In this day and age with screens dominating our lives it's no wonder that the appeal of tangible, printed materials hasn't diminished. Whether it's for educational purposes such as creative projects or simply adding an individual touch to the area, Rsa Encryption And Decryption Example are now a vital source. This article will take a dive in the world of "Rsa Encryption And Decryption Example," exploring their purpose, where they are, and how they can enhance various aspects of your life.
What Are Rsa Encryption And Decryption Example?
Rsa Encryption And Decryption Example cover a large range of downloadable, printable materials online, at no cost. They are available in numerous kinds, including worksheets templates, coloring pages, and many more. The great thing about Rsa Encryption And Decryption Example lies in their versatility as well as accessibility.
Rsa Encryption And Decryption Example

Rsa Encryption And Decryption Example
Rsa Encryption And Decryption Example -
[desc-5]
[desc-1]
How To Solve AES Decryption Example AES Decryption Example Solved
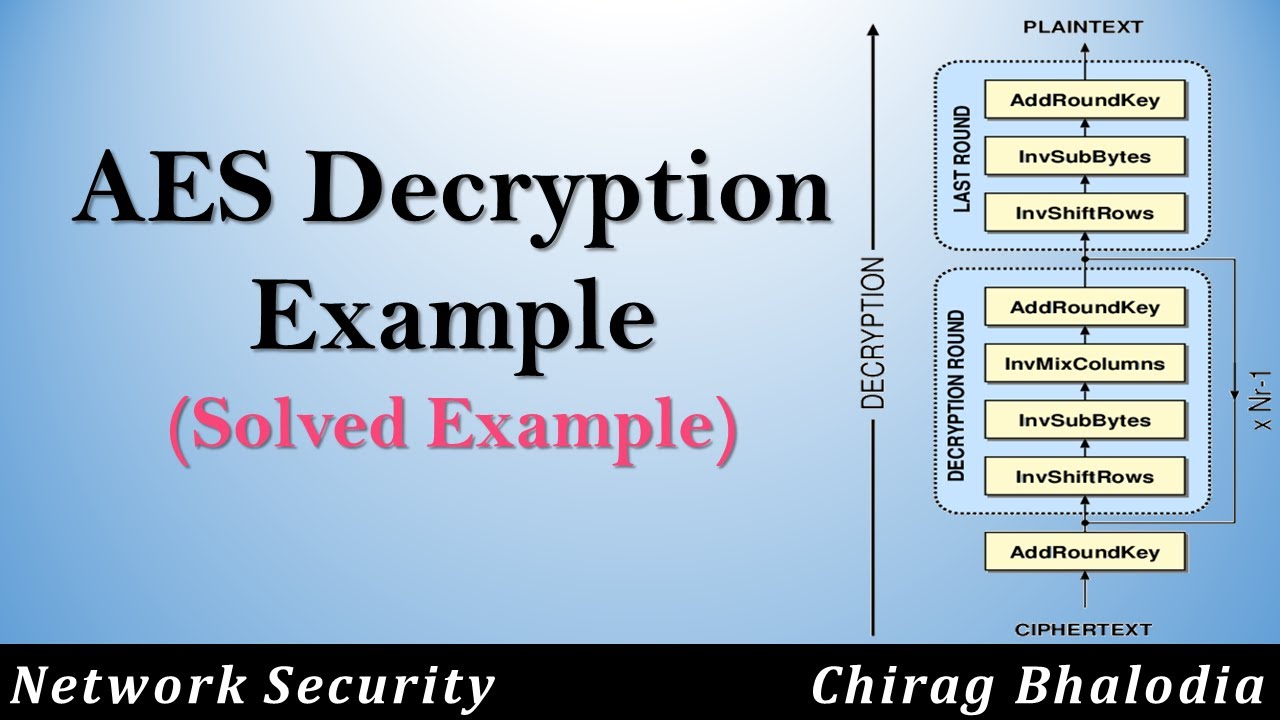
How To Solve AES Decryption Example AES Decryption Example Solved
[desc-4]
[desc-6]
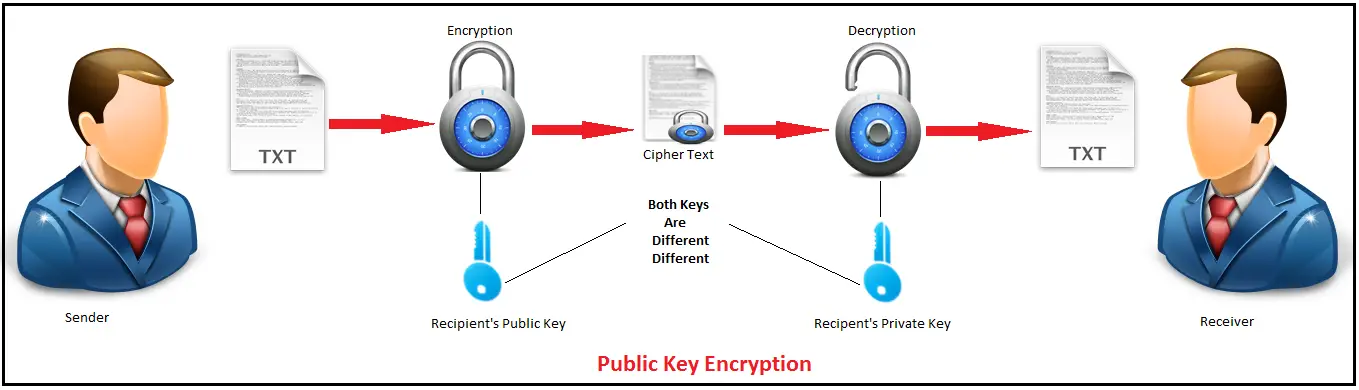
RSA Encryption System

RSA Encryption System
[desc-9]
[desc-7]
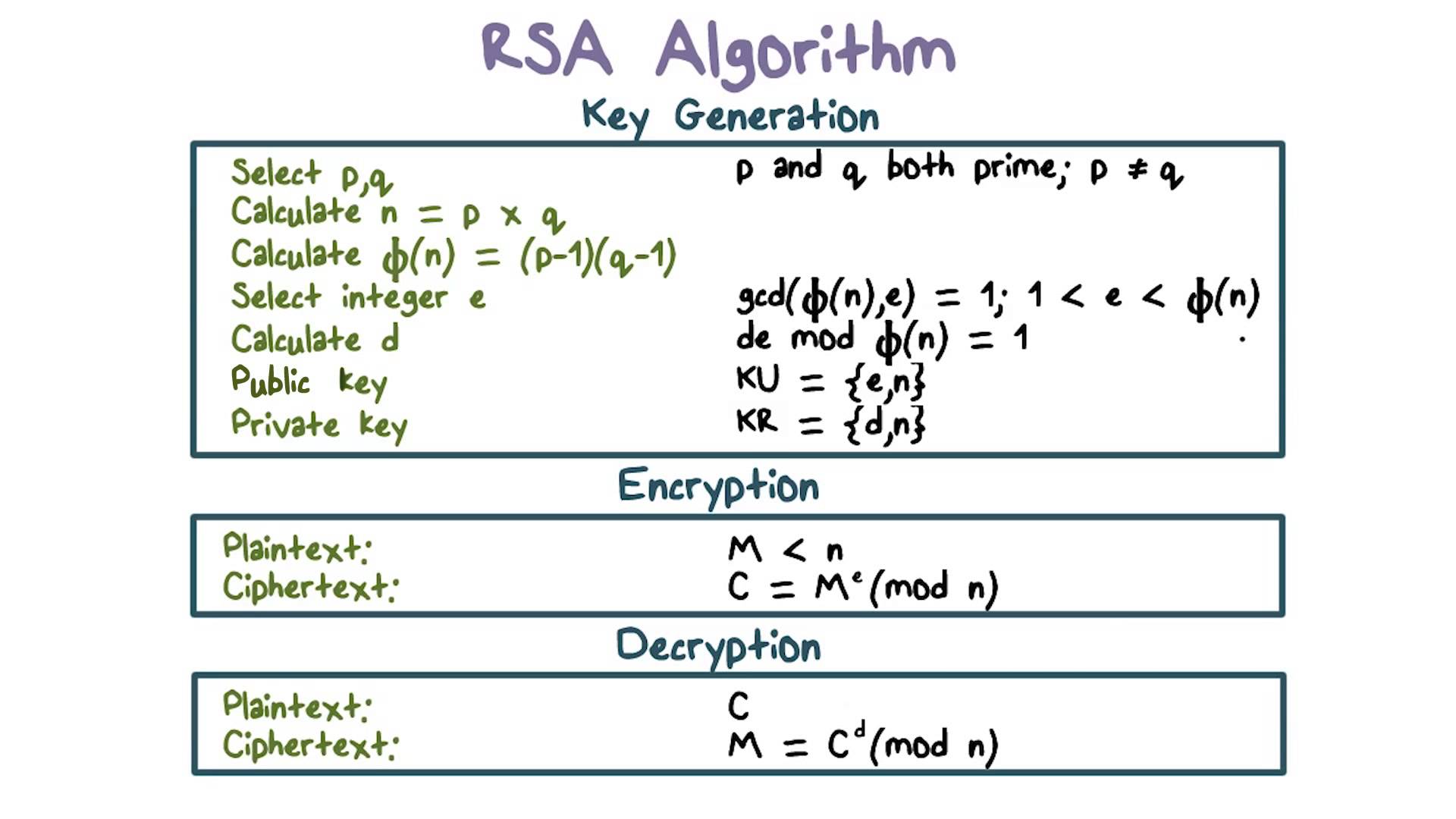
Des Rsa Encryption Cheat Sheet
RSA Algorithm In C And C Encryption And Decryption

How To Perform AES Encryption In NET

TLS Essentials 3 Confidentiality With AES RSA Hybrid Encryption

Schematic Diagram Of The RSA Algorithm Encryption And Decryption And
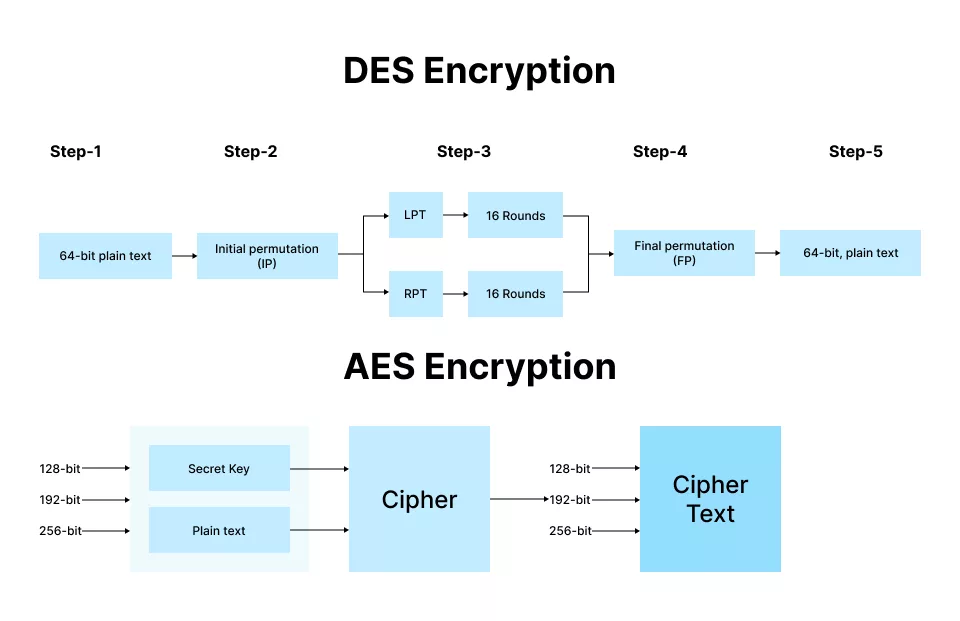
RSA Vs AES Encryption Know Key Differences

RSA Vs AES Encryption Know Key Differences

What Is Asymmetric Encryption How Does It Work InfoSec Insights