In this age of electronic devices, in which screens are the norm it's no wonder that the appeal of tangible, printed materials hasn't diminished. No matter whether it's for educational uses, creative projects, or simply adding an extra personal touch to your space, What Is Public Key Encryption In Cyber Security have proven to be a valuable source. For this piece, we'll dive to the depths of "What Is Public Key Encryption In Cyber Security," exploring what they are, how they can be found, and ways they can help you improve many aspects of your daily life.
Get Latest What Is Public Key Encryption In Cyber Security Below
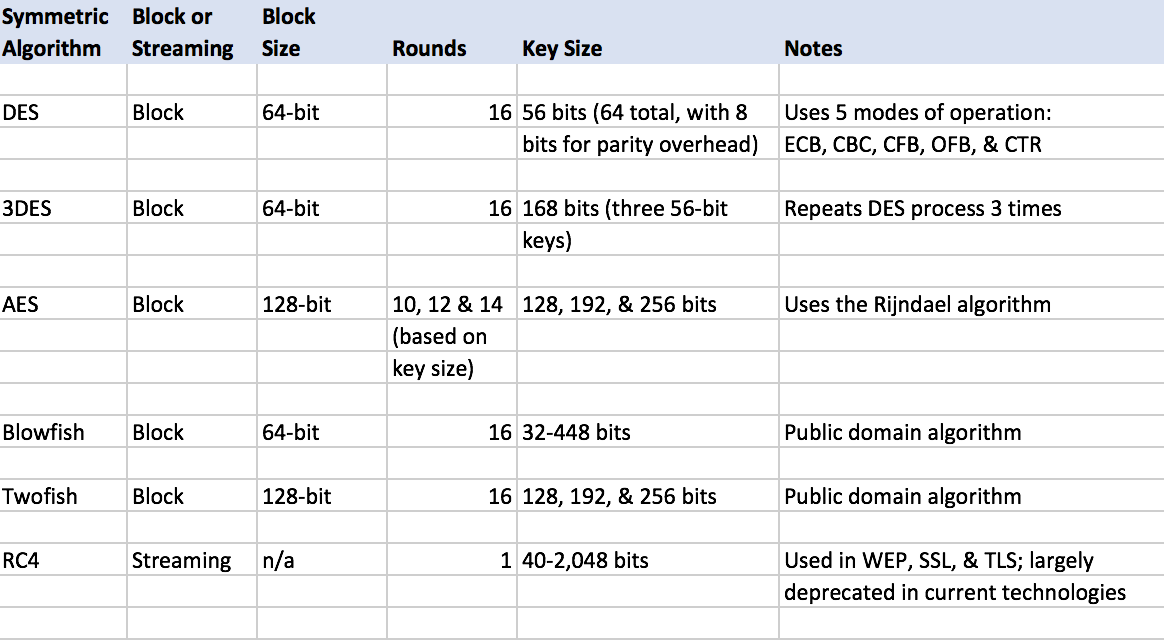
What Is Public Key Encryption In Cyber Security
What Is Public Key Encryption In Cyber Security -
Przejd do menu g wnego Przejd do tre ci Przejd do wyszukiwarki Przejd do mapy strony
Przejd do menu g wnego Przejd do tre ci Przejd do wyszukiwarki Przejd do mapy strony
What Is Public Key Encryption In Cyber Security include a broad array of printable materials online, at no cost. These printables come in different designs, including worksheets templates, coloring pages and more. The beauty of What Is Public Key Encryption In Cyber Security lies in their versatility as well as accessibility.
More of What Is Public Key Encryption In Cyber Security
DKIM Twilio

DKIM Twilio
Mo esz skontaktowa si z nami telefonicznie 609 307 182 mailowo biuro kwadraciak jaslo pl b d osobi cie w siedzibie Biura Tadeusza Ko ciuszki 13 38 200 Jas o Mo esz tak e
Dzia ka 9 5ar pod us ugi przy granicy PL UA 84 Granica Kro cienko gmina Ustrzyki Dolne powiat bieszczadzki wojew dztwo podkarpackie Polska
The What Is Public Key Encryption In Cyber Security have gained huge popularity due to several compelling reasons:
-
Cost-Effective: They eliminate the need to buy physical copies or costly software.
-
Modifications: We can customize the design to meet your needs be it designing invitations planning your schedule or even decorating your home.
-
Educational value: Printables for education that are free are designed to appeal to students from all ages, making them an invaluable instrument for parents and teachers.
-
Convenience: instant access numerous designs and templates will save you time and effort.
Where to Find more What Is Public Key Encryption In Cyber Security
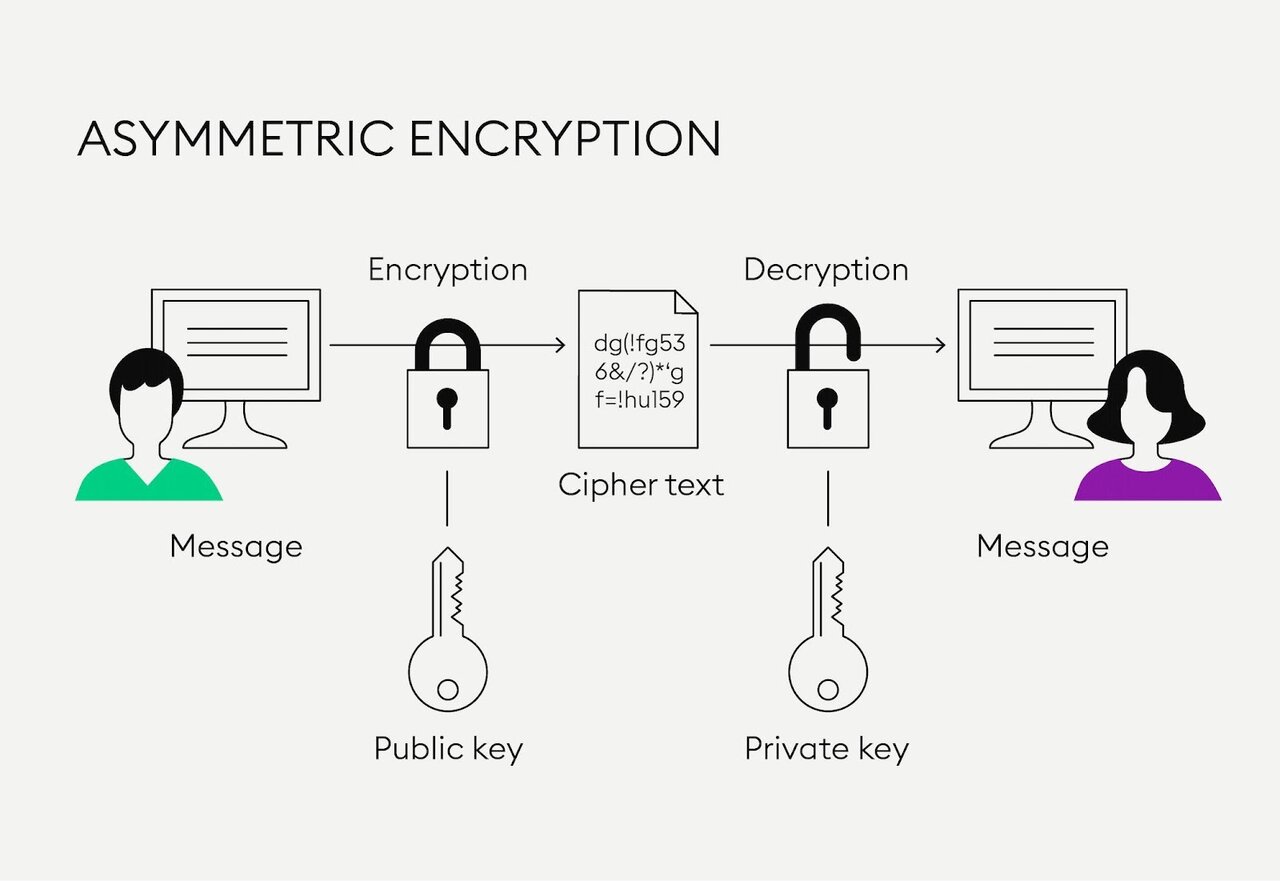
Obecnie na Pa stwowej Akademii Nauk Stosowanych w Kro nie prowadzi kursy z praktycznej znajomo ci j zyka angielskiego oraz kursy telekonferencyjne z uczelniami partnerskimi na
KPU w Kro nie Kadra wspomagaj ca proces dydaktyczny dr hab Mariola Grzebyk prof KPU
We hope we've stimulated your interest in printables for free Let's find out where you can discover these hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy offer an extensive collection of What Is Public Key Encryption In Cyber Security designed for a variety objectives.
- Explore categories such as furniture, education, crafting, and organization.
2. Educational Platforms
- Educational websites and forums typically offer free worksheets and worksheets for printing Flashcards, worksheets, and other educational tools.
- The perfect resource for parents, teachers and students in need of additional sources.
3. Creative Blogs
- Many bloggers post their original designs and templates for free.
- The blogs are a vast range of interests, that range from DIY projects to planning a party.
Maximizing What Is Public Key Encryption In Cyber Security
Here are some new ways ensure you get the very most of printables for free:
1. Home Decor
- Print and frame stunning art, quotes, or seasonal decorations that will adorn your living spaces.
2. Education
- Print out free worksheets and activities to help reinforce your learning at home either in the schoolroom or at home.
3. Event Planning
- Create invitations, banners, and decorations for special occasions such as weddings, birthdays, and other special occasions.
4. Organization
- Keep track of your schedule with printable calendars including to-do checklists, daily lists, and meal planners.
Conclusion
What Is Public Key Encryption In Cyber Security are an abundance of innovative and useful resources designed to meet a range of needs and hobbies. Their access and versatility makes these printables a useful addition to your professional and personal life. Explore the endless world of What Is Public Key Encryption In Cyber Security now and open up new possibilities!
Frequently Asked Questions (FAQs)
-
Are What Is Public Key Encryption In Cyber Security truly gratis?
- Yes you can! You can download and print these items for free.
-
Can I make use of free printables to make commercial products?
- It's all dependent on the rules of usage. Always verify the guidelines provided by the creator prior to using the printables in commercial projects.
-
Do you have any copyright violations with printables that are free?
- Some printables may come with restrictions on usage. You should read these terms and conditions as set out by the author.
-
How do I print printables for free?
- Print them at home with printing equipment or visit a local print shop for premium prints.
-
What software will I need to access printables at no cost?
- The majority are printed in the PDF format, and can be opened with free software like Adobe Reader.
Encryption And Decryption Jean s Blog

Schutz Vor Asymmetrischen Oder Symmetrischen Bedrohungen Shop

Check more sample of What Is Public Key Encryption In Cyber Security below
Public Key Encryption How Does Public Key Encryption Work
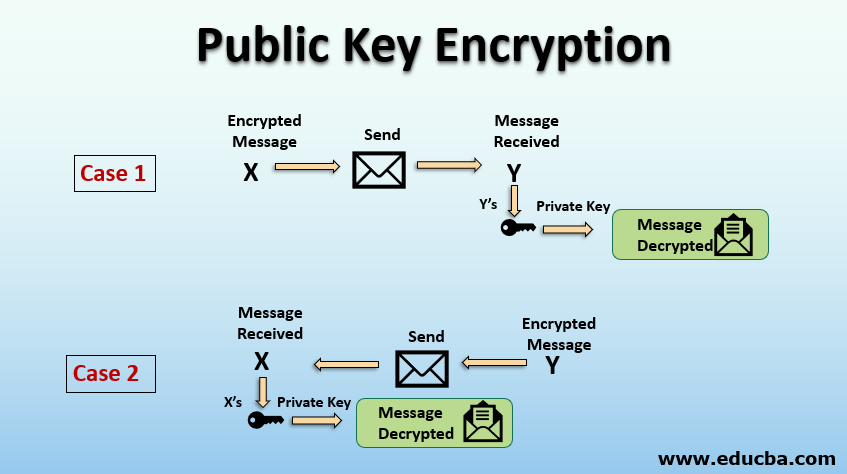
Public And Private Key Encryption System News Com
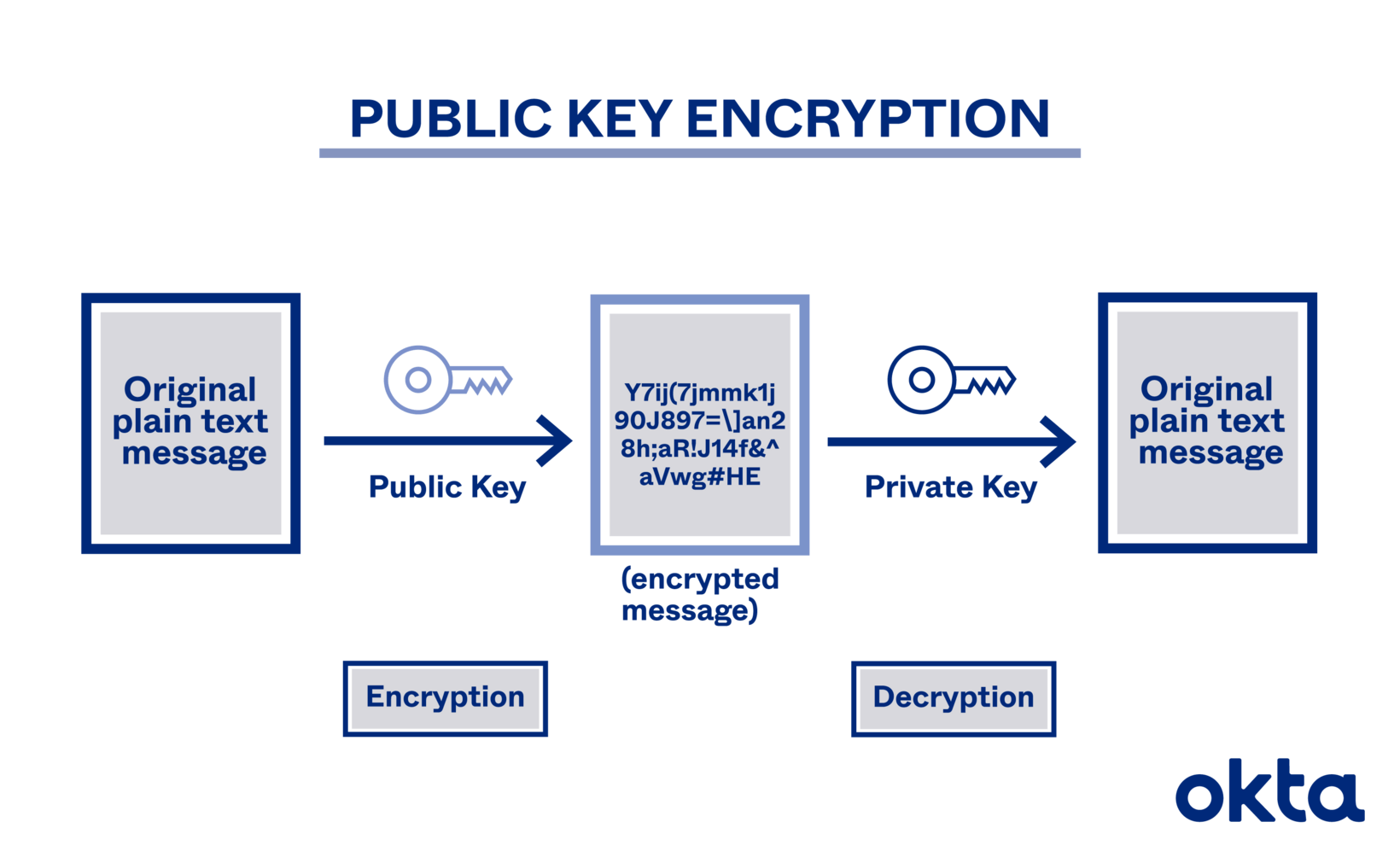
Digital Signature Cryptography Know 2 Major Forms Of Encryption

What Is The Role Of Encryption In E Commerce Explain Encryption E

Public Key Cryptography Algorithms

Public Key Cryptography Algorithms


https://www.krosno.pl › urzad-miasta
Przejd do menu g wnego Przejd do tre ci Przejd do wyszukiwarki Przejd do mapy strony

https://www.krosno.pl › dla-mieszkancow › o-miescie
Przejd do menu g wnego Przejd do tre ci Przejd do wyszukiwarki Przejd do mapy strony
Przejd do menu g wnego Przejd do tre ci Przejd do wyszukiwarki Przejd do mapy strony
Przejd do menu g wnego Przejd do tre ci Przejd do wyszukiwarki Przejd do mapy strony

What Is The Role Of Encryption In E Commerce Explain Encryption E

Public And Private Key Encryption System News Com

Public Key Cryptography Algorithms

Public Key Cryptography Algorithms

Public Key Cryptography Algorithms
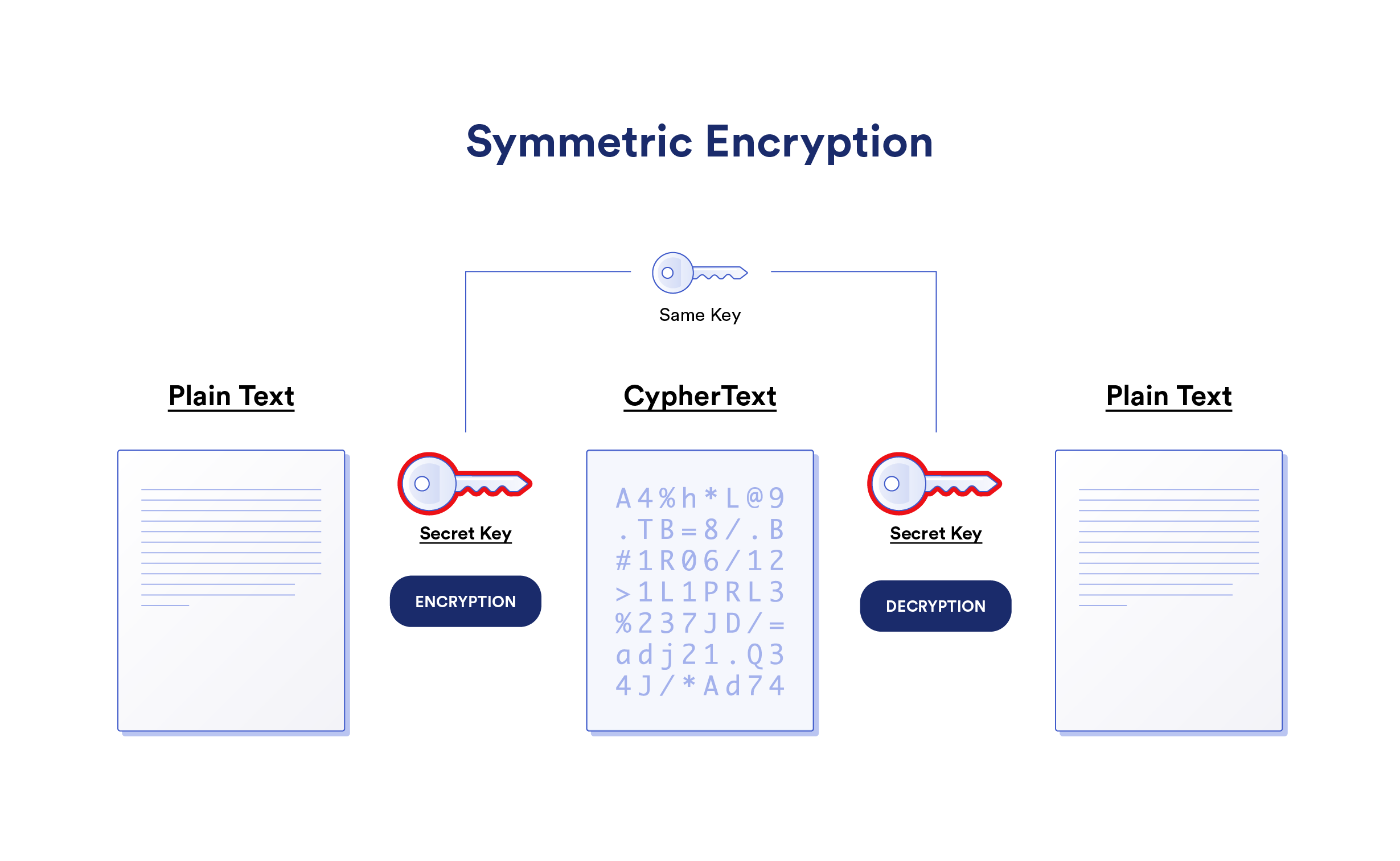
What Is Zero Knowledge Encryption Chainlink Blog

What Is Zero Knowledge Encryption Chainlink Blog

Encryption TRICKSTER