In this age of electronic devices, when screens dominate our lives and our lives are dominated by screens, the appeal of tangible printed materials hasn't faded away. For educational purposes or creative projects, or simply to add an individual touch to your area, What Uses Asymmetric Encryption To Digitally Sign An Executable have become an invaluable source. In this article, we'll take a dive in the world of "What Uses Asymmetric Encryption To Digitally Sign An Executable," exploring their purpose, where to find them and how they can enrich various aspects of your life.
Get Latest What Uses Asymmetric Encryption To Digitally Sign An Executable Below
What Uses Asymmetric Encryption To Digitally Sign An Executable
What Uses Asymmetric Encryption To Digitally Sign An Executable -
In Japanese the words pronounced as and pronounced as have different meanings and uses 1 This word refers to the ridge of a roof or the highest point
all all of 4 Hinative
What Uses Asymmetric Encryption To Digitally Sign An Executable cover a large array of printable documents that can be downloaded online at no cost. These resources come in many forms, including worksheets, templates, coloring pages and many more. The appealingness of What Uses Asymmetric Encryption To Digitally Sign An Executable lies in their versatility as well as accessibility.
More of What Uses Asymmetric Encryption To Digitally Sign An Executable
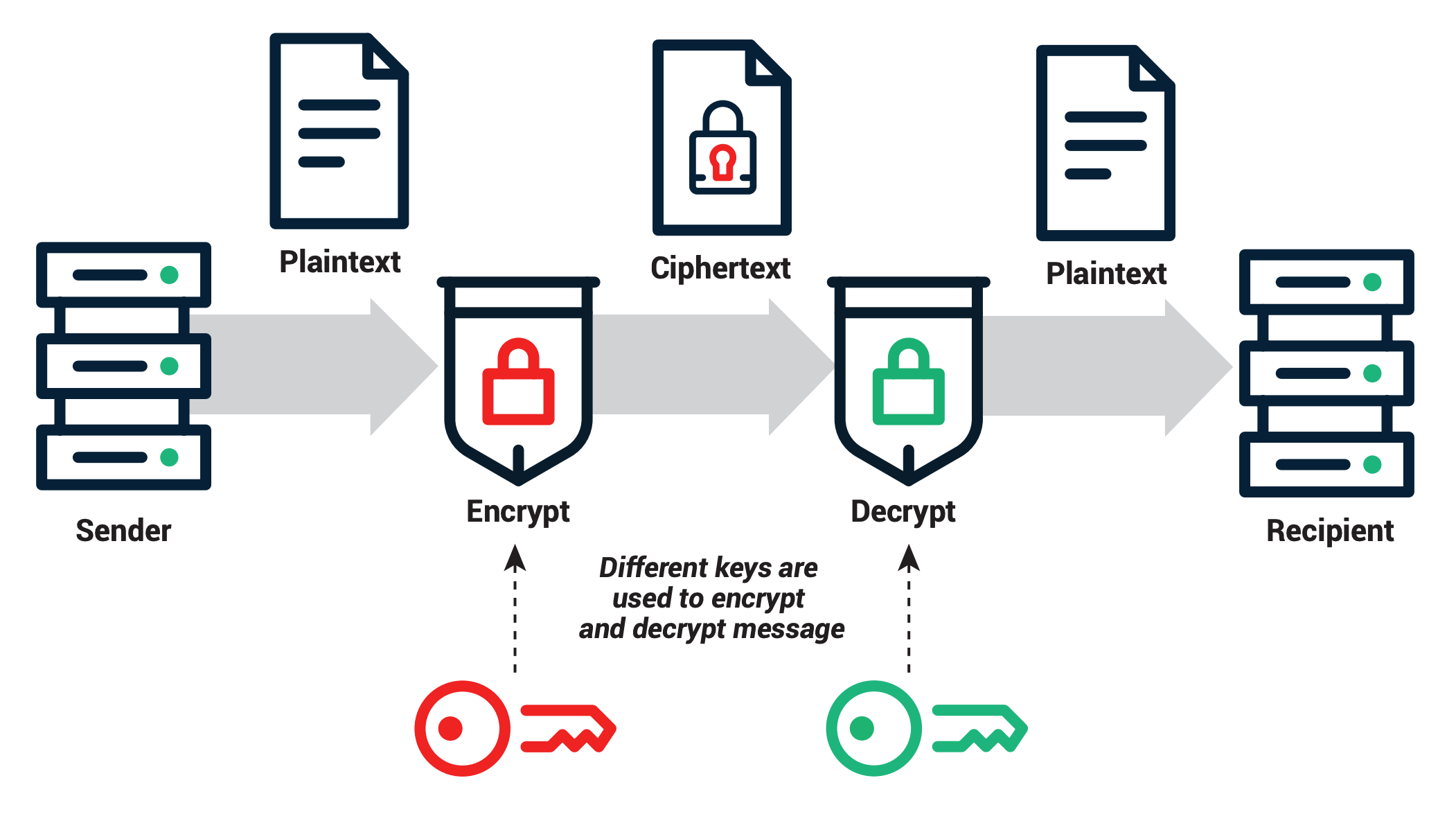
Symmetric Vs Asymmetric Encryption Differences Explained

Symmetric Vs Asymmetric Encryption Differences Explained
normal sentence Teachers are at school There are teachers at school Case1 in this picture in my view image picture There are teachers
uses transitive verb
Print-friendly freebies have gained tremendous popularity for several compelling reasons:
-
Cost-Efficiency: They eliminate the need to buy physical copies of the software or expensive hardware.
-
customization It is possible to tailor designs to suit your personal needs for invitations, whether that's creating them making your schedule, or even decorating your house.
-
Educational Use: Free educational printables can be used by students of all ages, which makes them an essential tool for parents and educators.
-
Affordability: You have instant access many designs and templates saves time and effort.
Where to Find more What Uses Asymmetric Encryption To Digitally Sign An Executable
Asymmetric Cryptography Gitcoins

Asymmetric Cryptography Gitcoins
Sin nimo de by by tells how something happened or what caused it to happen He was shot by the killer From indicates where something originated It came from Germany Of marks
align w be in l 2 Hinative
In the event that we've stirred your interest in printables for free We'll take a look around to see where you can get these hidden gems:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy have a large selection and What Uses Asymmetric Encryption To Digitally Sign An Executable for a variety motives.
- Explore categories like the home, decor, craft, and organization.
2. Educational Platforms
- Forums and educational websites often provide worksheets that can be printed for free along with flashcards, as well as other learning materials.
- This is a great resource for parents, teachers and students who are in need of supplementary resources.
3. Creative Blogs
- Many bloggers post their original designs with templates and designs for free.
- These blogs cover a broad variety of topics, starting from DIY projects to party planning.
Maximizing What Uses Asymmetric Encryption To Digitally Sign An Executable
Here are some new ways ensure you get the very most of What Uses Asymmetric Encryption To Digitally Sign An Executable:
1. Home Decor
- Print and frame beautiful artwork, quotes or decorations for the holidays to beautify your living areas.
2. Education
- Use free printable worksheets to enhance your learning at home as well as in the class.
3. Event Planning
- Create invitations, banners, as well as decorations for special occasions like weddings and birthdays.
4. Organization
- Stay organized by using printable calendars or to-do lists. meal planners.
Conclusion
What Uses Asymmetric Encryption To Digitally Sign An Executable are a treasure trove of fun and practical tools that meet a variety of needs and desires. Their access and versatility makes them a fantastic addition to your professional and personal life. Explore the vast collection of What Uses Asymmetric Encryption To Digitally Sign An Executable today to unlock new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables that are free truly gratis?
- Yes you can! You can download and print these documents for free.
-
Can I download free printables in commercial projects?
- It's all dependent on the terms of use. Be sure to read the rules of the creator prior to utilizing the templates for commercial projects.
-
Do you have any copyright problems with What Uses Asymmetric Encryption To Digitally Sign An Executable?
- Some printables could have limitations regarding their use. Be sure to read the terms of service and conditions provided by the creator.
-
How can I print What Uses Asymmetric Encryption To Digitally Sign An Executable?
- Print them at home using printing equipment or visit a local print shop for top quality prints.
-
What software do I need in order to open What Uses Asymmetric Encryption To Digitally Sign An Executable?
- The majority of printed documents are in PDF format. These can be opened with free programs like Adobe Reader.
Encryption Choices Rsa Vs Aes Explained Prey

What Is Asymmetric Encryption Babypips

Check more sample of What Uses Asymmetric Encryption To Digitally Sign An Executable below
What Is Asymmetric Encryption How Does It Work InfoSec Insights

Public Key Cryptography Decoded What Is Cryptography Ntirawen

A Practical Guide To Asymmetric Encryption Part 1 Krupesh Anadkat

We Cannot Live Without Cryptography TechSpot
10 Examples Of Asymmetric Encryption Vivid Examples
Public Key Encryption What Is Public Cryptography Okta AU NZ

https://ja.hinative.com › questions
all all of 4 Hinative

https://ja.hinative.com › questions
Anna Marie und Chris sind Geschwister Anna Marie and Chris are siblings Geschwester only works amongst sisters whereas Geschwister works with siblings of any sex On a sidenote in
all all of 4 Hinative
Anna Marie und Chris sind Geschwister Anna Marie and Chris are siblings Geschwester only works amongst sisters whereas Geschwister works with siblings of any sex On a sidenote in

We Cannot Live Without Cryptography TechSpot

Public Key Cryptography Decoded What Is Cryptography Ntirawen

10 Examples Of Asymmetric Encryption Vivid Examples

Public Key Encryption What Is Public Cryptography Okta AU NZ

What Is Asymmetric Encryption DZone

Digital Signature Cryptography Know 2 Major Forms Of Encryption

Digital Signature Cryptography Know 2 Major Forms Of Encryption
RSA Algorithm Theory And Implementation In Python AskPython