In a world with screens dominating our lives but the value of tangible printed items hasn't gone away. It doesn't matter if it's for educational reasons and creative work, or simply adding an individual touch to the home, printables for free are a great resource. In this article, we'll take a dive through the vast world of "What Applications Use Symmetric Encryption," exploring the different types of printables, where they can be found, and how they can improve various aspects of your daily life.
Get Latest What Applications Use Symmetric Encryption Below
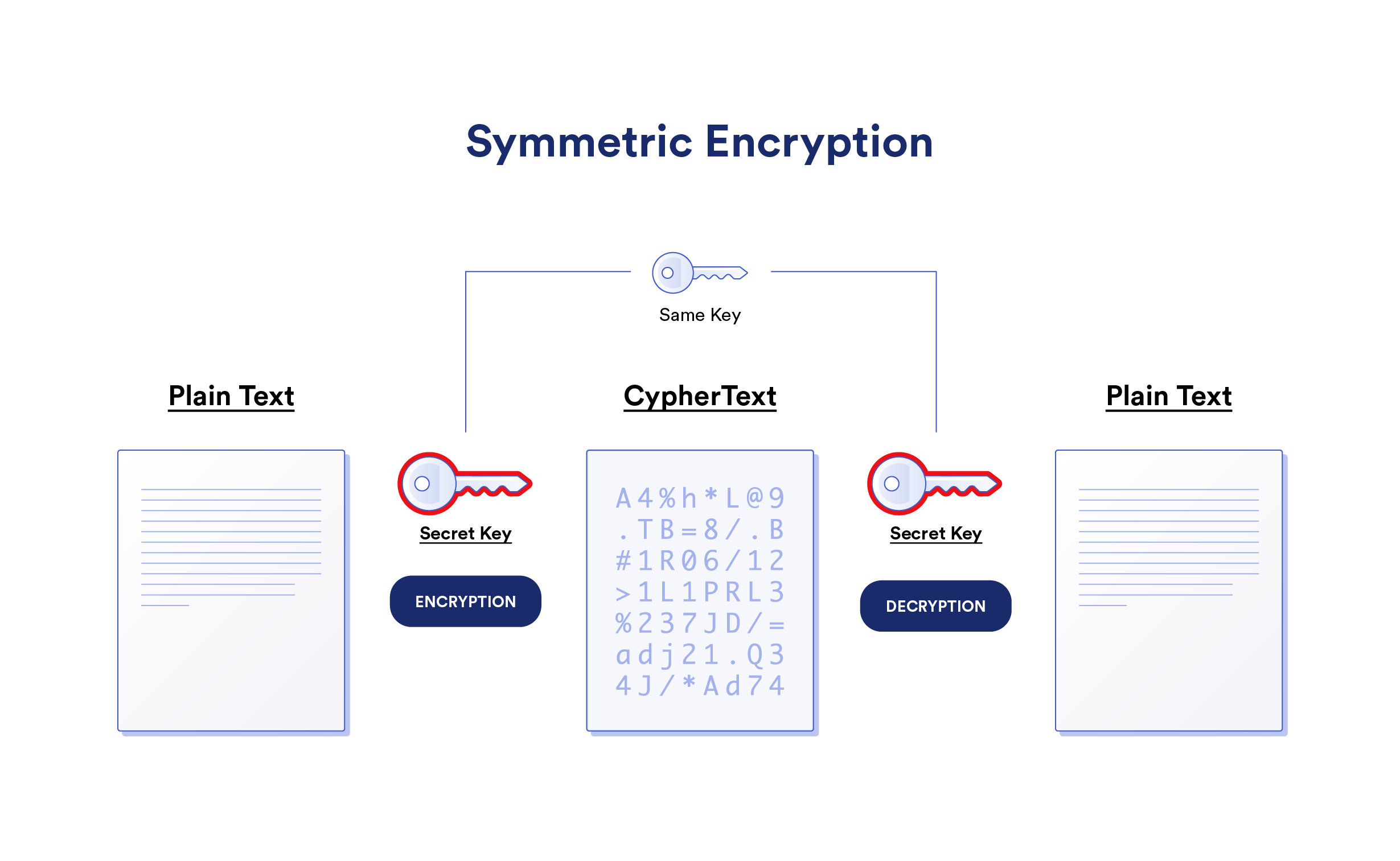
What Applications Use Symmetric Encryption
What Applications Use Symmetric Encryption -
Mise a jour chrome Accueil Applications Logiciels Ipad trop vieux pour application Guide Est ce risqu de forcer l installation IOS d un ancien IPAD Forum iPad Mise a jour
Sysinternals psinfo exe provides the most complete information of all the suggestions given and it can be run on any Windows PC from the command line directly from
What Applications Use Symmetric Encryption cover a large collection of printable documents that can be downloaded online at no cost. These printables come in different designs, including worksheets templates, coloring pages and many more. The appeal of printables for free is their versatility and accessibility.
More of What Applications Use Symmetric Encryption
What Is Zero Knowledge Encryption Chainlink Blog
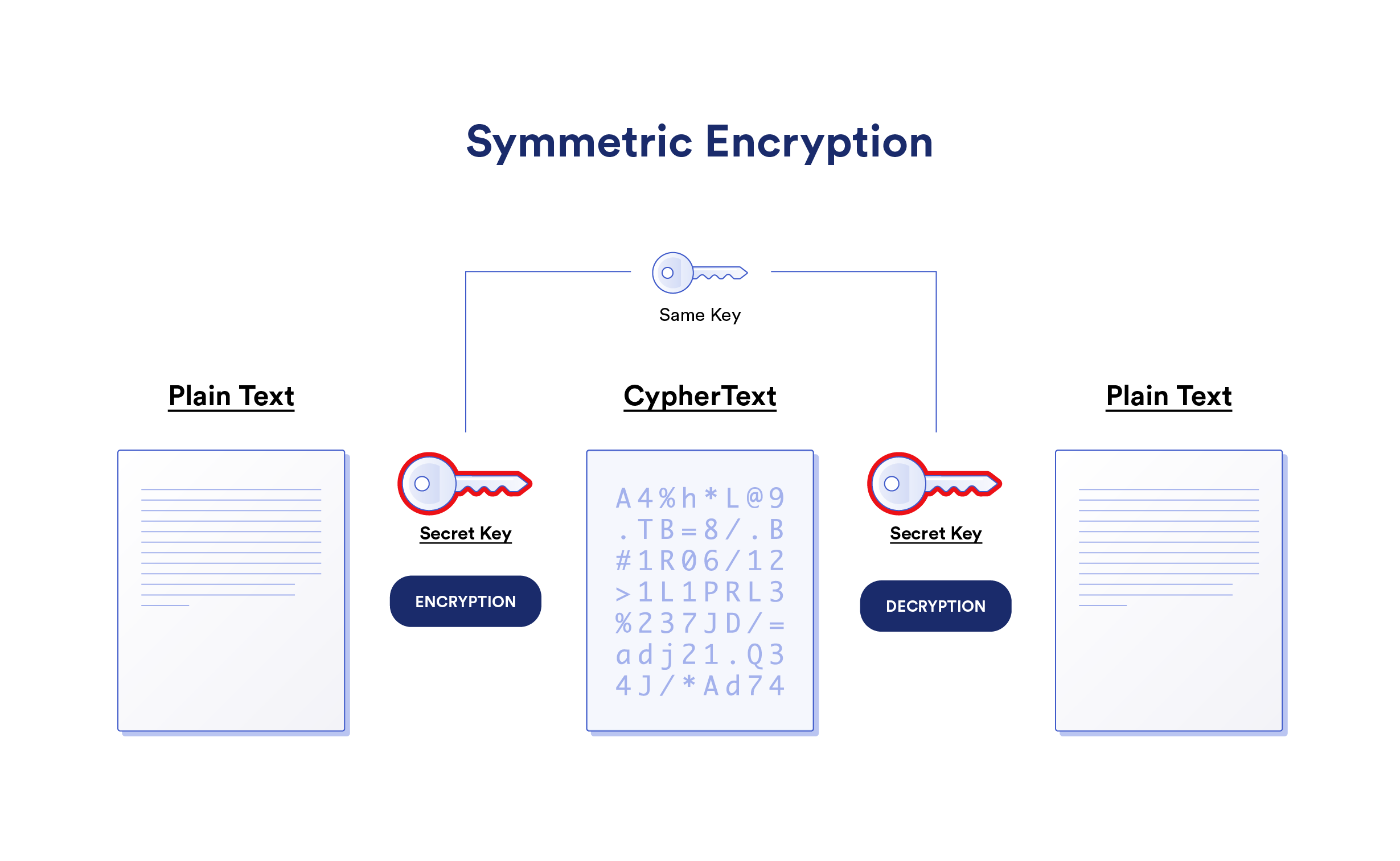
What Is Zero Knowledge Encryption Chainlink Blog
I am writing this reply to confirm that it also works for legacy applications Very well made product And this should definitely be marked as the solution I had been searching for a
Bonsoir tous j aimerais savoir si il est possible de connaitre par le biais de quelconque logiciel ou commande Windows la liste de tous les logiciels et ex cutables lanc s pendant une
What Applications Use Symmetric Encryption have garnered immense popularity due to numerous compelling reasons:
-
Cost-Effective: They eliminate the need to purchase physical copies or costly software.
-
The ability to customize: It is possible to tailor printables to fit your particular needs when it comes to designing invitations or arranging your schedule or even decorating your home.
-
Educational Worth: Printables for education that are free offer a wide range of educational content for learners from all ages, making them an essential source for educators and parents.
-
The convenience of Fast access numerous designs and templates cuts down on time and efforts.
Where to Find more What Applications Use Symmetric Encryption
How To Share A Key In Symmetric Cryptography Baeldung On Computer
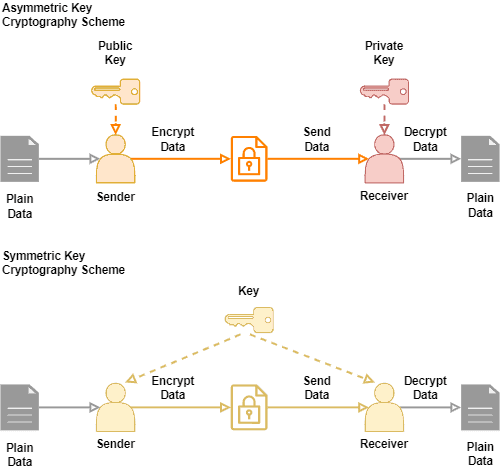
How To Share A Key In Symmetric Cryptography Baeldung On Computer
Applications without a requested execution level attribute Interactive processes running as a standard user with UAC enabled Before a 32 bit process is created the following
HKEY CLASSES ROOT Applications Windows R
We've now piqued your interest in printables for free Let's look into where you can find these hidden gems:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide a large collection with What Applications Use Symmetric Encryption for all needs.
- Explore categories like decorations for the home, education and the arts, and more.
2. Educational Platforms
- Educational websites and forums frequently offer worksheets with printables that are free including flashcards, learning materials.
- The perfect resource for parents, teachers and students who are in need of supplementary resources.
3. Creative Blogs
- Many bloggers provide their inventive designs as well as templates for free.
- These blogs cover a broad variety of topics, everything from DIY projects to planning a party.
Maximizing What Applications Use Symmetric Encryption
Here are some innovative ways for you to get the best of printables that are free:
1. Home Decor
- Print and frame beautiful artwork, quotes or seasonal decorations to adorn your living areas.
2. Education
- Print free worksheets to enhance your learning at home as well as in the class.
3. Event Planning
- Design invitations, banners, as well as decorations for special occasions such as weddings and birthdays.
4. Organization
- Stay organized with printable planners including to-do checklists, daily lists, and meal planners.
Conclusion
What Applications Use Symmetric Encryption are a treasure trove of creative and practical resources that cater to various needs and needs and. Their accessibility and versatility make them a wonderful addition to the professional and personal lives of both. Explore the vast array of What Applications Use Symmetric Encryption today and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables available for download really for free?
- Yes you can! You can print and download these items for free.
-
Can I use free printables to make commercial products?
- It's determined by the specific conditions of use. Always review the terms of use for the creator prior to printing printables for commercial projects.
-
Do you have any copyright violations with What Applications Use Symmetric Encryption?
- Some printables may come with restrictions regarding usage. You should read the terms and conditions provided by the author.
-
How can I print printables for free?
- Print them at home with any printer or head to an area print shop for premium prints.
-
What software will I need to access printables that are free?
- A majority of printed materials are in the format of PDF, which is open with no cost software, such as Adobe Reader.
SSH Cos E Come Funziona Secure Shell Creativemotions

What Is Symmetric Key Cryptography Encryption Security Wiki

Check more sample of What Applications Use Symmetric Encryption below
Symmetric Vs Asymmetric Encryption Differences Explained

Cryptography 101 Sandfield
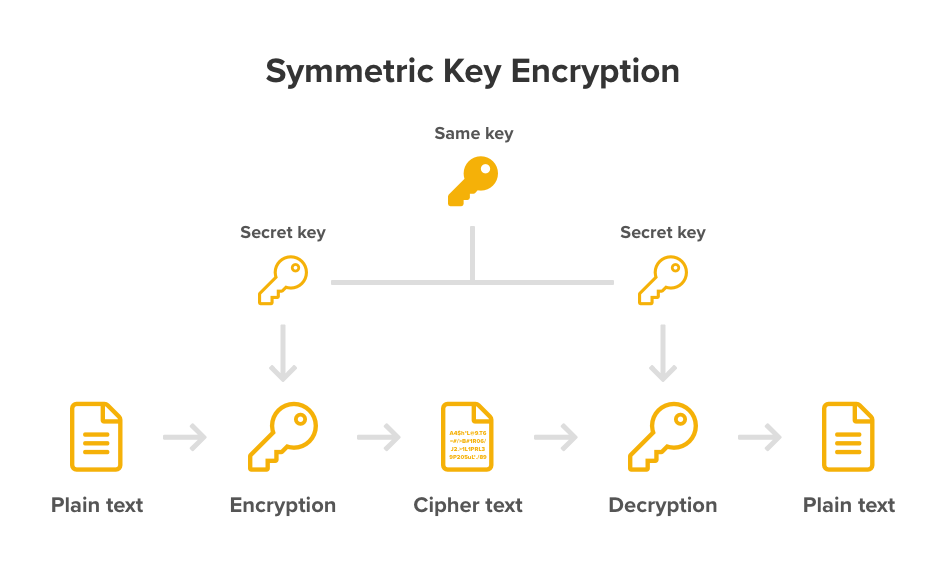
Encryption Choices Rsa Vs Aes Explained Prey

Asymmetric Encryption What It Is Why Your Security Depends On It
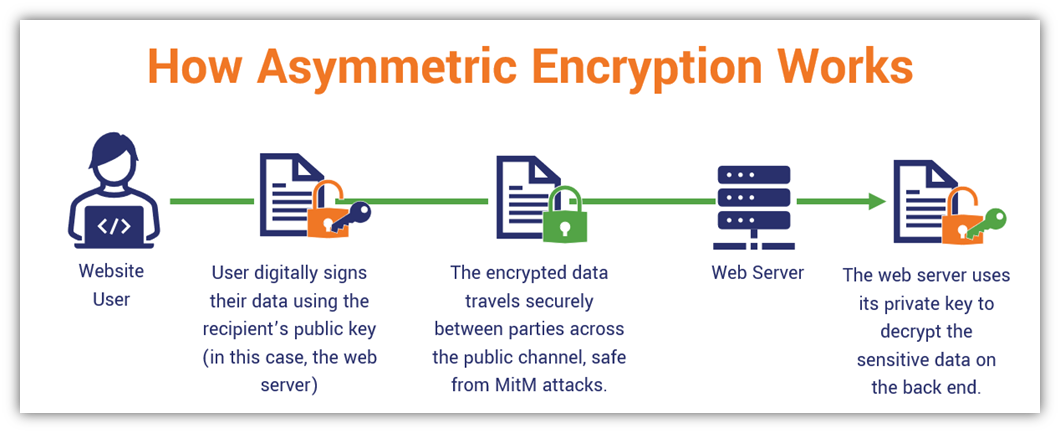
A Practical Guide To Asymmetric Encryption Part 1 Krupesh Anadkat

Public Key Encryption What Is Public Cryptography Okta AU NZ

https://superuser.com › questions
Sysinternals psinfo exe provides the most complete information of all the suggestions given and it can be run on any Windows PC from the command line directly from
https://forums.commentcamarche.net › forum
Product PC 17 HP I5 10e 8G 512SSD Operating System Microsoft Windows 10 64 Bit Bonjour Je viens d acheter mon ordinateur portable
Sysinternals psinfo exe provides the most complete information of all the suggestions given and it can be run on any Windows PC from the command line directly from
Product PC 17 HP I5 10e 8G 512SSD Operating System Microsoft Windows 10 64 Bit Bonjour Je viens d acheter mon ordinateur portable

Asymmetric Encryption What It Is Why Your Security Depends On It

Cryptography 101 Sandfield

A Practical Guide To Asymmetric Encryption Part 1 Krupesh Anadkat

Public Key Encryption What Is Public Cryptography Okta AU NZ

Public Key Cryptography Decoded What Is Cryptography Ntirawen
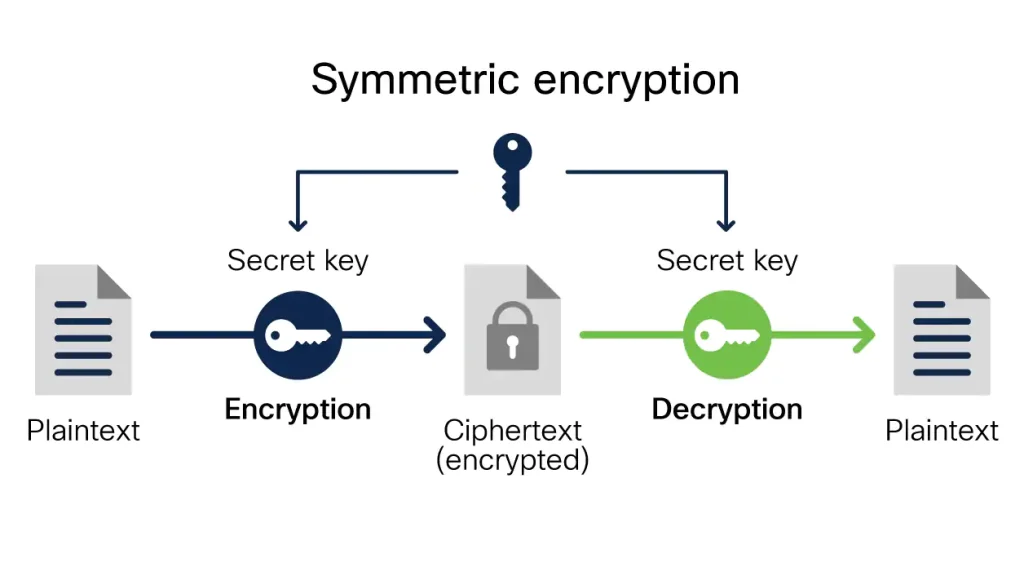
Encryption THE CHETTER

Encryption THE CHETTER

What Is Symmetric And Asymmetric Encryption Examples