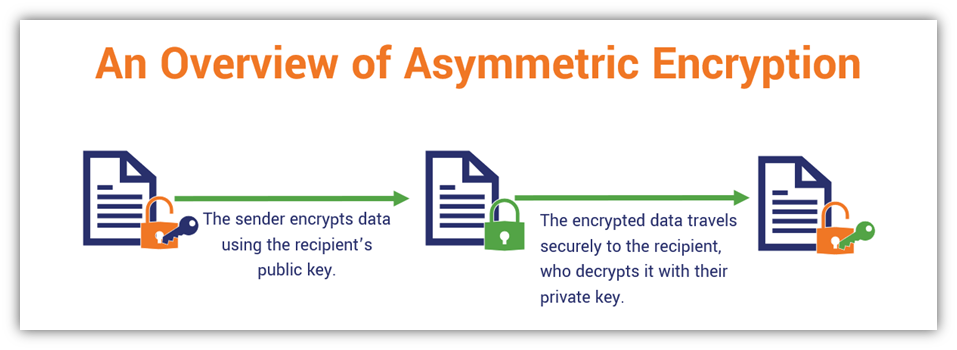
Asymmetric Encryption What It Is Why Your Security Depends On It
I m just following up on unpaid invoices and noticed that you have yet to make payment on your invoice Given that invoice is now xx days overdue you ll need to make payment within the
Not page 42 and the following The adjective following calls for a noun It looks like you re using the following to mean what follows the current point in the text or
Now that we've piqued your curiosity about Which Of The Following Is An Example Of Asymmetric Encryption Algorithm We'll take a look around to see where you can find these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide an extensive selection of Which Of The Following Is An Example Of Asymmetric Encryption Algorithm for various uses.
- Explore categories like interior decor, education, crafting, and organization.
2. Educational Platforms
- Educational websites and forums frequently provide worksheets that can be printed for free Flashcards, worksheets, and other educational materials.
- Ideal for teachers, parents and students in need of additional sources.
3. Creative Blogs
- Many bloggers share their innovative designs and templates, which are free.
- The blogs covered cover a wide spectrum of interests, ranging from DIY projects to party planning.
Maximizing Which Of The Following Is An Example Of Asymmetric Encryption Algorithm
Here are some new ways that you can make use use of printables that are free:
1. Home Decor
- Print and frame gorgeous art, quotes, or seasonal decorations that will adorn your living areas.
2. Education
- Use printable worksheets from the internet to reinforce learning at home and in class.
3. Event Planning
- Design invitations, banners and decorations for special occasions like weddings or birthdays.
4. Organization
- Be organized by using printable calendars along with lists of tasks, and meal planners.
Conclusion
Which Of The Following Is An Example Of Asymmetric Encryption Algorithm are an abundance of practical and imaginative resources for a variety of needs and preferences. Their availability and versatility make them a fantastic addition to any professional or personal life. Explore the endless world of Which Of The Following Is An Example Of Asymmetric Encryption Algorithm now and unlock new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free absolutely free?
- Yes you can! You can print and download these files for free.
-
Are there any free templates for commercial use?
- It is contingent on the specific rules of usage. Always check the creator's guidelines before utilizing their templates for commercial projects.
-
Do you have any copyright issues in printables that are free?
- Some printables could have limitations concerning their use. Check the terms and conditions provided by the author.
-
How can I print printables for free?
- Print them at home using the printer, or go to the local print shops for the highest quality prints.
-
What software must I use to open printables at no cost?
- The majority of PDF documents are provided in the PDF format, and can be opened using free software like Adobe Reader.
Asymmetric Encryption What It Is Why Your Security Depends On It
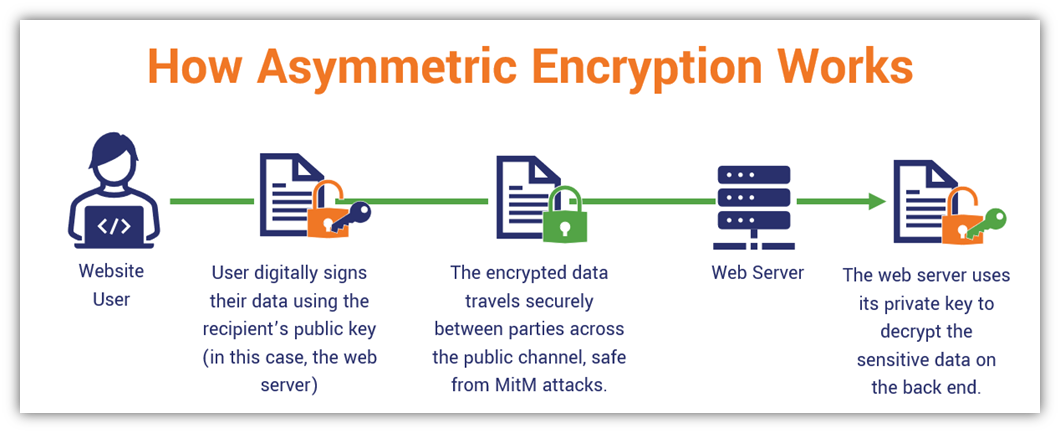
How To Decrypt Encrypted Schematic Calamity

Check more sample of Which Of The Following Is An Example Of Asymmetric Encryption Algorithm below
Symmetric And Asymmetric Key Encryption Explained In Plain English
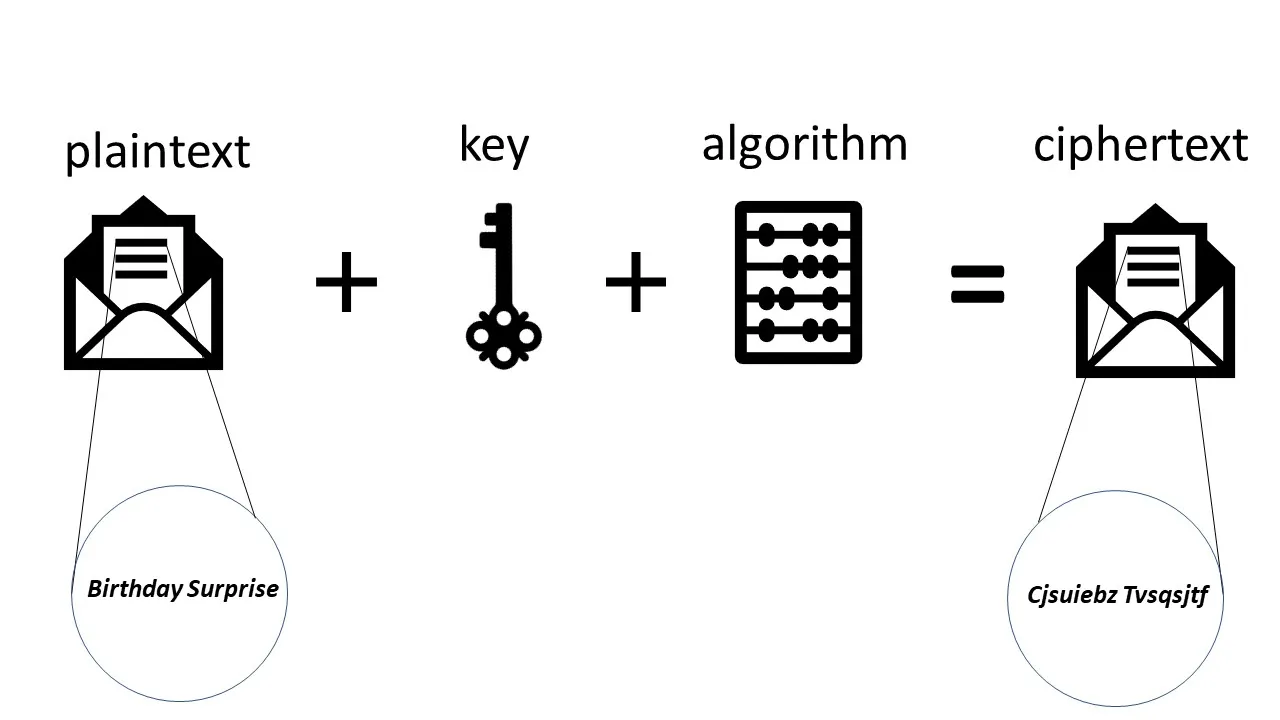
What Is Asymmetric Encryption Bitpanda Academy

What Is Asymmetric Encryption

What Is Asymmetric Encryption Its Main Principles Okta
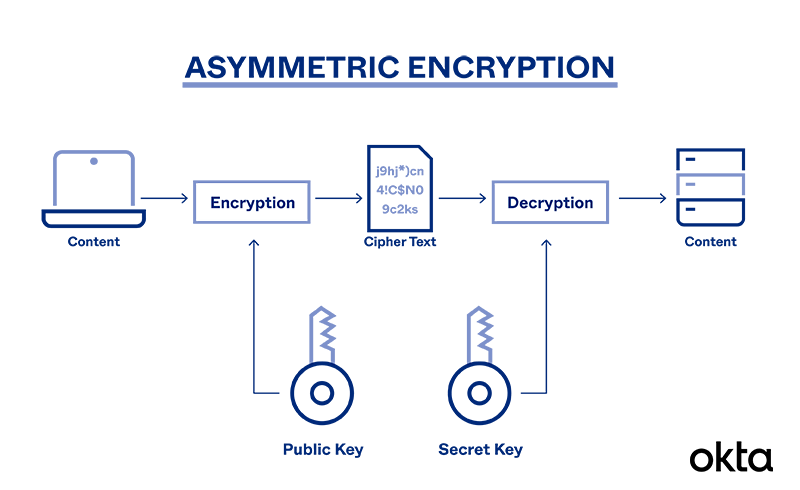
What Is Asymmetric Encryption Babypips

Asymmetric Encryption For Dummies The Signal Chief
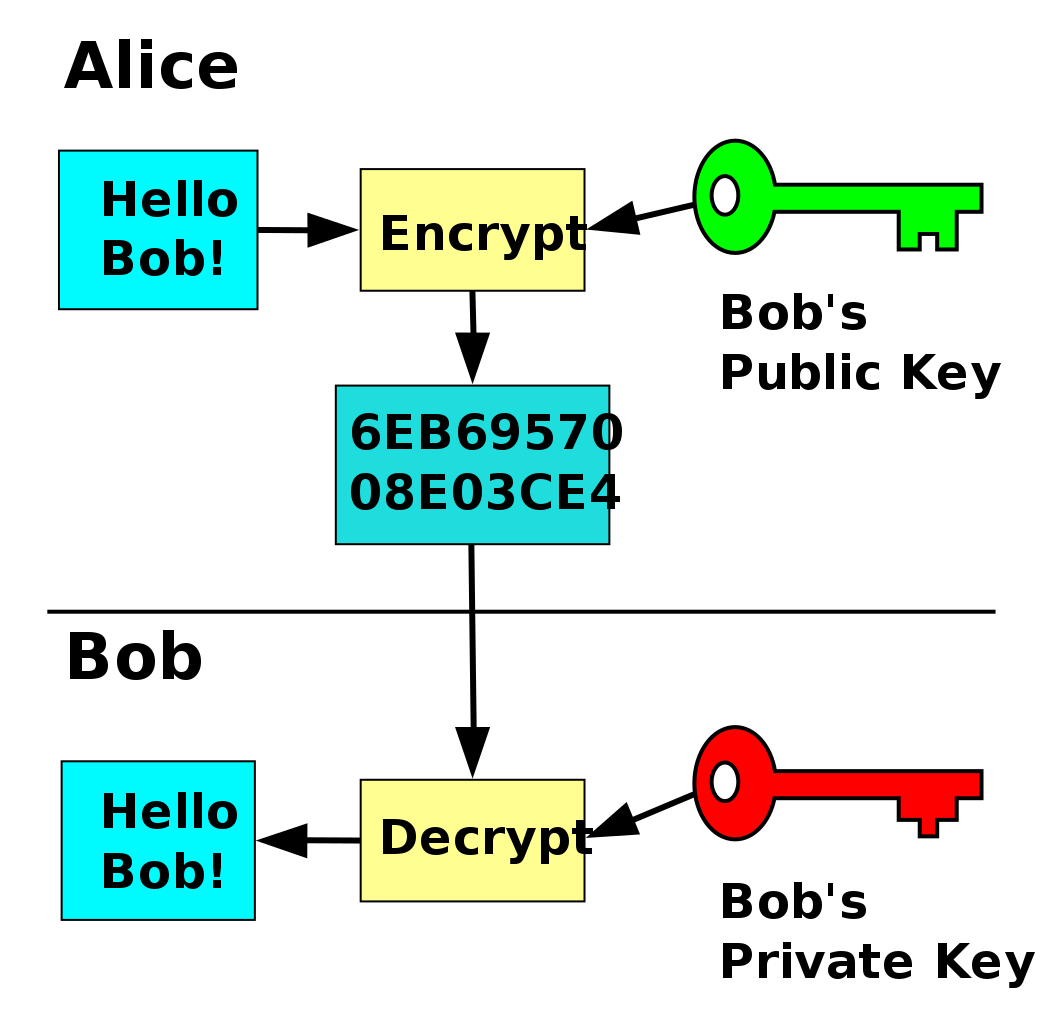
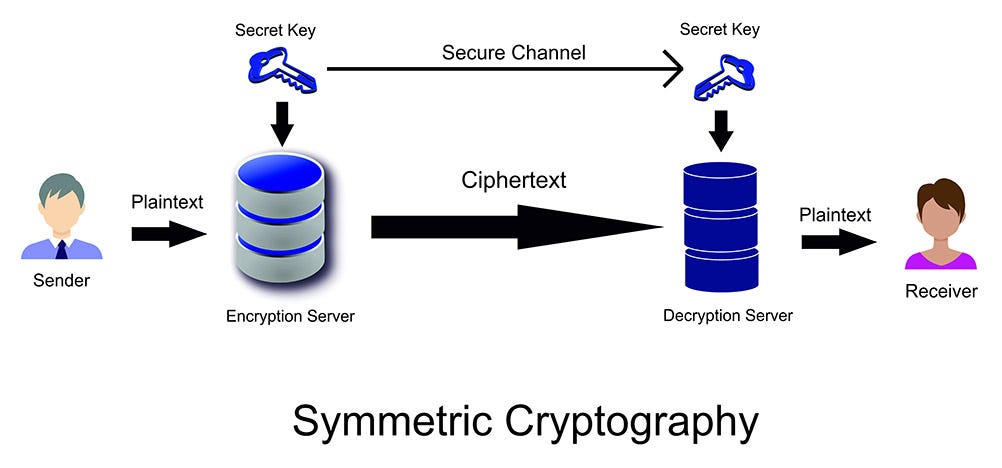
https://ell.stackexchange.com › questions
I looked up the dictionary Merriam Unabridged and it is the following the following the following one or ones used to introduce a list a quotation etc

https://ell.stackexchange.com › questions
No you don t have to say the following when you use a colon like that The following or as follows is often used for a long complex list like the one below I want to add a
I looked up the dictionary Merriam Unabridged and it is the following the following the following one or ones used to introduce a list a quotation etc
No you don t have to say the following when you use a colon like that The following or as follows is often used for a long complex list like the one below I want to add a

What Is Asymmetric Encryption Its Main Principles Okta

What Is Asymmetric Encryption Bitpanda Academy

What Is Asymmetric Encryption Babypips

Asymmetric Encryption For Dummies The Signal Chief

Asymmetric Encryption How Asymmetric Encryption Works

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

What Is Asymmetric Encryption Read Symmetric Vs Asymmetric Encryption