In this age of electronic devices, where screens rule our lives it's no wonder that the appeal of tangible, printed materials hasn't diminished. It doesn't matter if it's for educational reasons in creative or artistic projects, or simply to add a personal touch to your space, Public Key Encryption In Network Security are now an essential source. For this piece, we'll take a dive through the vast world of "Public Key Encryption In Network Security," exploring what they are, where to locate them, and how they can improve various aspects of your lives.
Get Latest Public Key Encryption In Network Security Below
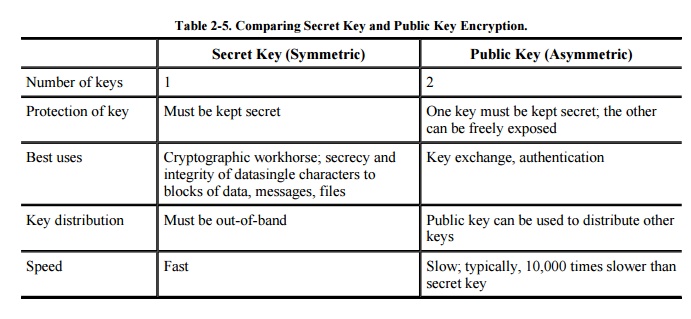
Public Key Encryption In Network Security
Public Key Encryption In Network Security -
gadgets gaming Public Blog
Public Public
Public Key Encryption In Network Security include a broad array of printable materials that are accessible online for free cost. These printables come in different forms, like worksheets coloring pages, templates and many more. The attraction of printables that are free is in their versatility and accessibility.
More of Public Key Encryption In Network Security
Cryptography JessicaLetitia

Cryptography JessicaLetitia
Public Outlet 1 000 smartphones wearables
iRepair Public 20 Public Online
Print-friendly freebies have gained tremendous popularity for several compelling reasons:
-
Cost-Efficiency: They eliminate the need to buy physical copies or costly software.
-
customization: There is the possibility of tailoring the templates to meet your individual needs, whether it's designing invitations making your schedule, or even decorating your home.
-
Educational Value Education-related printables at no charge can be used by students from all ages, making these printables a powerful aid for parents as well as educators.
-
Accessibility: Quick access to numerous designs and templates can save you time and energy.
Where to Find more Public Key Encryption In Network Security
Encryption Choices Rsa Vs Aes Explained Prey

Encryption Choices Rsa Vs Aes Explained Prey
To Public smartphones Public smartphone
gaming Public 1300 games PC PS5 PS4 Xbox One Nintendo Switch Nintendo 3DS 2DS mouse keyboards
We hope we've stimulated your curiosity about Public Key Encryption In Network Security we'll explore the places you can discover these hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy offer a huge selection of Public Key Encryption In Network Security suitable for many objectives.
- Explore categories such as the home, decor, management, and craft.
2. Educational Platforms
- Educational websites and forums often provide worksheets that can be printed for free as well as flashcards and other learning tools.
- Ideal for parents, teachers as well as students searching for supplementary sources.
3. Creative Blogs
- Many bloggers share their creative designs as well as templates for free.
- These blogs cover a broad selection of subjects, everything from DIY projects to planning a party.
Maximizing Public Key Encryption In Network Security
Here are some unique ways create the maximum value use of printables for free:
1. Home Decor
- Print and frame beautiful images, quotes, as well as seasonal decorations, to embellish your living spaces.
2. Education
- Use printable worksheets for free to aid in learning at your home, or even in the classroom.
3. Event Planning
- Design invitations for banners, invitations as well as decorations for special occasions such as weddings or birthdays.
4. Organization
- Get organized with printable calendars with to-do lists, planners, and meal planners.
Conclusion
Public Key Encryption In Network Security are an abundance with useful and creative ideas that cater to various needs and needs and. Their accessibility and flexibility make these printables a useful addition to each day life. Explore the world of Public Key Encryption In Network Security today to explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables for free really available for download?
- Yes they are! You can download and print these documents for free.
-
Does it allow me to use free printouts for commercial usage?
- It is contingent on the specific conditions of use. Always consult the author's guidelines prior to printing printables for commercial projects.
-
Do you have any copyright violations with Public Key Encryption In Network Security?
- Certain printables may be subject to restrictions regarding usage. Make sure you read the terms and condition of use as provided by the author.
-
How do I print Public Key Encryption In Network Security?
- Print them at home using either a printer at home or in an area print shop for premium prints.
-
What program do I need to run printables that are free?
- The majority of printables are in PDF format. These can be opened with free software like Adobe Reader.
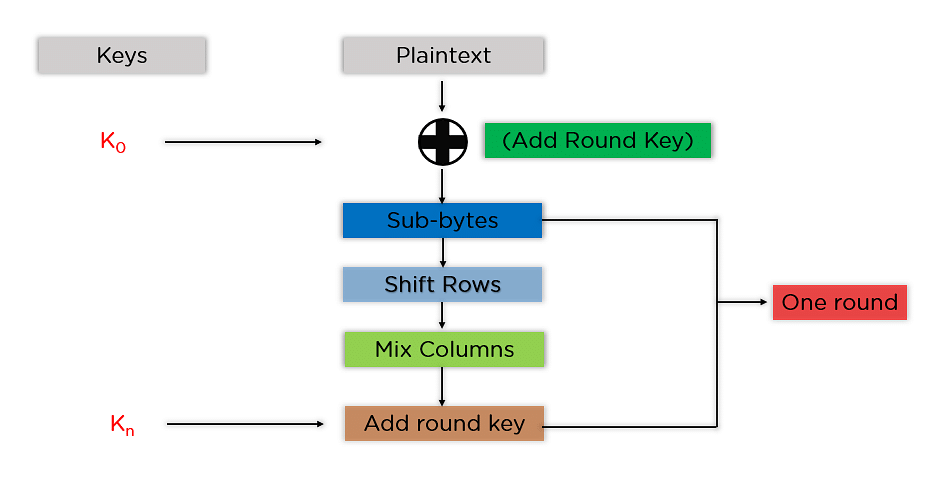
How Public Key Encryption Ensures Data Integrity

Encryption And Decryption Jean s Blog

Check more sample of Public Key Encryption In Network Security below
What Is Symmetric Key Cryptography Encryption Security Wiki

Pgp Files
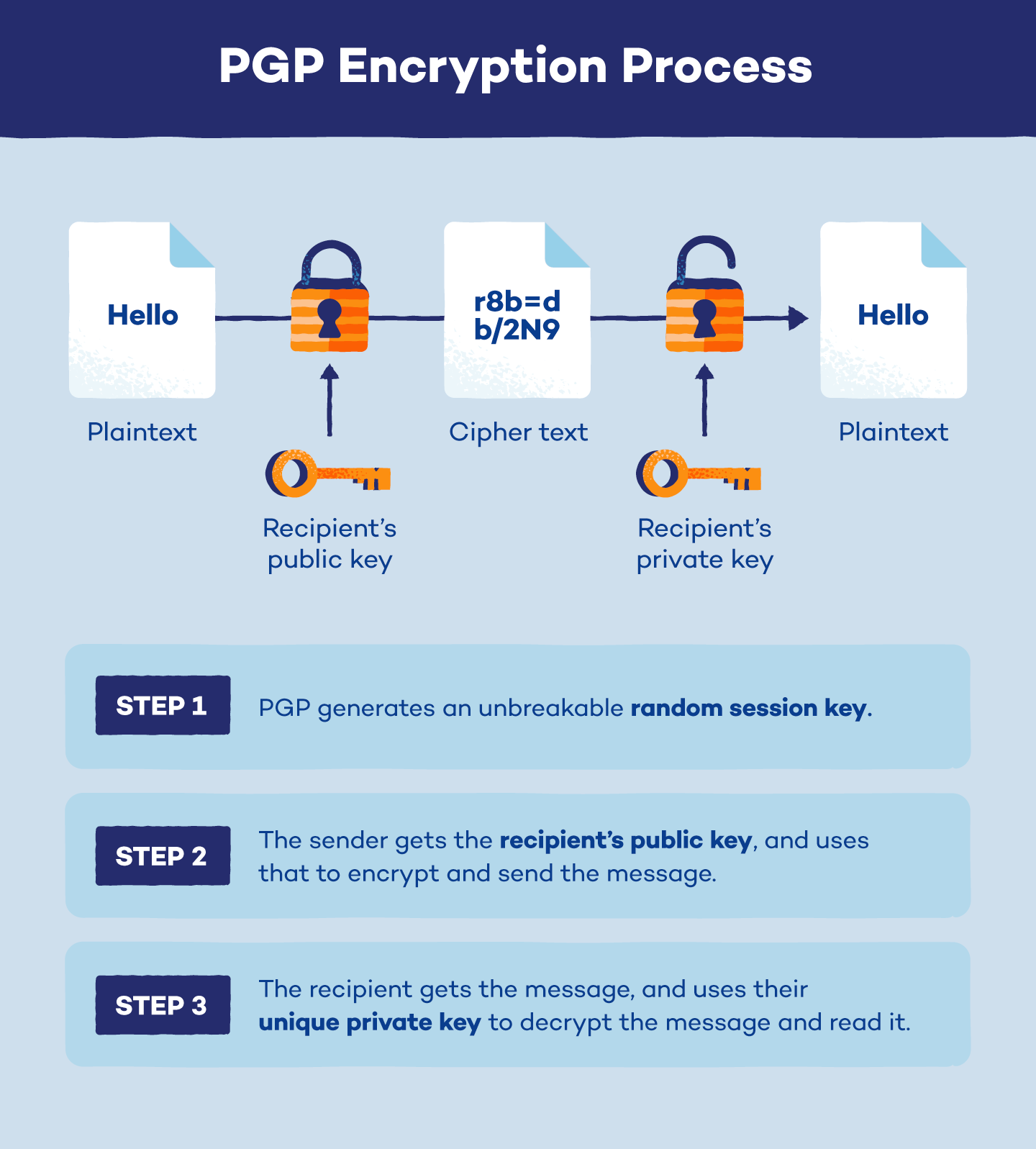
What Is Identity Based Encryption IBE
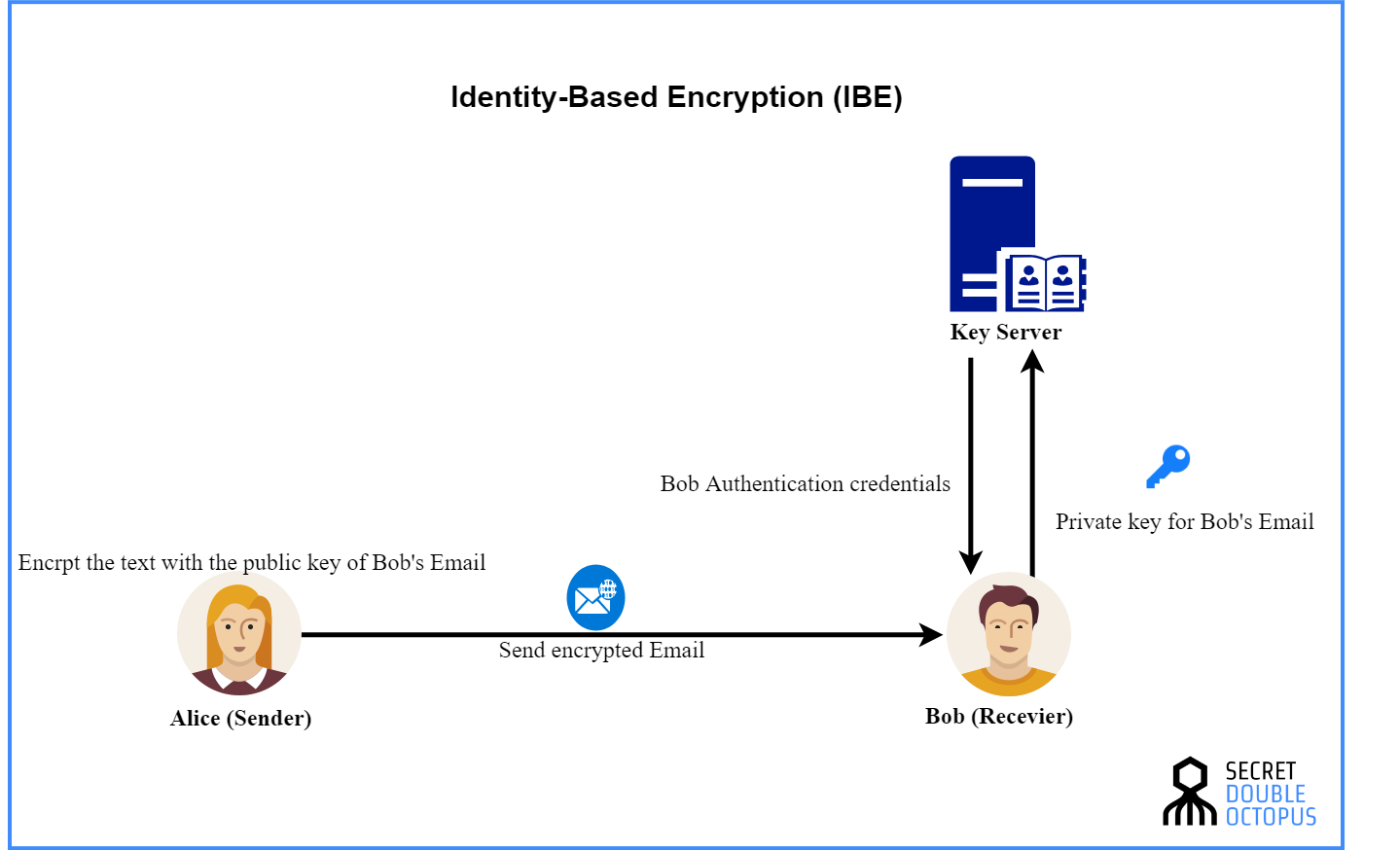
Advantages And Disadvantages Of PGP Encryption UseMyNotes
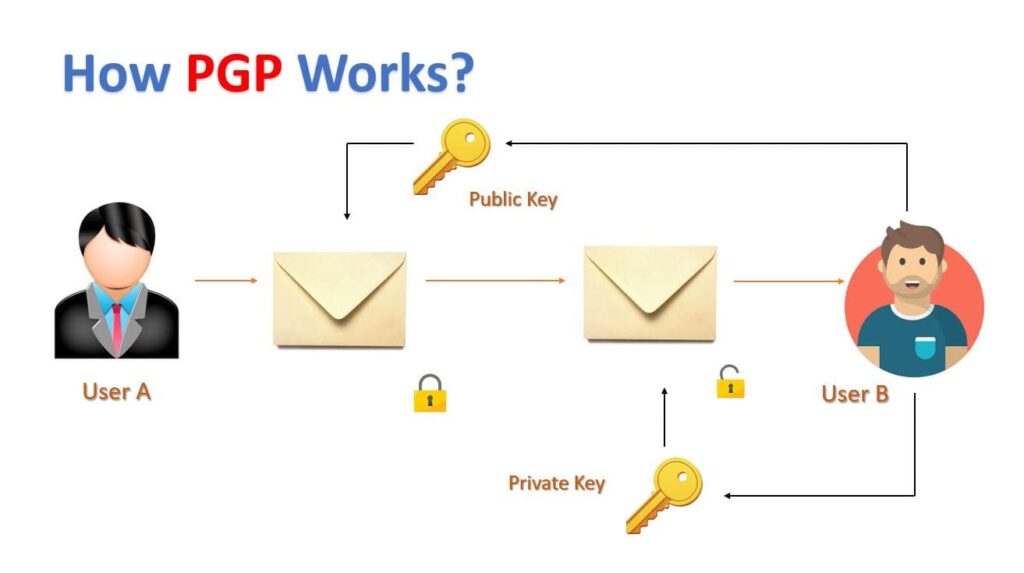
RSA Algorithm Secure Your Data With Public Key Encryption
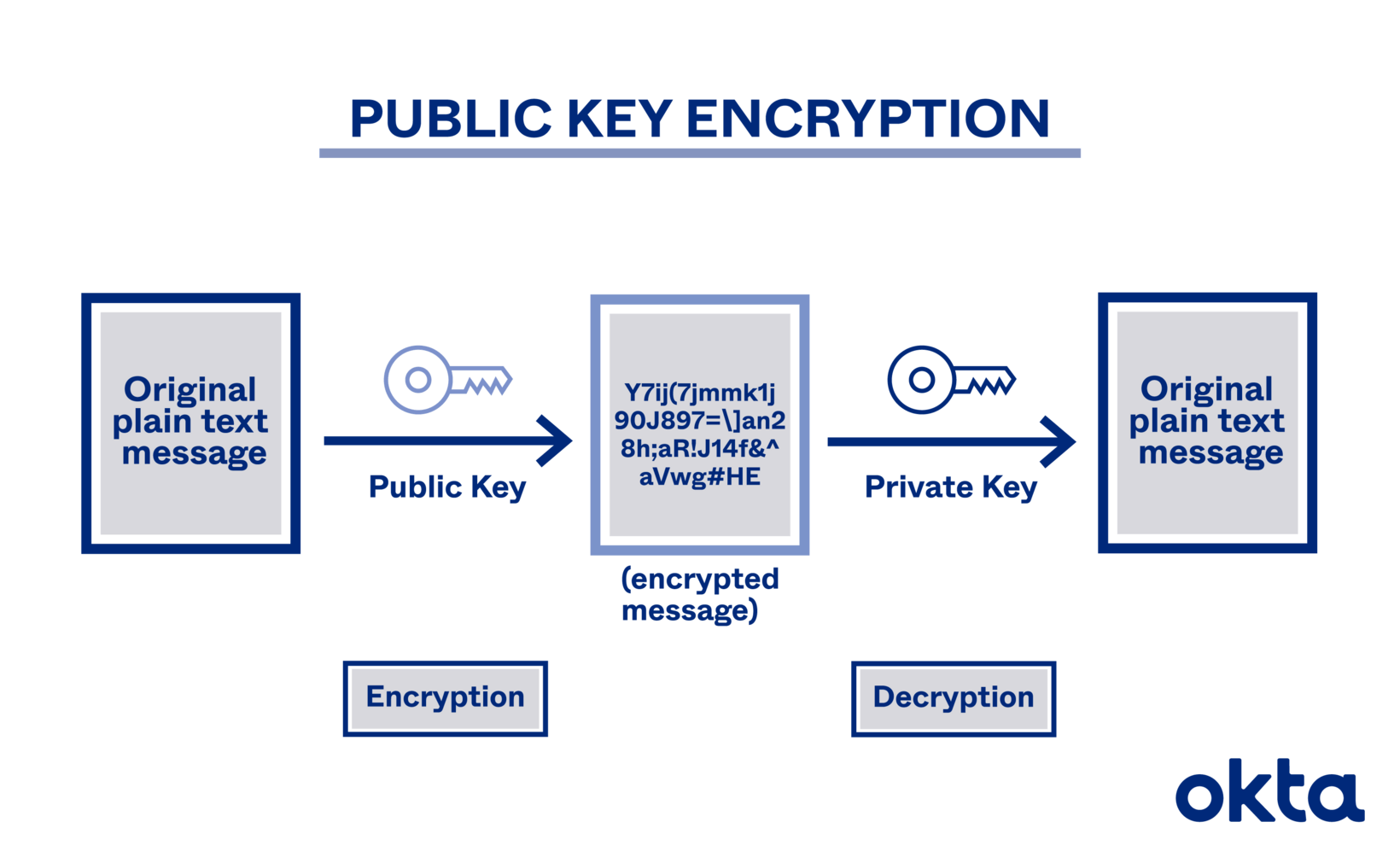
Public Key Encryption What Is Public Cryptography Okta


Public Public
Public Entertainment online

Advantages And Disadvantages Of PGP Encryption UseMyNotes

Pgp Files

RSA Algorithm Secure Your Data With Public Key Encryption

Public Key Encryption What Is Public Cryptography Okta

UNIT II NETWORK SECURITY AND CRYPTOGRAPHY

Public Key Cryptography Decoded What Is Cryptography Ntirawen

Public Key Cryptography Decoded What Is Cryptography Ntirawen
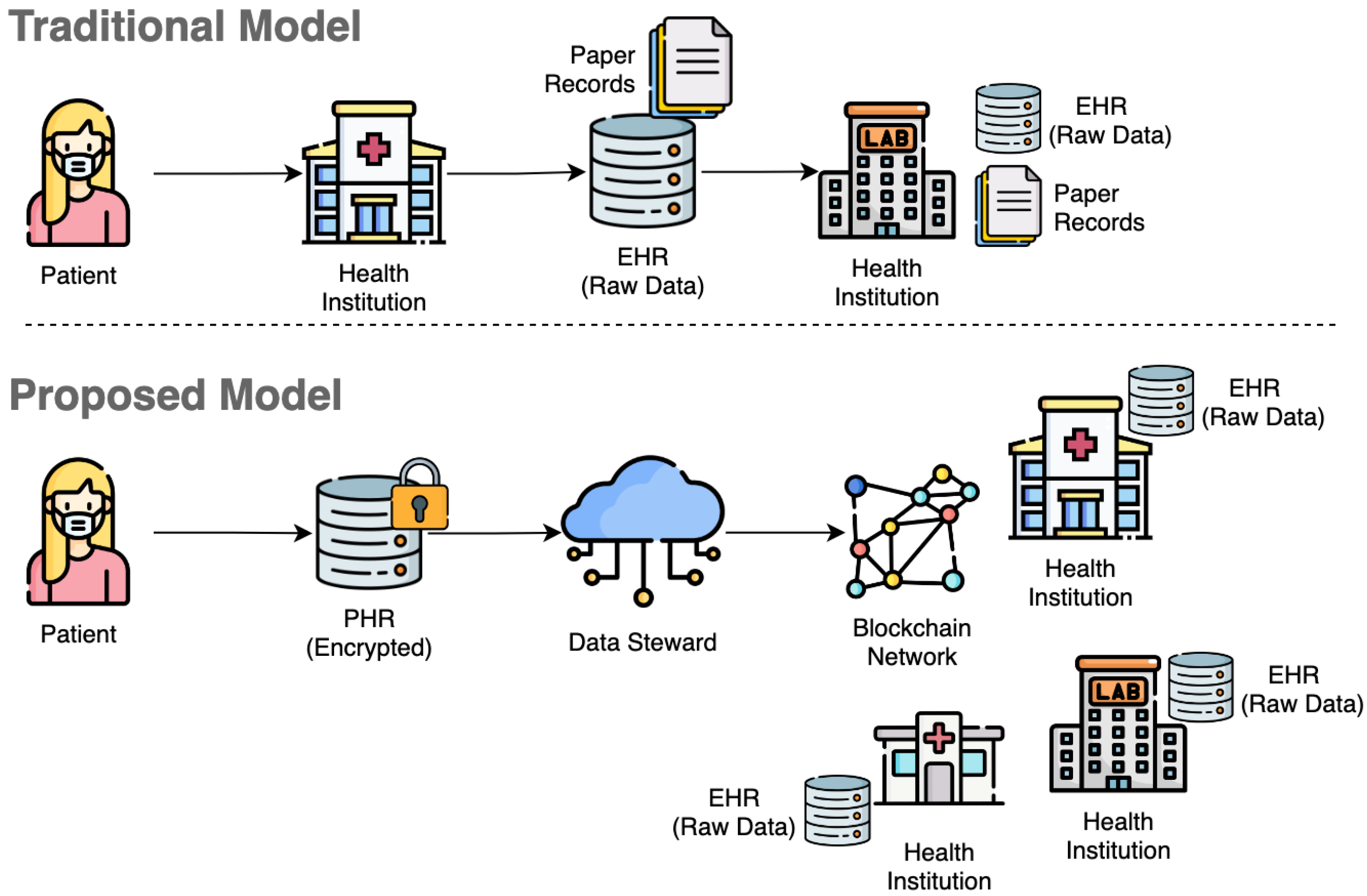
Sensors Free Full Text A Blockchain Based End to End Data