Today, when screens dominate our lives and our lives are dominated by screens, the appeal of tangible printed products hasn't decreased. Be it for educational use such as creative projects or just adding the personal touch to your space, What Is Nist In Cyber Security have proven to be a valuable resource. In this article, we'll dive into the sphere of "What Is Nist In Cyber Security," exploring their purpose, where to get them, as well as how they can enhance various aspects of your life.
Get Latest What Is Nist In Cyber Security Below
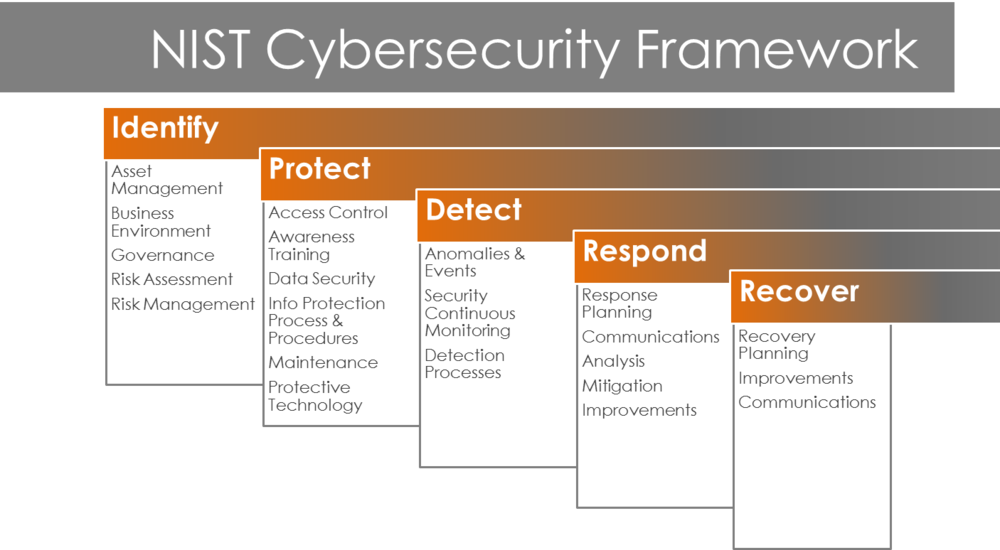
What Is Nist In Cyber Security
What Is Nist In Cyber Security -
A security operations center SOC improves an organization s threat detection response and prevention capabilities by unifying and coordinating all cybersecurity technologies and operations A SOC usually pronounced sock and sometimes called an information security operations center or ISOC is an in house or outsourced team of IT
Cybersecurity aims to protect computer systems applications devices data financial assets and people against ransomware and other malware phishing scams data theft and other cyberthreats At the enterprise level cybersecurity is a key component of an organization s overall risk management strategy According to Cybersecurity Ventures
What Is Nist In Cyber Security provide a diverse selection of printable and downloadable materials online, at no cost. They are available in numerous formats, such as worksheets, templates, coloring pages, and much more. The value of What Is Nist In Cyber Security is their versatility and accessibility.
More of What Is Nist In Cyber Security
Strengthen Security Of Your Data Center With The NIST Cybersecurity

Strengthen Security Of Your Data Center With The NIST Cybersecurity
Zero trust is a security strategy for modern multicloud networks Instead of focusing on the network perimeter a zero trust security model enforces security policies for each individual connection between users devices applications and data Zero trust operates on the principle of never trust always verify rather than granting
Incident response sometimes called cybersecurity incident response refers to an organization s processes and technologies for detecting and responding to cyberthreats security breaches or cyberattacks A formal incident response plan enables cybersecurity teams to limit or prevent damage The goal of incident response is to prevent
Printables for free have gained immense popularity due to a myriad of compelling factors:
-
Cost-Effective: They eliminate the necessity of purchasing physical copies or expensive software.
-
customization: The Customization feature lets you tailor print-ready templates to your specific requirements be it designing invitations, organizing your schedule, or even decorating your home.
-
Educational Benefits: Printing educational materials for no cost can be used by students of all ages. This makes them an essential source for educators and parents.
-
Easy to use: The instant accessibility to a variety of designs and templates cuts down on time and efforts.
Where to Find more What Is Nist In Cyber Security
Nist Cyber Security Framework Ref Twitter ReTweet EXTRAORDINAIRE

Nist Cyber Security Framework Ref Twitter ReTweet EXTRAORDINAIRE
Network security has three chief aims to prevent unauthorized access to network resources to detect and stop cyberattacks and security breaches in progress and to ensure that authorized users have secure access to the network resources they need when they need them As networks grow in size and complexity so does the risk of cyberattack
O NIST Cybersecurity Framework NIST CSF consiste em padr es diretrizes e pr ticas recomendadas que ajudam as organiza es a melhorar seu gerenciamento de riscos de seguran a cibern tica O NIST CSF foi projetado para ser flex vel o suficiente para se integrar aos processos de seguran a existentes em qualquer organiza o em
We've now piqued your curiosity about What Is Nist In Cyber Security We'll take a look around to see where they are hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide an extensive selection of What Is Nist In Cyber Security suitable for many purposes.
- Explore categories like decorations for the home, education and organization, and crafts.
2. Educational Platforms
- Educational websites and forums typically provide free printable worksheets including flashcards, learning tools.
- This is a great resource for parents, teachers and students who are in need of supplementary resources.
3. Creative Blogs
- Many bloggers provide their inventive designs or templates for download.
- The blogs are a vast selection of subjects, from DIY projects to party planning.
Maximizing What Is Nist In Cyber Security
Here are some innovative ways of making the most of What Is Nist In Cyber Security:
1. Home Decor
- Print and frame beautiful images, quotes, or seasonal decorations to adorn your living areas.
2. Education
- Print worksheets that are free to aid in learning at your home and in class.
3. Event Planning
- Designs invitations, banners and decorations for special occasions like birthdays and weddings.
4. Organization
- Stay organized by using printable calendars with to-do lists, planners, and meal planners.
Conclusion
What Is Nist In Cyber Security are a treasure trove of creative and practical resources catering to different needs and preferences. Their accessibility and flexibility make them an invaluable addition to your professional and personal life. Explore the many options of What Is Nist In Cyber Security now and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables actually available for download?
- Yes they are! You can print and download these files for free.
-
Can I use the free printables in commercial projects?
- It's based on the terms of use. Always review the terms of use for the creator before using printables for commercial projects.
-
Are there any copyright rights issues with printables that are free?
- Some printables could have limitations on usage. Make sure you read the terms and regulations provided by the designer.
-
How do I print What Is Nist In Cyber Security?
- Print them at home using an printer, or go to any local print store for better quality prints.
-
What program will I need to access printables that are free?
- Most PDF-based printables are available in the format of PDF, which can be opened with free software like Adobe Reader.
A Quick NIST Cybersecurity Framework Summary Cipher

Cybersecurity Starts With Your Employees Nist Riset
Check more sample of What Is Nist In Cyber Security below
NIST Framework For CyberSecurity AT NET Services
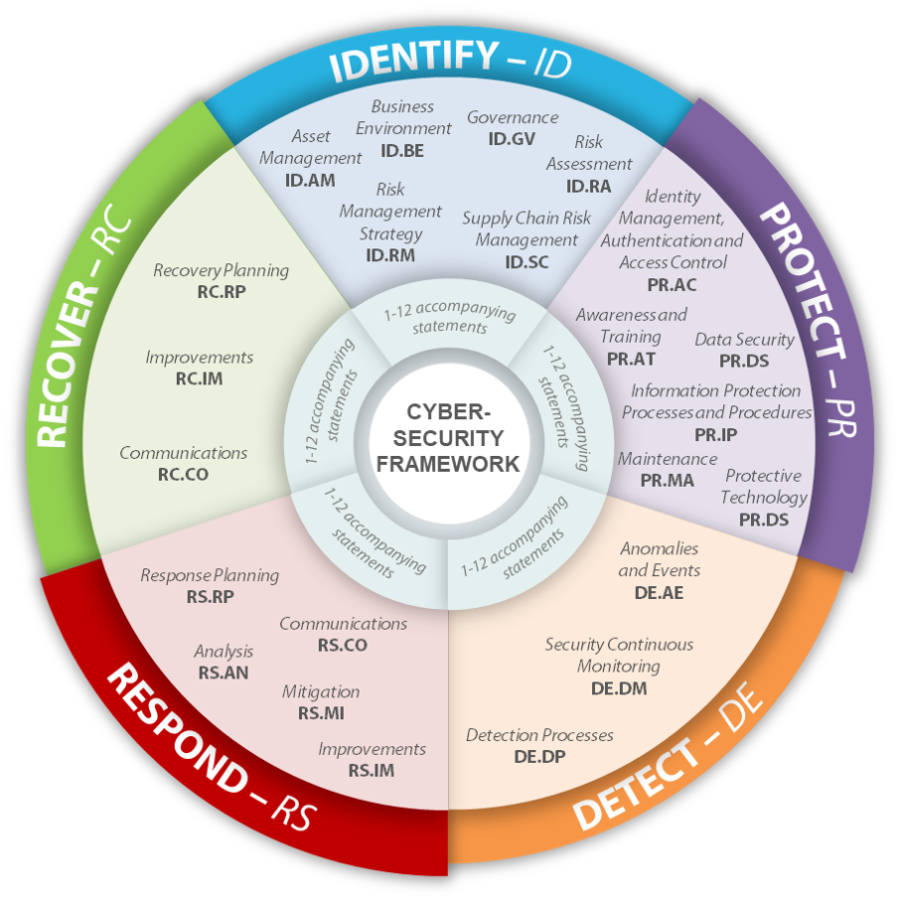
NIST Releases Version 1 1 Of Its Popular Cybersecurity Framework NIST

What Is The NIST Cybersecurity Framework CSF

NIST Support CorCystems

Cybersecurity Resources Control Framework Nist Engineers System
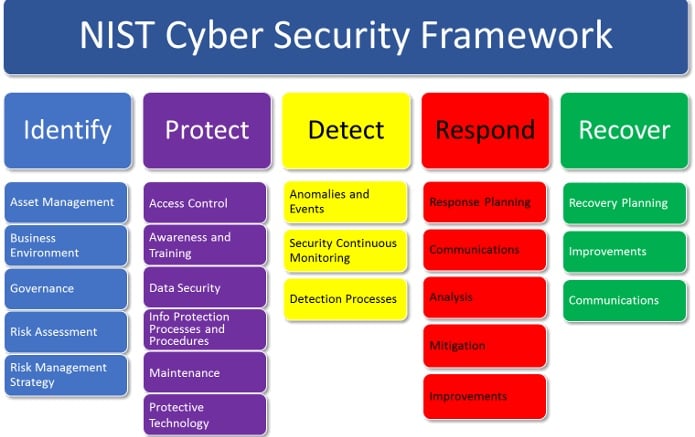
NIST CSF Overview YouTube


https://www.ibm.com/topics/cybersecurity
Cybersecurity aims to protect computer systems applications devices data financial assets and people against ransomware and other malware phishing scams data theft and other cyberthreats At the enterprise level cybersecurity is a key component of an organization s overall risk management strategy According to Cybersecurity Ventures

https://www.ibm.com/topics/cyber-risk-management
Cyber risk management initiatives offer companies a way to map and manage their shifting attack surfaces improving security posture The broader threat landscape also evolves constantly Every month roughly 2 000 new vulnerabilities are added to the NIST National Vulnerability Database link resides outside ibm
Cybersecurity aims to protect computer systems applications devices data financial assets and people against ransomware and other malware phishing scams data theft and other cyberthreats At the enterprise level cybersecurity is a key component of an organization s overall risk management strategy According to Cybersecurity Ventures
Cyber risk management initiatives offer companies a way to map and manage their shifting attack surfaces improving security posture The broader threat landscape also evolves constantly Every month roughly 2 000 new vulnerabilities are added to the NIST National Vulnerability Database link resides outside ibm

NIST Support CorCystems

NIST Releases Version 1 1 Of Its Popular Cybersecurity Framework NIST

Cybersecurity Resources Control Framework Nist Engineers System

NIST CSF Overview YouTube

MEP Centers Aid Manufacturers On Cybersecurity NIST

NIST Cyber Security Framework

NIST Cyber Security Framework
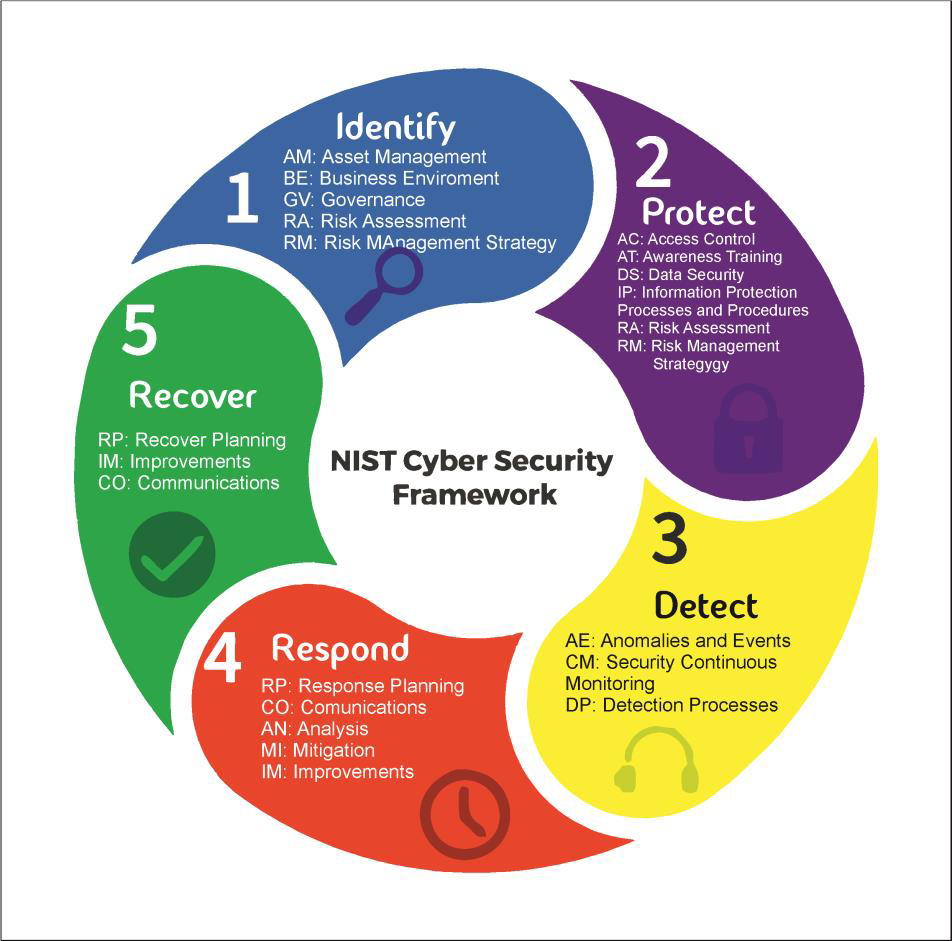
Entendiendo El Framework For Improving Critical Infrastructure