In this digital age, in which screens are the norm it's no wonder that the appeal of tangible printed products hasn't decreased. For educational purposes for creative projects, simply to add an individual touch to your space, What Is Public Key Cryptography In Cyber Security have become an invaluable resource. In this article, we'll take a dive into the world "What Is Public Key Cryptography In Cyber Security," exploring the different types of printables, where they are, and what they can do to improve different aspects of your lives.
Get Latest What Is Public Key Cryptography In Cyber Security Below

What Is Public Key Cryptography In Cyber Security
What Is Public Key Cryptography In Cyber Security -
Public Public
Public
Printables for free cover a broad range of downloadable, printable content that can be downloaded from the internet at no cost. They come in many forms, including worksheets, templates, coloring pages and much more. The benefit of What Is Public Key Cryptography In Cyber Security is their flexibility and accessibility.
More of What Is Public Key Cryptography In Cyber Security
Java
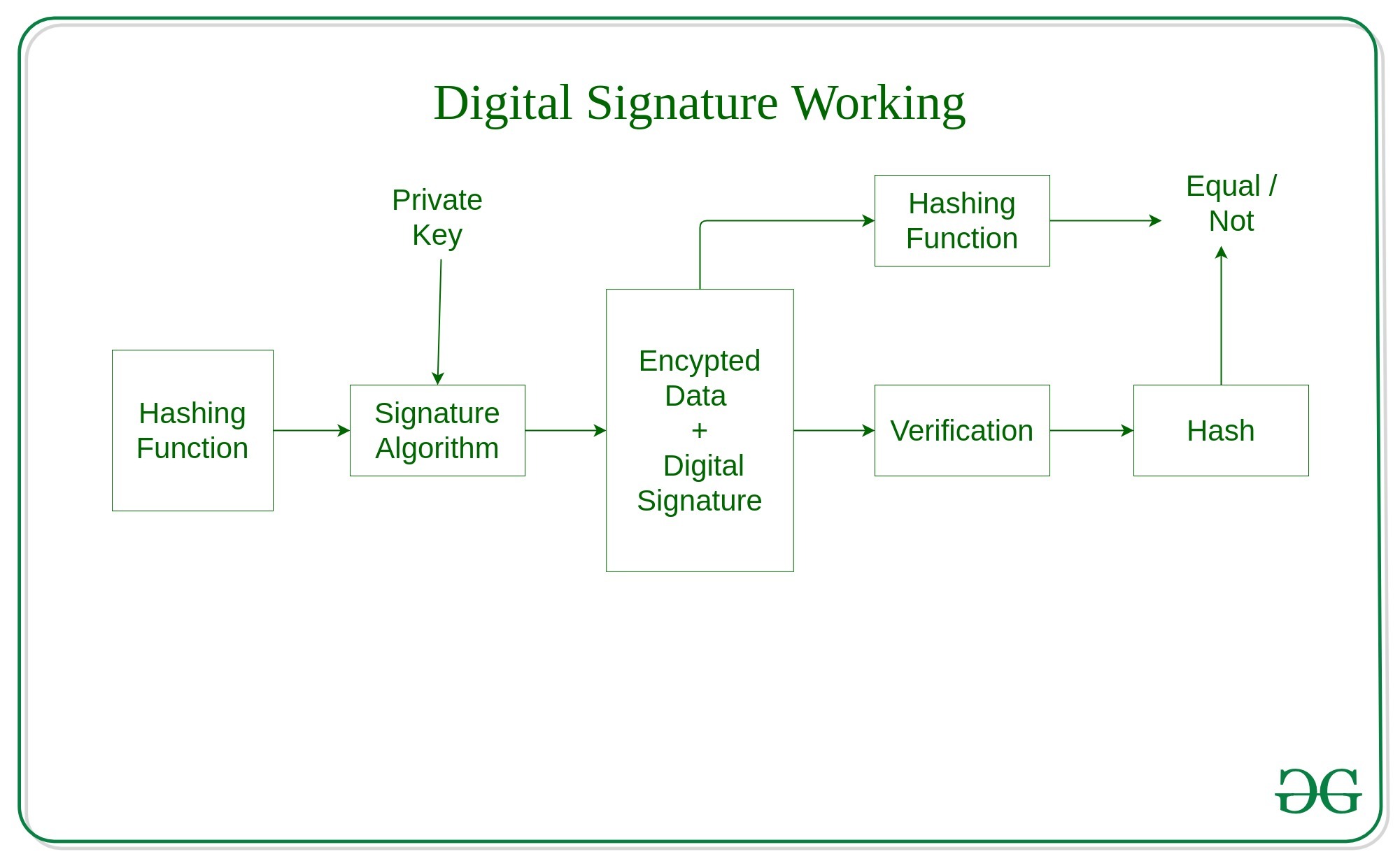
Java
Public smartphone To Public smartphones
iPhone 13 iPhone 13 Pro iPhone 13 Pro Max Public iPhone 13
Print-friendly freebies have gained tremendous recognition for a variety of compelling motives:
-
Cost-Effective: They eliminate the requirement to purchase physical copies or costly software.
-
Individualization The Customization feature lets you tailor printed materials to meet your requirements whether you're designing invitations for your guests, organizing your schedule or decorating your home.
-
Educational Worth: These What Is Public Key Cryptography In Cyber Security provide for students from all ages, making them a vital source for educators and parents.
-
Simple: Quick access to the vast array of design and templates cuts down on time and efforts.
Where to Find more What Is Public Key Cryptography In Cyber Security
Public And Private Key Encryption System News Com
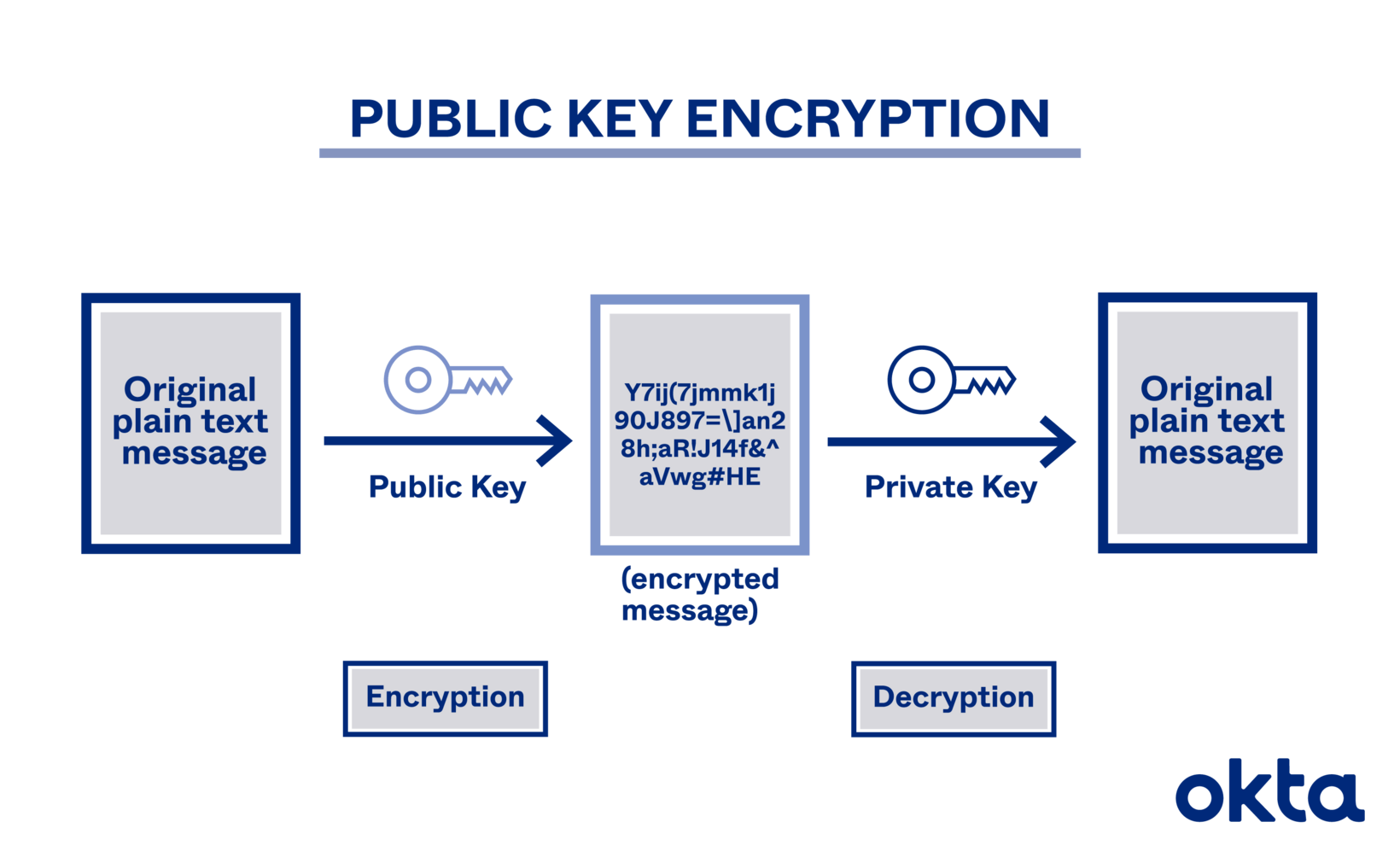
Public And Private Key Encryption System News Com
Public In Over On ear headphones headsets bluetooth gaming B iLuv
inverter air condition inverter air
If we've already piqued your curiosity about What Is Public Key Cryptography In Cyber Security We'll take a look around to see where you can find these hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a wide selection of What Is Public Key Cryptography In Cyber Security designed for a variety goals.
- Explore categories such as decoration for your home, education, management, and craft.
2. Educational Platforms
- Educational websites and forums typically offer worksheets with printables that are free along with flashcards, as well as other learning materials.
- The perfect resource for parents, teachers and students looking for extra resources.
3. Creative Blogs
- Many bloggers are willing to share their original designs and templates, which are free.
- The blogs covered cover a wide range of interests, starting from DIY projects to party planning.
Maximizing What Is Public Key Cryptography In Cyber Security
Here are some creative ways in order to maximize the use of printables that are free:
1. Home Decor
- Print and frame gorgeous artwork, quotes as well as seasonal decorations, to embellish your living spaces.
2. Education
- Use printable worksheets for free to aid in learning at your home as well as in the class.
3. Event Planning
- Design invitations for banners, invitations and other decorations for special occasions like weddings or birthdays.
4. Organization
- Keep your calendars organized by printing printable calendars with to-do lists, planners, and meal planners.
Conclusion
What Is Public Key Cryptography In Cyber Security are a treasure trove of practical and innovative resources that satisfy a wide range of requirements and desires. Their access and versatility makes them a great addition to your professional and personal life. Explore the vast world of printables for free today and discover new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free are they free?
- Yes, they are! You can download and print these tools for free.
-
Do I have the right to use free printables for commercial uses?
- It's based on the terms of use. Make sure you read the guidelines for the creator prior to printing printables for commercial projects.
-
Are there any copyright issues when you download What Is Public Key Cryptography In Cyber Security?
- Some printables may contain restrictions in their usage. Always read the terms and condition of use as provided by the author.
-
How can I print printables for free?
- You can print them at home with either a printer at home or in a print shop in your area for higher quality prints.
-
What software is required to open printables that are free?
- The majority are printed in the format of PDF, which can be opened using free software like Adobe Reader.
Digital Signature Cryptography Know 2 Major Forms Of Encryption

Public Key Cryptography Algorithms

Check more sample of What Is Public Key Cryptography In Cyber Security below
Public Key Cryptography Algorithms

What Is Public Key Cryptography
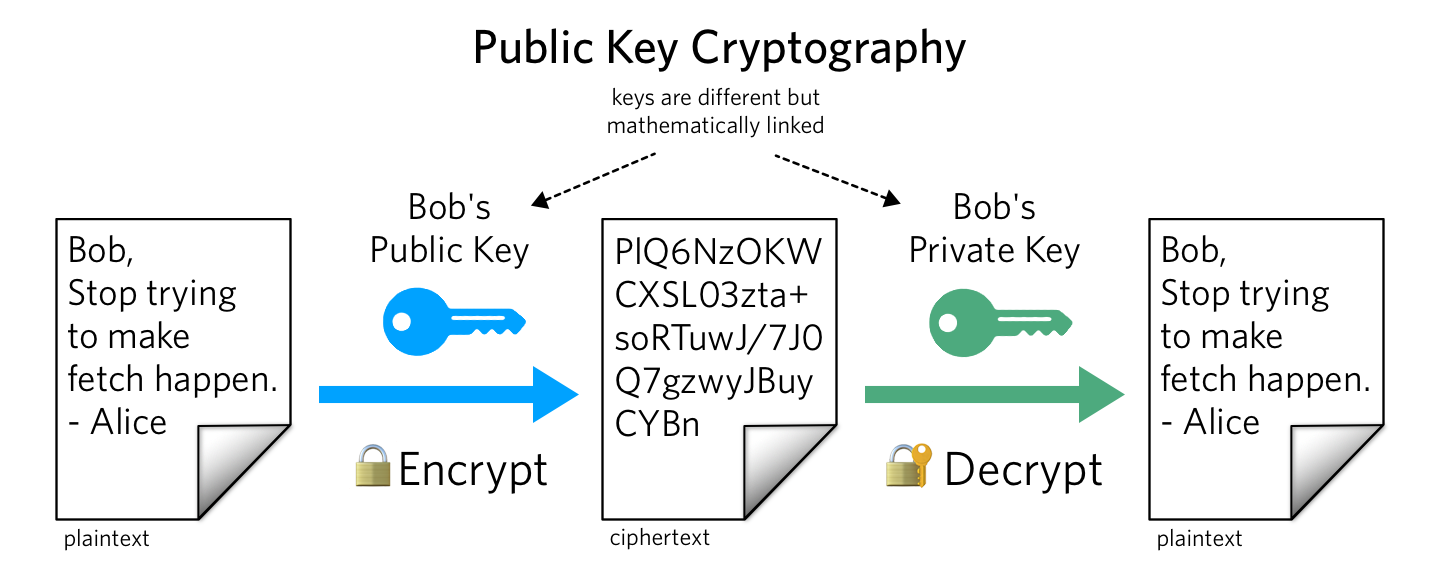
Common Encryption Types Protocols And Algorithms Expl Vrogue co

Public Key Cryptography With A Cryptographic Hash

Cryptage Cryptographie Ic ne De Vecteur De Protection Des Donn es
![]()
What Is Secret Key Cryptography A Complete Guide Helenix



Public
Public online Public gr

Public Key Cryptography With A Cryptographic Hash

What Is Public Key Cryptography
Cryptage Cryptographie Ic ne De Vecteur De Protection Des Donn es

What Is Secret Key Cryptography A Complete Guide Helenix
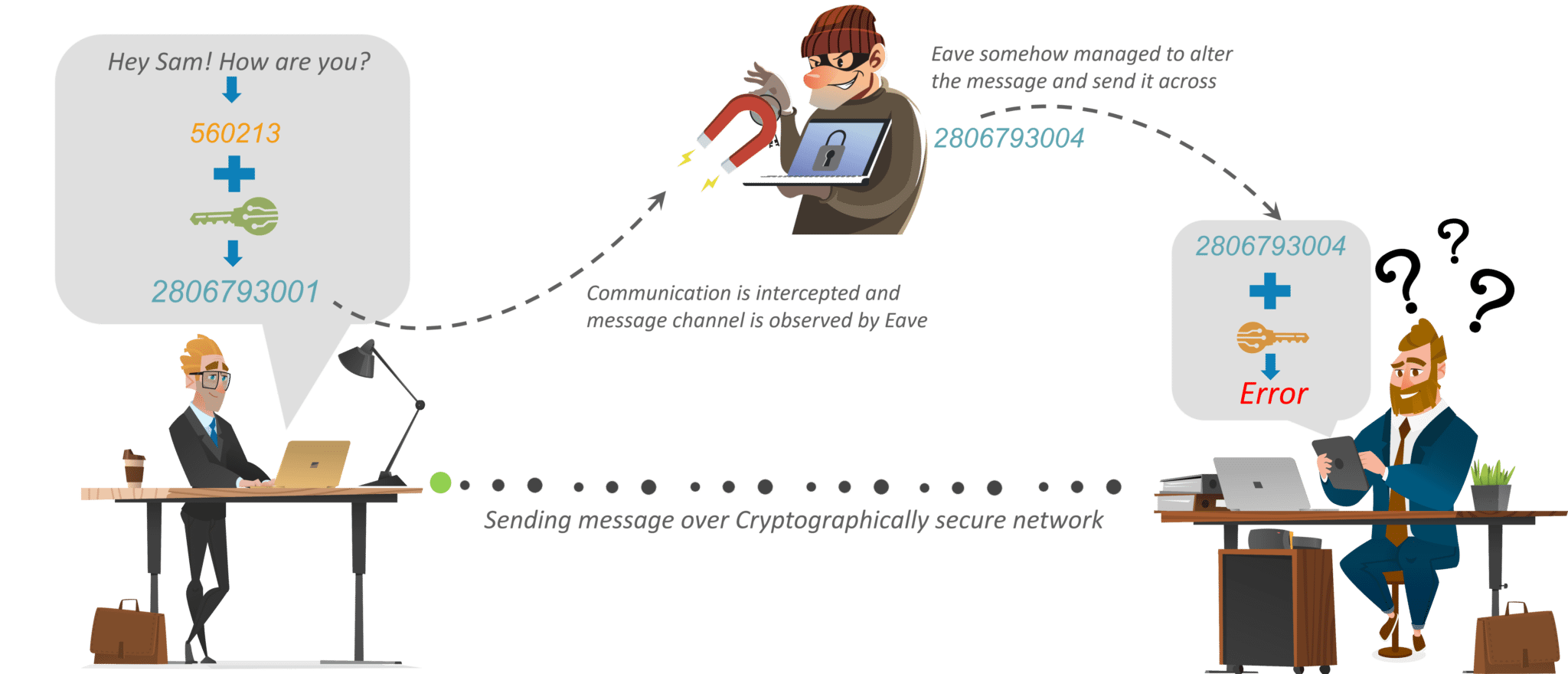
Cryptography The Art Of Encryption SPark

Elliptic Curve Cryptography In Blockchain Basic Introduction

Elliptic Curve Cryptography In Blockchain Basic Introduction
What Is Cryptography In Security Types Of Cryptography