In this age of electronic devices, where screens have become the dominant feature of our lives but the value of tangible printed materials hasn't faded away. Be it for educational use project ideas, artistic or simply adding personal touches to your area, Symmetric Encryption Uses Public Or Private Key have become an invaluable source. With this guide, you'll take a dive deep into the realm of "Symmetric Encryption Uses Public Or Private Key," exploring the different types of printables, where to find them, and how they can add value to various aspects of your lives.
Get Latest Symmetric Encryption Uses Public Or Private Key Below
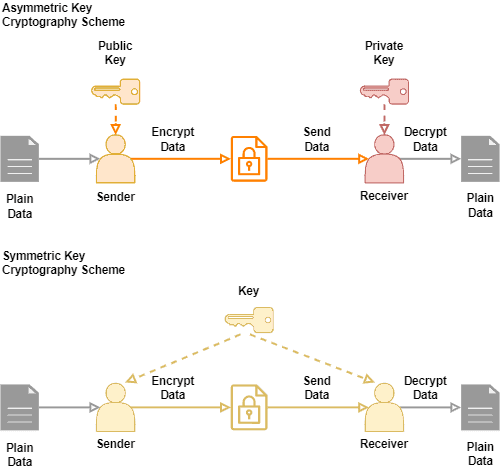
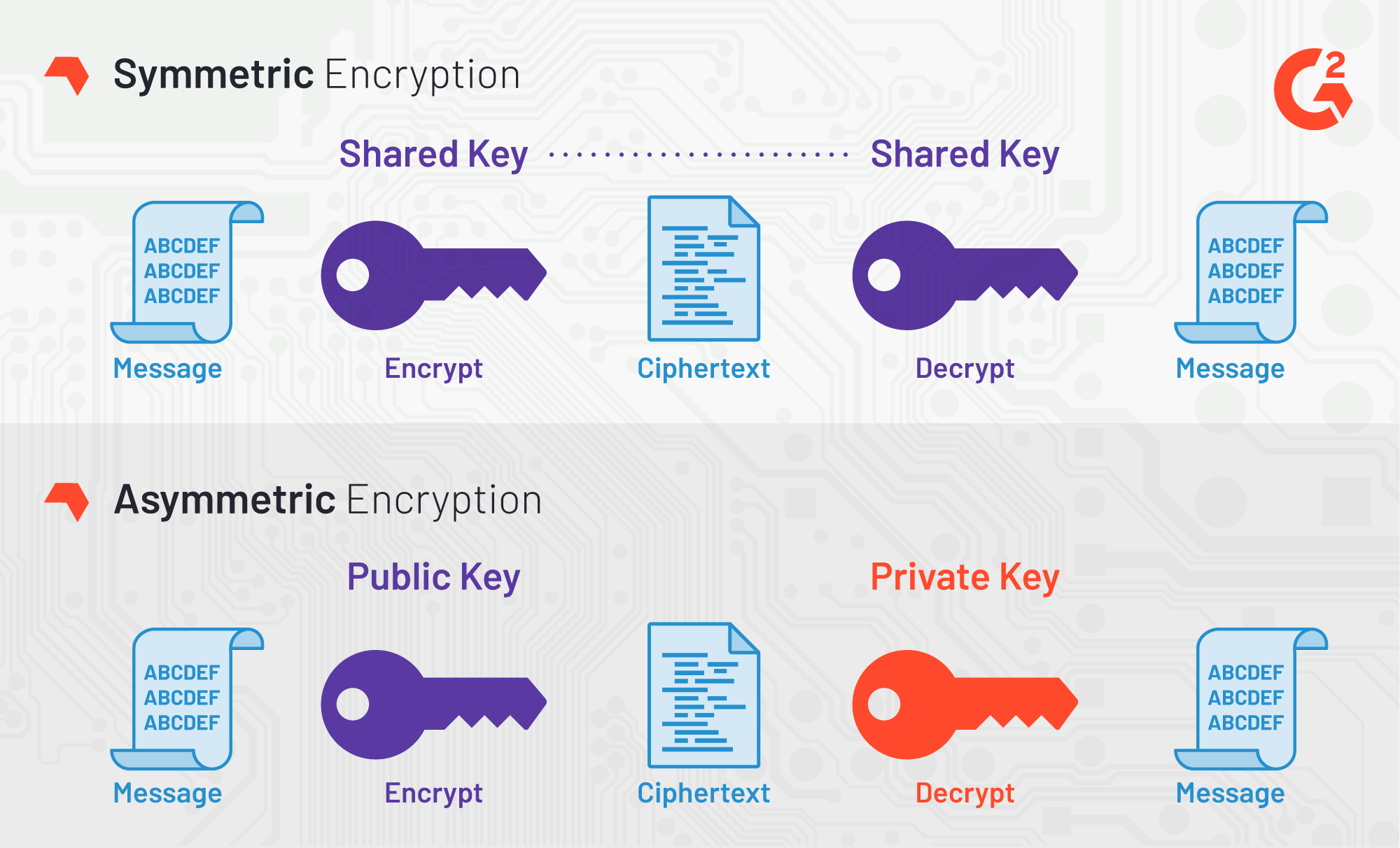
Symmetric Encryption Uses Public Or Private Key
Symmetric Encryption Uses Public Or Private Key -
I m doing a big migration from OpenDCIM to Netbox and I need migrate my device type images via API and I have not been able to find a way for doing this If this it s
I want to create an application for the phone from which it will be possible to attach images to racks How can I add images using REST API requests I thought the request
Symmetric Encryption Uses Public Or Private Key offer a wide array of printable material that is available online at no cost. They come in many forms, including worksheets, templates, coloring pages and many more. The great thing about Symmetric Encryption Uses Public Or Private Key lies in their versatility as well as accessibility.
More of Symmetric Encryption Uses Public Or Private Key
What Is Symmetric Key Cryptography Encryption Security Wiki

What Is Symmetric Key Cryptography Encryption Security Wiki
REST API NetBox s REST API powered by the Django REST Framework provides a robust yet accessible interface for creating modifying and deleting objects Employing HTTP for transfer
NetBox provides a powerful and comprehensive REST API that allows for programmatic interaction with all aspects of the platform This document describes the
Symmetric Encryption Uses Public Or Private Key have gained immense popularity because of a number of compelling causes:
-
Cost-Effective: They eliminate the requirement of buying physical copies or expensive software.
-
customization The Customization feature lets you tailor the templates to meet your individual needs be it designing invitations to organize your schedule or even decorating your house.
-
Educational Worth: Downloads of educational content for free cater to learners of all ages, which makes them a vital tool for teachers and parents.
-
Convenience: You have instant access an array of designs and templates, which saves time as well as effort.
Where to Find more Symmetric Encryption Uses Public Or Private Key
Encryption Choices Rsa Vs Aes Explained Prey

Encryption Choices Rsa Vs Aes Explained Prey
REST API Plugins can declare custom endpoints on NetBox s REST API to retrieve or manipulate models or other data These behave very similarly to views except that instead of
REST API Plugins can declare custom endpoints on NetBox s REST API to retrieve or manipulate models or other data These behave very similarly to views except that instead of
We hope we've stimulated your curiosity about Symmetric Encryption Uses Public Or Private Key We'll take a look around to see where you can discover these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide a variety of Symmetric Encryption Uses Public Or Private Key designed for a variety motives.
- Explore categories such as furniture, education, management, and craft.
2. Educational Platforms
- Forums and websites for education often offer free worksheets and worksheets for printing for flashcards, lessons, and worksheets. materials.
- Ideal for parents, teachers and students in need of additional resources.
3. Creative Blogs
- Many bloggers share their imaginative designs with templates and designs for free.
- The blogs covered cover a wide range of topics, that includes DIY projects to planning a party.
Maximizing Symmetric Encryption Uses Public Or Private Key
Here are some unique ways that you can make use of Symmetric Encryption Uses Public Or Private Key:
1. Home Decor
- Print and frame beautiful images, quotes, or even seasonal decorations to decorate your living areas.
2. Education
- Use printable worksheets from the internet for teaching at-home also in the classes.
3. Event Planning
- Make invitations, banners and decorations for special occasions such as weddings or birthdays.
4. Organization
- Keep track of your schedule with printable calendars along with lists of tasks, and meal planners.
Conclusion
Symmetric Encryption Uses Public Or Private Key are an abundance of practical and innovative resources which cater to a wide range of needs and desires. Their access and versatility makes them an essential part of each day life. Explore the many options of Symmetric Encryption Uses Public Or Private Key and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are Symmetric Encryption Uses Public Or Private Key really completely free?
- Yes you can! You can download and print these tools for free.
-
Can I make use of free printables to make commercial products?
- It's contingent upon the specific conditions of use. Always verify the guidelines provided by the creator before utilizing printables for commercial projects.
-
Are there any copyright issues when you download Symmetric Encryption Uses Public Or Private Key?
- Certain printables might have limitations on their use. Always read these terms and conditions as set out by the designer.
-
How can I print Symmetric Encryption Uses Public Or Private Key?
- Print them at home with either a printer at home or in any local print store for superior prints.
-
What program do I require to open printables for free?
- The majority are printed in the format PDF. This can be opened with free programs like Adobe Reader.
Public Key Cryptography Basics Site Reliability Engineering

Asymmetric Encryption How Asymmetric Encryption Works

Check more sample of Symmetric Encryption Uses Public Or Private Key below
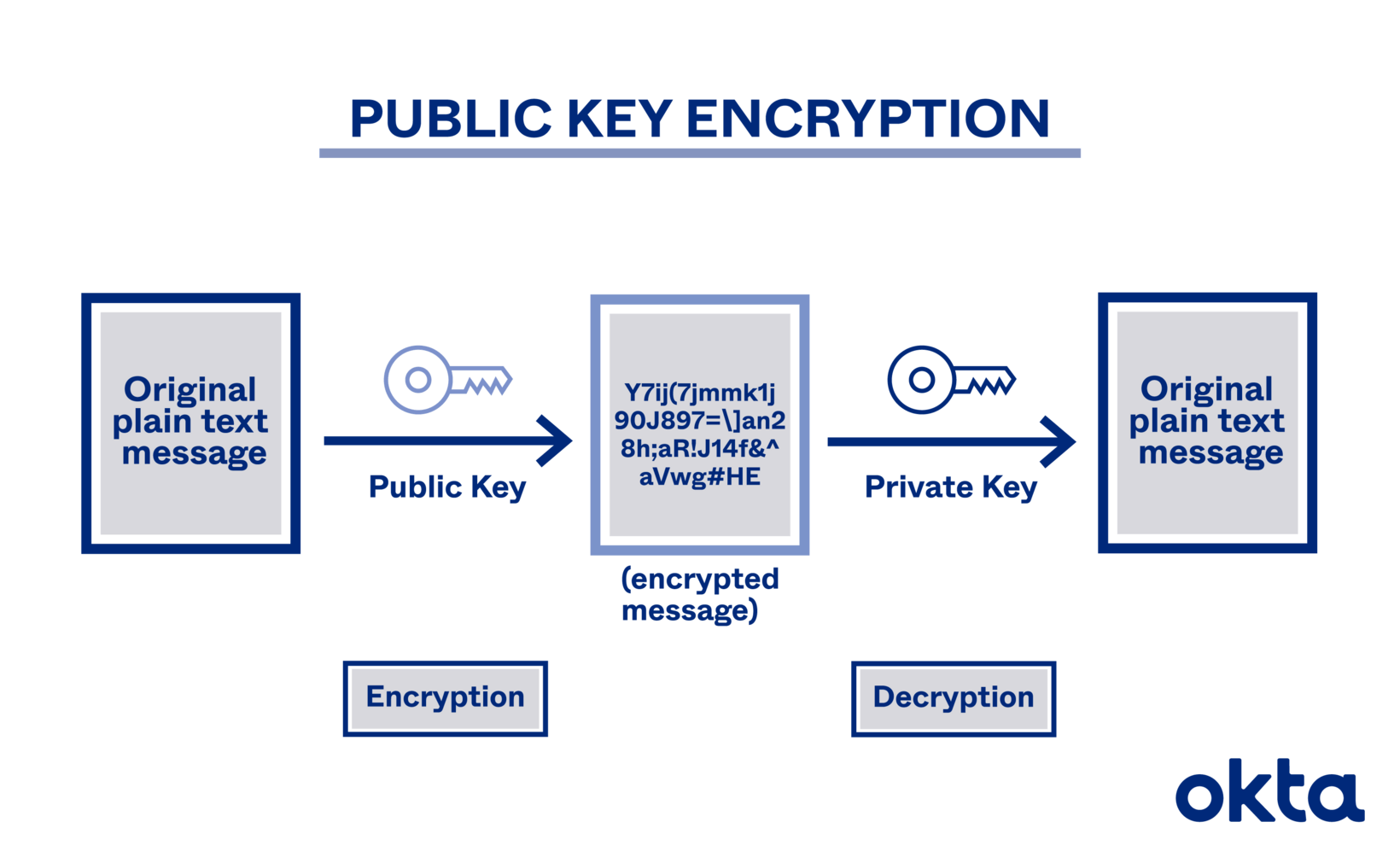
Public Key Encryption What Is Public Cryptography Okta
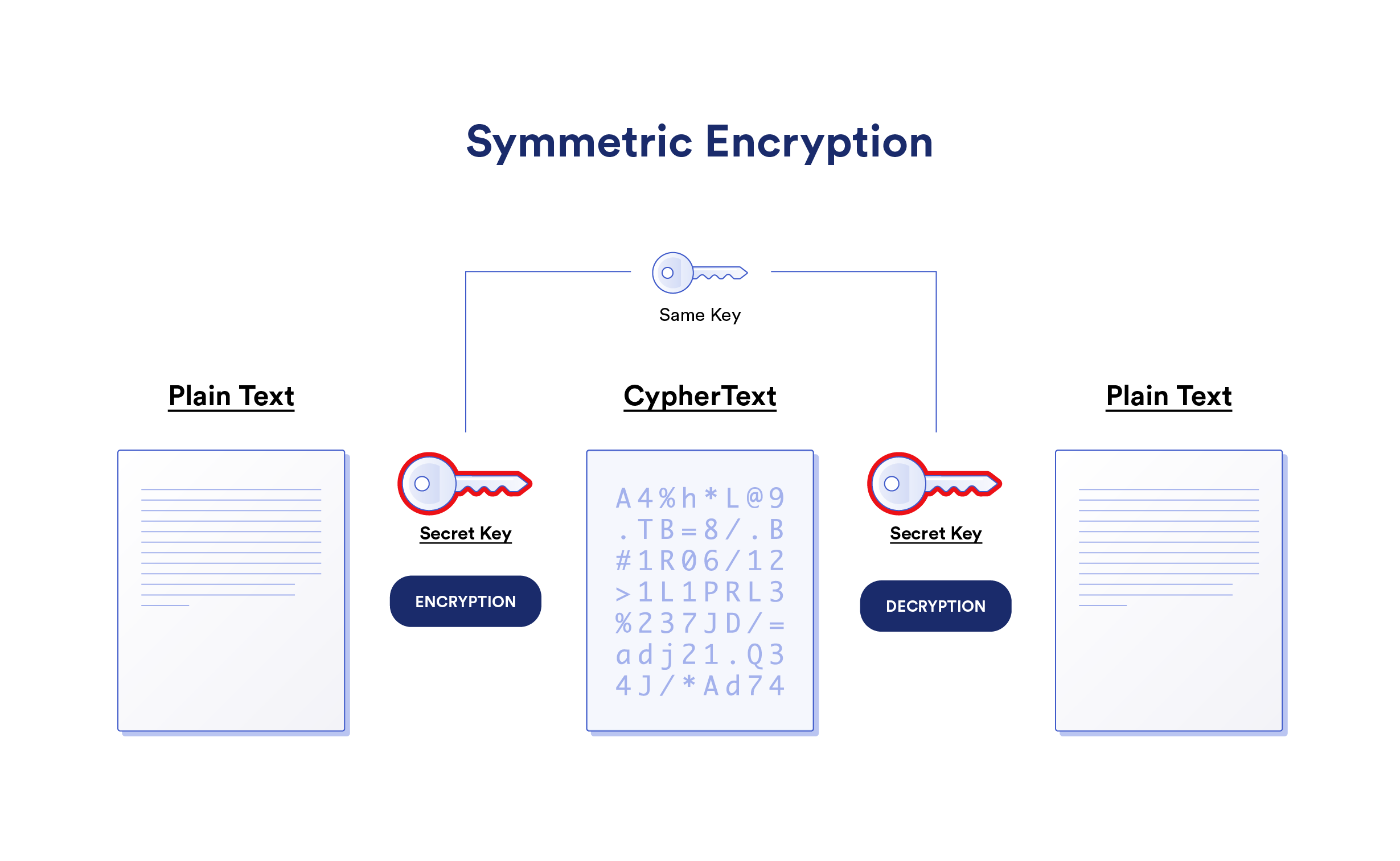
Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Asymmetric Encryption What It Is Why Your Security Depends On It

CoinStats What Is Zero Knowledge Encryption
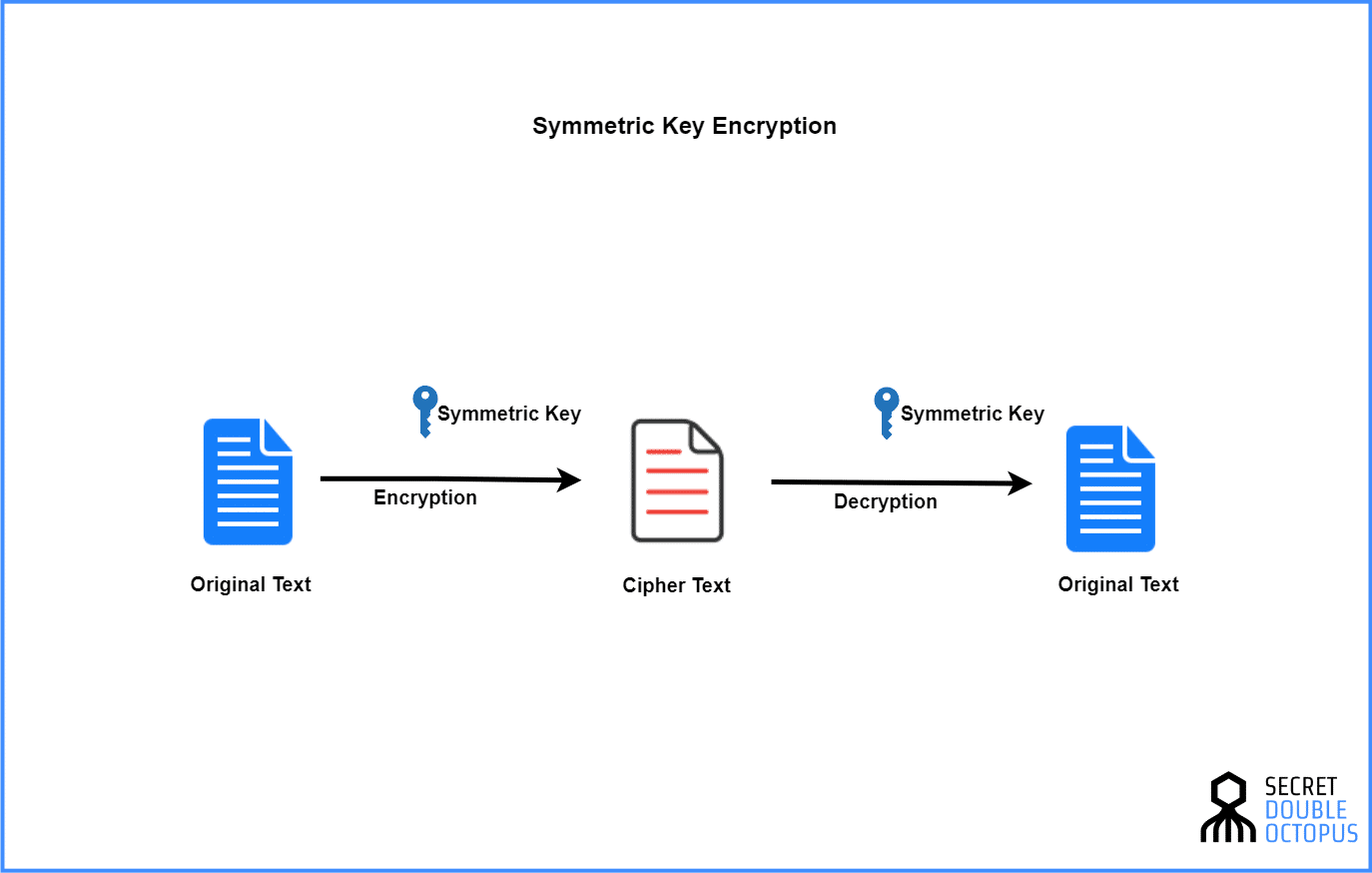
Symmetric Key Encryption Complete Guide To Symmetric Key Encryption

Symmetric Encryption Algorithms Live Long Encrypt Security Boulevard


https://github.com › netbox-community › netbox › discussions
I want to create an application for the phone from which it will be possible to attach images to racks How can I add images using REST API requests I thought the request
https://netboxlabs.com › docs › netbox › integrations › rest-api
Comprehensive interactive documentation of all REST API endpoints is available on a running NetBox instance at api schema swagger ui This interface provides a convenient sandbox for
I want to create an application for the phone from which it will be possible to attach images to racks How can I add images using REST API requests I thought the request
Comprehensive interactive documentation of all REST API endpoints is available on a running NetBox instance at api schema swagger ui This interface provides a convenient sandbox for

CoinStats What Is Zero Knowledge Encryption

Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023

Symmetric Key Encryption Complete Guide To Symmetric Key Encryption

Symmetric Encryption Algorithms Live Long Encrypt Security Boulevard

CARA KERJA PUBLIC KEY PRIVATE KEY DALAM ENKRIPSI ASIMETRIS SERTIFIKAT

Asymmetric Encryption How Asymmetric Encryption Works

Asymmetric Encryption How Asymmetric Encryption Works
What Does Encryption Mean And Why Is It Important