In the age of digital, with screens dominating our lives, the charm of tangible, printed materials hasn't diminished. Be it for educational use project ideas, artistic or just adding personal touches to your area, Ssh Key Exchange Algorithms List are now an essential resource. The following article is a dive through the vast world of "Ssh Key Exchange Algorithms List," exploring their purpose, where you can find them, and how they can be used to enhance different aspects of your life.
Get Latest Ssh Key Exchange Algorithms List Below
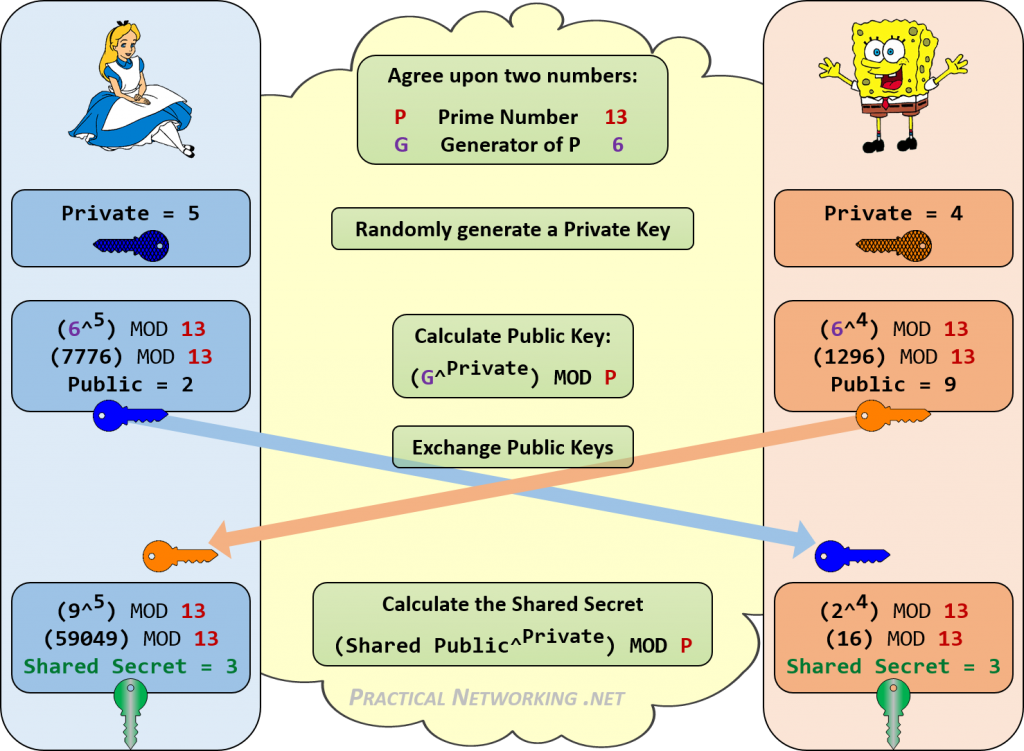
Ssh Key Exchange Algorithms List
Ssh Key Exchange Algorithms List -
COMMAND PID USER FD TYPE DEVICE SIZE OFF NODE NAME ssh 8492 me 3u IPv4 0x9fdfe6f804b4a45d 0t0 TCP vpnhost example 59464 remotehost ssh
SO during run time also I was unable to create the ssh known hosts file If you face the similar issue then see if you can write the known hosts file in the tmp location This is mostly write
Printables for free include a vast selection of printable and downloadable materials available online at no cost. These materials come in a variety of formats, such as worksheets, templates, coloring pages, and much more. The benefit of Ssh Key Exchange Algorithms List lies in their versatility and accessibility.
More of Ssh Key Exchange Algorithms List
Weak Key Exchange Algorithm Diffie hellman group14 sha1 Is Enabled By

Weak Key Exchange Algorithm Diffie hellman group14 sha1 Is Enabled By
If you can connect to the original client host via SSH then you can use the scp command to copy the file An example session could look something like this barry earth
Ssh has the i option to tell which private key file to use when authenticating i identity file Selects a file from which the identity private key for RSA or DSA authentication is read
Ssh Key Exchange Algorithms List have garnered immense recognition for a variety of compelling motives:
-
Cost-Efficiency: They eliminate the need to buy physical copies or expensive software.
-
Customization: We can customize print-ready templates to your specific requirements when it comes to designing invitations planning your schedule or decorating your home.
-
Educational value: Downloads of educational content for free cater to learners of all ages, making them a great tool for parents and educators.
-
Easy to use: Access to various designs and templates saves time and effort.
Where to Find more Ssh Key Exchange Algorithms List
SFTP Files
SFTP Files
However I suffered from the SSH tunnel being closed due to inactivity depsite the ssh process staying up This can easily be overcome by having the client in my case the VPS ping the
The SSH keys and configuration file reside in C ProgramData ssh which is a hidden folder The default shell used by SSH is the Windows command shell This needs to
Now that we've ignited your interest in Ssh Key Exchange Algorithms List Let's take a look at where the hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy provide a large collection in Ssh Key Exchange Algorithms List for different goals.
- Explore categories such as decorating your home, education, craft, and organization.
2. Educational Platforms
- Educational websites and forums often provide free printable worksheets with flashcards and other teaching tools.
- This is a great resource for parents, teachers as well as students who require additional resources.
3. Creative Blogs
- Many bloggers provide their inventive designs and templates for free.
- These blogs cover a broad array of topics, ranging that includes DIY projects to planning a party.
Maximizing Ssh Key Exchange Algorithms List
Here are some unique ways of making the most of printables that are free:
1. Home Decor
- Print and frame gorgeous images, quotes, or even seasonal decorations to decorate your living spaces.
2. Education
- Print out free worksheets and activities to reinforce learning at home, or even in the classroom.
3. Event Planning
- Design invitations, banners as well as decorations for special occasions like birthdays and weddings.
4. Organization
- Stay organized with printable calendars checklists for tasks, as well as meal planners.
Conclusion
Ssh Key Exchange Algorithms List are a treasure trove of creative and practical resources for a variety of needs and passions. Their accessibility and flexibility make these printables a useful addition to each day life. Explore the vast collection that is Ssh Key Exchange Algorithms List today, and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are Ssh Key Exchange Algorithms List truly are they free?
- Yes they are! You can download and print these free resources for no cost.
-
Do I have the right to use free printables for commercial uses?
- It's determined by the specific conditions of use. Always verify the guidelines provided by the creator before using printables for commercial projects.
-
Are there any copyright issues with printables that are free?
- Some printables could have limitations in their usage. Check the terms of service and conditions provided by the creator.
-
How do I print printables for free?
- Print them at home with a printer or visit the local print shop for the highest quality prints.
-
What program will I need to access printables for free?
- Most PDF-based printables are available in the format PDF. This can be opened using free software such as Adobe Reader.
Sieben Behaupten Ihr Mac Generate Rsa Key Unmittelbar Bevorstehend
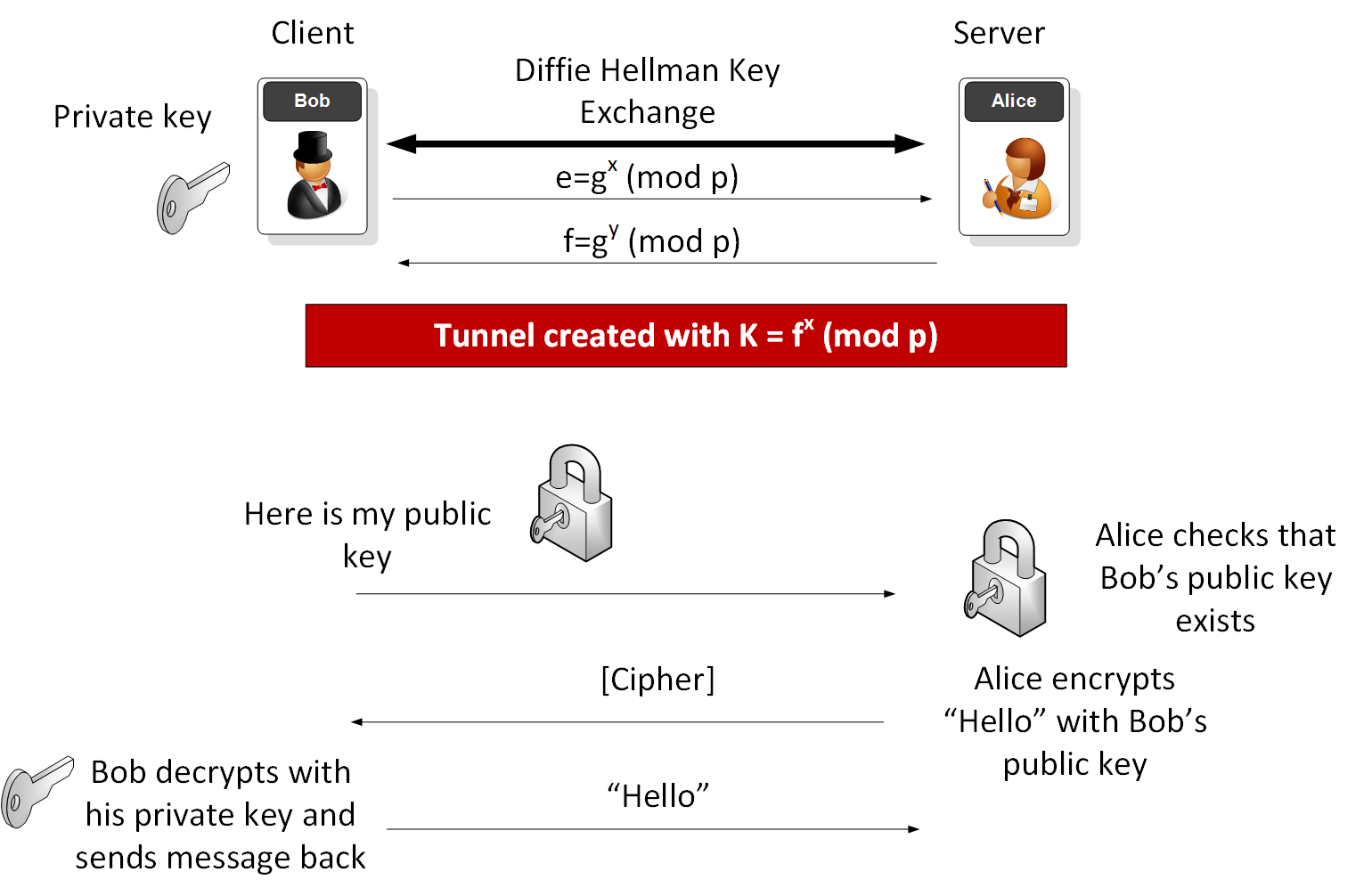
The Diffie Hellman Key Exchange Protocol 21 Download Scientific

Check more sample of Ssh Key Exchange Algorithms List below
SSH Weak MAC Algorithms Enabled In InterScan Messaging Security
SSH ssh
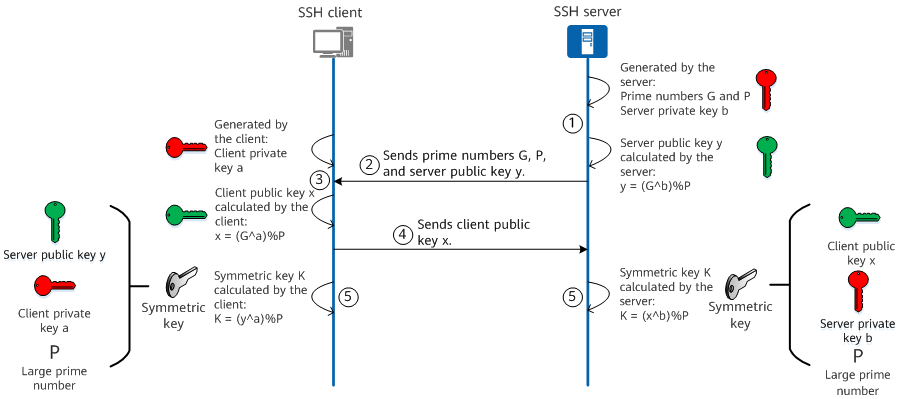
Public Key Cryptography Algorithms

Comparing SSH Keys RSA DSA ECDSA Or EdDSA
SSH Weak Key Exchange Algorithms Enabled Virtue Security

Bitvise SSH The SSH Session Has Terminated With Error


https://superuser.com › questions
SO during run time also I was unable to create the ssh known hosts file If you face the similar issue then see if you can write the known hosts file in the tmp location This is mostly write

https://superuser.com › questions
Stack Exchange Network Stack Exchange network consists of 183 Q A communities including Stack Overflow the largest most trusted online community for
SO during run time also I was unable to create the ssh known hosts file If you face the similar issue then see if you can write the known hosts file in the tmp location This is mostly write
Stack Exchange Network Stack Exchange network consists of 183 Q A communities including Stack Overflow the largest most trusted online community for

Comparing SSH Keys RSA DSA ECDSA Or EdDSA

SSH ssh

SSH Weak Key Exchange Algorithms Enabled Virtue Security

Bitvise SSH The SSH Session Has Terminated With Error
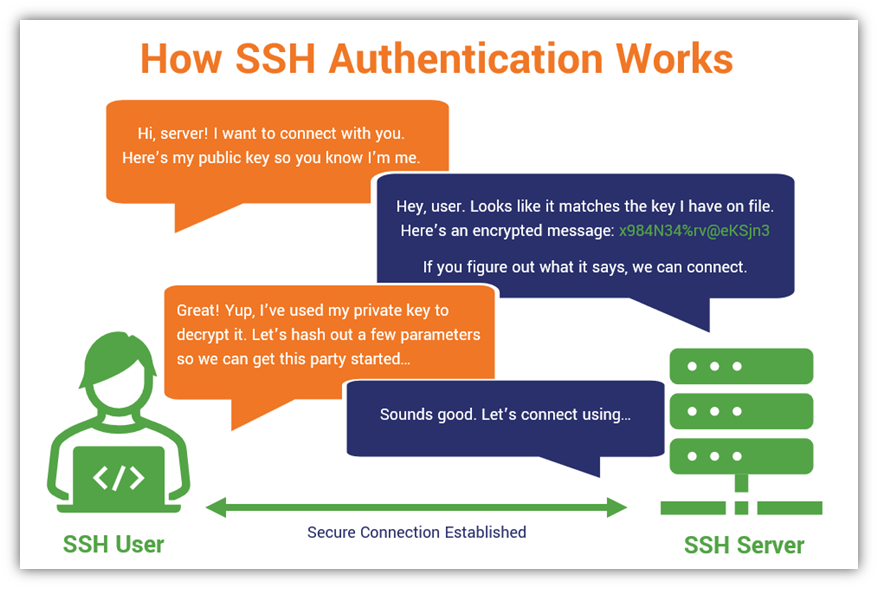
How To Use Ssh Key For Git Pull

Common Encryption Types Protocols And Algorithms Expl Vrogue co

Common Encryption Types Protocols And Algorithms Expl Vrogue co
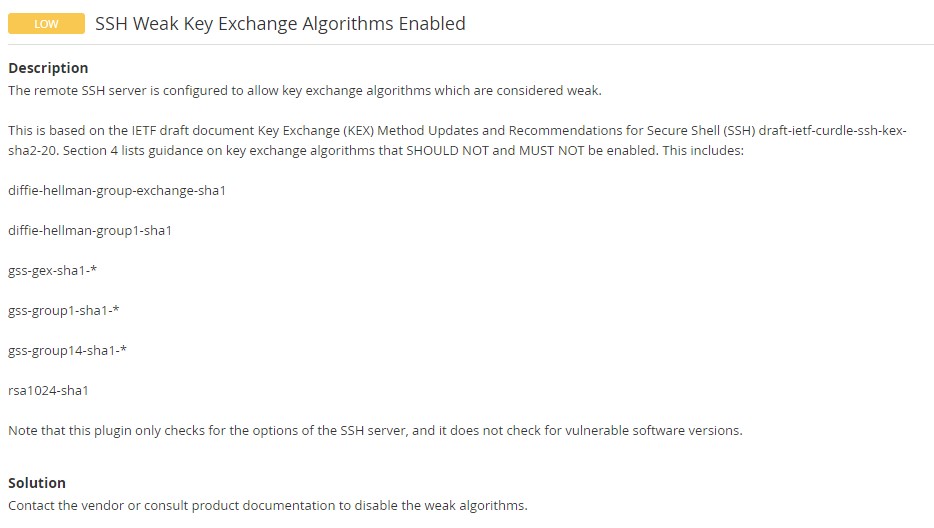
Disable Weak Key Exchange Algorithm CBC Mode In SSH Techglimpse