In the age of digital, where screens have become the dominant feature of our lives The appeal of tangible printed materials isn't diminishing. Be it for educational use, creative projects, or just adding a personal touch to your space, Public Key Encryption Example Code are now an essential source. For this piece, we'll dive to the depths of "Public Key Encryption Example Code," exploring the different types of printables, where to find them and ways they can help you improve many aspects of your lives.
Get Latest Public Key Encryption Example Code Below
Public Key Encryption Example Code
Public Key Encryption Example Code -
Bonjour Voici mon adresse courriel avec laquelle je me connecte compte Public Mobile mxxxxxxxxxxxx et num ro de t l phone associ s au compte 5xxxxxxxxx
Paid money mistakenly to telus integrated communications and want a refund but Public Mobile Telus in Get Support an hour ago Please fix your website my account doesnt
Public Key Encryption Example Code cover a large collection of printable materials available online at no cost. They come in many forms, like worksheets coloring pages, templates and much more. The appeal of printables for free is their versatility and accessibility.
More of Public Key Encryption Example Code
The Ultimate Guide To Symmetric Encryption
The Ultimate Guide To Symmetric Encryption
Paid money mistakenly to telus integrated communications and want a refund but Public Mobile Telus in Get Support 2 hours ago Please fix your website my account doesnt
Hey Community We are excited to announce that starting today we re introducing eSIM availability to both new and existing subscribers along with the rollout of multiple
Public Key Encryption Example Code have garnered immense recognition for a variety of compelling motives:
-
Cost-Effective: They eliminate the need to buy physical copies of the software or expensive hardware.
-
customization: The Customization feature lets you tailor printing templates to your own specific requirements whether it's making invitations and schedules, or decorating your home.
-
Educational Impact: Education-related printables at no charge can be used by students from all ages, making them an invaluable instrument for parents and teachers.
-
Accessibility: You have instant access various designs and templates saves time and effort.
Where to Find more Public Key Encryption Example Code
A Perfect Guide On What Are Public And Private Keys TECHNOLOGY NYOOOZ
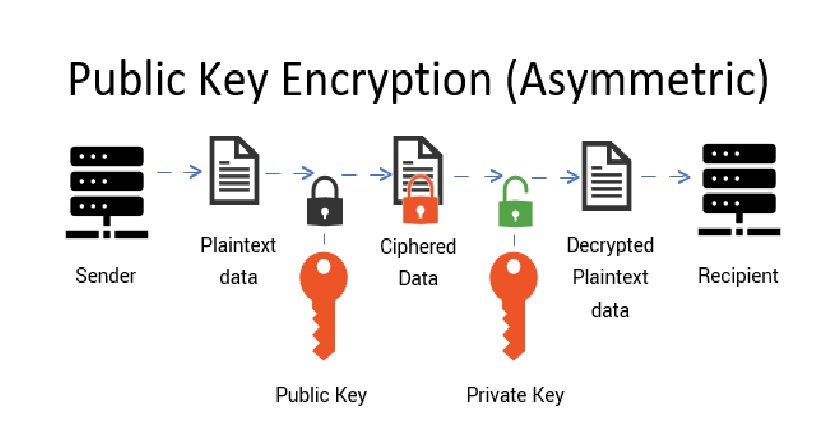
A Perfect Guide On What Are Public And Private Keys TECHNOLOGY NYOOOZ
I realized that I have to change credit cards on my plan as I changed cards and my service stopped at my plan renewal date yesterday However when I try to log in to self
You will be required to login to your Public Mobile Community Account to contact CS Agent Once you are finished making the ticket with CS Agent please ensure that you monitor for
We've now piqued your interest in Public Key Encryption Example Code Let's find out where the hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a variety with Public Key Encryption Example Code for all objectives.
- Explore categories like interior decor, education, organizing, and crafts.
2. Educational Platforms
- Forums and educational websites often provide worksheets that can be printed for free including flashcards, learning materials.
- Ideal for teachers, parents and students looking for extra resources.
3. Creative Blogs
- Many bloggers provide their inventive designs and templates, which are free.
- These blogs cover a broad range of interests, ranging from DIY projects to party planning.
Maximizing Public Key Encryption Example Code
Here are some creative ways how you could make the most use of Public Key Encryption Example Code:
1. Home Decor
- Print and frame stunning images, quotes, or festive decorations to decorate your living spaces.
2. Education
- Use printable worksheets from the internet to enhance your learning at home or in the classroom.
3. Event Planning
- Design invitations and banners and decorations for special occasions such as weddings, birthdays, and other special occasions.
4. Organization
- Stay organized with printable planners checklists for tasks, as well as meal planners.
Conclusion
Public Key Encryption Example Code are a treasure trove with useful and creative ideas for a variety of needs and hobbies. Their accessibility and versatility make them a great addition to both professional and personal life. Explore the plethora of Public Key Encryption Example Code to discover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables actually for free?
- Yes, they are! You can print and download the resources for free.
-
Can I use the free printables for commercial use?
- It is contingent on the specific rules of usage. Always read the guidelines of the creator before using their printables for commercial projects.
-
Do you have any copyright violations with Public Key Encryption Example Code?
- Some printables may come with restrictions in their usage. Check the terms and conditions set forth by the designer.
-
How do I print Public Key Encryption Example Code?
- You can print them at home using your printer or visit an in-store print shop to get superior prints.
-
What software do I require to open printables free of charge?
- Most PDF-based printables are available in PDF format, which can be opened using free software like Adobe Reader.
Asymmetric Encryption For Dummies The Signal Chief
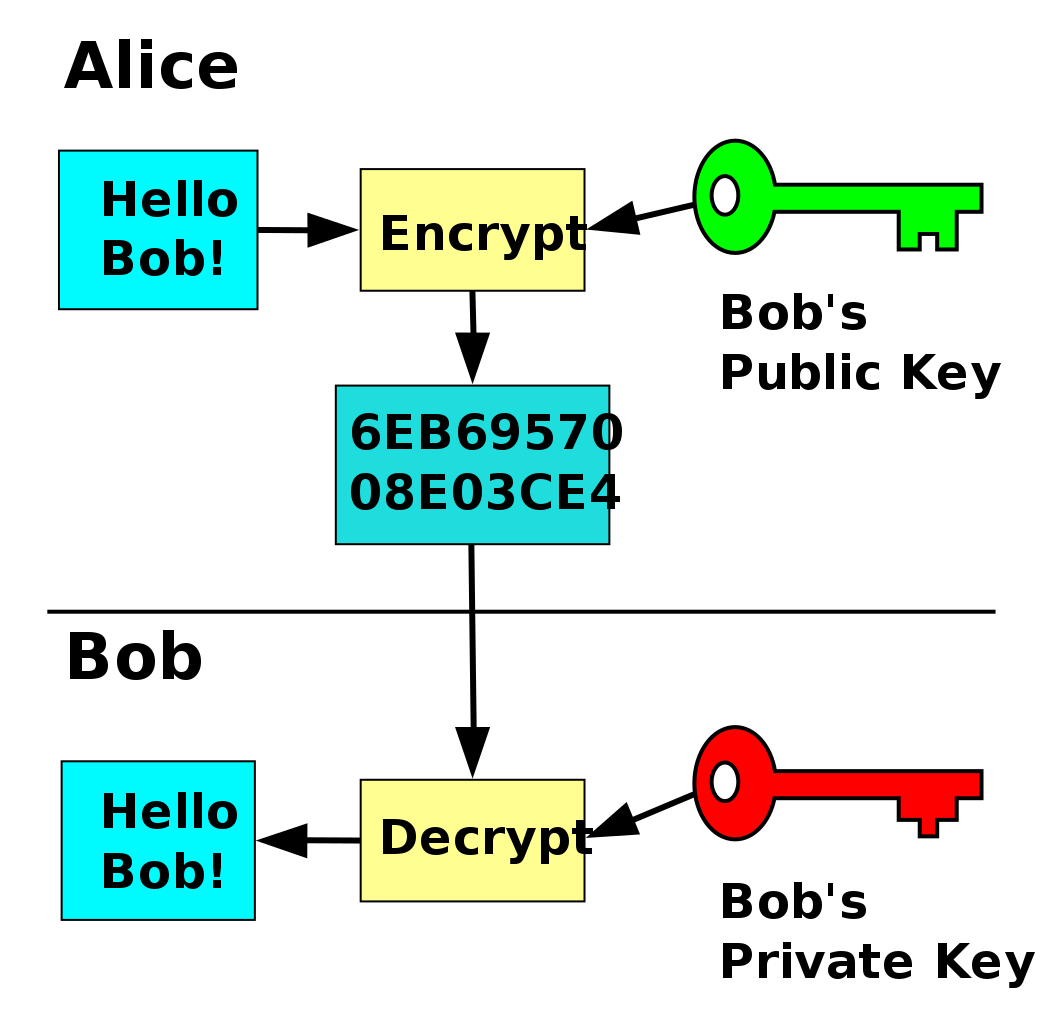
Symmetric And Asymmetric Key Encryption Explained In Plain English
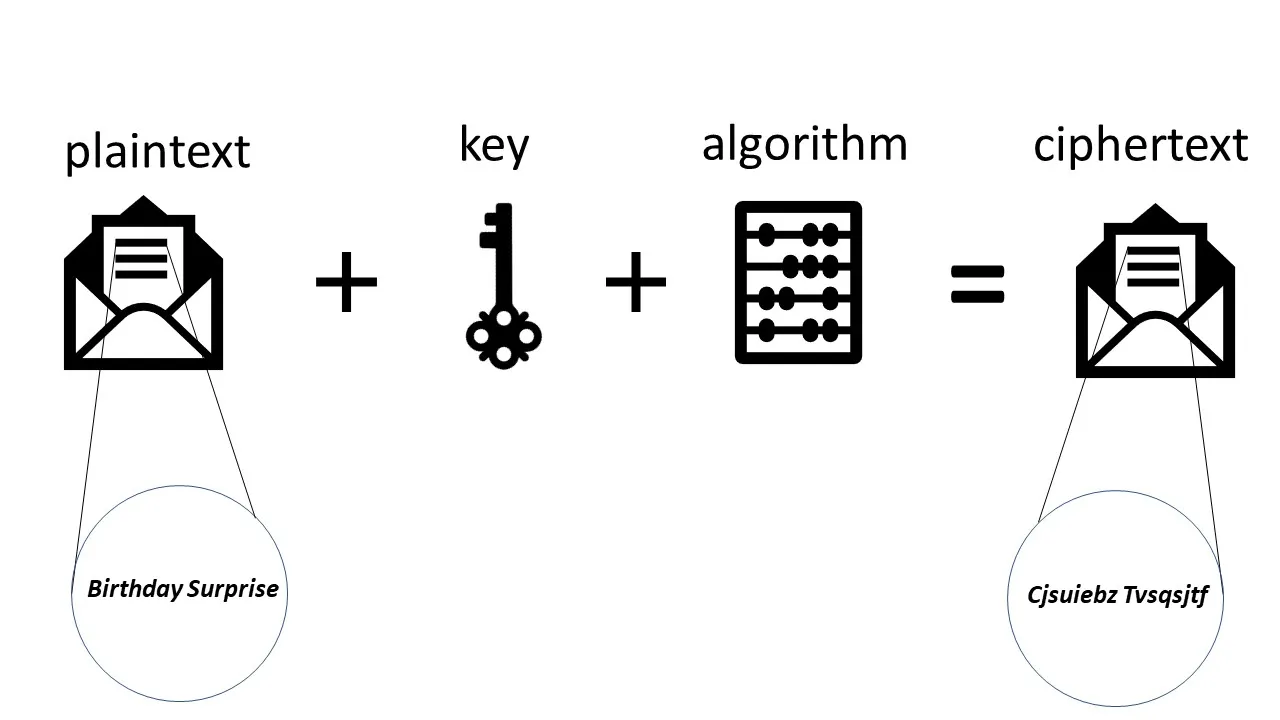
Check more sample of Public Key Encryption Example Code below
RSA Encryption Brilliant Math Science Wiki

How Public Key Encryption Ensures Data Integrity

What Is Encryption A 5 Minute Overview Of Everything Encryption
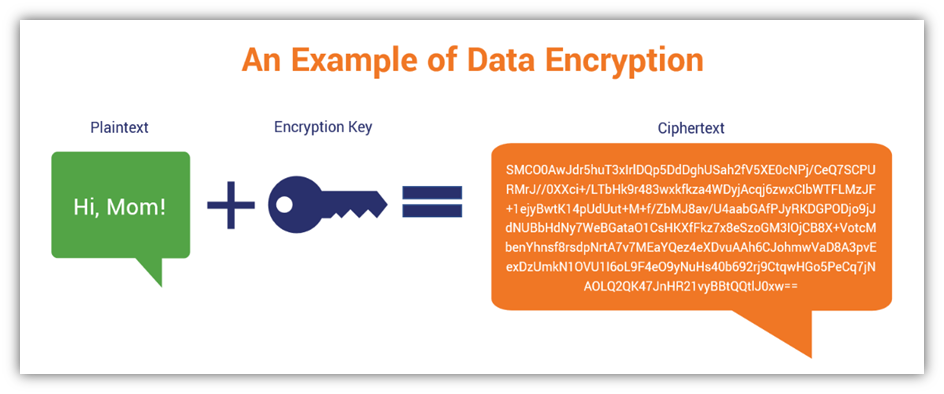
RSA Algorithm Secure Your Data With Public Key Encryption
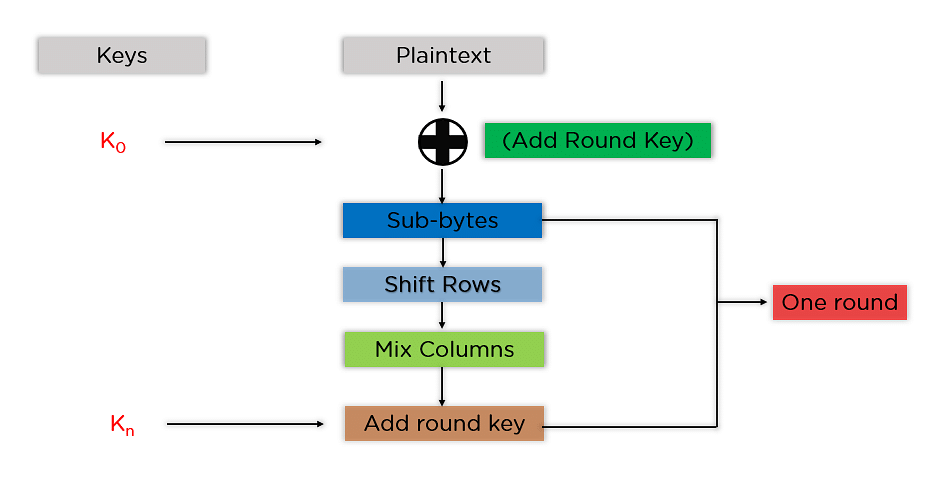
Unix Linux Encryption SSH Seyeoniii
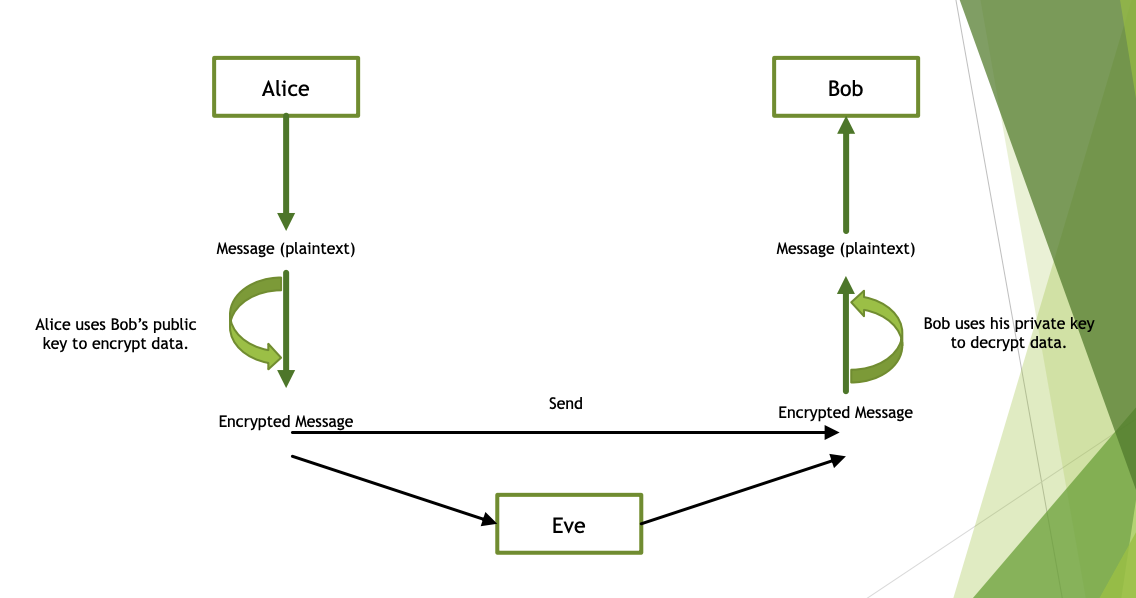
What Is Asymmetric Encryption Babypips

https://productioncommunity.publicmobile.ca › Get-Support › Login-to-m…
Paid money mistakenly to telus integrated communications and want a refund but Public Mobile Telus in Get Support an hour ago Please fix your website my account doesnt
https://productioncommunity.publicmobile.ca › Get-Support › My-Accoun…
Hello I do not recall the email address and password for my account login Please let me know how I can proceed to login as I need to update my payment info as my credit card
Paid money mistakenly to telus integrated communications and want a refund but Public Mobile Telus in Get Support an hour ago Please fix your website my account doesnt
Hello I do not recall the email address and password for my account login Please let me know how I can proceed to login as I need to update my payment info as my credit card

RSA Algorithm Secure Your Data With Public Key Encryption

How Public Key Encryption Ensures Data Integrity

Unix Linux Encryption SSH Seyeoniii

What Is Asymmetric Encryption Babypips
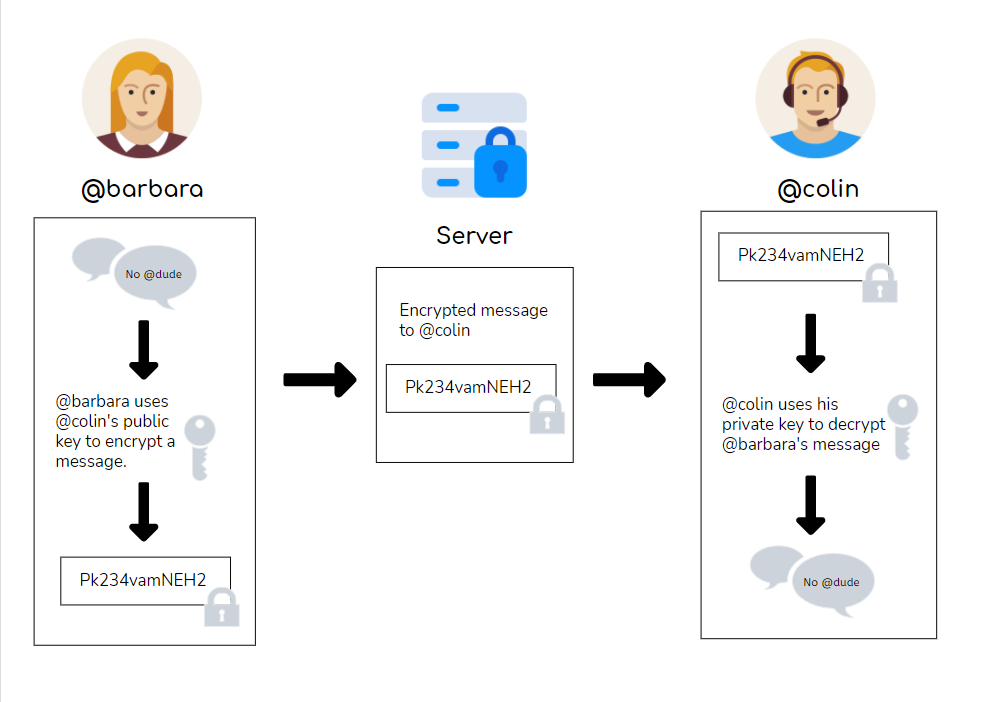
What Is End to End Encryption E2EE The Company
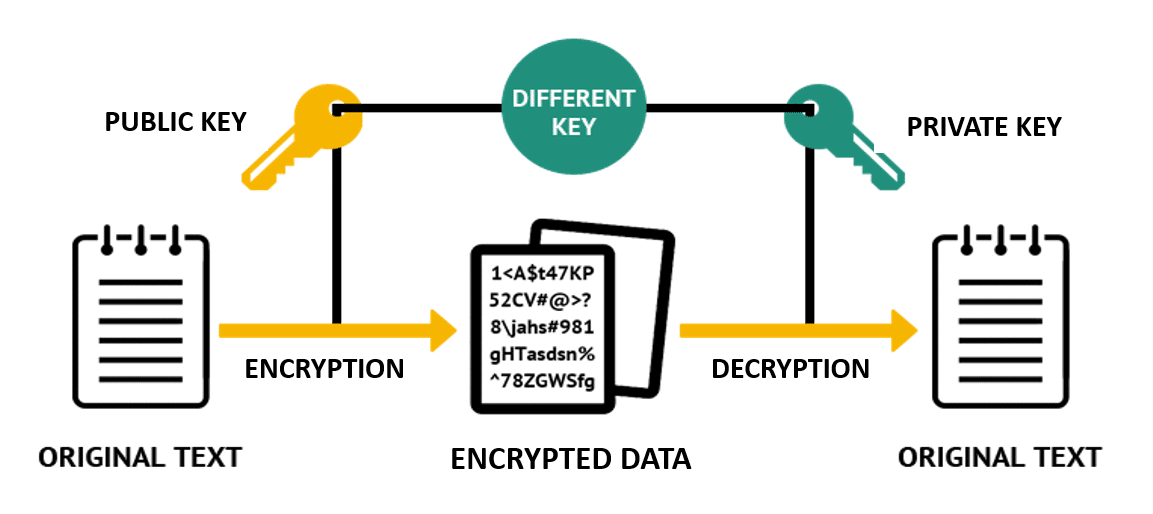
What Is Data Encryption Definition Types And Best Practices Kinsta

What Is Data Encryption Definition Types And Best Practices Kinsta
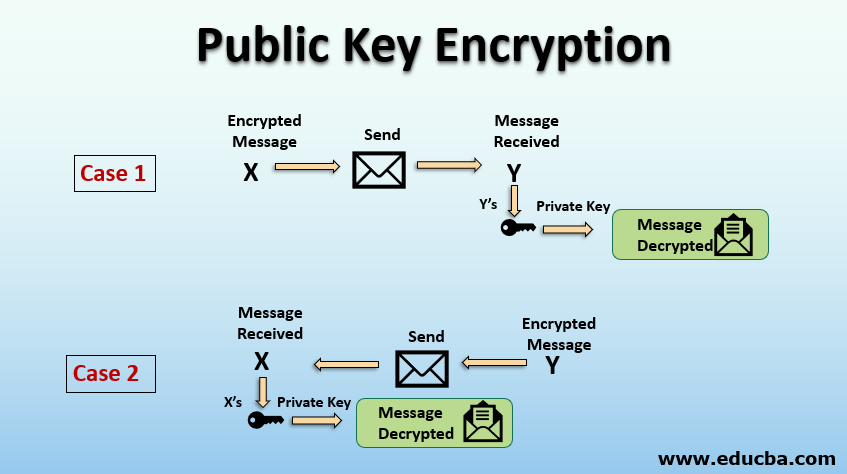
Public Key Encryption How Does Public Key Encryption Work