In this age of technology, with screens dominating our lives and our lives are dominated by screens, the appeal of tangible printed items hasn't gone away. For educational purposes or creative projects, or simply to add an extra personal touch to your home, printables for free are now an essential source. In this article, we'll take a dive deep into the realm of "Types Of Encryption Algorithms In Cyber Security," exploring the benefits of them, where you can find them, and how they can be used to enhance different aspects of your life.
Get Latest Types Of Encryption Algorithms In Cyber Security Below

Types Of Encryption Algorithms In Cyber Security
Types Of Encryption Algorithms In Cyber Security -
We can often see in online group conversations messages composed of random letters like fjqofudnelfi as a response to something surprising or unexpected Is there a name
Types of things vs types of thing When using the phrase types of or kinds of it often seems appropriate to follow with a singular noun e g types of rock but at other times a plural noun
The Types Of Encryption Algorithms In Cyber Security are a huge variety of printable, downloadable materials that are accessible online for free cost. The resources are offered in a variety types, like worksheets, templates, coloring pages and much more. The appealingness of Types Of Encryption Algorithms In Cyber Security is their versatility and accessibility.
More of Types Of Encryption Algorithms In Cyber Security
Common Encryption Types Protocols And Algorithms Explained
Common Encryption Types Protocols And Algorithms Explained
I would like to create a list of terms from beginner to expert using as many terms as possible which represent different levels of expertise I have constructed by myself Newbie Novice Rookie
In many examples of modern grammar the five key components of clause structure are defined as subjects objects verbs complements and adjuncts My question is
Types Of Encryption Algorithms In Cyber Security have gained a lot of popularity for several compelling reasons:
-
Cost-Efficiency: They eliminate the necessity to purchase physical copies or expensive software.
-
customization: We can customize printing templates to your own specific requirements such as designing invitations to organize your schedule or even decorating your house.
-
Educational Use: Educational printables that can be downloaded for free are designed to appeal to students from all ages, making them a vital instrument for parents and teachers.
-
Affordability: The instant accessibility to many designs and templates reduces time and effort.
Where to Find more Types Of Encryption Algorithms In Cyber Security
What Is CRYPTOGRAPHY And Its Types TheCScience

What Is CRYPTOGRAPHY And Its Types TheCScience
CSDN Linux No such file or directory Linux No such file or directory
A man s cry is different from a woman s Similarly a toddler s cry differs from an adolescent s More importantly however there are no current studies or research about the
We hope we've stimulated your interest in Types Of Encryption Algorithms In Cyber Security Let's look into where you can get these hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a wide selection and Types Of Encryption Algorithms In Cyber Security for a variety reasons.
- Explore categories such as decorating your home, education, organizational, and arts and crafts.
2. Educational Platforms
- Educational websites and forums typically provide worksheets that can be printed for free or flashcards as well as learning tools.
- It is ideal for teachers, parents and students who are in need of supplementary resources.
3. Creative Blogs
- Many bloggers share their creative designs as well as templates for free.
- These blogs cover a wide range of interests, all the way from DIY projects to planning a party.
Maximizing Types Of Encryption Algorithms In Cyber Security
Here are some creative ways that you can make use use of Types Of Encryption Algorithms In Cyber Security:
1. Home Decor
- Print and frame stunning art, quotes, or seasonal decorations that will adorn your living spaces.
2. Education
- Utilize free printable worksheets for teaching at-home as well as in the class.
3. Event Planning
- Designs invitations, banners and decorations for special events like weddings or birthdays.
4. Organization
- Be organized by using printable calendars along with lists of tasks, and meal planners.
Conclusion
Types Of Encryption Algorithms In Cyber Security are a treasure trove of innovative and useful resources catering to different needs and hobbies. Their accessibility and flexibility make these printables a useful addition to your professional and personal life. Explore the world of Types Of Encryption Algorithms In Cyber Security to uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free cost-free?
- Yes, they are! You can download and print these items for free.
-
Can I utilize free printables for commercial purposes?
- It's dependent on the particular conditions of use. Always read the guidelines of the creator prior to printing printables for commercial projects.
-
Do you have any copyright concerns with Types Of Encryption Algorithms In Cyber Security?
- Certain printables may be subject to restrictions on usage. Be sure to read the terms and regulations provided by the author.
-
How do I print printables for free?
- You can print them at home with the printer, or go to the local print shops for better quality prints.
-
What program do I need to open printables that are free?
- Most printables come in the PDF format, and can be opened using free programs like Adobe Reader.
Cryptography CyberSecurity Studio
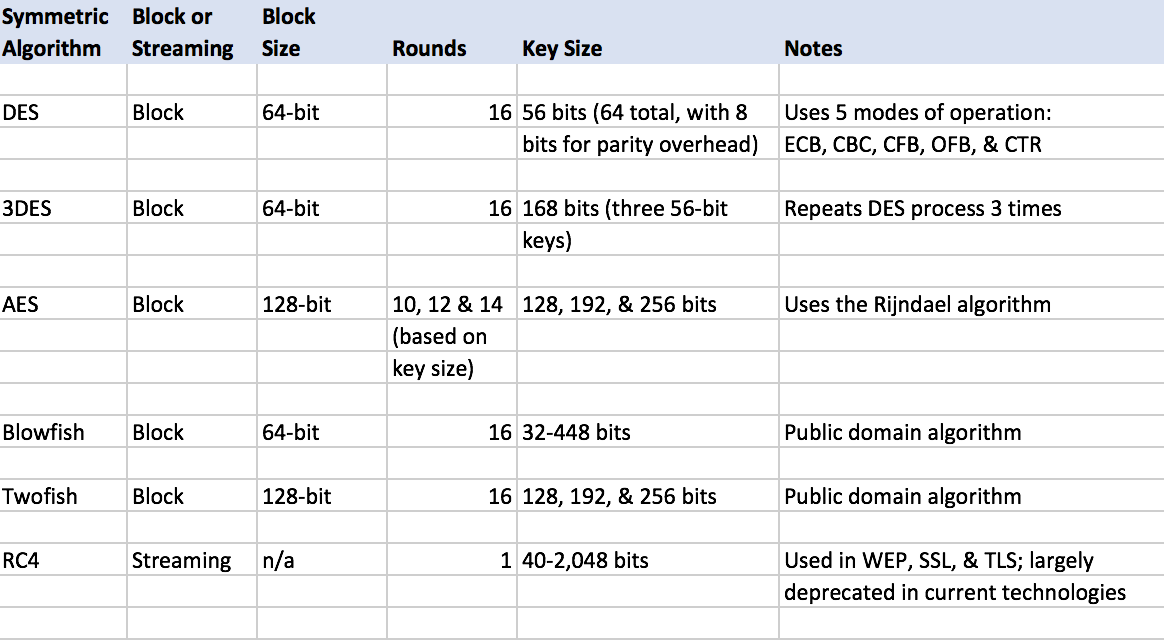
Cryptographic Algorithms List

Check more sample of Types Of Encryption Algorithms In Cyber Security below
Cryptography CyberSecurity Studio
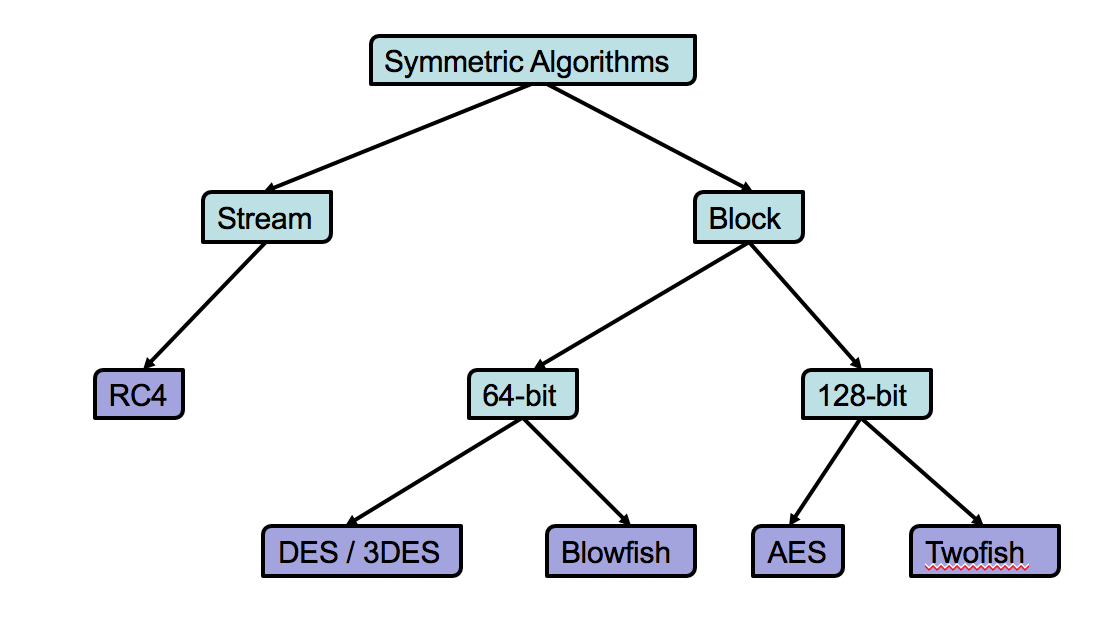
Unlocking Blockchain s Fort Knox The Power Of Cryptography For

Fees An Proportion Starting Awards Charged Go Assistants Of Property

Clip Which One Of The Following Is Not A Mode Of Operation For The Data

What Is Encryption How It Works Types Of Encryption Norton

Encryption THE CHETTER
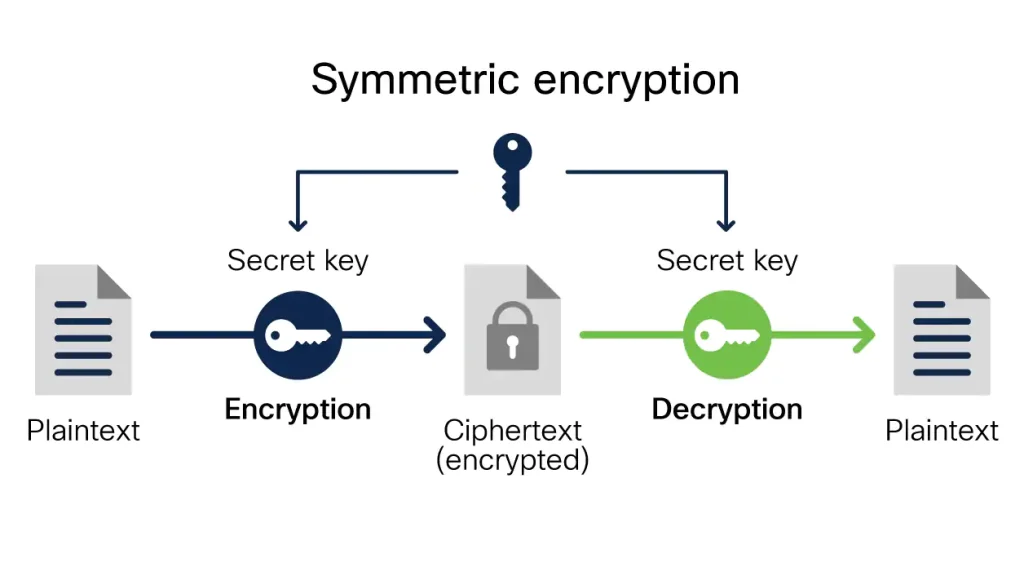
https://english.stackexchange.com › questions
Types of things vs types of thing When using the phrase types of or kinds of it often seems appropriate to follow with a singular noun e g types of rock but at other times a plural noun

https://english.stackexchange.com › questions
If we want to know the exact kind of a group of brids should we say A What is the kind of these birds or B What kind of birds are these birds If the questions above are
Types of things vs types of thing When using the phrase types of or kinds of it often seems appropriate to follow with a singular noun e g types of rock but at other times a plural noun
If we want to know the exact kind of a group of brids should we say A What is the kind of these birds or B What kind of birds are these birds If the questions above are

Clip Which One Of The Following Is Not A Mode Of Operation For The Data

Unlocking Blockchain s Fort Knox The Power Of Cryptography For

What Is Encryption How It Works Types Of Encryption Norton

Encryption THE CHETTER
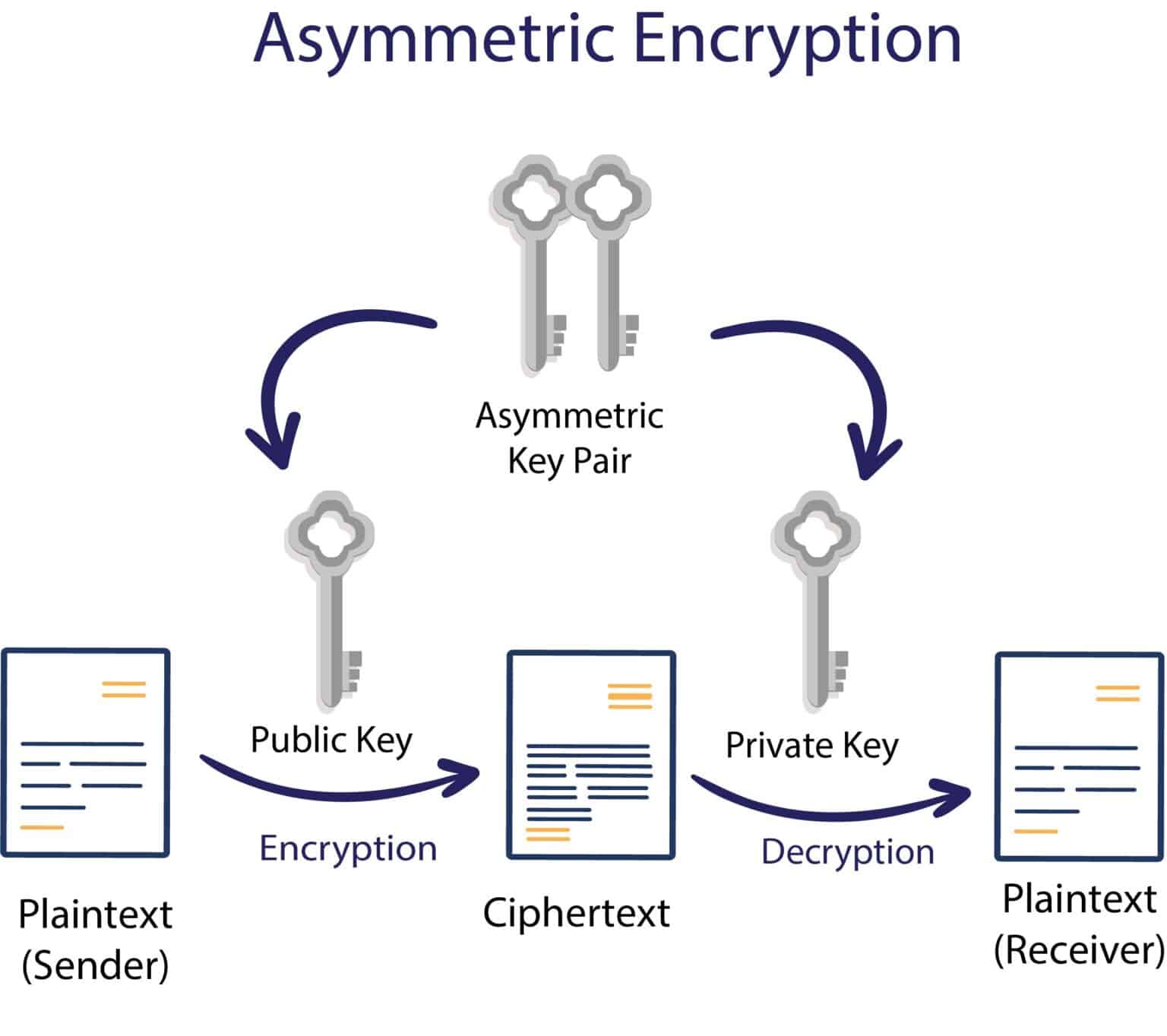
What Is The Difference Between Symmetric And Asymmetric Encryption
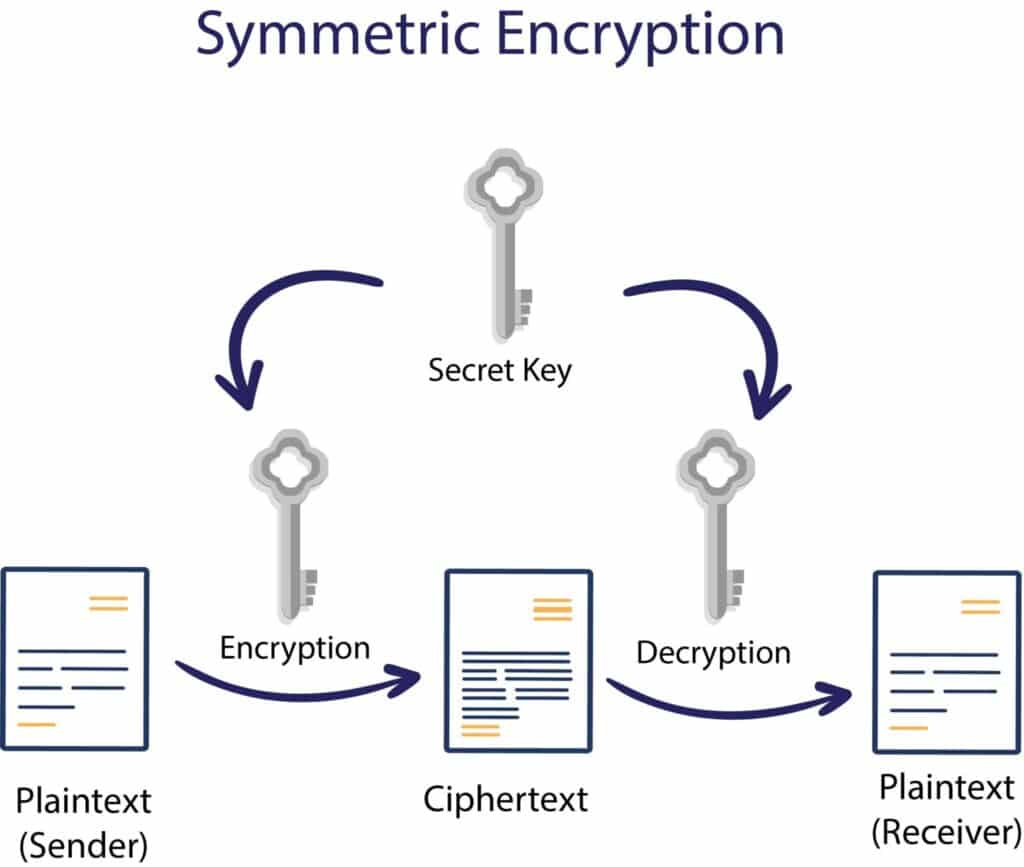
What Is The Role Of Encryption In E Commerce Explain Encryption E

What Is The Role Of Encryption In E Commerce Explain Encryption E
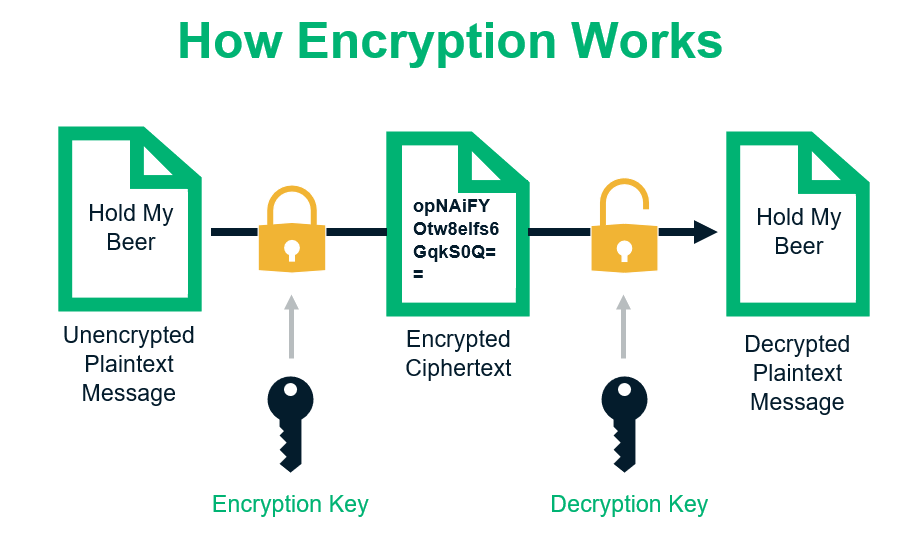
Encryption L G Nh ng i u C n Bi t V M H a Tin T c T n Mi n Hosting