In the age of digital, with screens dominating our lives and our lives are dominated by screens, the appeal of tangible printed objects hasn't waned. Be it for educational use, creative projects, or just adding an extra personal touch to your space, Types Of Encryption Techniques In Network Security are a great resource. For this piece, we'll take a dive in the world of "Types Of Encryption Techniques In Network Security," exploring the benefits of them, where to get them, as well as ways they can help you improve many aspects of your lives.
Get Latest Types Of Encryption Techniques In Network Security Below

Types Of Encryption Techniques In Network Security
Types Of Encryption Techniques In Network Security -
We can often see in online group conversations messages composed of random letters like fjqofudnelfi as a response to something surprising or unexpected Is there a name
Types of things vs types of thing When using the phrase types of or kinds of it often seems appropriate to follow with a singular noun e g types of rock but at other times a plural noun
Types Of Encryption Techniques In Network Security cover a large selection of printable and downloadable resources available online for download at no cost. They are available in a variety of forms, like worksheets templates, coloring pages, and many more. The value of Types Of Encryption Techniques In Network Security is in their variety and accessibility.
More of Types Of Encryption Techniques In Network Security
What Is Data Encryption Types Algorithms Techniques And Methods
What Is Data Encryption Types Algorithms Techniques And Methods
I would like to create a list of terms from beginner to expert using as many terms as possible which represent different levels of expertise I have constructed by myself Newbie Novice Rookie
In many examples of modern grammar the five key components of clause structure are defined as subjects objects verbs complements and adjuncts My question is
Types Of Encryption Techniques In Network Security have garnered immense popularity due to numerous compelling reasons:
-
Cost-Effective: They eliminate the necessity to purchase physical copies or expensive software.
-
Modifications: They can make printables to your specific needs such as designing invitations as well as organizing your calendar, or decorating your home.
-
Education Value Downloads of educational content for free provide for students of all ages, which makes the perfect device for teachers and parents.
-
An easy way to access HTML0: You have instant access a myriad of designs as well as templates is time-saving and saves effort.
Where to Find more Types Of Encryption Techniques In Network Security
How Public Key Encryption Ensures Data Integrity

How Public Key Encryption Ensures Data Integrity
CSDN Linux No such file or directory Linux No such file or directory
A man s cry is different from a woman s Similarly a toddler s cry differs from an adolescent s More importantly however there are no current studies or research about the
If we've already piqued your interest in printables for free Let's take a look at where you can get these hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a wide selection of Types Of Encryption Techniques In Network Security to suit a variety of objectives.
- Explore categories like furniture, education, the arts, and more.
2. Educational Platforms
- Educational websites and forums usually offer worksheets with printables that are free Flashcards, worksheets, and other educational tools.
- This is a great resource for parents, teachers or students in search of additional resources.
3. Creative Blogs
- Many bloggers share their innovative designs as well as templates for free.
- These blogs cover a wide range of interests, starting from DIY projects to planning a party.
Maximizing Types Of Encryption Techniques In Network Security
Here are some inventive ways of making the most use of printables that are free:
1. Home Decor
- Print and frame beautiful artwork, quotes, or even seasonal decorations to decorate your living areas.
2. Education
- Print free worksheets to build your knowledge at home or in the classroom.
3. Event Planning
- Design invitations, banners as well as decorations for special occasions such as weddings or birthdays.
4. Organization
- Stay organized by using printable calendars checklists for tasks, as well as meal planners.
Conclusion
Types Of Encryption Techniques In Network Security are a treasure trove of useful and creative resources that cater to various needs and preferences. Their accessibility and versatility make them a valuable addition to the professional and personal lives of both. Explore the endless world of Types Of Encryption Techniques In Network Security right now and discover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables for free really free?
- Yes they are! You can download and print these files for free.
-
Do I have the right to use free printouts for commercial usage?
- It's determined by the specific rules of usage. Always review the terms of use for the creator before using any printables on commercial projects.
-
Are there any copyright concerns when using printables that are free?
- Certain printables could be restricted regarding their use. Be sure to read the terms and conditions provided by the designer.
-
How can I print printables for free?
- Print them at home with any printer or head to a local print shop to purchase top quality prints.
-
What program do I require to open printables free of charge?
- The majority of printed documents are in the format PDF. This can be opened using free software, such as Adobe Reader.
What Is Encryption How It Works Types Of Encryption Norton

DS141 Telegram LIHKG

Check more sample of Types Of Encryption Techniques In Network Security below
Pixrron Food And Drinks

1 Different Types Of Cryptographic Techniques 2 Download
How To Decrypt Apco 25 Encryption Software Friendsefira
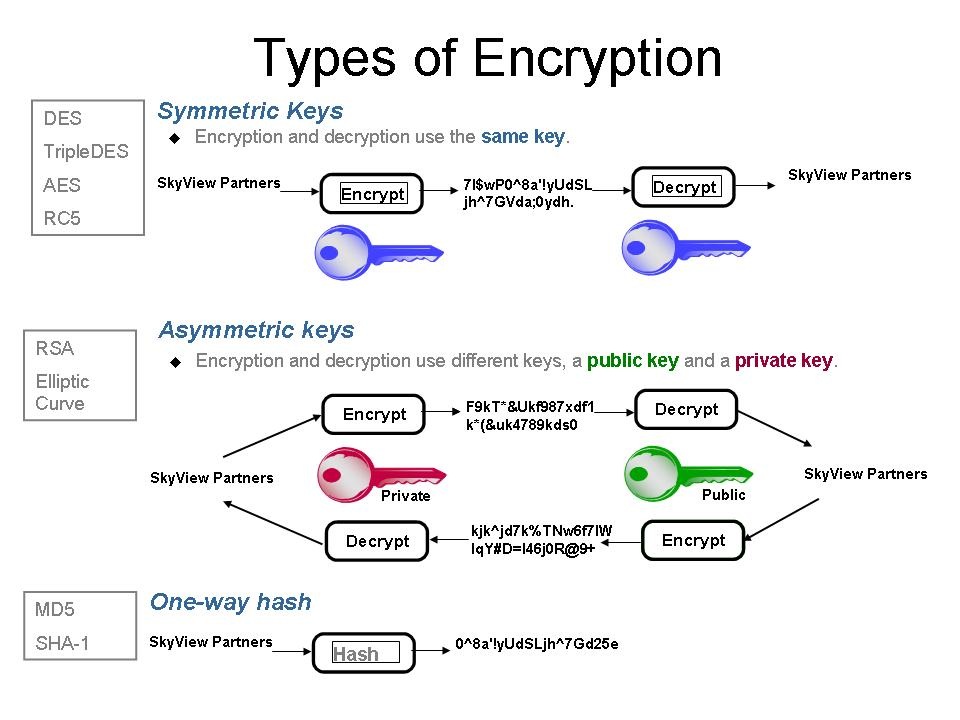
What Is Cryptography In Security What Are The Different Types Of
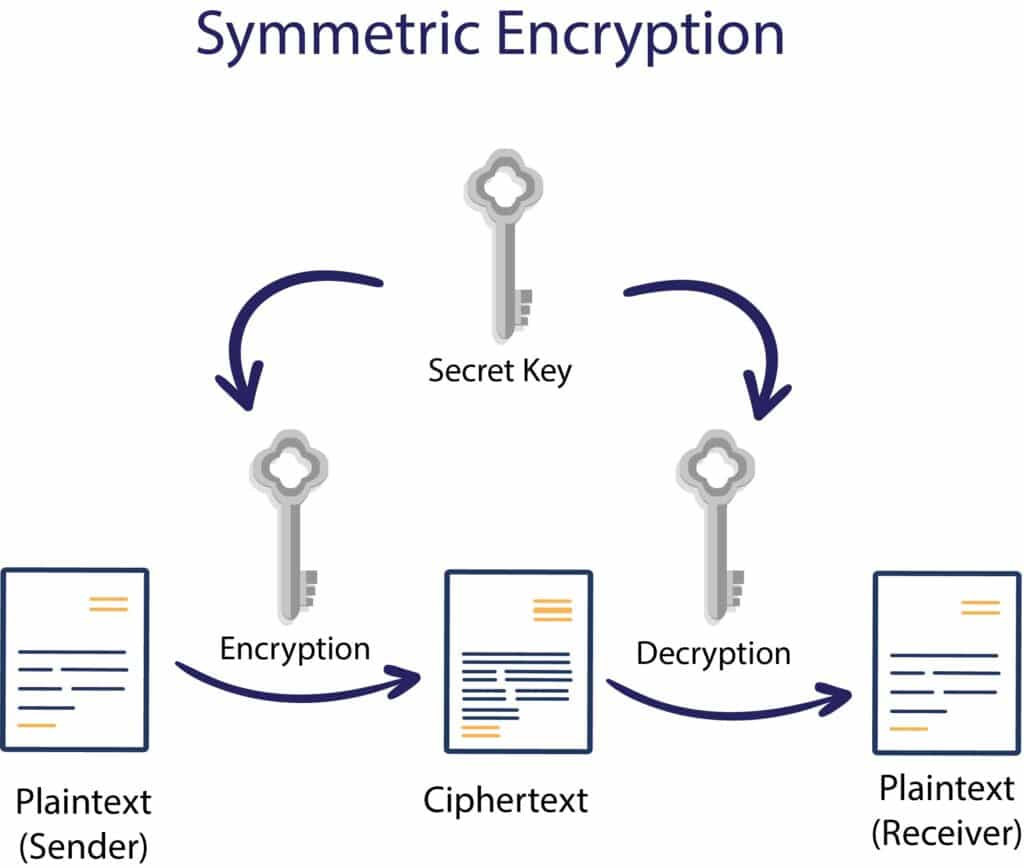
Encryption Techniques
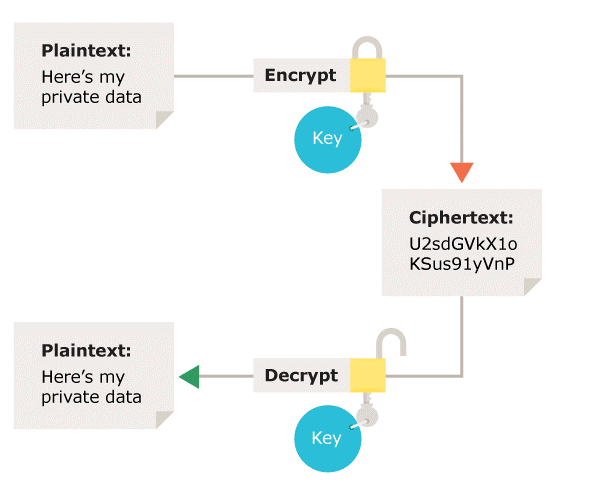
What Is Secret Key Cryptography A Complete Guide Helenix


https://english.stackexchange.com › questions
Types of things vs types of thing When using the phrase types of or kinds of it often seems appropriate to follow with a singular noun e g types of rock but at other times a plural noun
https://english.stackexchange.com › questions
If we want to know the exact kind of a group of brids should we say A What is the kind of these birds or B What kind of birds are these birds If the questions above are
Types of things vs types of thing When using the phrase types of or kinds of it often seems appropriate to follow with a singular noun e g types of rock but at other times a plural noun
If we want to know the exact kind of a group of brids should we say A What is the kind of these birds or B What kind of birds are these birds If the questions above are

What Is Cryptography In Security What Are The Different Types Of
1 Different Types Of Cryptographic Techniques 2 Download

Encryption Techniques

What Is Secret Key Cryptography A Complete Guide Helenix
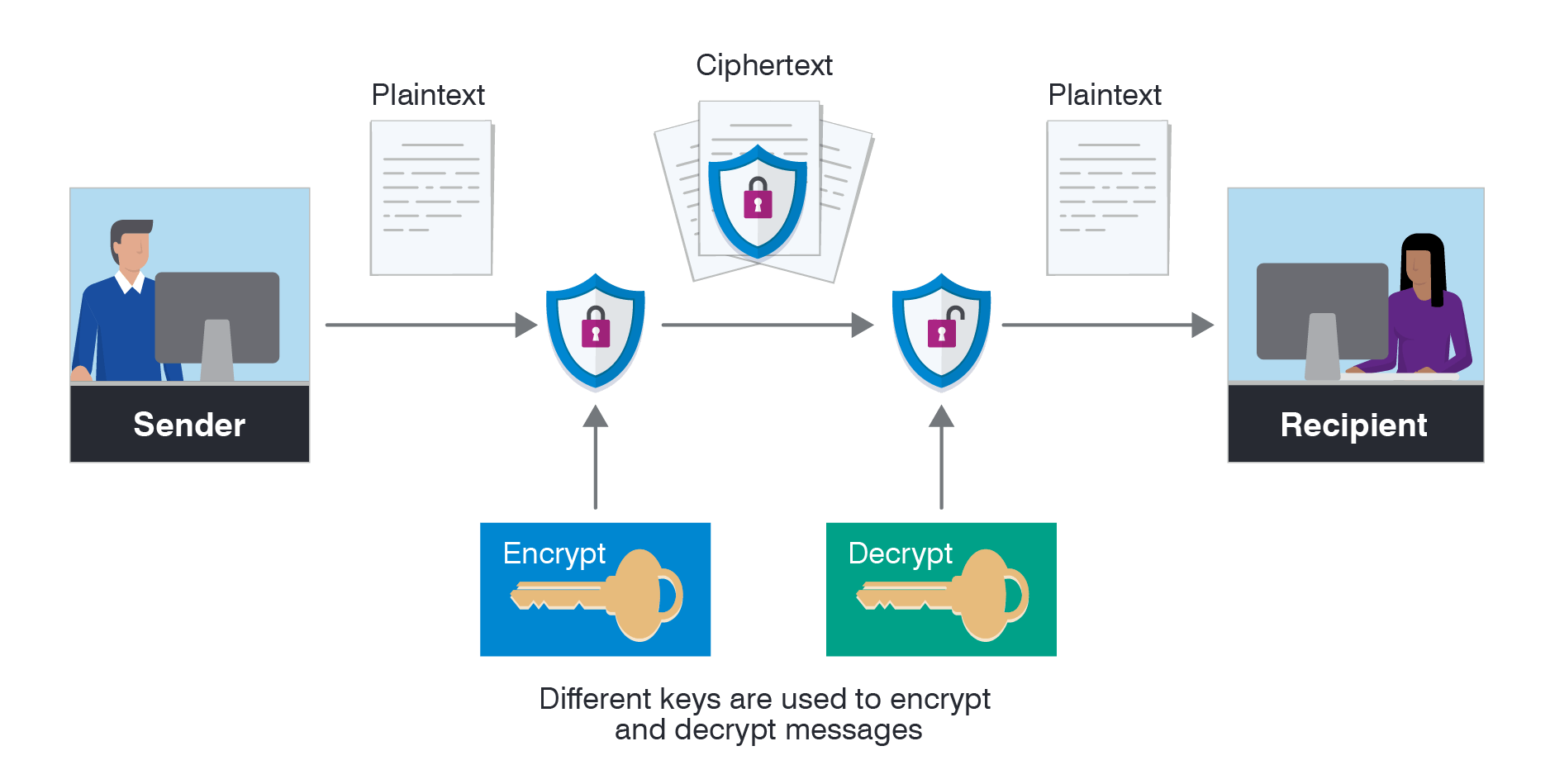
What Is Encryption Javatpoint
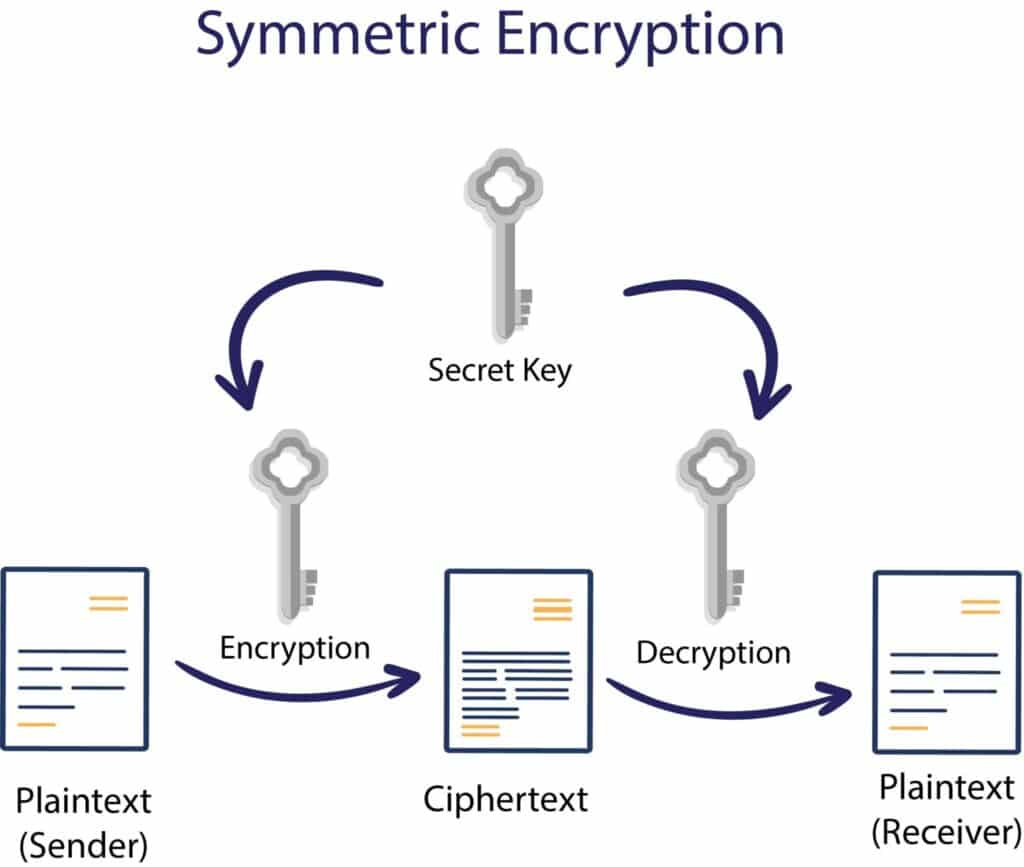
What Is The Role Of Encryption In E Commerce Explain Encryption E

What Is The Role Of Encryption In E Commerce Explain Encryption E

Password Encryption Presentation