In a world where screens have become the dominant feature of our lives and our lives are dominated by screens, the appeal of tangible printed materials hasn't faded away. Be it for educational use for creative projects, simply adding an individual touch to the home, printables for free can be an excellent source. This article will dive to the depths of "What Uses Asymmetric Encryption," exploring the different types of printables, where they are, and how they can improve various aspects of your lives.
Get Latest What Uses Asymmetric Encryption Below

What Uses Asymmetric Encryption
What Uses Asymmetric Encryption -
In Japanese the words pronounced as and pronounced as have different meanings and uses 1 This word refers to the ridge of a roof or the highest point
all all of 4 Hinative
The What Uses Asymmetric Encryption are a huge assortment of printable items that are available online at no cost. They are available in numerous designs, including worksheets templates, coloring pages, and more. The value of What Uses Asymmetric Encryption is in their variety and accessibility.
More of What Uses Asymmetric Encryption
Symmetric Encryption IB Computer Science
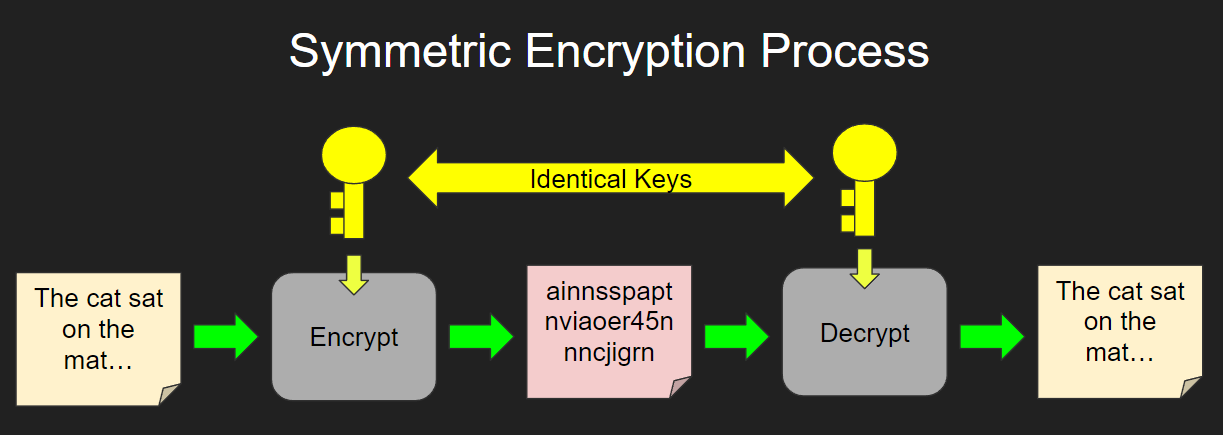
Symmetric Encryption IB Computer Science
normal sentence Teachers are at school There are teachers at school Case1 in this picture in my view image picture There are teachers
uses transitive verb
What Uses Asymmetric Encryption have gained immense popularity for several compelling reasons:
-
Cost-Efficiency: They eliminate the requirement of buying physical copies of the software or expensive hardware.
-
The ability to customize: They can make designs to suit your personal needs, whether it's designing invitations making your schedule, or even decorating your house.
-
Educational value: Free educational printables can be used by students of all ages, making them an invaluable tool for parents and educators.
-
An easy way to access HTML0: immediate access a variety of designs and templates will save you time and effort.
Where to Find more What Uses Asymmetric Encryption
Asymmetric Vs Symmetric Encryption Definitions Differences Hashed

Asymmetric Vs Symmetric Encryption Definitions Differences Hashed
Sin nimo de by by tells how something happened or what caused it to happen He was shot by the killer From indicates where something originated It came from Germany Of marks
align w be in l 2 Hinative
We've now piqued your interest in What Uses Asymmetric Encryption Let's take a look at where you can find these gems:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide a wide selection and What Uses Asymmetric Encryption for a variety motives.
- Explore categories such as the home, decor, management, and craft.
2. Educational Platforms
- Forums and websites for education often provide free printable worksheets or flashcards as well as learning materials.
- Ideal for teachers, parents as well as students searching for supplementary sources.
3. Creative Blogs
- Many bloggers share their imaginative designs as well as templates for free.
- These blogs cover a broad range of interests, ranging from DIY projects to planning a party.
Maximizing What Uses Asymmetric Encryption
Here are some fresh ways for you to get the best use of printables for free:
1. Home Decor
- Print and frame beautiful artwork, quotes or seasonal decorations that will adorn your living areas.
2. Education
- Print free worksheets to reinforce learning at home and in class.
3. Event Planning
- Design invitations, banners, as well as decorations for special occasions like weddings or birthdays.
4. Organization
- Stay organized by using printable calendars as well as to-do lists and meal planners.
Conclusion
What Uses Asymmetric Encryption are a treasure trove filled with creative and practical information which cater to a wide range of needs and preferences. Their availability and versatility make them an essential part of any professional or personal life. Explore the vast array of printables for free today and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free for free?
- Yes they are! You can print and download these free resources for no cost.
-
Do I have the right to use free printables for commercial purposes?
- It is contingent on the specific terms of use. Always read the guidelines of the creator prior to printing printables for commercial projects.
-
Are there any copyright rights issues with What Uses Asymmetric Encryption?
- Certain printables might have limitations concerning their use. Always read the terms and condition of use as provided by the creator.
-
How can I print printables for free?
- You can print them at home with printing equipment or visit a local print shop to purchase more high-quality prints.
-
What software do I require to view What Uses Asymmetric Encryption?
- A majority of printed materials are with PDF formats, which can be opened using free software like Adobe Reader.
Asymmetric Encryption Method Advantages And Disadvantages Electrodummies

What Is Asymmetric Encryption DZone

Check more sample of What Uses Asymmetric Encryption below
Asymmetric Encryption For Dummies The Signal Chief
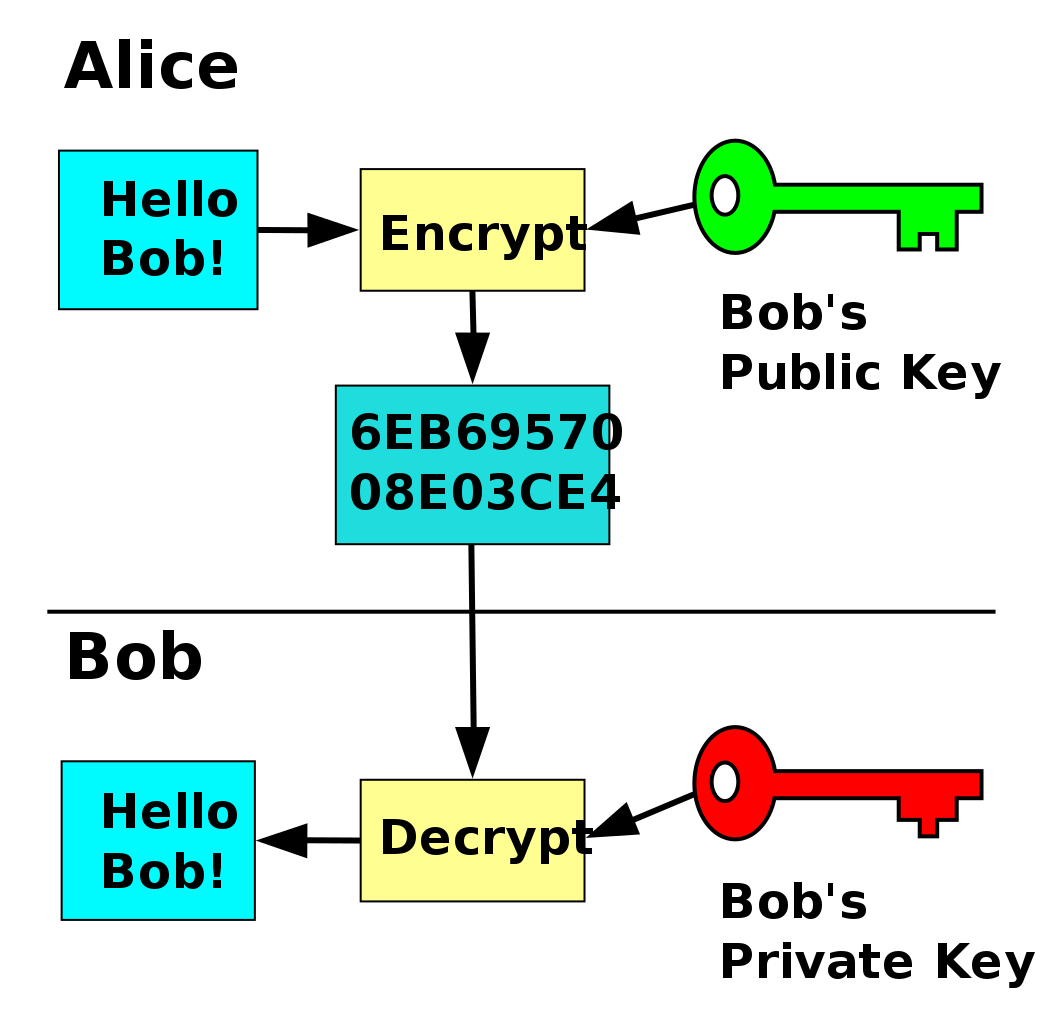
A Practical Guide To Asymmetric Encryption Part 1 Krupesh Anadkat

What Is Asymmetric Encryption And How It Works
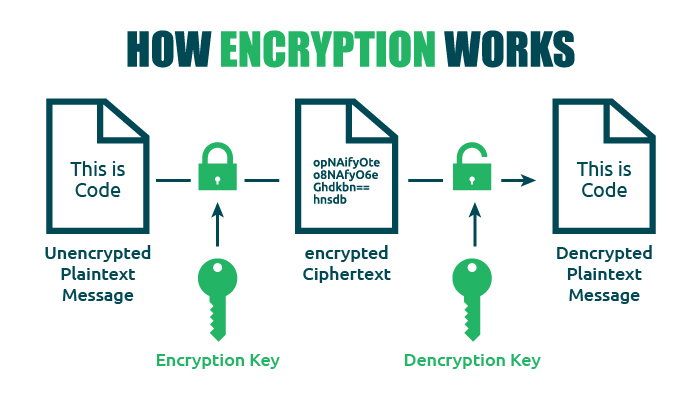
Public Key Cryptography Decoded What Is Cryptography Ntirawen

Symmetric Vs Asymmetric Encryption Differences Explained

All You Need To Know About Asymmetric Encryption

https://ja.hinative.com › questions
all all of 4 Hinative
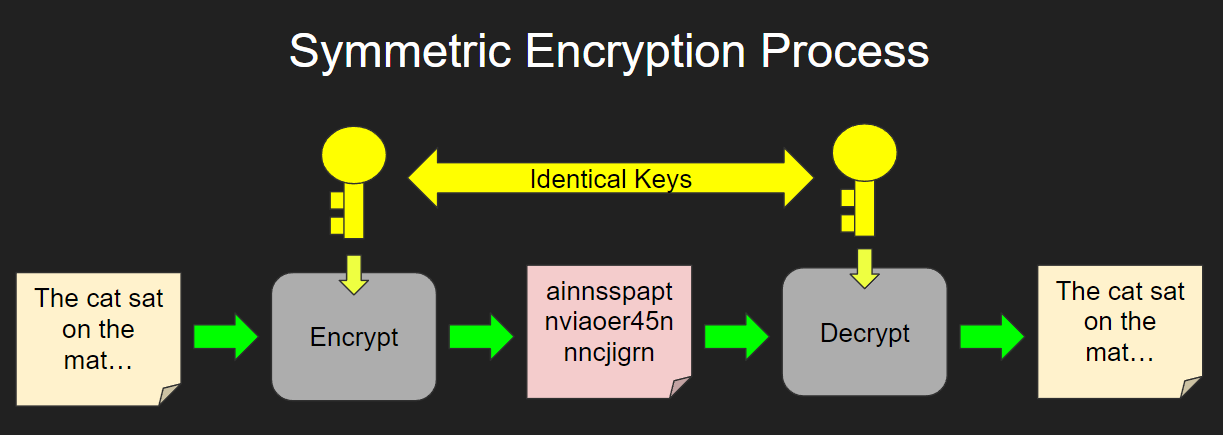
https://ja.hinative.com › questions
Anna Marie und Chris sind Geschwister Anna Marie and Chris are siblings Geschwester only works amongst sisters whereas Geschwister works with siblings of any sex On a sidenote in
all all of 4 Hinative
Anna Marie und Chris sind Geschwister Anna Marie and Chris are siblings Geschwester only works amongst sisters whereas Geschwister works with siblings of any sex On a sidenote in

Public Key Cryptography Decoded What Is Cryptography Ntirawen

A Practical Guide To Asymmetric Encryption Part 1 Krupesh Anadkat

Symmetric Vs Asymmetric Encryption Differences Explained
All You Need To Know About Asymmetric Encryption
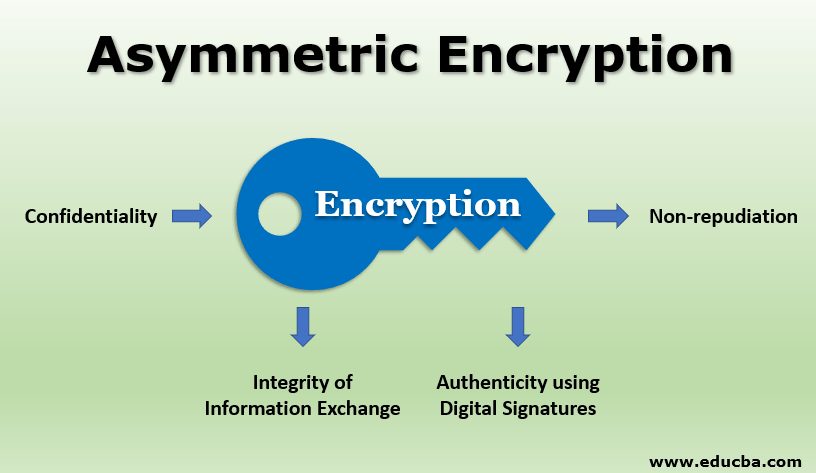
Asymmetric Encryption How Does It Work Applications And Advantages
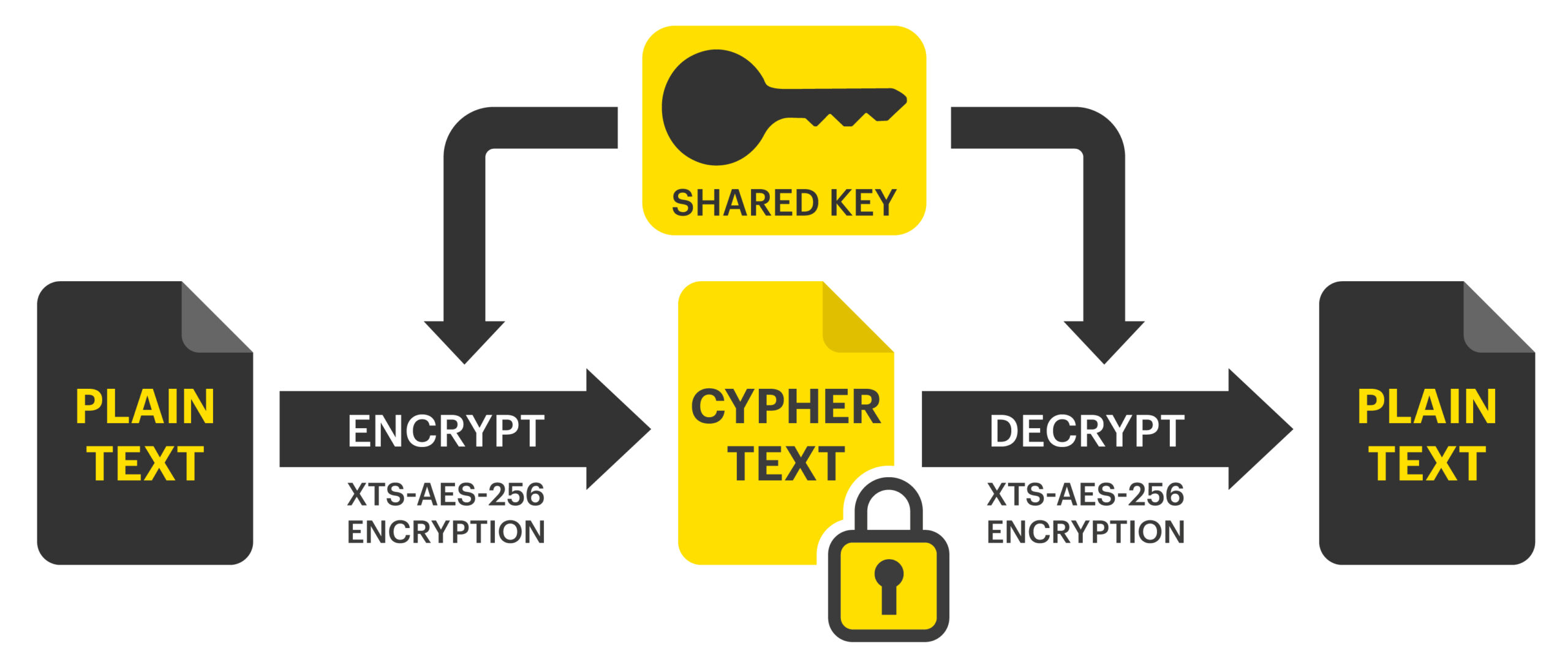
Encryption A Beginner s Guide Start Learning With StorMagic

Encryption A Beginner s Guide Start Learning With StorMagic

What Is Asymmetric Encryption How Does It Work InfoSec Insights